Kubernetes was first presented in 2014, and it almost entirely changed the way technological and even non-tech companies use infrastructure for running their applications. The Kubernetes platform still feels new and exciting — it has awesome features and can fit most use cases.
But hackers find the combination of new technology and user inexperience that's just right for their malicious activity. Deploying your product on a Kubernetes cluster has a different security cost than on a traditional Linux server.
What are the risks of using Kubernetes?
The risks of a Kubernetes (K8s) deployment are actually the same as in traditional Linux servers. Most of them can be summed up to these 3 targets:
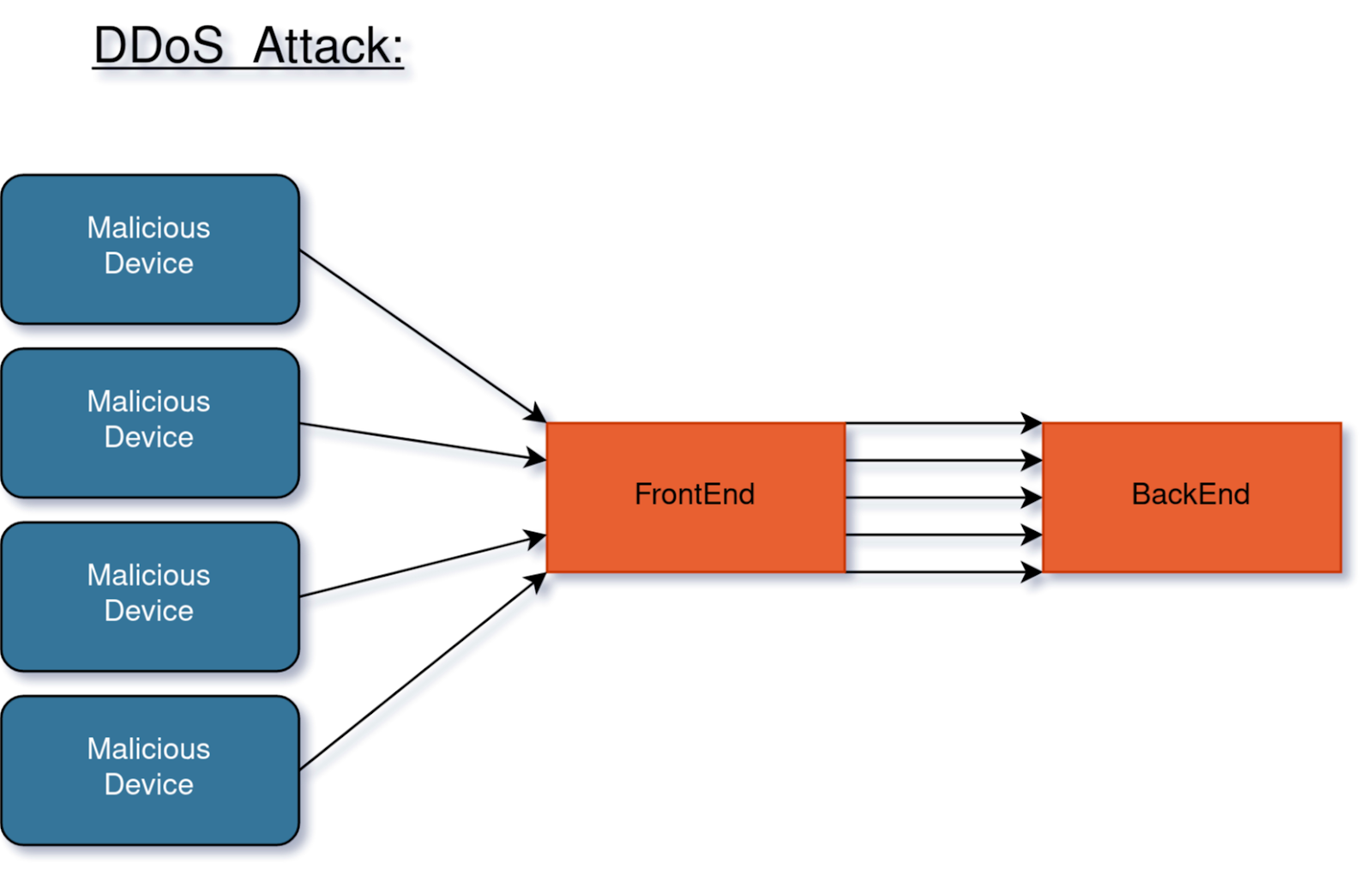
- Denial of Service (DoS): These kinds of attacks want your service down. They can be caused in many different ways, including distributed denial of service (DDoS) attacks or SQL injections that erase your databases. As there is no direct profit to the attacker, these attacks are of most interest to malicious groups who disagree with your company values or products, or to your competitors.
- Information exfiltration: Another type of attack targets the information you hold. These attacks can collect your information, like your profits, source codes, names of employees, and so on. Or they can collect private data about your customers and users — who they are, their credit card numbers, health state, financial assets, and everything you know about them. None of this is data you want to be known outside the company.
- Hardware hijack: A hardware hijack is any type of attack that runs a malicious code on your compute resources and causes them to operate in a way that you did not program or intend them to run. Most of these attacks are related to cryptocurrency. They typically either turn your CPU/GPU to Bitcoin miner or conduct a ransomware attack by encrypting your file system and requesting you to pay ransom (usually in Bitcoin) to unencrypt it. As the important point here for attackers is profit, not the identity of the victim, these attacks usually originate from bots or automatic scripts, rather than with dedicated special operations of malicious groups or individuals.
How can you defend yourself?
Securing deployments and identifying malicious activity on Kubernetes clusters is similar to how it's done on traditional Linux servers. Most of the differences are in the implementation itself. But there are some distinctions worth mentioning. Let's focus in on the operating system aspects of security.
Processes and system calls
“The system call is the fundamental interface between an application and the Linux kernel." —Linux manual pageLinux has over 400 different system calls. These can be used for requesting to read a file, executing another program, sending a network message, and more. As you've probably guessed, these operations can be risky when used by unwanted programs.
The Linux Kernel has security mechanisms against malware, but it isn't fully protected. So system calls may seem legitimate even when they aren't. Tracking these system calls can give good insight on what a process does. In native Linux, it can be easy to track these down from a single point on the server. However, in K8s Linux nodes, the distribution, dynamics, and containerization makes this mission a very complex task.
Network security
The internet connection is your face for the customers, but it's also the entry point for various malicious software into your infrastructure. Luckily, the big cloud providers and most of the internet-facing frameworks are well-protected against these attacks. But nothing is 100% safe. Moreover, some of the images you are using may contain security holes themselves. These can cause a malicious program to initiate from inside your cluster.
