See the Updates section at the end of this post for new information as it comes to light, including reports of exploitation.
Description
On Tuesday, September 21, 2021, VMware published security advisory VMSA-2021-0020, which includes details on CVE-2021-22005, a critical file upload vulnerability (CVSSv3 9.8) in vCenter Server that allows remote code execution (RCE) on the appliance. Successful exploitation of this vulnerability is achieved simply by uploading a specially crafted file via port 443 “regardless of the configuration settings of vCenter Server.”
VMware has published an FAQ outlining the details of this vulnerability and makes it clear that this should be patched “immediately.” A workaround is also being provided by VMware — however, its use is not being recommended and should only be used as a temporary solution.
You can find Rapid7's vulnerability analysis on AttackerKB which contains a root cause analysis and full RCE information.
Affected products
- vCenter Server versions 6.7 and 7.0
- Cloud Foundation (vCenter Server) 3.x, 4.x
Guidance
We echo VMware’s advice that impacted servers should be patched right away. While there are currently no reports of exploitation, we expect this to quickly change within days — just as previous critical vCenter vulnerabilities did (CVE-2021-21985, CVE-2021-21972). Additionally, Rapid7 recommends that, as a general practice, network access to critical organizational infrastructure only be allowed via VPN and never open to the public internet.
We will update this post as more information becomes available, such as information on exploitation.
Rapid7 customers
A vulnerability check for CVE-2021-22005 is under development and will be available to InsightVM and Nexpose customers in an upcoming content release pending the QA process.
In the meantime, InsightVM customers can use Query Builder to find assets that have vCenter Server installed by creating the following query: software.description contains vCenter Server. Rapid7 Nexpose customers can create a Dynamic Asset Group based on a filtered asset search for Software name contains vCenter Server.
Updates
[September 22, 2021]
An InsightVM and Nexpose vulnerability check for CVE-2021-22005 is scheduled to be released on the afternoon (EST) of September 22, 2021.
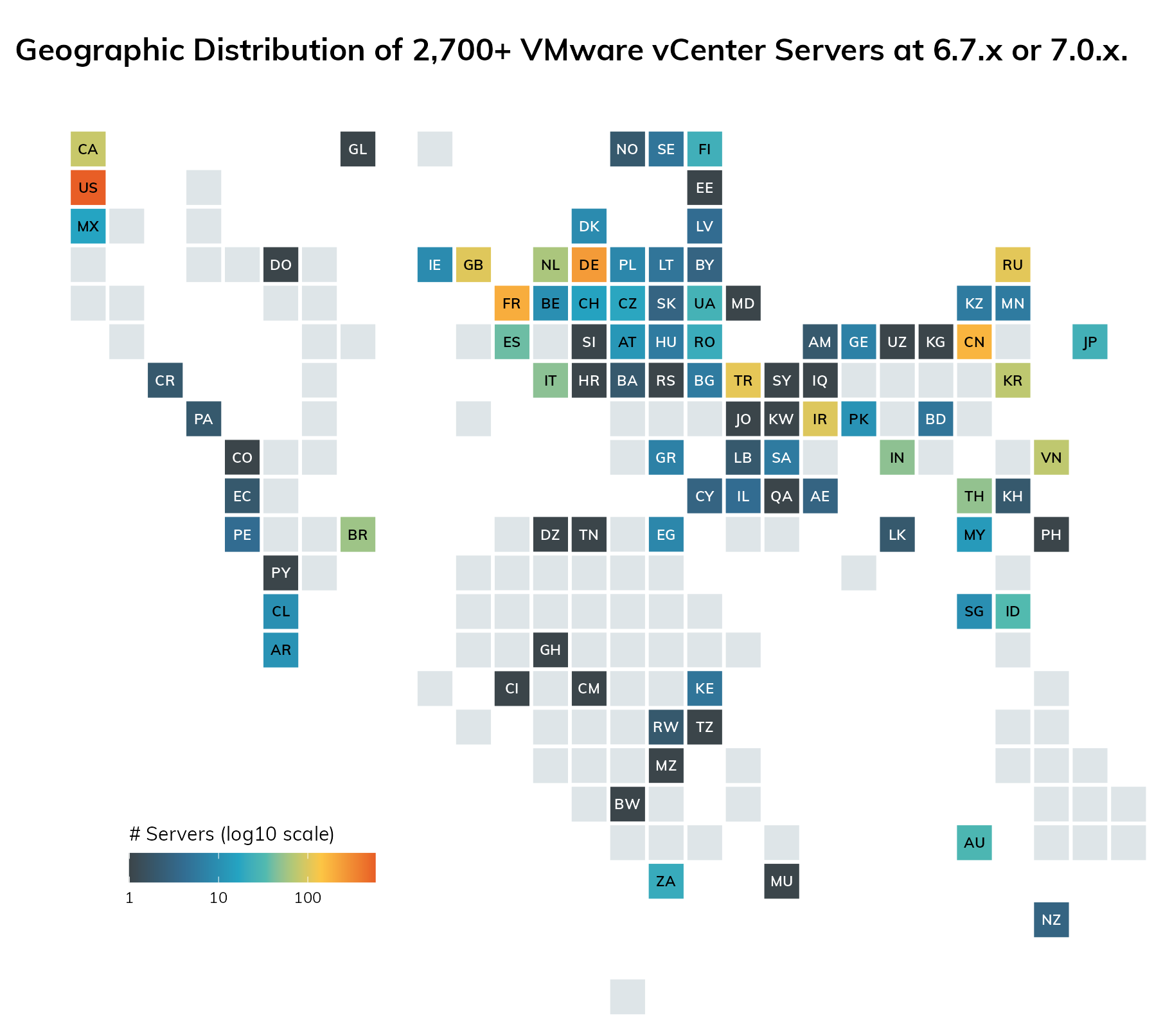
Rapid7 Labs estimates there are over 2,700 vulnerable vCenter servers exposed to the public internet. This represents only a fraction of vulnerable servers, however, as attackers with existing network ingress will be tempted to utilize that access to take advantage of this vulnerability.
[September 23, 2021]
CVE-2021-22005 authenticated checks for InsightVM and Nexpose are available in content update 3594982882, released on September 23, 2021.
[September 24, 2021]
CVE-2021-22005 is now being exploited in the wild.
[September 29, 2021]
Updated description to include a link to the Rapid7 analysis on AttackerKB
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe