It's been a long few days as organizations' security teams have worked to map, quantify, and mitigate the immense risk presented by the Log4Shell vulnerability within Log4j. As can be imagined, cybercriminals are working overtime as well, as they seek out ways to exploit this vulnerability.
The Rapid7 Threat Intelligence team is tracking the attacker's-eye view and the related chatter on the clear, deep, and dark web within our Threat Intelligence platform. Here are 4 observations based on what we've seen at the onset of the identification of CVE-2021-44228.
1. We see a spike in hacker chatter and security researchers' publications about Log4j.
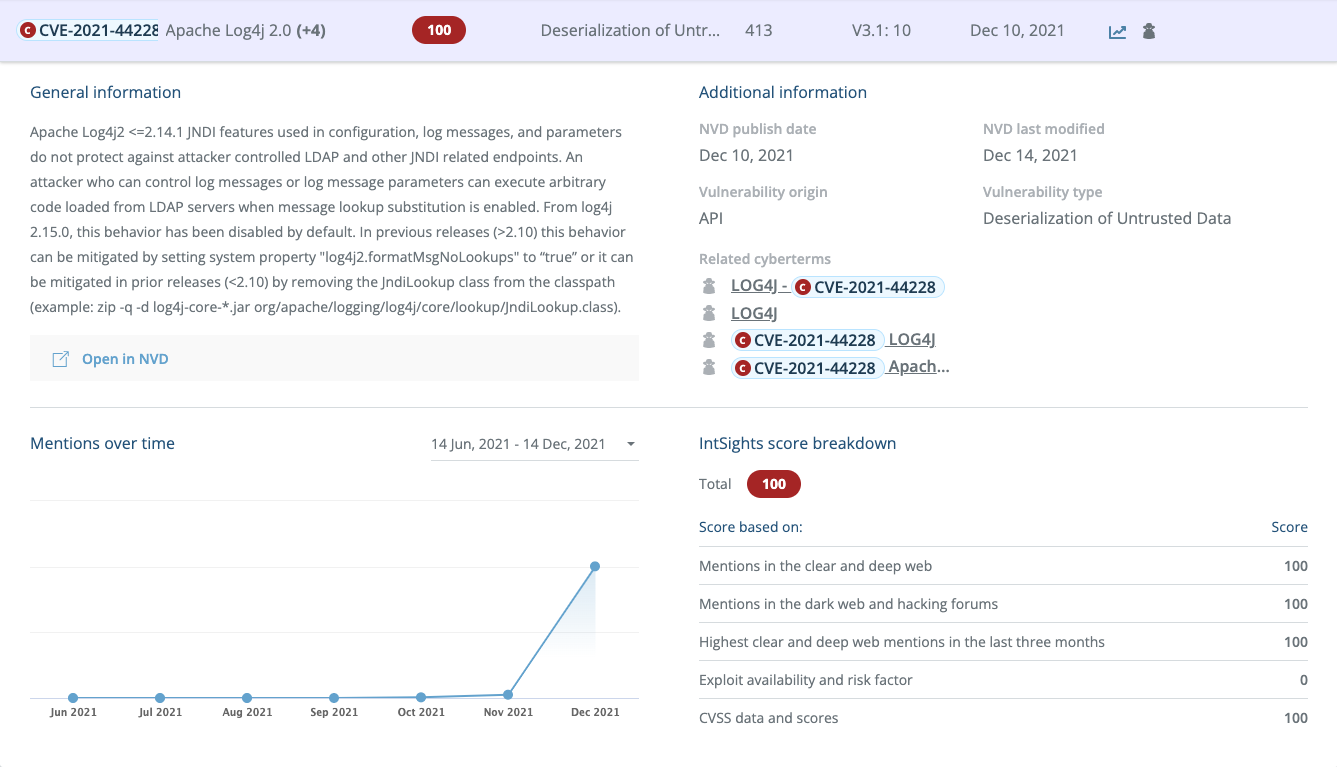
Increased hacker chatter is a key indicator of an emerging threat that security teams must account for. Clearly the spike here is no surprise – however, it is important to monitor and understand the types and scope of the chatter in order to get a clear picture of what's on the horizon.
2. Hackers – specifically from the Russian, Chinese, and Turkish communities – show interest in the vulnerability and are actively sharing scanners and exploits.
