Threat intelligence is a critical part of an organization's cybersecurity strategy, but given how quickly the state of cybersecurity evolves, is the traditional model still relevant?
Whether you're a cybersecurity expert or someone who's looking to build a threat intelligence program from the ground up, this simple framework transforms the traditional model, so it can apply to the current landscape. It relies on the technologies available today and can be implemented in four simple steps.
A quick look at the threat intelligence framework
The framework we'll be referencing here is called the Intelligence Cycle, which breaks down into four phases:
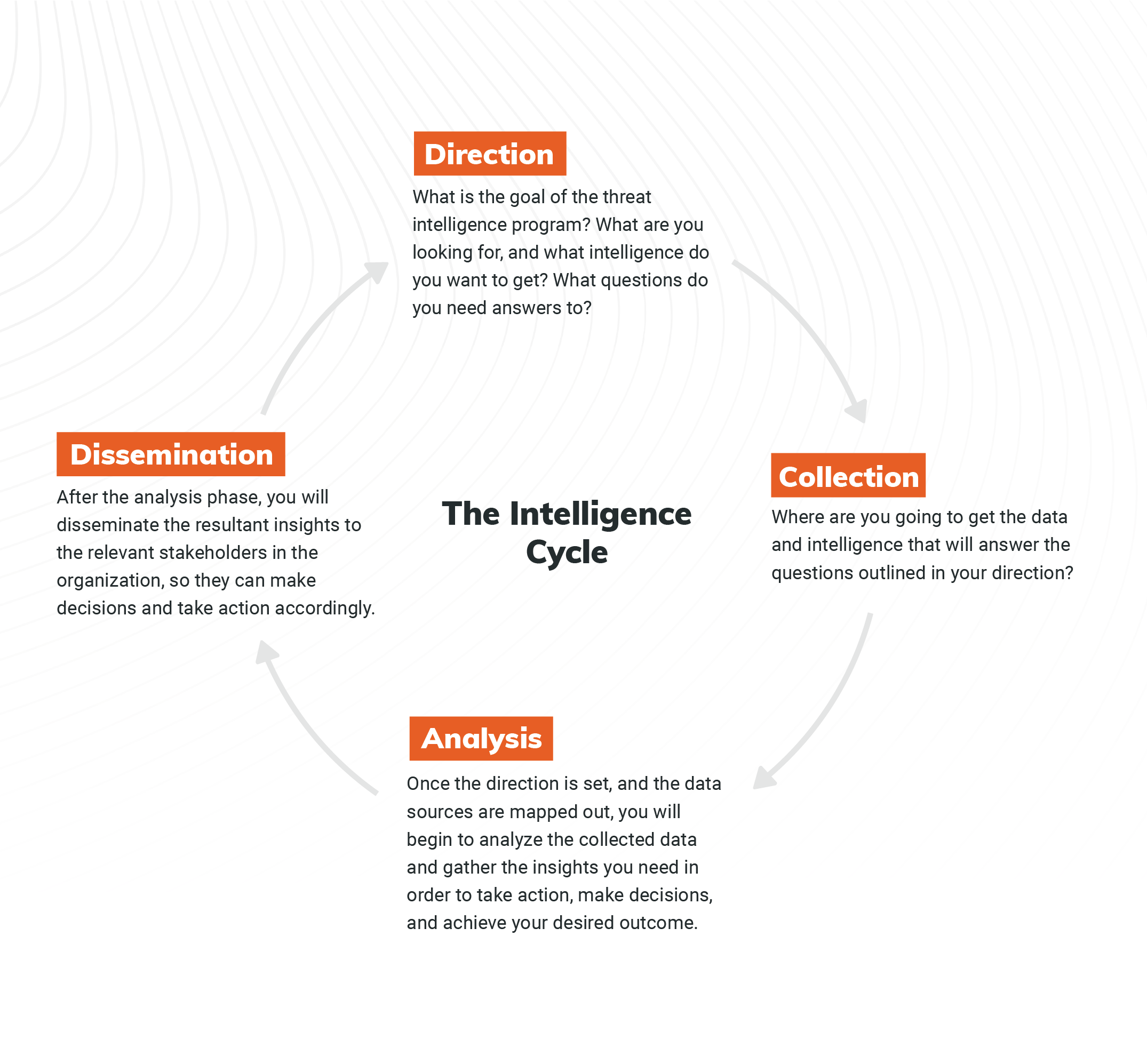
This is the traditional framework you can use to implement a threat intelligence program in your organization. Let's take a deeper look at each step, update them for the modern day, and outline how you can follow them in 2021.
To do this, we'll leverage a use case of credential leakage as an example, which is a very important use case today. According to Verizon's 2021 Data Breach Investigations Report, credentials remain one of the most sought-after data types, and it's this type of data that gets compromised the fastest. As such, credential leakage is an area organizations of all sizes should be aware of and familiar with, making it an optimal choice for illustrating how to build an effective threat intelligence program.
