See the Updates section at the end of this post for new information as it comes to light.
Whether you attended virtually, IRL, or not at all, Black Hat and DEF CON have officially wrapped, and security folks’ brains are replete with fresh information on new (and some not-so-new) vulnerabilities and exploit chains. The “hacker summer camp” conferences frequently also highlight attack surface area that may not be net-new — but that is subjected to renewed and redoubled community interest coming out of Vegas week. See Rapid7’s summaries here and here.
Here’s the specific attack surface area and a few of the exploit chains we’re keeping our eye on right now:
- Orange Tsai stole the show (as always) at Black Hat with a talk on fresh Microsoft Exchange attack surface area. All in all, Orange discussed CVEs from what appears to be four separate attack chains —including the ProxyLogon exploit chain that made headlines when it hit exposed Exchange servers as a zero-day attack back in March and the “ProxyShell” exploit chain, which debuted at Pwn2Own and targets three now-patched CVEs in Exchange. Exchange continues to be a critically important attack surface area, and defenders should keep patched on a top-priority or zero-day basis wherever possible.
- Print spooler vulnerabilities continue to cause nightmares. DEF CON saw the release of new privilege escalation exploits for Windows Print Spooler, and Black Hat featured a talk by Sangfor Technologies researchers that chronicled both new Windows Print Spooler vulnerabilities and past patch bypasses for vulns like CVE-2020-1048 (whose patch was bypassed three times). Given that many defenders are still trying to remediate the “PrintNightmare” vulnerability from several weeks ago, it’s fair to say that Windows Print Spooler will remain an important attack surface area to prioritize in future Patch Tuesdays.
- There’s also a new vulnerability in Pulse Connect Secure VPNs that caught our attention — the vuln is actually a bypass for CVE-2020-8260, which came out last fall and evidently didn’t completely fade away — despite the fact that it’s authenticated and requires admin access. With CISA’s warnings about APT attacks against Pulse Connect Secure devices, it’s probably wise to patch CVE-2021-22937 quickly.
- And finally, the SpecterOps crew gave a highly anticipated Black Hat talk on several new attack techniques that abuse Active Directory Certificate Services — something we covered previously in our summary of the PetitPotam attack chain. This is neat research for red teams, and it may well show up on blue teams’ pentest reports.
Microsoft Exchange ProxyShell chain
Patches: Available
Threat status: Possible threat (at least one report of exploitation in the wild)