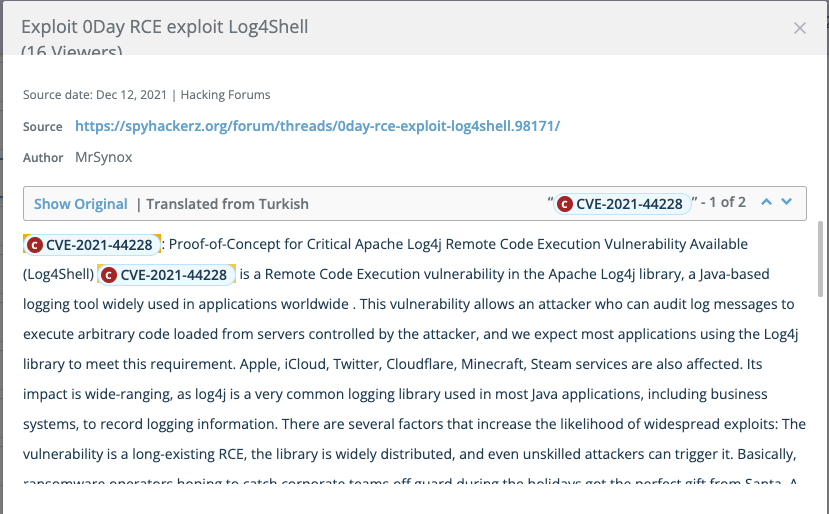
The following two screenshots show that bad actors have already developed and shared proof of concepts exploiting the vulnerability in Log4j. They also show the extent to which this vulnerability impacts user communities such as PC gamers, social media users, Apple/iCloud customers, and more.
