This blog post covers key takeaways from our 2021 Industry Cyber-Exposure Report (ICER): Fortune 500. Original analysis for these findings was conducted by Tom Sellers.
There are certain services that are generally considered to be high-risk when found available on the public internet. As an example, with very few exceptions, placing SMB file shares on the internet is considered a Bad Thing. Doing so may expose data, leak environmental information such as domain names, enable brute-force attacks against credentials, and provide a vector for exploiting vulnerabilities in the Windows Server Message Block (SMB) implementation, as was seen in the Conficker and WannaCry worms.
In our research across the public internet, we know that we’re only seeing a surface level of information, and we often try to find ways to understand what it is telling us about the organizations that operate these services. We can look at configuration and protocol details and use them as proxy markers for the internal environment and security maturity of an organization.
For example, if we discover an SMB service and can detect that it doesn’t support SMBv2, which was introduced in Windows Vista and Server 2008, we can make certain assumptions about the age of the operating system and/or requirements for legacy compatibility.
If an organization permits Telnet 20 connections to routers from a different country, we can make assumptions about the age of the equipment as well as the security policies for secure protocols and network access control lists (ACLs).
In order to get a sense of how well the Fortune 500 organizations were performing in this area, we surveyed SMB, Windows Remote Desktop Protocol (RDP), and Telnet on the default ports in their public IPv4 address space and reviewed service data where present.
Our findings show that:
- Most of the exposure was in 2 industrial groupings: Financials and Hotels, Restaurant, and Leisure.
- Of those hosts exposing SMB, 95% provided a hostname, 91% leaked the DNS name of the host, and 92% leaked the fully qualified domain name (FQDN) configured on the host.
- RDP 403 services were found across 61 companies. These were heavily skewed toward the Technology, Healthcare, and Financials industries.
- The Financials industry dominated the Telnet exposure list with 61% of the total.
We used Project Sonar and Recog to identify internet-facing SMB, Windows Remote Desktop Protocol (RDP), and Telnet services on the default ports that were in use for each organization in the Fortune 500. In each case, we fully negotiated the protocol to verify that we were indeed communicating with the expected service. This methodology has some limitations in that the results are constrained by the fact that:
- Services are only observed on the default ports. Telnet and, less commonly, RDP can be moved to non-default ports.
- Measurements are made only in IPv4-space.
- Certain IP ranges are not examined by Sonar by request.
- Certain cloud and ISP related ranges were excluded.
These constraints, if anything, generally result in underreporting of the findings.
Findings: RDP, SMB, and Telnet
We should start this section by stating that any non-zero number of these services made available to the general internet is considered to be unacceptable in organizations with mature security programs. Followers of the Rapid7 blog and past Rapid7 research reports will be quite familiar with this advice, but looking at the calendar here in 2021, we have to note that it's been a while since the last major worm outbreak on the internet. NotPetya (SMB) was 2018, WannaCry (also SMB) was 2017, and Mirai (Telnet) was way back in 2016. Despite all the vulnerability and exploit churn we saw in 2019 and 2020, we appear to be overdue for another self-replicating issue across open ports to insecure services. Closing off your exposure to these services will certainly save you weeks of cleanup later.
Windows Remote Desktop Protocol (RDP)
While some may think RDP should be considered an exception to this rule, we'd argue that there are commonly available techniques and technologies such as virtual private networks (VPNs), RDP gateways, and firewall access control lists (ACLs) that remove the risk related to this technology and so, as a general rule, RDP shouldn’t be exposed to source addresses outside of the organization.
Since we’re on the topic of RDP, let's start with the discussion with the findings there. On the default RDP port of 3389/tcp, we observed 403 services across 61 companies. These were heavily skewed toward the Technology, Healthcare, and Financials industries.