1. Set a direction
The first step in this process is to set the direction of your program, meaning you need to outline what you're looking for and what questions you want to ask and answer. To help with this, you can create Prioritized Intelligence Requirements, or PIRs, and a desired outcome.
For both your PIRs and desired outcome, you should aim to be as explicit as possible. In the case of credential leakage, for example, let's set our PIR as: “I want to identify any usernames and passwords belonging to my employees that have been exposed to an unauthorized entity."
We've selected these credentials for this example, because they are risky for the organization. Depending on your needs, you may identify different credentials with higher risk, but this is the type we're focusing on for this use case.
With this very specific PIR outlined, we can now determine a desired outcome, which would be something like: “I want to force password reset for any of these passwords that are being used in the corporate environment before threat actors can use them."
This is crucial, and later, we'll see how the desired outcome impacts how we build this threat intelligence program.
2. Map out what data to collect
Once you've set your PIRs and desired outcome, you need to map out the sources of intelligence that will serve the direction.
For this use case, let's identify how threat actors gain credentials. A few of the most common sources include:
- Endpoints (usually harvested by botnets)
- Third-party breaches
- Code repositories
- Posts on a forum/pastebin
- Dark web black markets that buy/sell credentials
In the past, you might have turned to individual vendors who could help you with each of these areas. For example, you may have worked with an organization that specializes in endpoint security and another that could tackle incident response management for third-party breaches. But today, you're better off finding a vendor who can support all the sources you need and provide complete coverage for all areas of risk, especially for something like credential leakage.
Regardless, by mapping out these sources, you can outline the areas you need to focus on for analysis.
3. Select your approach to analysis
Next up is analysis. You can take two approaches:
- Automated analysis: You can leverage AI or sophisticated algorithms that will classify relevant data into alerts of credential leakage, where the emails and passwords can be extracted and pulled out.
- Manual analysis: You can manually analyze the information by gathering all the data and having the analysts on your team review the data and decide what's relevant to your organization.
The biggest advantage of manual analysis is flexibility. You can put more human resources, intelligence, and insight into the process to surface only what is relevant. But there are also disadvantages — for example, this process is much slower than automated analysis.
In the first phase of our program, we specified that we want to force password resets before threat actors leverage them for a cyberattack. This means that speed is extremely crucial in this use case. Now, you can see how the desired outcome is helping us make a decision about the type of approach we should take for analysis.
Automated analysis also requires significantly fewer resources. You don't need a bunch of analysts to sort through the raw data and surface what is relevant. The classification and alerting of credential leakage is fully automated here. Plus, if threats are being automatically classified, they can likely be automatically remediated.
Let's take a look at this in practice: Say your algorithm finds an email and password mentioned on a forum. The AI can classify the incident and extract the relevant information (e.g., the email/username and password) in a machine-readable format. Then, a response can be automatically applied, like force resetting the password for the identified user.
As you can see, there are advantages and disadvantages for each approach. When you assess them against our desired outcome, it's clear that we should go with an automated approach for our credential leakage use case.
4. Disseminate analysis to take action
Finally, we come to the final phase: dissemination. Traditionally, when it comes to the intelligence cycle and the dissemination of threat intelligence, we talk about sending alerts and reports to the relevant stakeholders to review, so they can take action and respond accordingly.
But, as our example in the previous section shows, the future (and current state) of this process is fully automated remediation. With this in mind, we shouldn't just discuss how we distribute alerts and information in the organization — we should also think about how we can take the intelligence and distribute it to security devices to automatically prevent the upcoming attack.
For leaked credentials, this could mean sending the intelligence to the active directory to automatically force password reset without human intervention. This is a great example of how shifting to an automated solution can dramatically reduce the time to remediation.
Once again, let's go back to our PIR and desired outcome: We want to force the password reset before the threat actor uses the password. Speed is key here, so we should definitely automate the remediation. As such, we need a solution that takes the intelligence from the sources we've mapped out, automatically produces an alert with the information extracted, and then automatically remediates the threat to reduce risk as fast as possible.
A simplified and modernized approach to threat intelligence
In summary, this revamped Intelligence Cycle resembles how to build an effective threat intelligence program today.
Start by identifying your PIRs and desired outcome. Then, decide on a collection plan by outlining all sources that will drive the relevant intelligence. Next, for the vast majority of use cases, it's important to have an automated analysis algorithm in place to classify alerts quickly and precisely. And finally, you should transition from manual dissemination to automated remediation, which can dramatically reduce time to remediation — something that's more critical than ever due to the current state of cybersecurity.
By following these steps, you can build an effective threat intelligence program, and with this foundation in place, you can fine-tune it until you have a seamless process that saves your organization time and reduces risk across the board.
