| CVE | Vendor Advisory | AttackerKB | IVM Content | Patching Urgency | Last Update |
|---|---|---|---|---|---|
| CVE-2021-41773, CVE-2021-42013 | Apache Advisory | AttackerKB | Available | ASAP | October 12, 2021 15:00 ET |
See the Updates section at the end of this post for information on developments that occurred after initial publication.
On Monday, October 4, 2021, Apache published an advisory on CVE-2021-41773, an unauthenticated remote file disclosure vulnerability in HTTP Server version 2.4.49 and 2.4.50 (see the Updates section for more on 2.4.50). The vulnerability arises from the mishandling of URL-encoded path traversal characters in the HTTP GET request. Public proof-of-concept exploit code is widely available, and Apache and others have noted that this vulnerability is being exploited in the wild. Note that a non-default configuration is required for exploitability.
While the original advisory indicated that CVE-2021-41773 was merely an information disclosure bug, both Rapid7 and community researchers have verified that the vulnerability can be used for remote code execution when mod_cgi is enabled. While mod_cgi is not enabled in the default Apache Server HTTP configuration, it’s also not an uncommon feature to enable. With mod_cgi enabled, an attacker can execute arbitrary programs via HTTP POST requests. The initial RCE proof of concept resulted in blind command execution, and there have been multiple proofs of concept that coerce the HTTP server into sending the program’s output back to the attacker. Rapid7’s research team has a full root cause analysis of CVE-2021-41773 here along with proofs of concept.
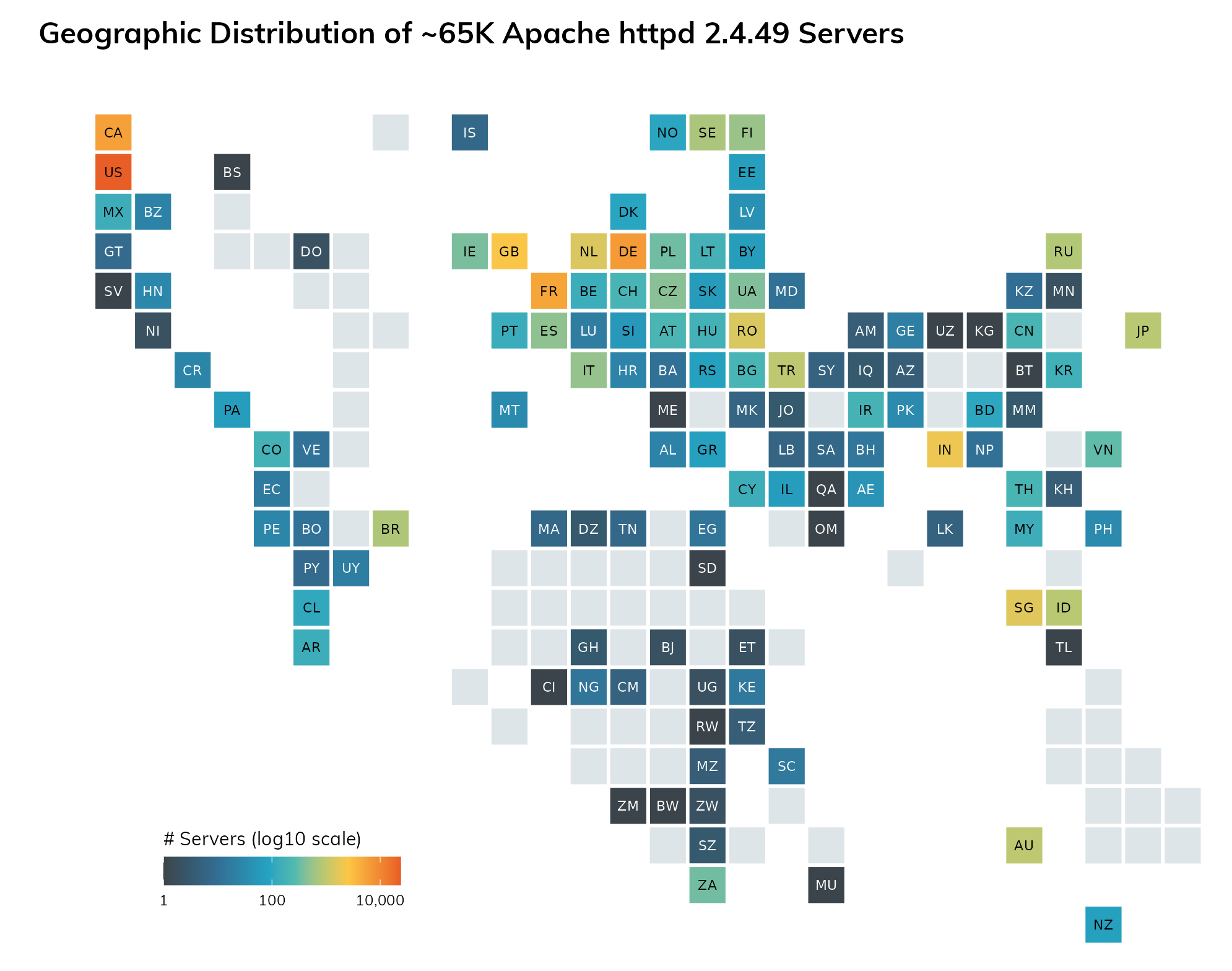
Rapid7 Labs has identified roughly 65,000 potentially vulnerable versions of Apache httpd exposed to the public internet. Our exposure estimate intentionally does not count multiple Apache servers on the same IP as different instances (this would substantially increase the number of exposed instances identified as vulnerable).
Mitigation guidance
Organizations that are using Apache HTTP Server 2.4.49 or 2.4.50 should determine whether they are using vulnerable configurations. If a vulnerable server is discovered, the server’s configuration file should be updated to include the filesystem directory directive with require all denied:
<Directory />
Require all denied
</Directory>
Apache HTTP Server users should update to 2.4.51 or later as soon as is practical. Updating to HTTP Server 2.4.51 remediates both CVE-2021-41773 and CVE-2021-42013. For more information, see Apache’s advisory here.
Rapid7 customers
A remote vulnerability check for CVE-2021-41773 was released to InsightVM and Nexpose customers in the October 6, 2021 content update.
A remote vulnerability check for CVE-2021-42013 was released to InsightVM and Nexpose customers in the October 7, 2021 content update.
Updates
October 7, 2021: Apache has updated their advisory to note that the patch for CVE-2021-41773 was incomplete, rendering HTTP Server 2.4.50 versions vulnerable when specific, non-default conditions are met. According to their advisory, "an attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives. If files outside of these directories are not protected by the usual default configuration require all denied, these requests can succeed. If CGI scripts are also enabled for these aliased pathes, this could allow for remote code execution."
CVE-2021-42013 has been assigned to track the incomplete fix for CVE-2021-41773. CVE-2021-42013 has been fixed in HTTP Server version 2.4.51 released October 7, 2021. For more information, see Apache's advisory.
This issue only affects Apache 2.4.49 and Apache 2.4.50 and not earlier versions.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