It goes without saying that Microsoft Exchange is a high-value, popular attack surface that gets constant attention from threat actors and researchers alike. That attention is increasing yet again after prominent security researcher Orange Tsai gave a talk at Black Hat USA last week revealing details on an attack chain first demonstrated at Pwn2Own. The chain, dubbed “ProxyShell,” allows an attacker to take over an unpatched Exchange server. ProxyShell is similar to ProxyLogon (i.e., CVE-2021-26855 and CVE-2021-27065), which continues to be popular in targeted attacks and opportunistic scans despite the fact that it was patched in March 2021.
Two of the three vulnerabilities used for ProxyShell were patched in April by Microsoft and the third was patched in July. As of August 9, 2021, private exploits have already been developed, and it’s probably only a matter of time before public exploit code is released, which may allow for broader exploitation of the vulns in this attack chain (in spite of its complexity!). Rapid7 estimates that there are, at least, nearly 75,000 ProxyShell-vulnerable exchange servers online:
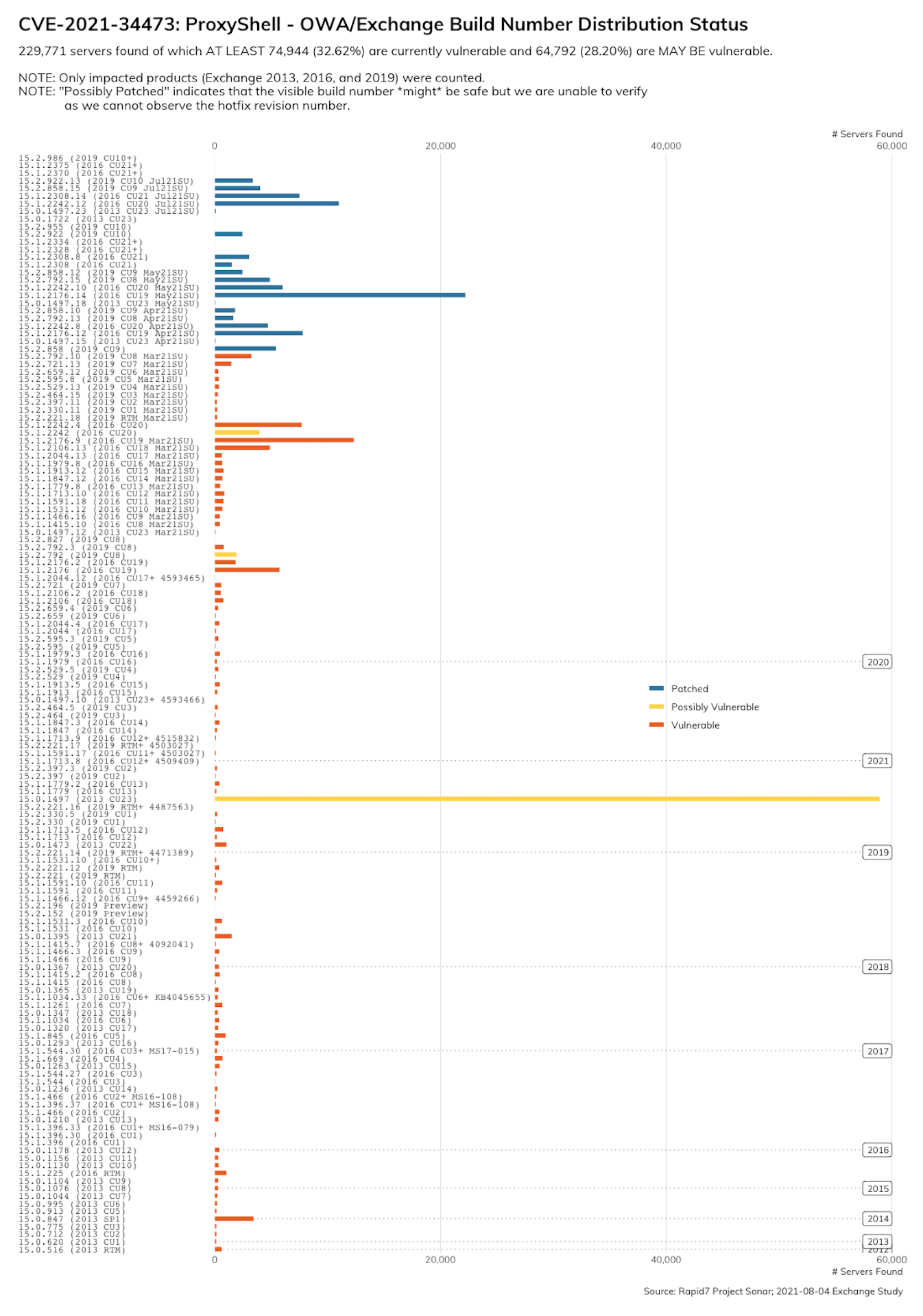
We strongly recommend that Exchange admins confirm that updates have been applied appropriately; if you haven’t patched yet, you should do so immediately on an emergency basis.
One gotcha when it comes to Exchange administration is that Microsoft only releases security fixes for the most recent Cumulative Update versions, so it’s vital to stay up to date with these quarterly releases in order to react quickly when new patches are published.
ProxyShell CVEs:
Windows Print Spooler — and more printer woes
Patches: Varies by CVE, mostly available
Threat status: Varies by CVE, active and impending
The Windows Print Spooler was the subject of renewed attention after the premature disclosure of the PrintNightmare vulnerability earlier this summer, followed by new Black Hat and DEF CON talks last week. Among the CVEs discussed were a quartet of 2020 vulns (three of which were bypasses descended from CVE-2020-1048, which has been exploited in the wild since last year), three new remote code execution vulnerabilities arising from memory corruption flaws, and two new local privilege escalation vulnerabilities highlighted by researcher Jacob Baines. Of this last group, one vulnerability — CVE-2021-38085 — remains unpatched.
On August 11, 2021, Microsoft assigned CVE-2021-36958 to the latest Print Spooler remote code execution vulnerability which appears to require local system access and user interaction. Further details are limited at this time. However, as mitigation, Microsoft is continuing to recommend stopping and disabling the Print Spooler service. Even after this latest zero-day vulnerability is patched, we strongly recommend leaving the Print Spooler service disabled wherever possible. Read Rapid7’s blog on PrintNightmare for further details and updates.
