Last week, Amazon Web Services (AWS) announced an improvement to its IAM Access Analyzer that allows its users to proactively analyze and validate Identity & Access Management (IAM) policies against more than 100 checks and receive actionable recommendations on improving its security and efficacy.
By providing actionable recommendations, this new functionality has the potential to add a massive amount of value for AWS customers by minimizing the time and guesswork required for developers to remediate potentially risky issues with IAM policies. These checks can currently be run against four resource types, including IAM Policies, IAM Roles, Service Control Policies (SCPs), and S3 Buckets, with coverage for additional resource types expected in the future.
To make it easy for users to differentiate between urgent and non-urgent issues, the IAM Access Analyzer prioritizes the results of the checks by breaking them into four categories:
- Security Warnings
- Errors
- General Warnings
- Suggestions
The one feature gap in this otherwise massively valuable functionality is that the policy validator works on an account-by-account and region-by-region basis. This means that, for customers with a high number of accounts or regions within their AWS environment, there’s not a centralized view of these recommendations across their entire AWS footprint.
To solve this pain point, our engineers sat down and built out support for the IAM Access Analyzer policy recommendations to DivvyCloud within 48 hours of AWS’s announcement. This means that, from the DivvyCloud console, our customers can now get an overview of all findings and recommendations from AWS’s IAM Access Analyzer policy validator from across all accounts and regions on a single screen.
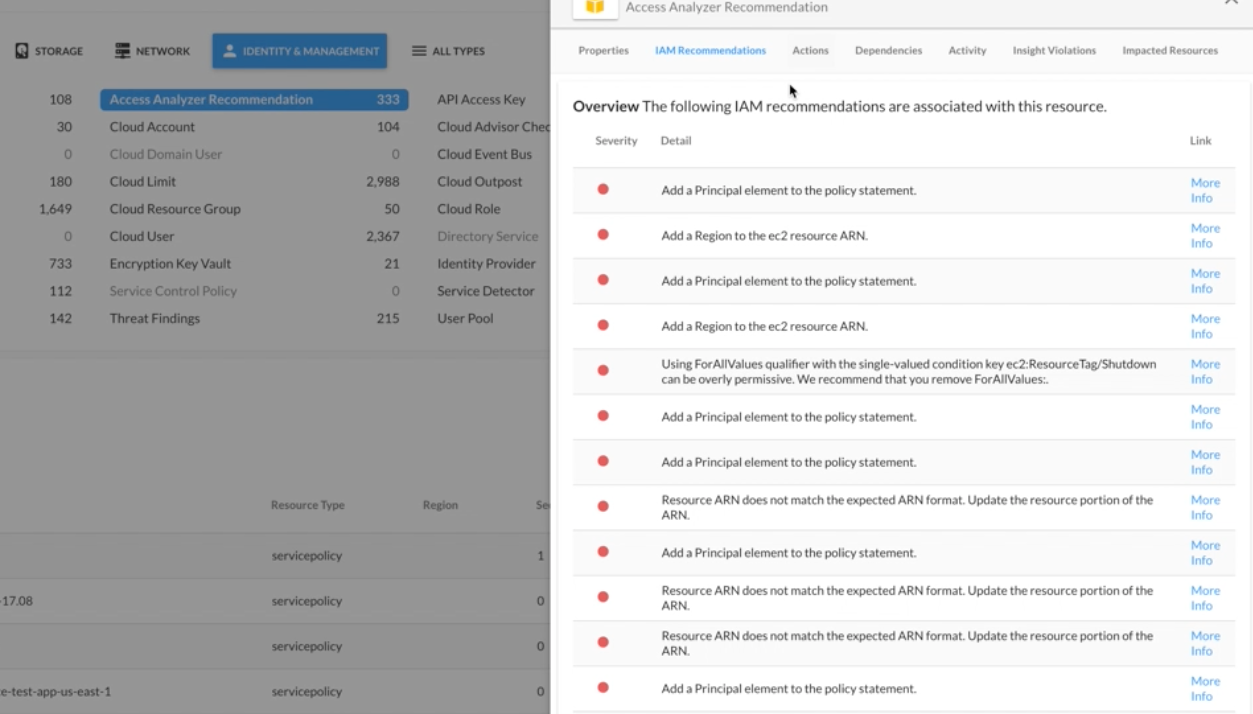
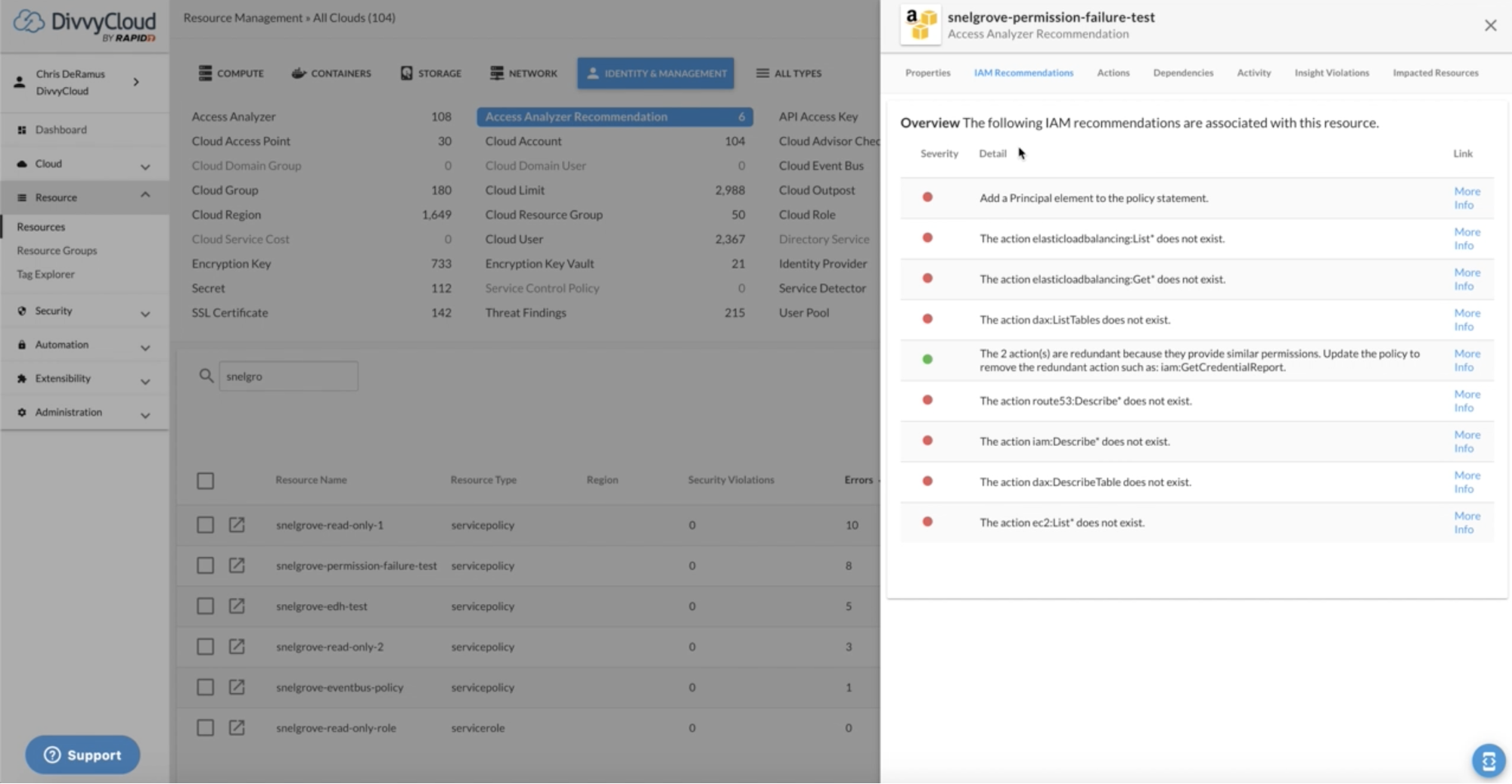
In the DivvyCloud console, these findings are broken down into the four categories listed above, so teams can easily understand whether the issue is a significant security risk or a minor error that can be cleaned up at a later time.
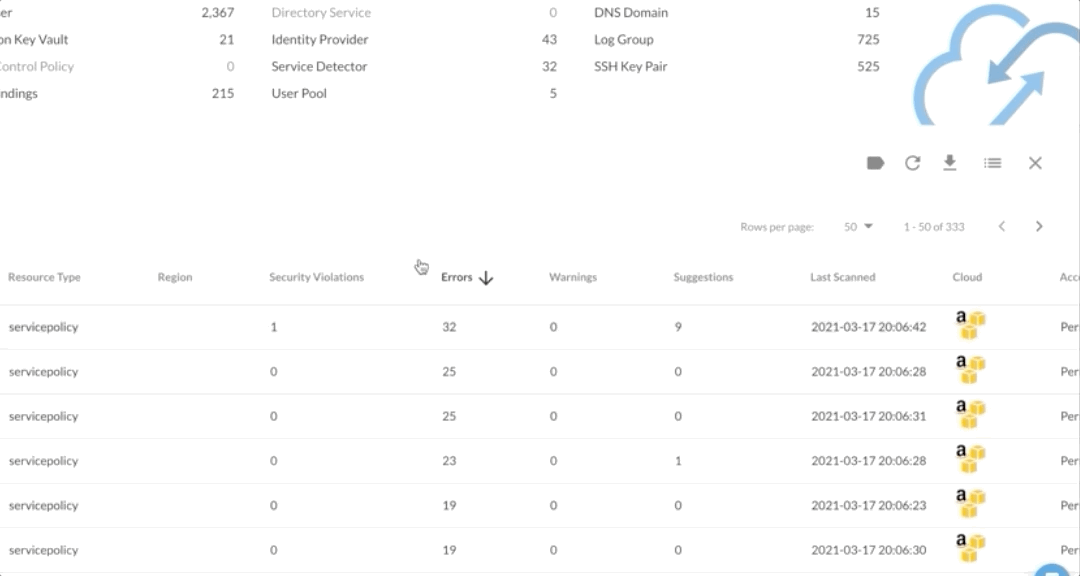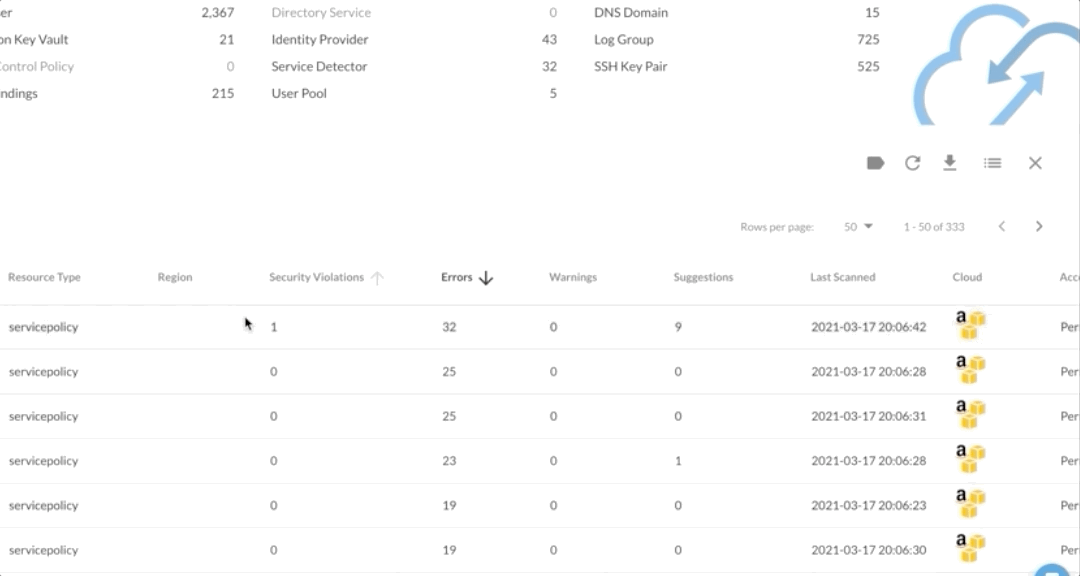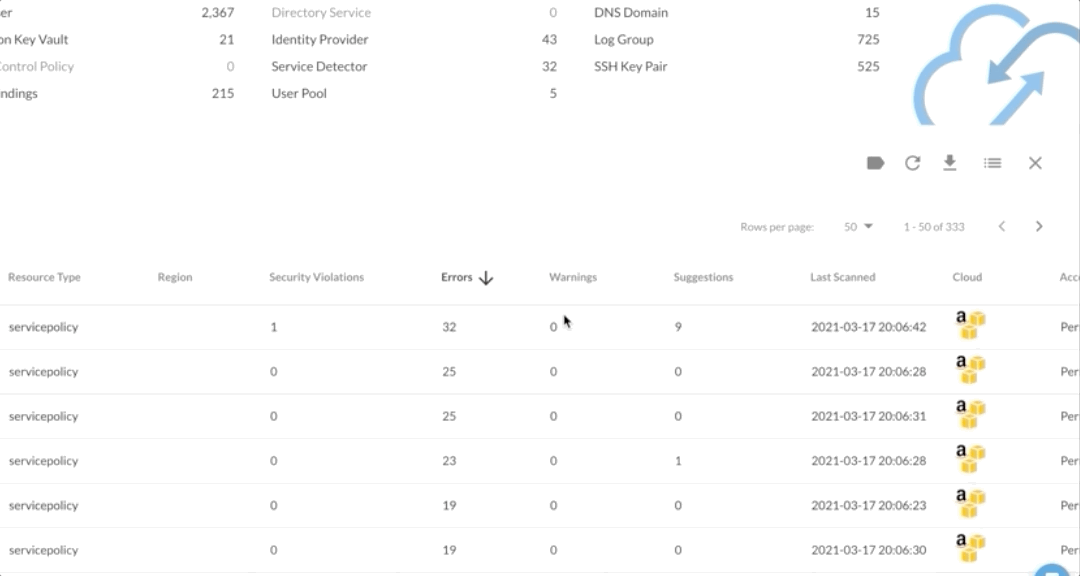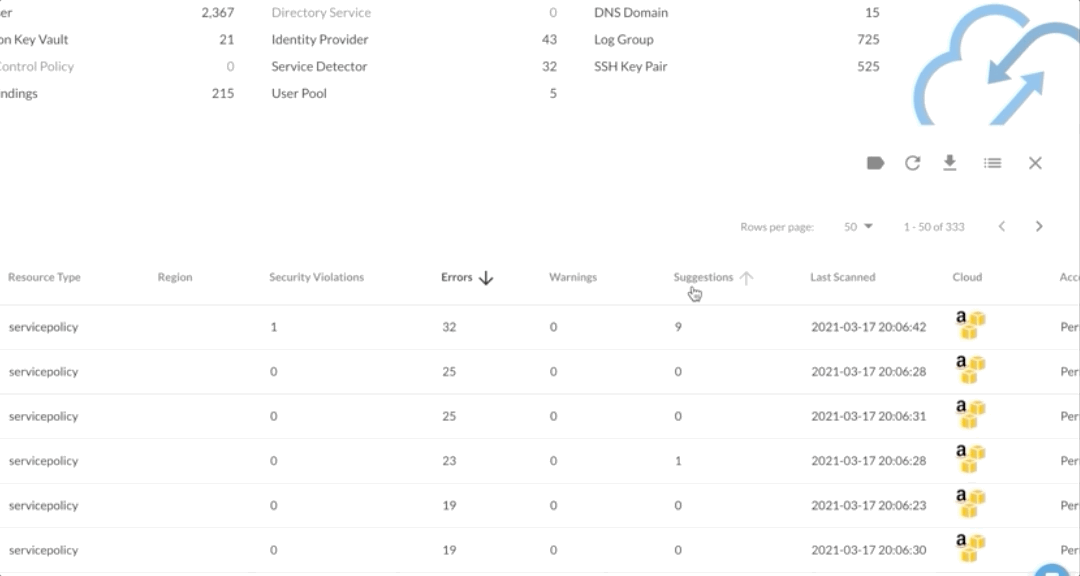
The results are easily searchable by resource name and filterable by category, making it easy to check on specific resources of high importance. And when users want to get more context about a problem, they can simply click “More Info” to see AWS documentation that explains why the policy configuration is a problem and what they can do to remediate that issue.
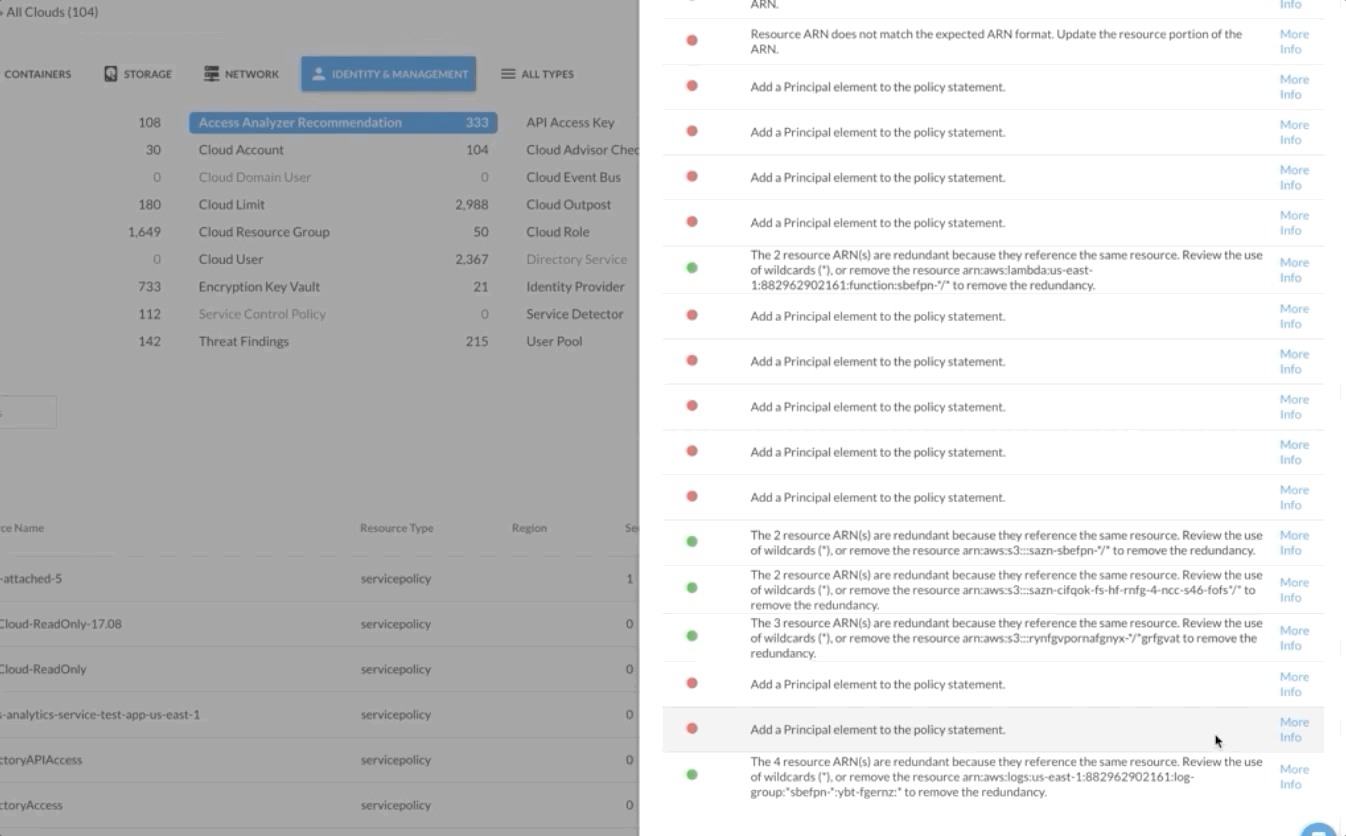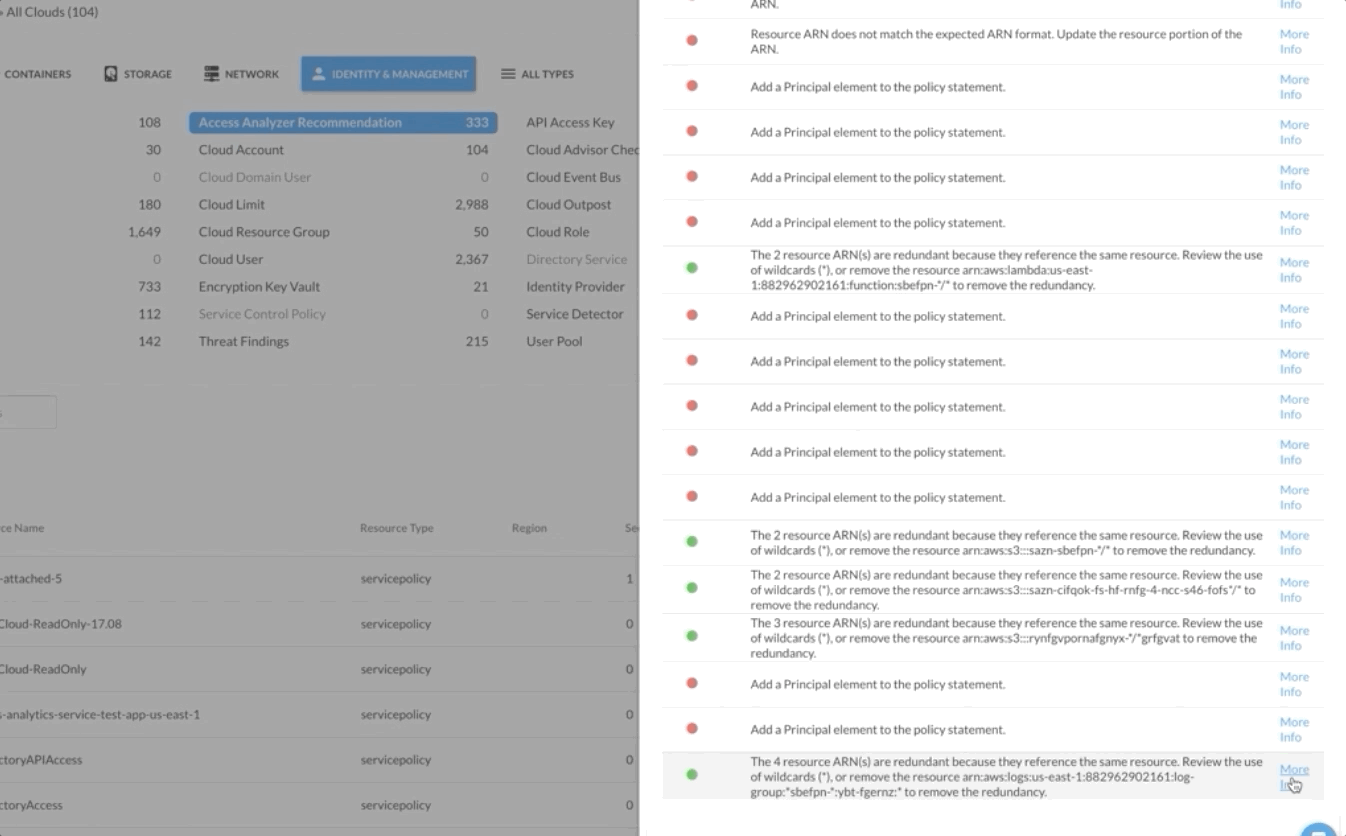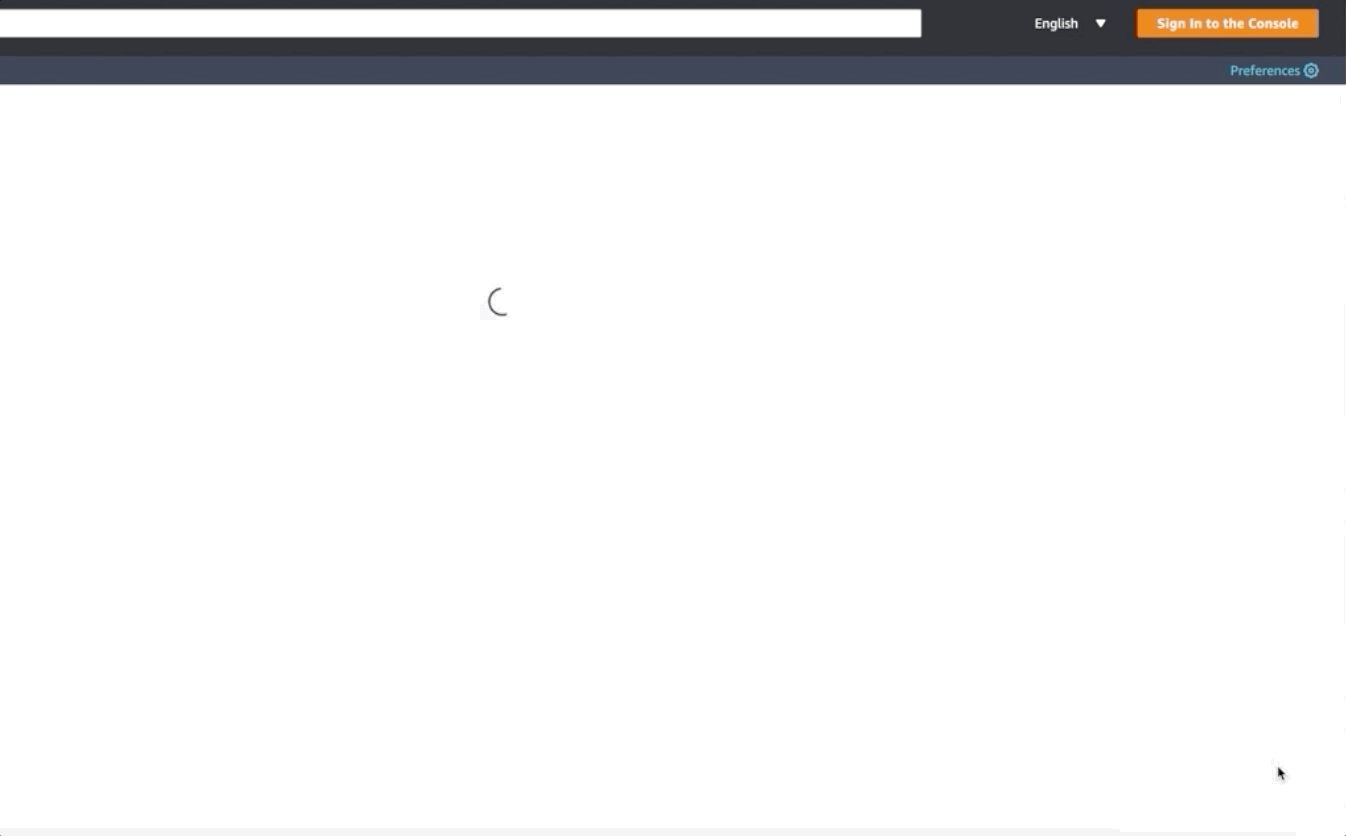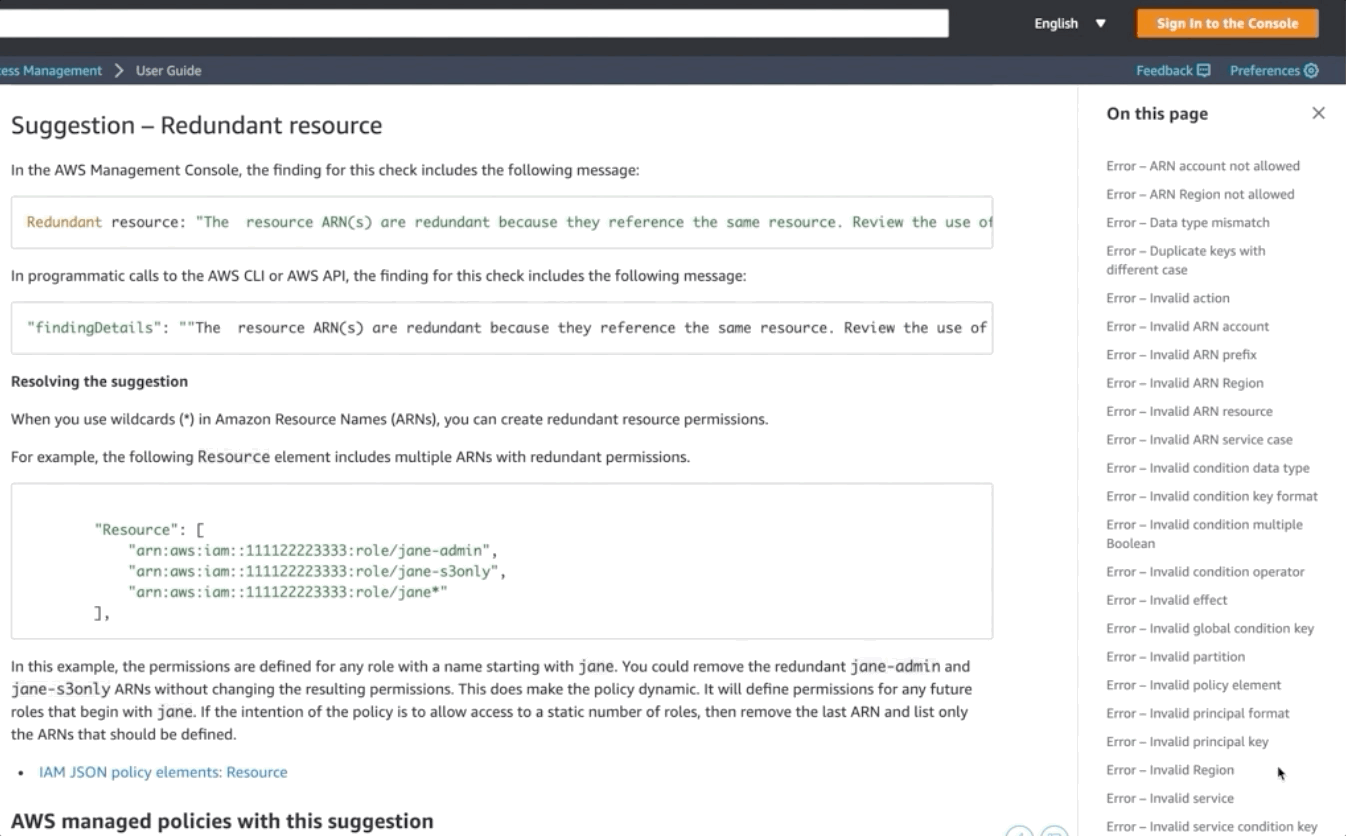
At this time, the IAM policy recommendations are updated daily within the DivvyCloud console, but an upcoming release will enable users to automatically run these checks within 60 seconds of an IAM policy being updated on a supported resource. This means that teams will have real-time visibility into any risky changes to IAM policies, as well as the ability to automatically respond by sending a Slack message, creating a support ticket, or completely killing the resource altogether.
While we’re always striving to complement and extend the value provided by new AWS features, this particular DivvyCloud update stands out for two reasons.
First, we believe this will make this IAM policy validator significantly easier to use. This validator has the potential to greatly improve an organization’s ability to maintain effective least privilege best practices. By putting all of those recommendations in a single place, with the additional environmental context available in the DivvyCloud console, we believe we can save our customers a significant amount of time and effort.
Second, releasing this update within days of Amazon’s announcement highlights our development team’s ability to be remarkably agile. The team has built a solution that is exceedingly adaptable and able to almost immediately provide coverage for new functionality that is released by cloud service providers, including AWS, Azure, GCP, Alibaba, and most recently, Oracle Cloud. Our goal is to provide our customers with a solution that moves at the speed of cloud, so that they have the ability to drive innovation in their own business, rather than slowing it down.
Want to learn more about how you can gain control of your organization’s IAM policy? Click here to check out our whitepaper, Gaining Control Over IAM Cloud Chaos.