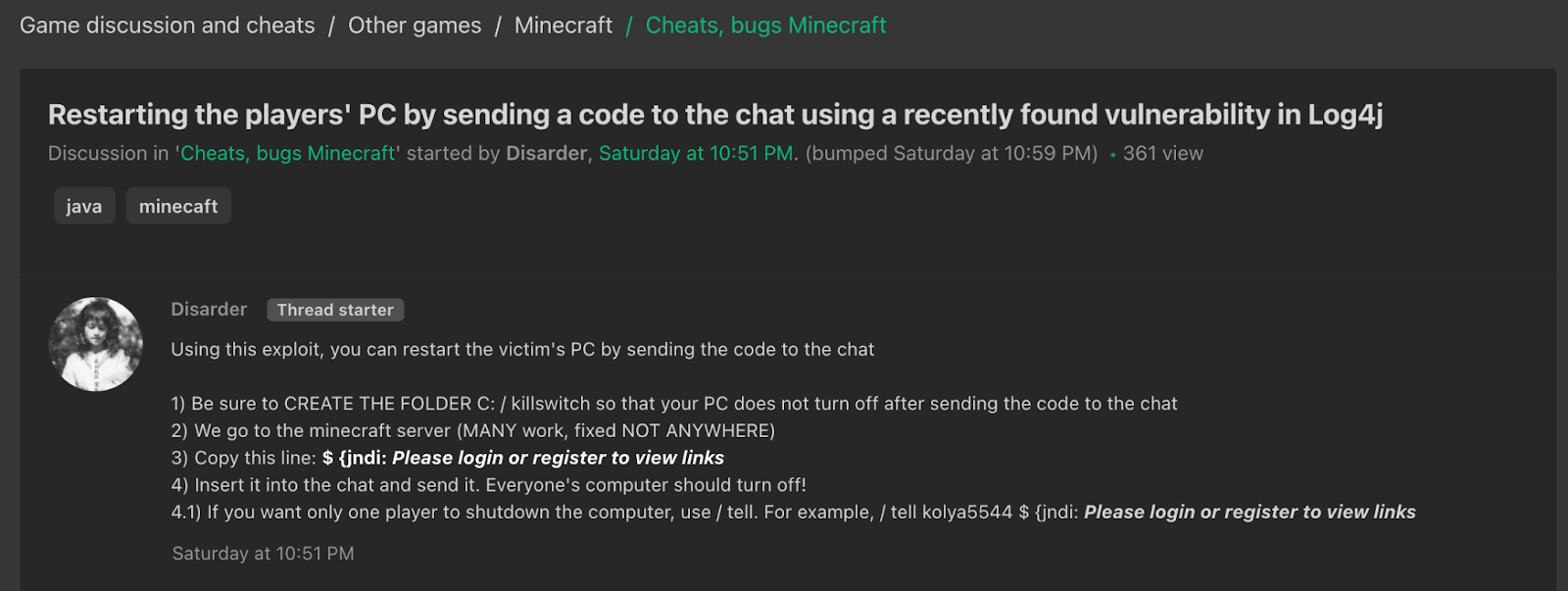
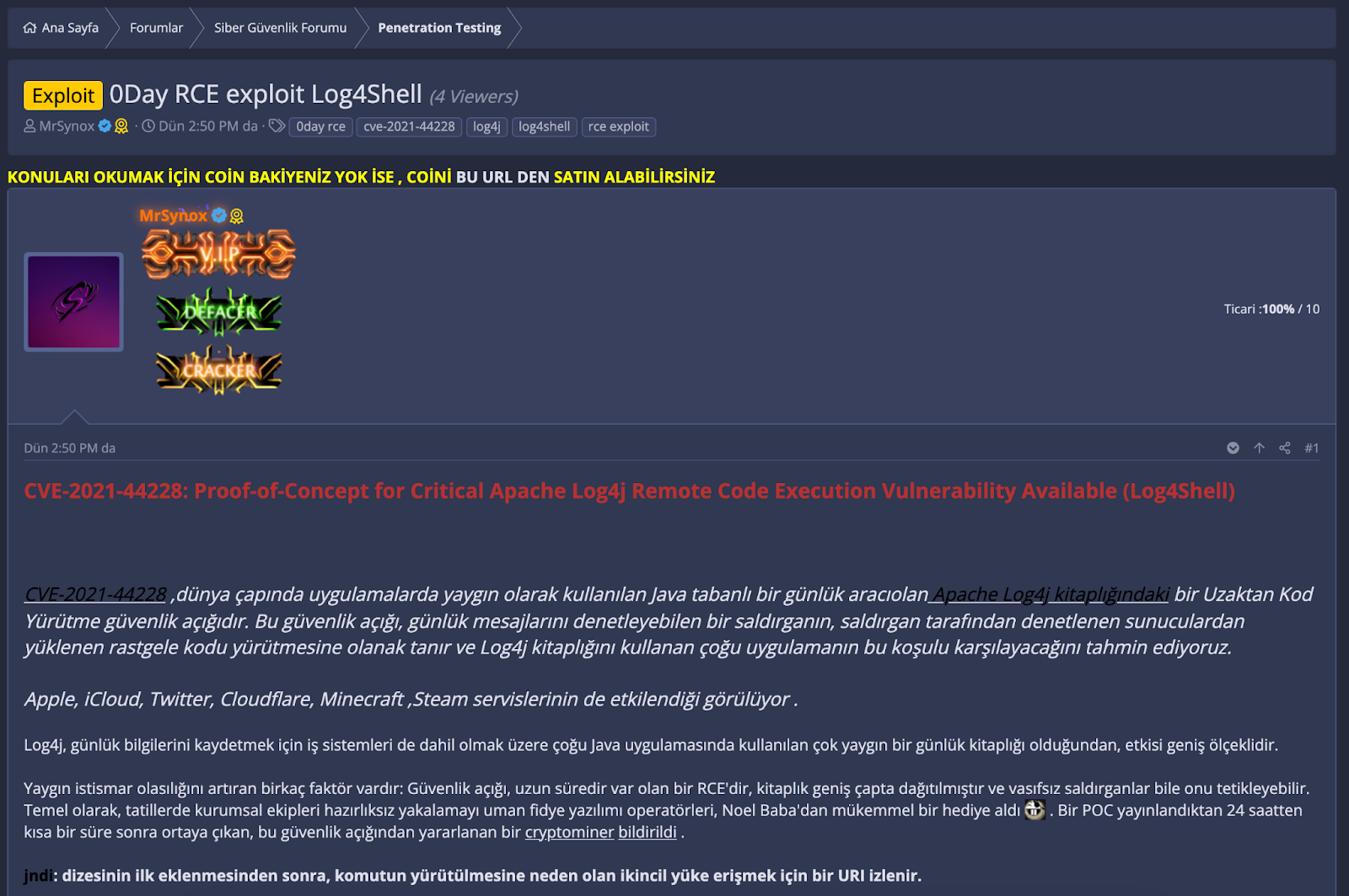
3. Code with a proof of concept for the exploit has been published on GitHub.
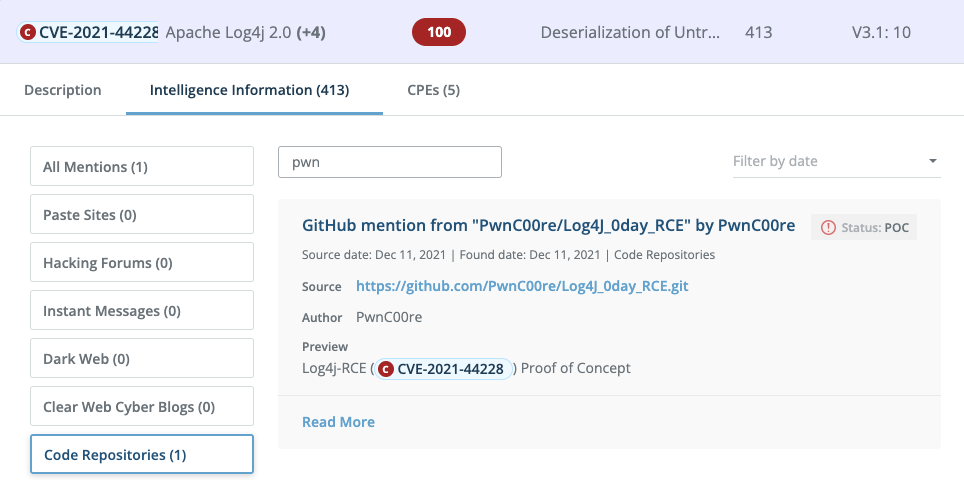
The underground cybercrime community functions like any other business model, but what sets it apart is the spirit with which bad actors share their work for mass consumption. The example above is completely open and free for anyone to access and utilize.
