On Tuesday, May 25, 2021, VMware published security advisory VMSA-2021-0010, which includes details on CVE-2021-21985, a critical remote code execution vulnerability in the vSphere Client (HTML5) component of vCenter Server (6.5, 6.7, and 7.0) and VMware Cloud Foundation (3.x and 4.x). The vulnerability arises from lack of input validation in the Virtual SAN Health Check plug-in, which is enabled by default in vCenter Server. Successful exploitation requires network access to port 443 and allows attackers to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server. CVE-2021-21985 carries a CVSSv3 base score of 9.8.
While there are no reports of exploitation in the wild as of May 26, 2021, defenders may remember that CVE-2021-21972, another critical vCenter Server vulnerability from earlier this year, saw widespread exploitation within a few days of disclosure. It is likely that this latest severe flaw will follow suit, and we strongly recommend patching on an emergency basis, particularly given the increased prevalence of ransomware (whose operators often already have access to corporate networks via phished, leaked, reused, or otherwise stolen credentials). Edit June 5, 2021: Exploitation is now occurring in the wild. See AttackerKB for full technical analysis.
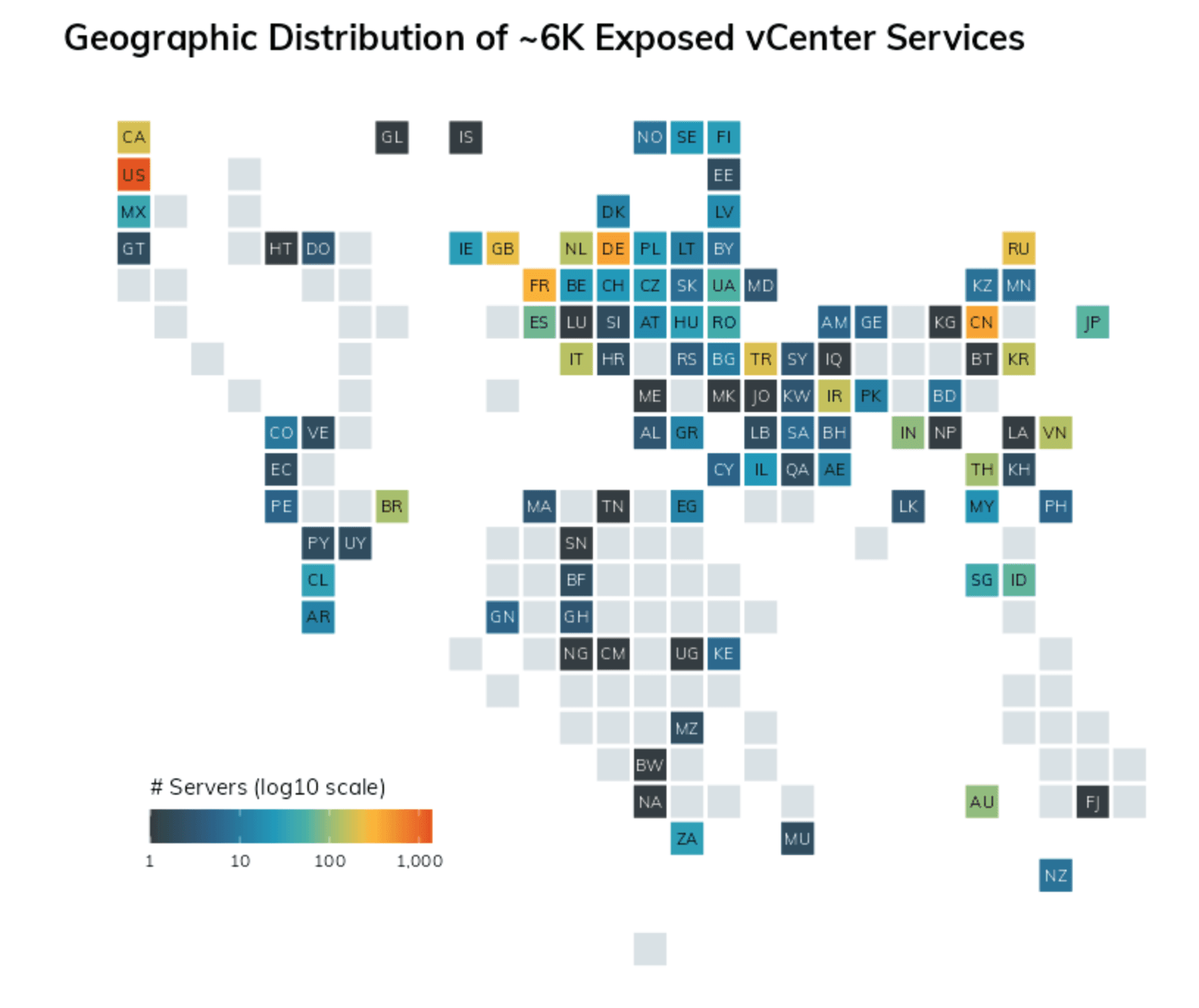
Rapid7 Labs identified roughly 6,000 instances of vCenter Server exposed to the public internet as of May 26, 2021:

Recommendations
VMware has a number of resources available for vCenter Server customers looking to understand and address CVE-2021-21985 and other vulnerabilities in this week’s advisory, including a blog post and a supplemental FAQ.
Organizations should update to an unaffected version of vCenter Server immediately, without waiting for their regular patch cycles. Those with emergency patch or incident response procedures should consider invoking them, particularly if their implementations of vCenter Server are (or were recently) exposed to the public internet. If you are unable to patch immediately, VMware has instructions on disabling the Virtual SAN Health Check plugin here. Note that while disabling the plugin may mitigate exploitability, it does not remove the vulnerability.
Network administrators should ensure that vCenter Server is not exposed to the internet.
For further technical information of CVE-2021-21985, as well as community assessments of exploitability and attacker value, see AttackerKB. We'll update this blog post with more information as it becomes available.
Rapid7 Customers
InsightVM and Nexpose customers can assess their exposure to CVE-2021-21985 with a remote vulnerability check.
Update June 5, 2021: Multiple community sources have confirmed CVE-2021-21985 is being exploited in the wild.