This blog post covers key takeaways from our 2021 Industry Cyber-Exposure Report (ICER): Fortune 500. Original analysis for these findings was conducted by Bob Rudis.
Complexity is the enemy when it comes to successful security outcomes in an organization. Diversity in systems, technologies, and business processes present real, daily challenges for even the most mature security teams, especially when it comes to patch and vulnerability management. Patching even one major vulnerability can be a herculean task in many places. Diversity compounds complexity within each technology component. That is to say, an organization may have multiple web-server technologies in use. Each technology, in turn, may have its own hodgepodge of versions, which directly (negatively) impacts configuration management and patch management.
To get a feel for how these well-resourced organizations are performing in this area, we looked at 3 factors:
- The diversity of the portfolio of a selected technology—web servers—in use by each organization
- How well an organization maintains this portfolio
- How well organizations maintain critical services, such as email gateways
Our findings show that:
- Within a single technology stack (web servers), organizations in a staggering number of industries—Business Services, Financials, Healthcare, Leisure, Industrials, Media, Technology—expose 10 or more different versions of Apache and/or Nginx. All industries have 1 or more members exposing 3 or more different versions of IIS. This increases their respective attack surfaces and makes it difficult to deploy patches (when they bother to apply patches) due to testing and quality-assurance complexity.
- Organizations have serious difficulty keeping critical IT infrastructure—such as Microsoft Exchange—current. Only around 19% (30 out of 160) of the Fortune 500 that still run self-hosted Microsoft Exchange are running current/supported versions. Further, 18% are running end-of-life versions of Exchange 2007 and 2010, putting them at risk of future vulnerability exploitation.
We used Project Sonar and Recog to identify internet-facing technologies—web servers, file servers, DNS, SSH—that were in use for each organization in the Fortune 500. We then mapped them to available Common Platform Enumeration (CPE) strings. This methodology has some limitations in that the results are constrained by:
- The fingerprints available to Recog
- How promiscuous each fingerprint service is (i.e., whether Recog can extract version information)
- The ports and protocols Project Sonar studies
- Our measurement of only IPv4-space
- Sonar honoring IPv4 opt-out requests
These constraints, if anything, generally result in underreporting of the magnitude of the findings.
Version dispersion among web servers
Back in 2018, when we began our first foray into analyzing the cyber-exposure of the Fortune 500, we created the term “version dispersion” to refer to the diversity of versions within a service component an individual organization was exposing to the internet. With the dramatic rise in enterprise use of tooling such as Kubernetes, we expected to see a reduction in version dispersion of the 3 web servers—IIS, Apache, Nginx—that we previously measured.
There are at least more than 81 distinct versions of Nginx, 70 distinct versions of Apache, and 15—yes, 15—distinct versions of IIS running across Fortune 500 members. Let’s see how that stacks up by industry.
A higher density of points toward “1” on the X-axis means that each of the organizations those points represent are running with a low version dispersion. This means they have better control over server/service deployments and configurations, have fewer versions to test patches against, and can make changes faster and with more confidence than others. It also likely means they have a more rigorous “you must be this tall to deploy a server on the internet” rule than organizations further to the right on the X-axis. Attackers and cyber-insurance assessors alike notice such things, and may be more likely to target organizations that exhibit a more “wild wild west” stature.
Version dispersion: Focus on Microsoft Exchange
Some internet-facing services are more important than others. It’s one thing to have a crusty old Apache HTTPD server attached to the internet, which may only have a denial-of-service weakness. It is quite another thing to run old versions of what most organizations would–or should–deem critical infrastructure, such as Microsoft Exchange servers or VPN/gateway/remote access services.
To get a feel for how well these organizations maintain critical services, we’ll take a peek at Microsoft Exchange hygiene. Nearly 40% of Fortune 500 organizations still have at least one internet-facing Exchange server handling business-critical email, and Exchange has had a fair number of weaknesses—of varying criticality—uncovered over the years:
Surely these organizations take care to ensure this vital service is at peak resiliency, at least when it comes to security patches. Right?
The above figure paints a fairly disturbing picture of the state of Microsoft Exchange in the Fortune 500 in both currency (i.e., age of some server versions) and whether the deployed version is supported by standard Microsoft support contracts. On the plus side, 31% of discovered, precise-version fingerprinted instances are 2020 releases; 72% of these are at a version normally supported by Microsoft.
Fortunately, only a few are running Exchange 2007 (which has been at end-of-life status for a while). Unfortunately, a sizable chunk of the Fortune 500 did not seem to get the memo about Exchange 2010 reaching end-of-life status in October 2020.
Oddly enough, organizations that run Exchange 2013 do a much better job of keeping current than those running more recent releases. This appears to be largely due to Exchange 2013 having far fewer in-year updates than its siblings.
And, the outlook is still pretty grim across industries. The figure below shows release-and-support status of Exchange deployments in each industry, and virtually all of them are having trouble keeping current.
For those as curious as we were about that thin line of “supported” blue points right at the tail end of 2020, the build is “14.3.509”. This is a very recent—and unlisted on Microsoft’s support page—version of Exchange 2010, so it looks like it may not be so end-of-life after all.
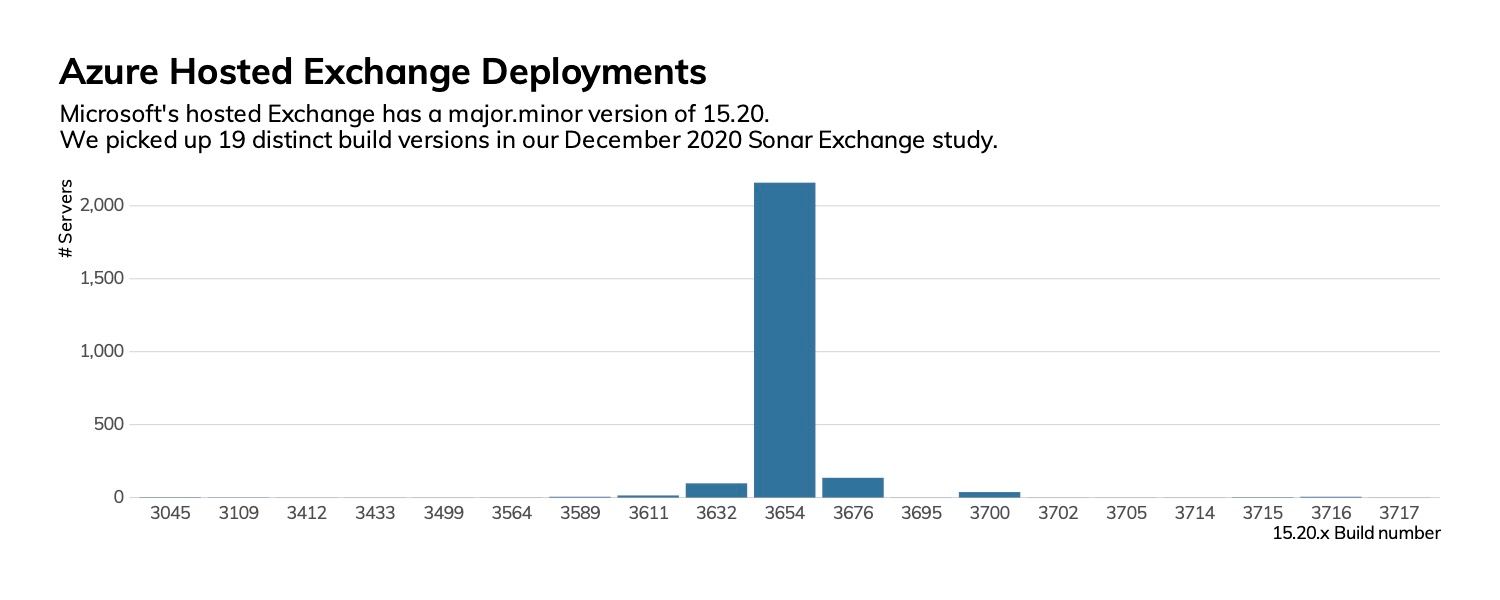
If keeping Exchange deployments updated, secure, and resilient is a challenge for you, take some comfort in the fact that even Microsoft has issues normalizing hosted Exchange (Microsoft 365) build levels.
CISO takeaways
For this section, we’ll be talking to 2 different sets of CISOs: those who see their image reflected in the mirrors in each of the sections, and those who have organizations like this as business partners or suppliers.
If you’re a security leader who is working to build resilience and safety into the DNA of your organization, issues such as technology sprawl, version management, and critical service maintenance are non-negotiable must-haves. The good news is that these aren’t just “security” issues. Organizations deploy services to meet a business need, and it is far easier to sustain service uptime and stability if there are fewer moving parts to maintain. To achieve buy-in with your peers, collect historical and current data regarding service degradation (and/or outages). Add to that data how long it takes IT, application, and operations teams to support each component of each business process. If you pair that up with information on the volume and severity of identified weaknesses (CVE-based or otherwise), you will find areas that have a solid business case to warrant partnering for improvement. As each area ameliorates, you’ll have far more agency to affect change in other lagging areas.
For those who shuddered at what this section revealed, make sure these are areas you look for when evaluating third parties on behalf of business-process stakeholders in your organization. It’s fairly straightforward to both ensure you’re asking about these potential areas of weakness and verifying that the answers you receive are accurate. There’s no guarantee that the internal exposure of organizations reflects what is seen externally. However, it is generally more likely that the internal picture is even worse than what is presented to the outside world. Holding your partners and suppliers to a higher level of safety and resilience will not only lessen the risk to your organization, but can also have a cascading positive effect as other organizations follow the standards you’re setting.
Want to learn more about the internet-facing cyber-exposure of the Fortune 500? Read our 2021 Industry Cyber-Exposure Report (ICER): Fortune 500.