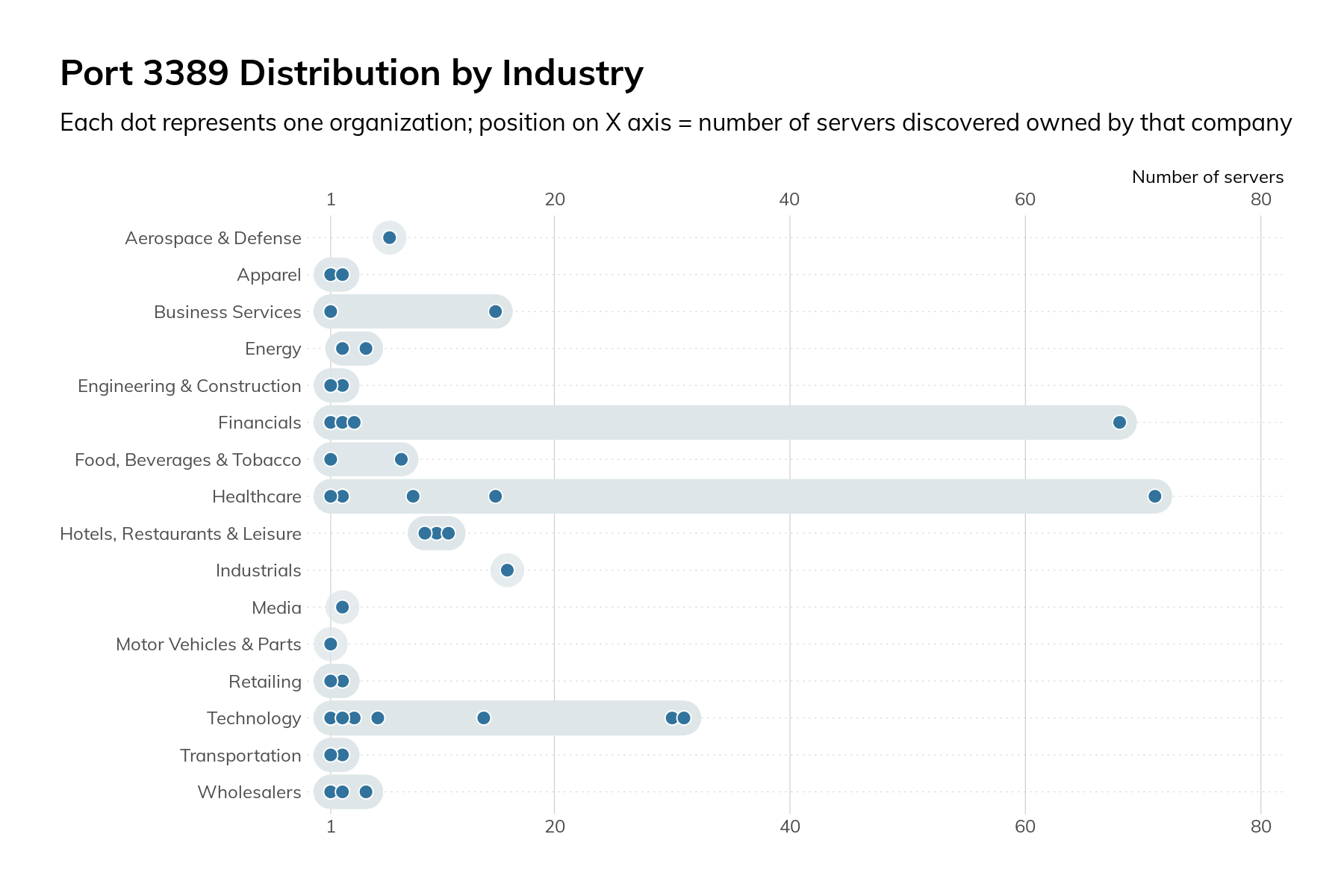
The graphic above shows that the overall numbers are mostly attributable to just a few companies and aren’t inherent to the operations of a specific industry.
On a positive note, when we looked at the security requirements for RDP authentication, we found that 92% required Network-Level Authentication (NLA). NLA, introduced in Windows Server 2008, enforces Transport Layer Security (TLS) protection of traffic in-flight, strengthens authentication options, and significantly reduces the risk and impacts related to brute force and certain denial-of-service attacks. NLA has been enabled by default since Windows 2012. The lack of NLA serves as a proxy indicator for older infrastructure either on the server itself or a requirement for compatibility with older clients. The only other reason for not having NLA enabled is that it doesn’t allow authentication with expired passwords. That is another reason to deploy RDP gateways, VPNs, or other infrastructure to provide facilities for changing the password as well as enable security access to remote desktop services.
Windows Server Message Block (SMB)
The SMB protocol is for file- and print-sharing as well as interprocess communication on Windows and compatible networks. We say this in every report, but SMB should never be exposed to the internet. The risks include data leakage from file shares, credential compromise via brute-force attacks, and malware infection (think of the previously noted Conficker and WannaCry) via vulnerabilities in the host operating system or service. Given the plethora of options for securely sharing files, SMB shares aren’t worth the risk.
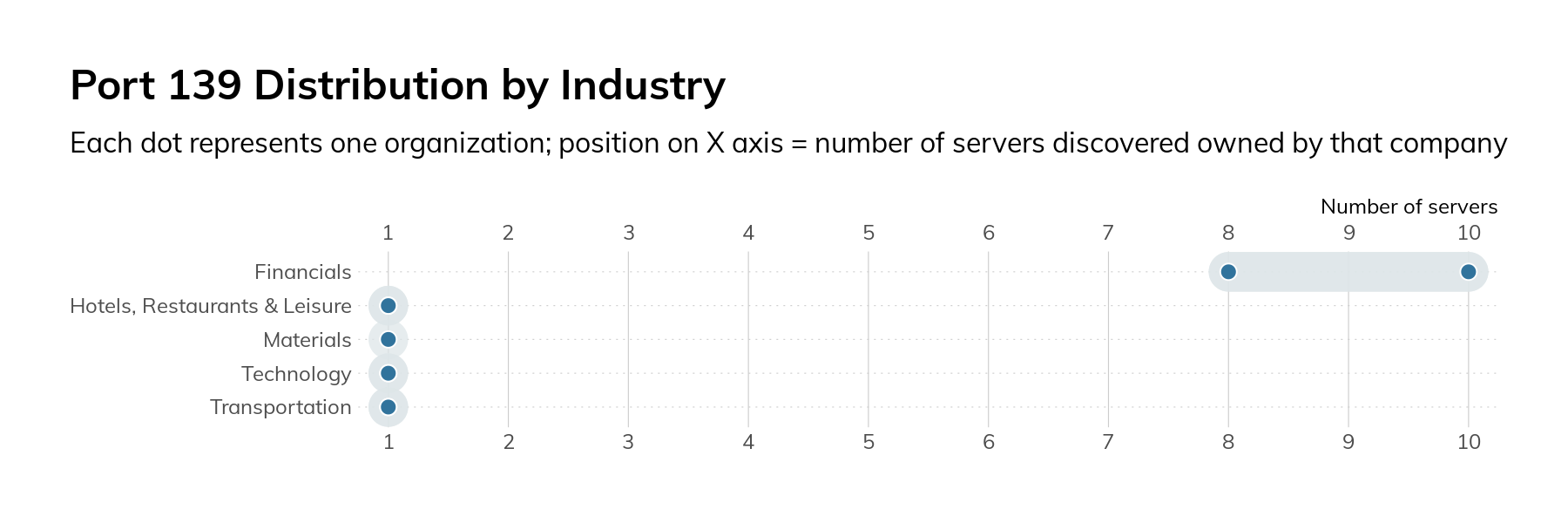
When we surveyed the Fortune 500, we decided to look at 2 different SMB ports: 139/tcp and 445/tcp. Port 139/tcp is used for older variants of SMB, and its presence is generally a sign of very old software and legacy requirements. In our surveys, we only found 25 servers across 9 companies. Most of these are running an open source SMB server called Samba. The oldest version of Samba we observed was released in late 2007 and contains quite a few critical vulnerabilities.
We also surveyed SMB on port 445/tcp. Introduced in Windows 2000, this transport for SMB removed some of the legacy protocol overhead. In our research, we observed 190 servers across 53 organizations. As in the case of RDP, most of the servers were attributed to just a handful of companies.
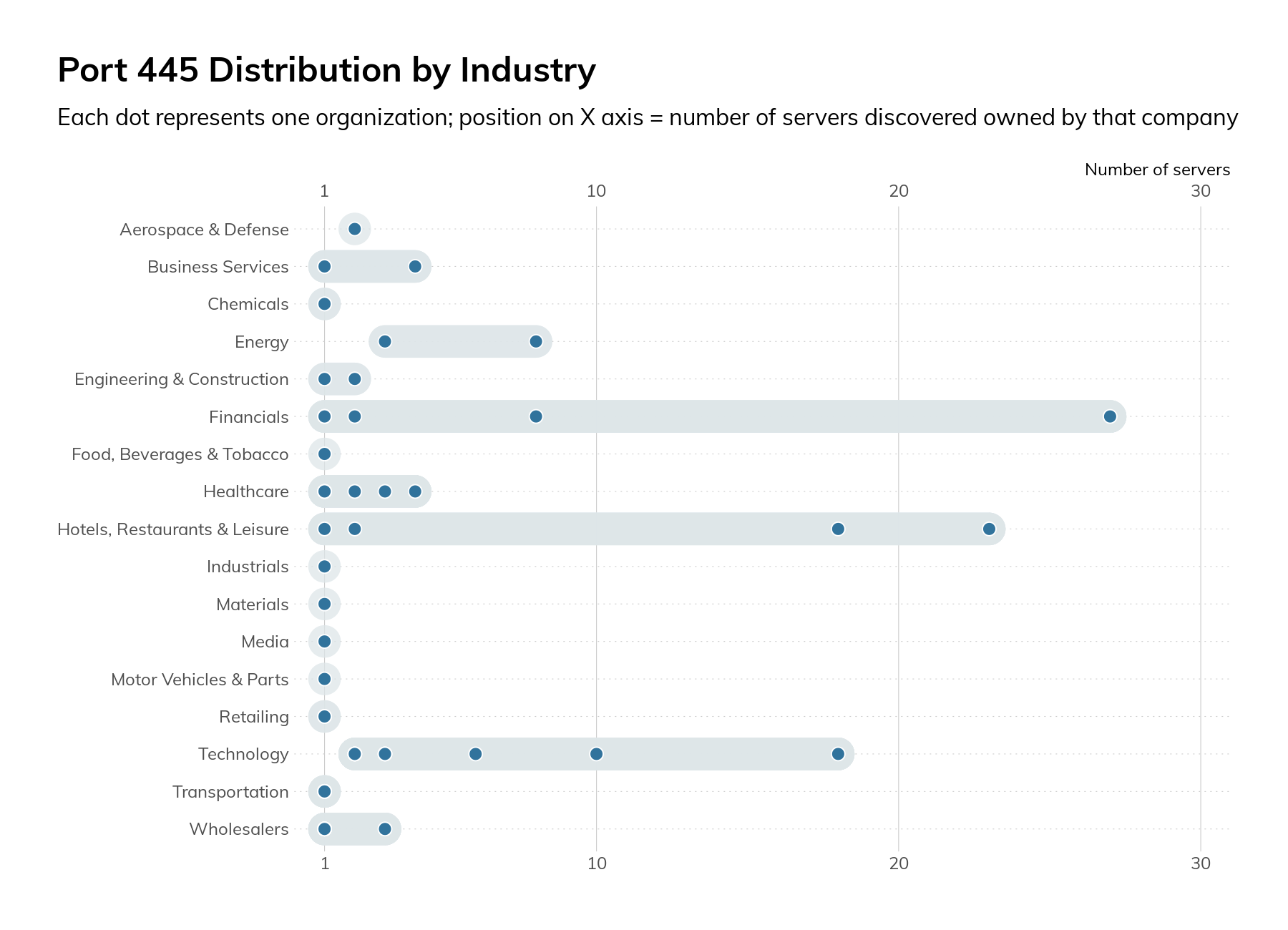
The mere presence of these SMB servers on the internet is cause for concern, but when we dug into the protocol configurations, the concern increased. All 190 servers supported SMBv1, which means they are missing several critical security controls, and attackers can force clients to downgrade to SMBv1 from more secure versions of the protocol. Also, 11% only supported SMBv1 and none of the more modern versions. We strongly recommend Microsoft’s guidance on SMB v1.
SMBv3.0 was released with Windows Server 2012 and included many security and performance improvements, such as encryption of data on the wire and protocol downgrade protections. Only 60% of the observed servers supported any version of SMBv3.
These SMB services also leaked information about the organization. Of the 190 services, 95% provided a hostname, 91% leaked the DNS name of the host, and 92% leaked the fully qualified domain name (FQDN) configured on the host. This information may indicate role (VCENTER01) or indicate internal organizational structure (db1.prod.us.corp.local).
Telnet
Telnet is a plaintext-based protocol used for providing remote console access to devices. It nearly always transmits credentials and data in cleartext and has no protections against man-in-the-middle (MiTM) injection of commands or data. Originally specified in 1969, Telnet is well past its “Use By” date and has been superseded by other, more secure technologies such as SSH. Our survey found 1,249 hosts across 131 companies. The vast majority of these hosts (756) were in the Financials industry, followed by 177 in the Hotels, Restaurants, and Leisure industry grouping.
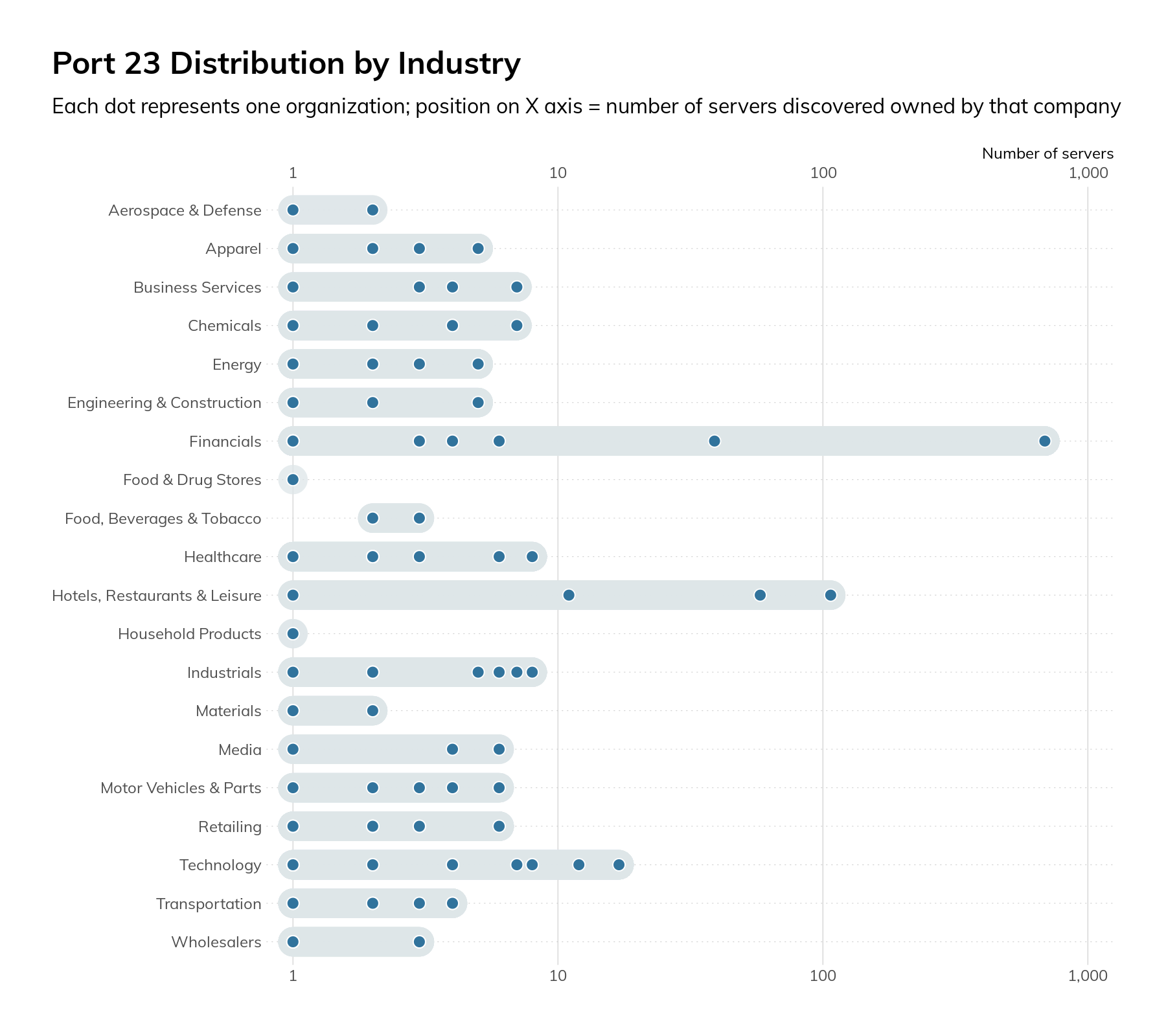
Most of the equipment was found to be a router or switch, though there were a handful of printers, industrial control systems (ICS) gateways, cameras, firewalls, and servers. As a general rule, it’s considered insecure to use Telnet as opposed to more secure protocols such as SSH. Also, if Telnet is unavoidable, firewall access control lists (ACLs) and other controls should be used to limit which internet IPs can access the devices. Since our survey process had to make connections from multiple IPs—in some cases in different countries—to validate a service, we can say that this was likely not in place or overly broad.
When we look across the surveyed protocols and industries, we can see that there are certain hotspots.
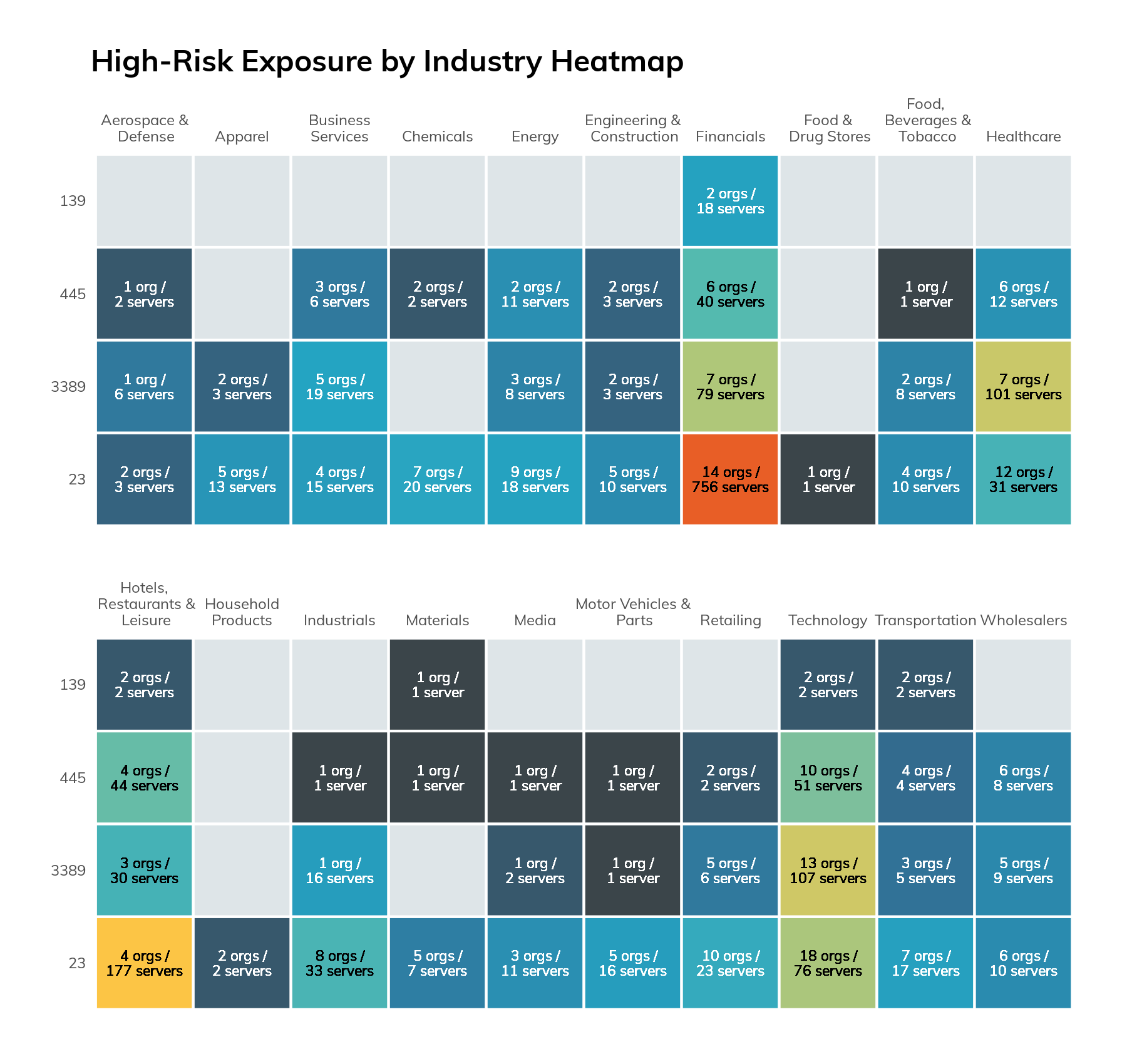
While we would expect to see more exposure in the Technology industry, the highest level of exposure was actually observed in 2 industries: Financials and Hotels, Restaurant, and Leisure. This is due to the outsized impact of just a few companies, which we will not name for obvious reasons. One company was responsible for 44% of all IP addresses that exposed at least 1 risky service. The next highest was a company that controls 8% of the list. On a more positive note, when excluding cloud and ISP network ranges, we did not observe these services on the default ports for 337 of the Fortune 500 companies.
CISO takeaways
The findings here indicate that even some of the most resourced companies are exposing services that have an outsized risk.
Our guidance for addressing the risks above isn’t to implement some advanced security controls or software, but to instead return to the basics. You can find all of them in the early parts of the CIS Top 20 controls.
- Develop and maintain an inventory of internet-facing hosts that includes software versions, roles, and services that are expected to be exposed, as well as the reason why. Make sure that this inventory is validated by outside-in scans of all of your public-facing IP ranges.
- Implement security policies and supporting configuration standards that enforce the use of secure protocols and configuration settings. Using the example of Telnet, every device currently using Telnet should be able to support SSH—and if it doesn’t, it is too old or insecure to be directly connected to the internet.
- Ensure that software and hardware are kept current. In many cases, such as with Microsoft Windows, newer software brings better security features and controls. Older software’s lack of these features can force security trade-offs and require the implementation of compensating controls, which add complexity.
Want to learn more about the internet-facing cyber-exposure of the Fortune 500? Read our 2021 Industry Cyber-Exposure Report (ICER): Fortune 500.