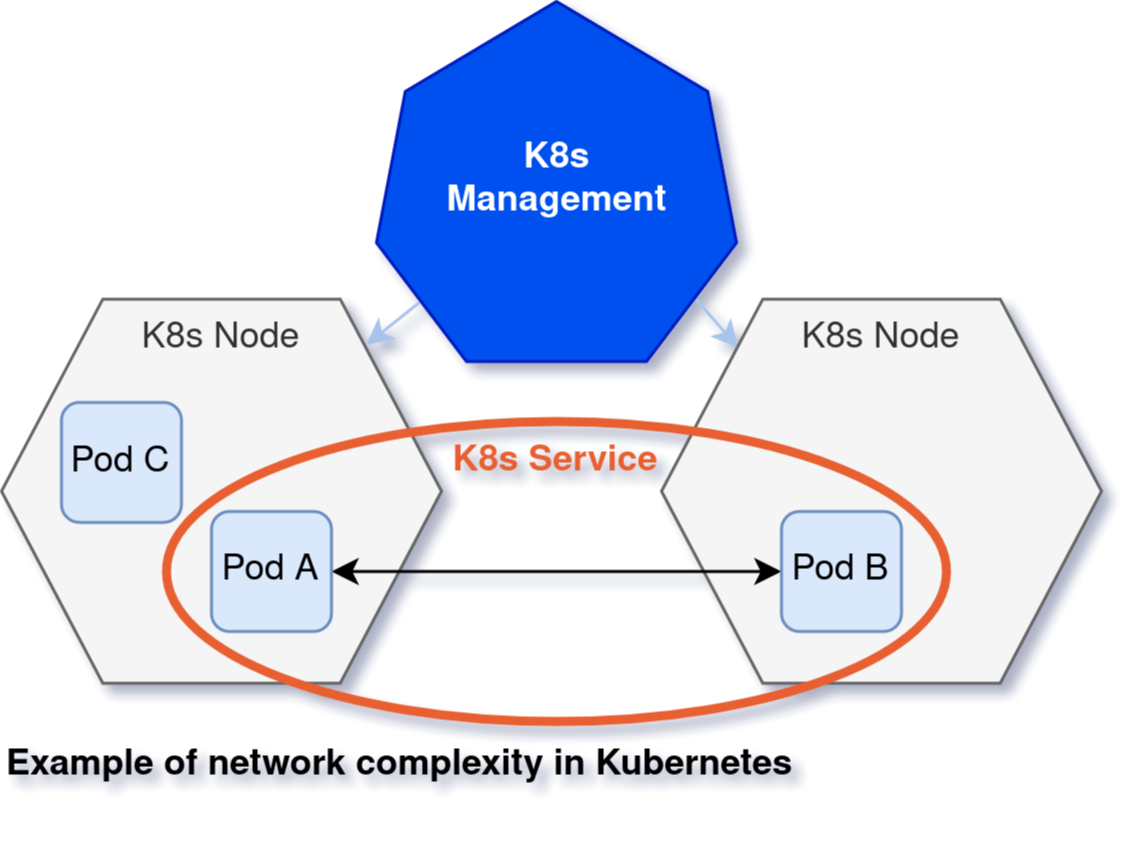
Tracking the network from the inside out can give you a lot of information on malicious activity. But you also have to consider the “east-to-west" traffic inside your infrastructure — the internal communication. In traditional Linux servers and VMs, you know exactly which microservices exist and define firewall services accordingly. However, in Kubernetes, the dynamic nature of the pods and resources makes it hard to track this traffic, so it can be difficult to find the network holes.
File system
It may seem easy to detect new files and file changes in order to determine unwanted changes, but tracking and analyzing your whole file system can be a large, complex task in Linux servers. They can have terabytes of storage, and reading them — especially from a magnetic hard disk — isn't fast enough to detect malicious activity when it happens. However, the containerization concept of Kubernetes can be to our advantage here, as container images are usually small, lightweight, and repetitive. Looking inside the containers files should have highly expected results.
More to come
This is one of two articles covering the detective resources that can help us identify unwanted activity in your Kubernetes clusters. In this first part, we saw that both Kubernetes and traditional Linux servers have vulnerabilities that originate in the processes, network, or file system. However, there are differences in how to monitor malicious activity in Kubernetes versus Linux. Some vulnerabilities may seem harder to defend in Kubernetes, but most of them are actually easier.
InsightCloudSec, Rapid7's cloud-native security platform, covers these differences and ensures your on-premises server farm is secured.
The next article will explain further about the unique aspects of Kubernetes security that do not exist in traditional Linux servers. Stay tuned!
Additional reading
Kubernetes Guardrails: Bringing DevOps and Security Together on Cloud
Stay Ahead of Threats With Cloud Workload Protection
Make Room for Cloud Security in Your 2022 Budget
Time to Act: Bridging the Gap in Cloud Automation Adoption
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe