Hot off the press, it’s another issue of the Patch Tuesday blog! While the number of vulnerabilities is low this month, there are a number of high risk items administrators will want to patch right away including a few that will require additional remediation steps. This Patch Tuesday also includes updates for three vulnerabilities that were publicly disclosed earlier this month. Let’s jump in.
Windows Elevation of Privilege Vulnerability aka HiveNightmare/SeriousSAM
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934
With a public proof-of-concept having been available for some time, administrators should prioritize taking action on CVE-2021-36934. Remediation for this vulnerability requires volume shadow copies for system files to be deleted. This is due to the nature of the vulnerability, as the files with the vulnerable permissions could be restored from a backup and accessed even after the patch is installed. Microsoft indicates they took caution not to delete users' backups, but the trade-off is that customers will need to do the chore themselves. We've updated our blog post with this additional information.
Windows LSA Spoofing Vulnerability aka ADV210003
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36942
Another high priority action for patching teams is CVE-2021-36942. This update patches one of the vectors used in the PetitPotam attack. After applying this update there are additional configurations required in order to protect systems from other attack vectors using registry keys. The InsightVM team has included detection for the registry keys needed to enable EPA and SMB Signing in addition to the normal update. Please see our blog post for more information.
Windows Services for NFS ONCRPC XDR Driver Remote Code Execution Vulnerability
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-26432
While Microsoft has not offered up any details for this vulnerability we can glean some info from the CVSS information. This remote code execution vulnerability is reachable from the network service with no authentication or user action required. There may not be an exploit available for this yet, but Microsoft indicates that “Exploitation [is] more likely”. Put this update near the top of your TODO list.
Windows TCP/IP Remote Code Execution Vulnerability
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-26424
Last on our list is a vulnerability that can result in remote execution on a Hyper-V host via the IPv6 networking stack. If Hyper-V is used in your environment this should be first on your list this month.
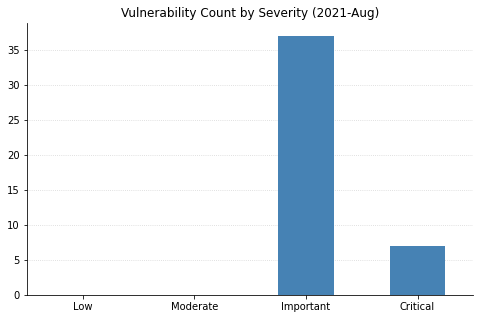
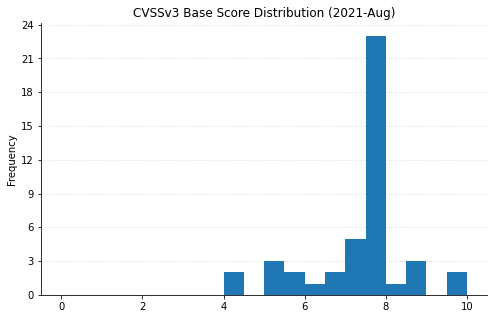
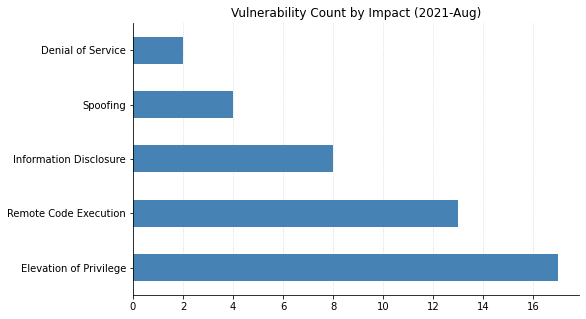
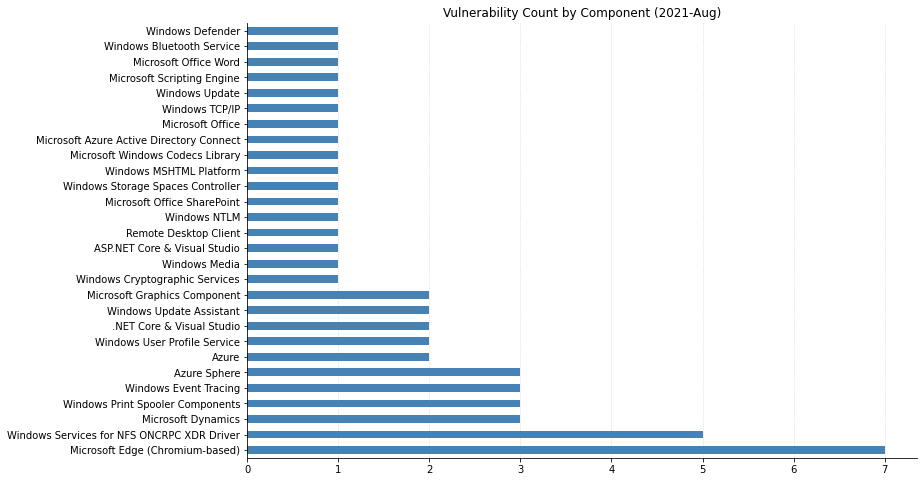
Summary Graphs
Summary Tables
Azure Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-36949 | Microsoft Azure Active Directory Connect Authentication Bypass Vulnerability | No | No | 7.1 | Yes |
| CVE-2021-26428 | Azure Sphere Information Disclosure Vulnerability | No | No | 4.4 | Yes |
| CVE-2021-26429 | Azure Sphere Elevation of Privilege Vulnerability | No | No | 7.7 | Yes |
| CVE-2021-26430 | Azure Sphere Denial of Service Vulnerability | No | No | 6 | Yes |
| CVE-2021-33762 | Azure CycleCloud Elevation of Privilege Vulnerability | No | No | 7 | No |
| CVE-2021-36943 | Azure CycleCloud Elevation of Privilege Vulnerability | No | No | 4 | No |
Browser Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-30597 | Chromium: CVE-2021-30597 Use after free in Browser UI | No | No | | Yes |
| CVE-2021-30596 | Chromium: CVE-2021-30596 Incorrect security UI in Navigation | No | No | | Yes |
| CVE-2021-30594 | Chromium: CVE-2021-30594 Use after free in Page Info UI | No | No | | Yes |
| CVE-2021-30593 | Chromium: CVE-2021-30593 Out of bounds read in Tab Strip | No | No | | Yes |
| CVE-2021-30592 | Chromium: CVE-2021-30592 Out of bounds write in Tab Groups | No | No | | Yes |
| CVE-2021-30591 | Chromium: CVE-2021-30591 Use after free in File System API | No | No | | Yes |
| CVE-2021-30590 | Chromium: CVE-2021-30590 Heap buffer overflow in Bookmarks | No | No | | Yes |
Developer Tools Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-34532 | ASP.NET Core and Visual Studio Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2021-34485 | .NET Core and Visual Studio Information Disclosure Vulnerability | No | No | 5 | Yes |
| CVE-2021-26423 | .NET Core and Visual Studio Denial of Service Vulnerability | No | No | 7.5 | No |
Microsoft Dynamics Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-36946 | Microsoft Dynamics Business Central Cross-site Scripting Vulnerability | No | No | 5.4 | No |
| CVE-2021-34524 | Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability | No | No | 8.1 | No |
| CVE-2021-36950 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4 | No |
Microsoft Office Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-36941 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2021-36940 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 7.6 | No |
| CVE-2021-34478 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
System Center Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-34471 | Microsoft Windows Defender Elevation of Privilege Vulnerability | No | No | 7.8 | Yes |
Windows Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-26426 | Windows User Account Profile Picture Elevation of Privilege Vulnerability | No | No | 7 | No |
| CVE-2021-36948 | Windows Update Medic Service Elevation of Privilege Vulnerability | Yes | No | 7.8 | No |
| CVE-2021-26432 | Windows Services for NFS ONCRPC XDR Driver Remote Code Execution Vulnerability | No | No | 9.8 | No |
| CVE-2021-26433 | Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability | No | No | 7.5 | Yes |
| CVE-2021-36926 | Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability | No | No | 7.5 | Yes |
| CVE-2021-36932 | Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability | No | No | 7.5 | Yes |
| CVE-2021-36933 | Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability | No | No | 7.5 | Yes |
| CVE-2021-26431 | Windows Recovery Environment Agent Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-34534 | Windows MSHTML Platform Remote Code Execution Vulnerability | No | No | 6.8 | Yes |
| CVE-2021-34530 | Windows Graphics Component Remote Code Execution Vulnerability | No | No | 7.8 | No |
| CVE-2021-34486 | Windows Event Tracing Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-34487 | Windows Event Tracing Elevation of Privilege Vulnerability | No | No | 7 | No |
| CVE-2021-36938 | Windows Cryptographic Primitives Library Information Disclosure Vulnerability | No | No | 5.5 | No |
| CVE-2021-36945 | Windows 10 Update Assistant Elevation of Privilege Vulnerability | No | No | 7.3 | No |
| CVE-2021-34536 | Storage Spaces Controller Elevation of Privilege Vulnerability | No | No | 7.8 | No |
Windows ESU Vulnerabilities
| CVE | Title | Exploited | Disclosed | CVSS3 | FAQ |
|---|
| CVE-2021-34484 | Windows User Profile Service Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-26424 | Windows TCP/IP Remote Code Execution Vulnerability | No | No | 9.9 | Yes |
| CVE-2021-36936 | Windows Print Spooler Remote Code Execution Vulnerability | No | Yes | 8.8 | No |
| CVE-2021-36947 | Windows Print Spooler Remote Code Execution Vulnerability | No | No | 8.8 | No |
| CVE-2021-34483 | Windows Print Spooler Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-36937 | Windows Media MPEG-4 Video Decoder Remote Code Execution Vulnerability | No | No | 7.8 | No |
| CVE-2021-36942 | Windows LSA Spoofing Vulnerability | No | Yes | 7.5 | Yes |
| CVE-2021-34533 | Windows Graphics Component Font Parsing Remote Code Execution Vulnerability | No | No | 7.8 | No |
| CVE-2021-26425 | Windows Event Tracing Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-36927 | Windows Digital TV Tuner device registration application Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-34537 | Windows Bluetooth Driver Elevation of Privilege Vulnerability | No | No | 7.8 | Yes |
| CVE-2021-34480 | Scripting Engine Memory Corruption Vulnerability | No | No | 6.8 | Yes |
| CVE-2021-34535 | Remote Desktop Client Remote Code Execution Vulnerability | No | No | 8.8 | Yes |