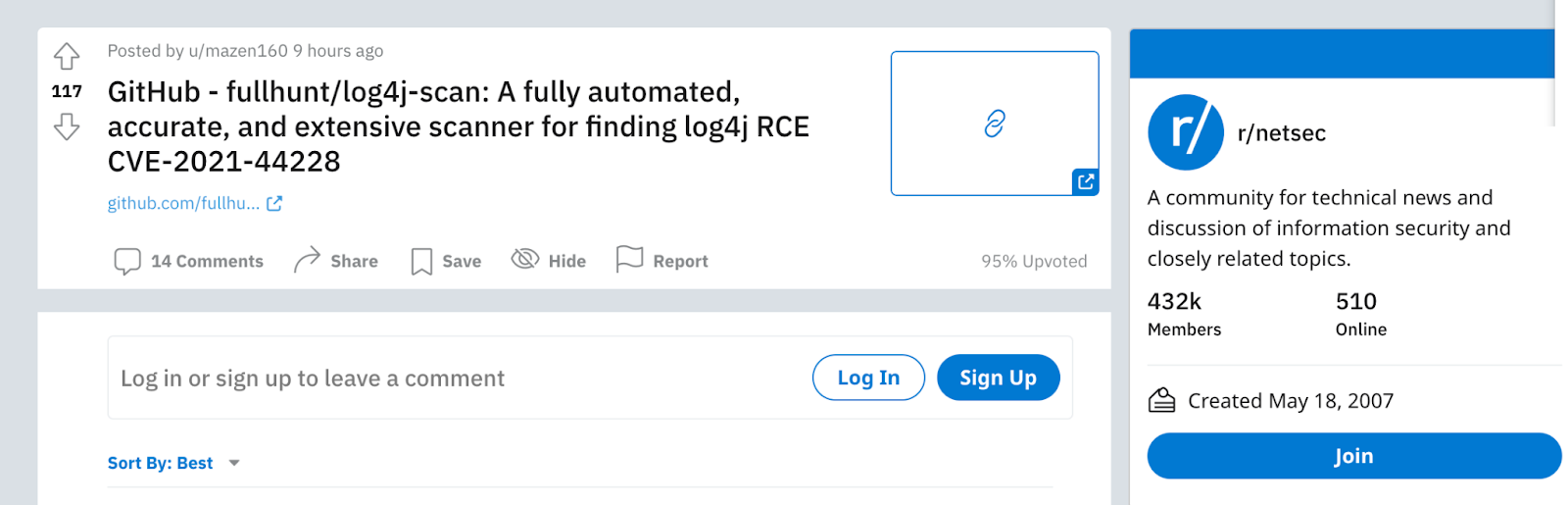
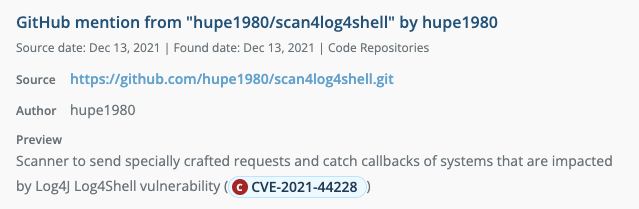
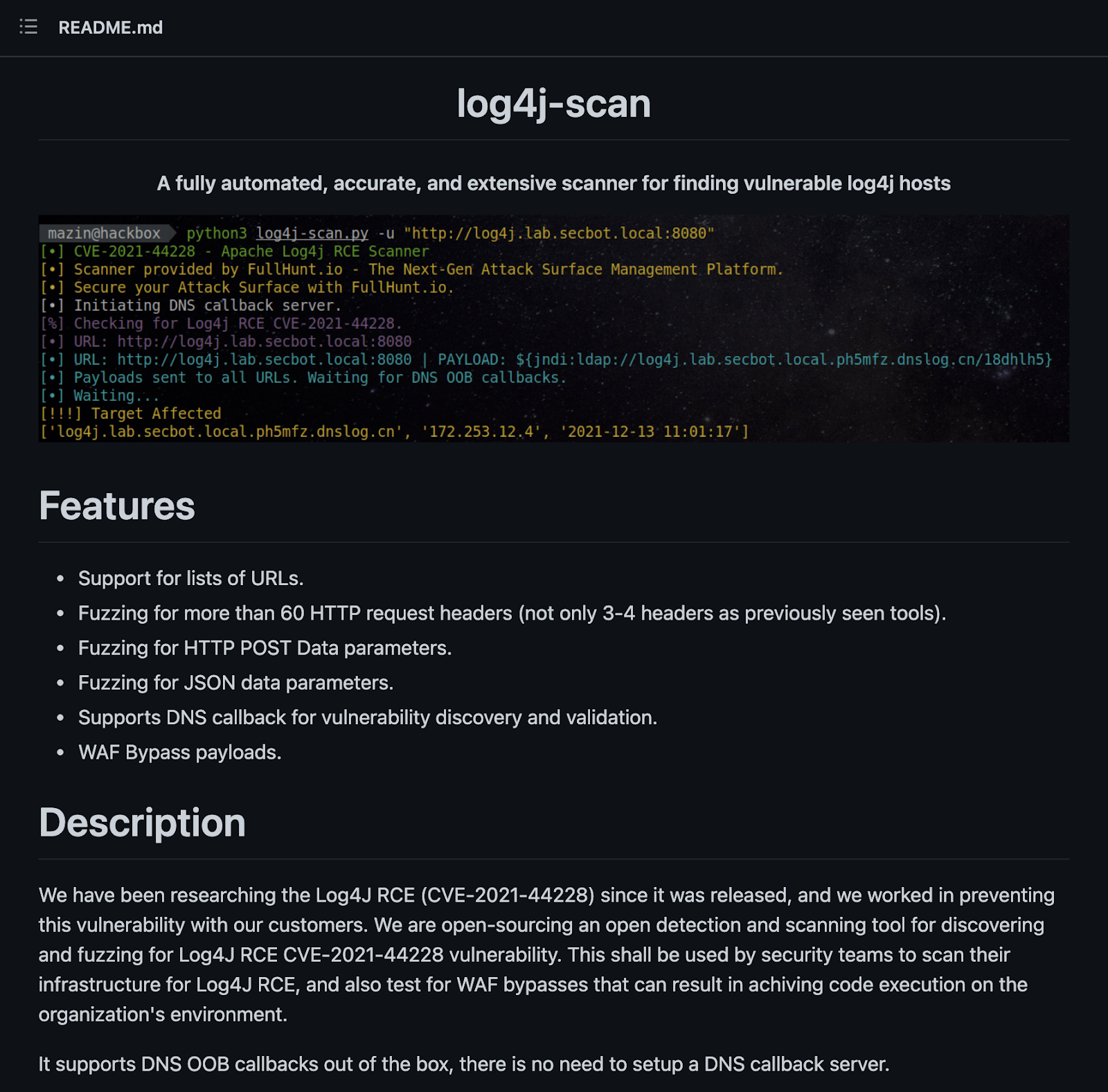
4. Various scanners were published on GitHub to identify vulnerable systems.
Scanners are the cybercriminal's tool of choice for finding specific vulnerabilities in networks communicating via the internet. Using a scanner, any company — regardless of size — can be a target.
While others look inside, we look outside
The bottom line is that threat actors are showing great interest in Log4j within underground communities, and they are leveraging these communities to share information and experience regarding exploiting this vulnerability. That emphasizes the need to quickly patch this vulnerability, before multiple cybercriminals put their hands on an exploit and start to utilize it on a large scale.
