| CVE | Vendor Advisory | AttackerKB | IVM Content | Patching Urgency | Last Update |
|---|---|---|---|---|---|
| CVE-2021-40438 | Apache Advisory | AttackerKB | 09/16/2021 (multiple) | ASAP | December 1, 2021 14:00 ET |
On September 16, 2021, Apache released version 2.4.49 of HTTP Server, which included a fix for CVE-2021-40438, a critical server-side request forgery (SSRF) vulnerability affecting Apache HTTP Server 2.4.48 and earlier versions. The vulnerability resides in mod_proxy and allows remote, unauthenticated attackers to force vulnerable HTTP servers to forward requests to arbitrary servers — giving them the ability to obtain or tamper with resources that would potentially otherwise be unavailable to them.
Since other vendors bundle HTTP Server in their products, we expect to see a continued trickle of downstream advisories as third-party software producers update their dependencies. Cisco, for example, has more than 20 products they are investigating as potentially affected by CVE-2021-40438, including a number of network infrastructure solutions and security boundary devices. To be exploitable, CVE-2021-40438 requires that mod_proxy be enabled. It carries a CVSSv3 score of 9.0.
Several sources have confirmed that they have seen exploit attempts of CVE-2021-40438 in the wild. As of November 30, 2021, there is no evidence yet of widespread attacks, but given httpd’s prevalence and typical exposure levels (and the fact that it’s commonly bundled across a wide ecosystem of products), it’s likely exploitation will continue — and potentially increase.
Rapid7's vulnerability research team has a detailed technical analysis of this vulnerability in AttackerKB, including a demo of how it can be exploited.
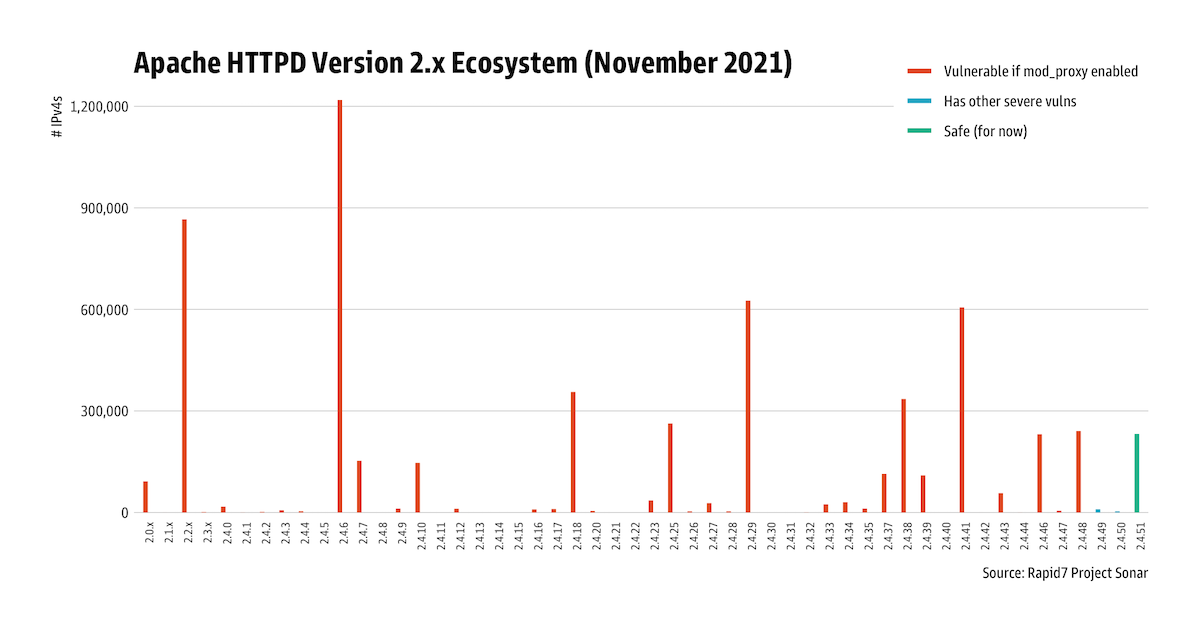
Affected versions
According to Apache’s advisory, all Apache HTTP Server versions up to 2.4.48 are vulnerable if mod_proxy is in use. CVE-2021-40438 is patched in Apache HTTP Server 2.4.49 and later.
Rapid7 Labs has observed over 4 million potentially vulnerable instances of Apache httpd 2.x:
Mitigation guidance
Apache HTTP Server versions 2.4.49 and 2.4.50 included other severe vulnerabilities that are known to be exploited in the wild, so Apache httpd customers should upgrade to the latest version (2.4.51 at time of writing) instead of upgrading incrementally.
We advise paying close attention particularly to firewall or other security boundary product advisories and prioritizing updates for those solutions. NVD’s entry for CVE-2021-40438 includes several downstream vendor advisories.
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to CVE-2021-40438 with both authenticated and unauthenticated vulnerability checks.
Updates
December 1, 2021: CISA has added CVE-2021-40438 to its list of Known Exploited Vulnerabilities and specified a remediation date of December 15, 2021 for federal agencies.
Download Rapid7's Annual Vulnerability Intelligence Report ▶︎
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
