This attack is ongoing. See the Updates section at the end of this post for new information as it comes to light. Rapid7 also has a technical analysis of the ProxyShell exploit chain in AttackerKB.
On August 5, 2021, in a Black Hat USA talk, DEVCORE researcher Orange Tsai shared information on several exploit chains targeting on-premises installations of Microsoft Exchange Server. Among the exploit chains presented were ProxyLogon, which was exploited en masse in February and March of 2021, and ProxyShell, an attack chain originally demonstrated at the Pwn2Own hacking competition this past April. As of August 12, 2021, multiple researchers have detected widespread opportunistic scanning and exploitation of Exchange servers using the ProxyShell chain.
According to Orange Tsai's demonstration, the ProxyShell exploit chain allows a remote unauthenticated attacker to execute arbitrary commands on a vulnerable on-premises instance of Microsoft Exchange Server via port 443. The exploit is comprised of three discrete CVEs:
- CVE-2021-34473, a remote code execution vulnerability patched April 13, 2021
- CVE-2021-34523, an elevation of privilege vulnerability patched April 13, 2021
- CVE-2021-31207, a security feature bypass patched May 11, 2021
While CVE-2021-34473 and CVE-2021-34523 were patched in April, Microsoft’s advisories note that they were inadvertently omitted from publication until July.
When chained, these vulnerabilities allow the attacker to bypass ACL controls, send a request to a PowerShell back-end, and elevate privileges, effectively authenticating the attacker and allowing for remote code execution. Both public and private proof-of-concept exploits have been released as of August 18, 2021—not surprising, since ProxyShell was first demonstrated more than four months ago at Pwn2Own. A number of technical analyses of the chain have also been published. See Rapid7's exploit chain analysis in AttackerKB.
Notably, there has been confusion about which CVE is which across various advisories and research descriptions — Microsoft, for instance, describes CVE-2021-34473 as a remote code execution vulnerability, but Orange Tsai’s Black Hat slides list CVE-2021-34473 as the initial ACL bypass. Community researchers have also expressed confusion over CVE numbering across the ProxyShell chain, but ultimately, the takeaway is the same: Organizations that have not patched these vulnerabilities should do so on an emergency basis and invoke incident response protocols to look for indicators of compromise.
Affected products
The following versions of Exchange Server are vulnerable to all three ProxyShell CVEs:
- Microsoft Exchange Server 2019 Cumulative Update 9
- Microsoft Exchange Server 2019 Cumulative Update 8
- Microsoft Exchange Server 2016 Cumulative Update 20
- Microsoft Exchange Server 2016 Cumulative Update 19
- Microsoft Exchange Server 2013 Cumulative Update 23
Organizations that rely on on-premises installations of Exchange Server and are not able to move to O365 should ensure that all Exchange instances are patched on a zero-day basis. In order to do this, it is vital that defenders keep up-to-date with quarterly Cumulative Updates, since Microsoft only releases security fixes for the most recent Cumulative Update versions.
While ProxyShell and March’s ProxyLogon exploit chain are the two attacks that have already resulted in widespread exploitation, they are not the only exploit chains targeting on-premises Exchange servers. Exchange continues to be valuable and accessible attack surface area for both sophisticated and run-of-the-mill threat actors, and we will certainly see additional widespread exploitation in the future.
Read more from our emergent threat response team on high-priority attack surface area, including Windows Print Spooler and Pulse Connect Secure VPNs.
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to all three ProxyShell CVEs with authenticated vulnerability checks.
The following attacker behavior detection is available InsightIDR customers:
- Suspicious Process - Process Spawned By Outlook Web Access
This detection will identify processes spawned by Microsoft IIS processes that have been configured to serve as Outlook Web Access web servers for Microsoft Exchange. Rogue processes being spawned may be an indication of a successful attack against these systems and has been observed targeted by various malicious actors.
If this detection fires in your environment, you should determine whether it is part of authorized administrator activity. Examine the parent process that spawned the command, and anything else that process may have spawned. If this activity is not benign or expected, consider rebuilding the host from a known, good source and having any possibly affected users change their passwords.
Updates
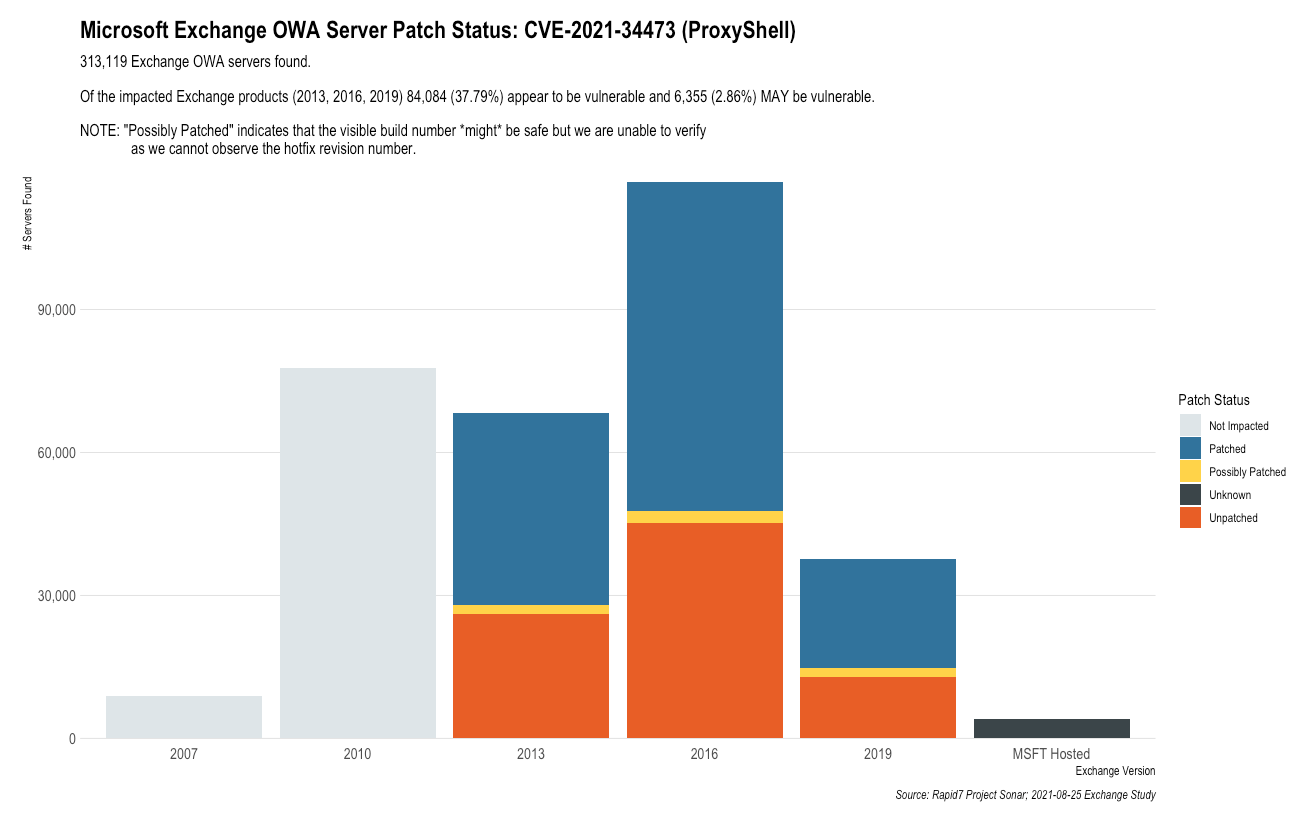
August 25, 2021: Rapid7 estimates that there are over 84,000 Exchange servers that appear vulnerable to the ProxyShell attack chain.
August 23, 2021: Multiple sources have now reported that at least one ransomware gang (LockFile) is chaining ProxyShell with PetitPotam (CVE-2021-36942) to compromise Windows domain controllers. See Rapid7's blog on PetitPotam for patching and additional required mitigation advice.
August 21, 2021: Rapid7's Managed Detection and Response (MDR) and Incident Response (IR) teams have noted a significant uptick in Exchange exploitation by multiple threat actors. Community researchers have also noted that attackers are exploiting the ProxyShell vulnerabilities to drop webshells and spread ransomware on vulnerable targets.
We are monitoring for additional attacker behavior and will update this blog as further information comes to light.
August 16, 2021: We have begun to see public proof-of-concept (PoC) code implementing the ProxyShell exploit chain. Exploitation is ongoing.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