Windows Print Spooler and related CVEs:
- CVE-2020-1048 (elevation of privilege vuln in Windows Print Spooler presented at Black Hat 2020; exploited in the wild, Metasploit module available)
- CVE-2020-1337 (patch bypass for CVE-2020-1048; Metasploit module available)
- CVE-2020-17001 (patch bypass variant for CVE-2020-1048)
- CVE-2020-17014 (patch bypass variant for CVE-2020-1048)
- CVE-2020-1300 (local privilege escalation technique known as “EvilPrinter” presented at DEF CON 2020)
- CVE-2021-24088 (new remote code execution vulnerability in the Windows local spooler, as presented at Black Hat 2021)
- CVE-2021-24077 (new remote code execution vulnerability in the Windows Fax Service, as presented at Black Hat 2021)
- CVE-2021-1722 (new remote code execution vulnerability in the Windows Fax Service, as presented at Black Hat 2021)
- CVE-2021-1675 (elevation of privilege vuln in Windows Print Spooler patched in June 2021)
- CVE-2021-34527, aka “PrintNightmare”
- CVE-2021-35449 (print driver local privilege escalation vulnerability, as presented at DEF CON 2021; Metasploit module in progress)
- CVE-2021-38085 (unpatched print driver local privilege escalation vulnerability, as presented at DEF CON 2021; Metasploit module in progress)
- CVE-2021-36958 (unpatched remote code execution vulnerability; announced August 11, 2021)
Currently, both PrintNightmare CVE-2021-34527 and CVE-2020-1048 are known to be exploited in the wild. As the list above demonstrates, patching print spooler and related vulns quickly and completely has been a challenge for Microsoft for the past year or so. The multi-step mitigations required for some vulnerabilities also give attackers an advantage. Defenders should harden printer setups wherever possible, including against malicious driver installation.
Pulse Connect Secure CVE-2021-22937
Patch: Available
Threat status: Impending (Exploitation expected soon)
On Monday, August 2, 2021, Ivanti published Security Advisory SA44858 which, among other fixes, includes a fix for CVE-2021-22937 for Pulse Connect Secure VPN Appliances running 9.1R11 or prior. Successful exploitation of this vulnerability, which carries a CVSSv3 score of 9.1, requires the use of an authenticated administrator account to achieve remote code execution (RCE) as user root.
Public proof-of-concept (PoC) exploit code has not been released as of this writing. However, this vulnerability is simply a workaround for CVE-2020-8260, an authentication bypass vulnerability that was heavily utilized by attackers, released in October 2020.
The Cybersecurity and Infrastructure Security Agency (CISA) has been monitoring the Exploitation of Pulse Connect Secure Vulnerabilities demonstrating that attackers have been targeting Ivanti Pulse Connect Secure products for over a year. Due to attacker focus on Pulse Connect Secure products, and especially last year’s CVE-2020-8260, Rapid7 recommends patching CVE-2021-22937 as soon as possible.
PetitPotam: Windows domain compromise
Patches: Available
Threat status: Threat (Exploited in the wild)
In July 2021, security researcher Topotam published a PoC implementation of a novel NTLM relay attack christened “PetitPotam.” The technique used in the PoC allows a remote, unauthenticated attacker to completely take over a Windows domain with the Active Directory Certificate Service (AD CS) running — including domain controllers. Rapid7 researchers have tested public PoC code against a Windows domain controller setup and confirmed exploitability. One of our senior researchers summed it up with: "This attack is too easy." You can read Rapid7’s full blog post here.
On August 10, 2021, Microsoft released a patch that addresses the PetitPotam NTLM relay attack vector in today's Patch Tuesday. Tracked as CVE-2021-36942, the August 2021 Patch Tuesday security update blocks the affected API calls OpenEncryptedFileRawA and OpenEncryptedFileRawW through the LSARPC interface. Windows administrators should prioritize patching domain controllers and will still need to take additional steps listed in KB5005413 to ensure their systems are fully mitigated.
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to the vulnerabilities in this post with authenticated vulnerability checks. Please note that details haven’t yet been released on CVE-2021-38085 and CVE-2021-36958; therefore, it’s still awaiting analysis and check development.
Updates
Pulse Connect Secure CVE-2021-22937
On August 24, 2021, the Cybersecurity & Infrastructure Security Agency (CISA) released Malware Analysis Report (AR21-236E) which includes indicators of compromise (IOCs) to assist with Pulse Connect Secure investigations.
Exchange’s ProxyToken
On August 30, 2021, details surrounding another Exchange vulnerability, “ProxyToken” CVE-2021-33766 became known. Like the recent Exchange vulnerabilities, Microsoft patched CVE-2021-33766 in April 2021, but the corresponding advisory was not published until July 2021.
ProxyToken takes advantage of a flaw in how Exchange authenticates requests across the frontend and backend portions of Exchange and allows an unauthenticated attacker to make configuration changes to other user’s email accounts which could impact the confidentiality of accounts. (Changes might include, but are not limited to, the copying and forwarding of the user’s email which would be useful for spearfishing campaigns and data exfiltration).
Rapid7 continues to emphasize the importance of ensuring Exchange servers are kept up to date with a truly short period between patch-release and patch-deployment and not allowing Exchange access from the public internet.
InsightVM customers have been able to detect whether this patch has been applied since the fix was published in April 2021.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe