Security for Kubernetes might not be quite the same as what you're used to. In our previous article, we covered why security is so important in both Linux on-premises servers and cloud Kubernetes clusters. We also talked about 3 major aspects of Linux server security — processes, network, and file system — and how they correspond to Kubernetes. So today, we'll talk more about the security concerns unique to Kubernetes.
Configurations
When trying to secure your infrastructure, you have to start by configuring it well. For example, this might mean disabling all unused features or using allow-policies wherever you can to keep your files, executables, or network available only to the intended entity. Both Linux servers and Kubernetes clusters have known vulnerabilities and recommendations.
One of the famous among these is the Center for Internet Security (CIS) recommendations, which are often used for compliance for insurance. Having a cloud security platform that can help implement these recommendations can be a major boon to your security.
API server
The Kubernetes API server is the admin panel, so to speak, of your cluster. In most deployments, this HTTP server is exposed to the internet. This means that a hacker that finds their way to the API server can have full control over your cluster.
Using the most strict authentication and authorization settings is highly recommended to prevent this. If you can set your cluster to private, with access only allowed from an internal network, you can sleep well at night. And just as with with configurations, you should be aware at all times of who (and what) can have access to which resources and operations in your cluster.
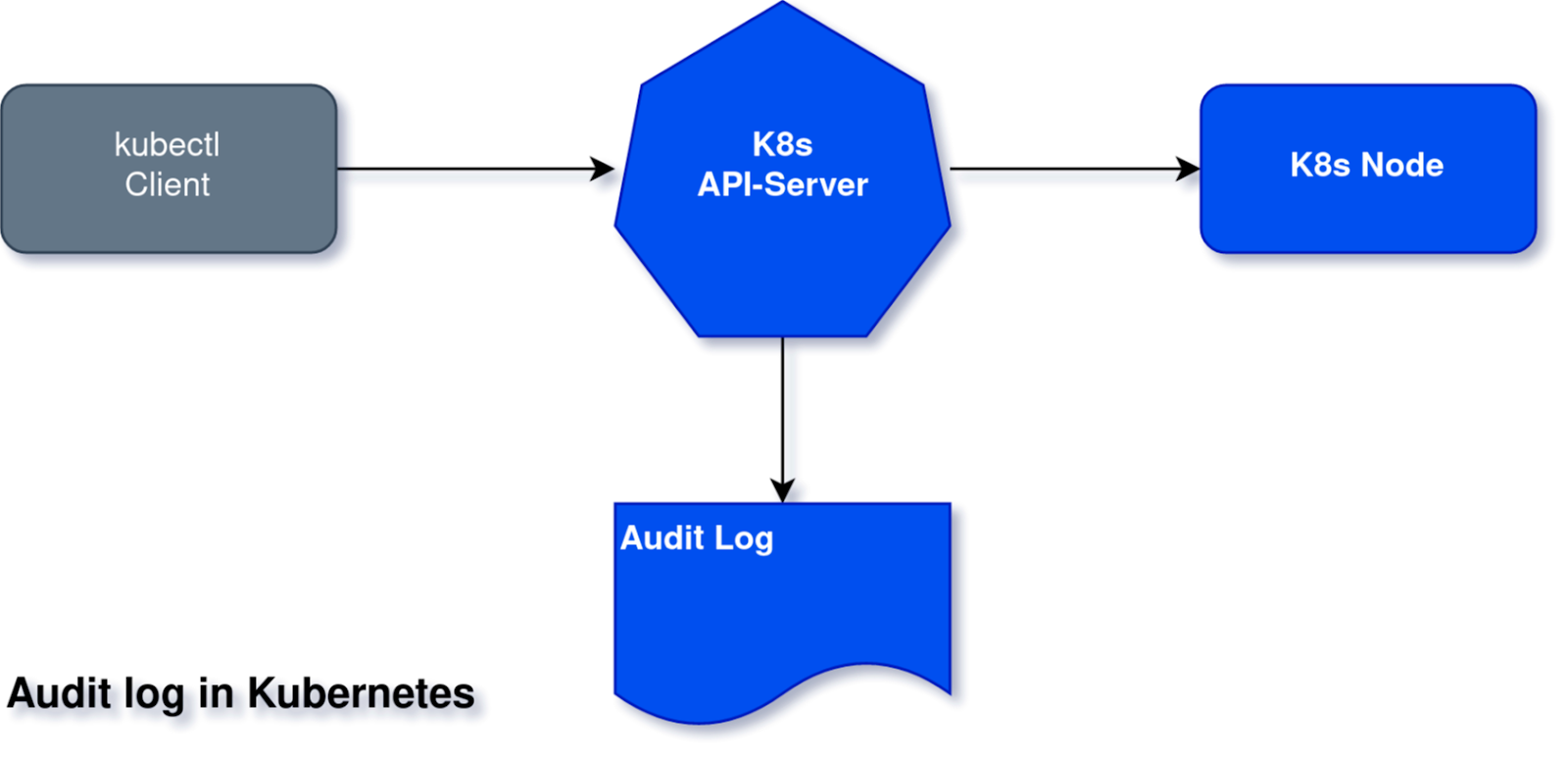
Audit log and other Kubernetes logs
In Kubernetes, there are additional attack vectors using the Kubernetes control plane itself that don't exist in Linux server security. For example, an attack could call the Kubernetes API to load a new pod you didn't want.
Kubernetes and cloud providers invest a lot of effort in preventing unauthorized users and machines from doing this. But there is always a chance that one of your employees gets hacked or a badly configured service account has too much power. Kubernetes logs all requests to its audit log so they can be investigated later in case of a breach. Additional logs include the kube-API log or etcd (resources DB) log.
Container runtime
Container runtime is also a unique aspect of Kubernetes security. In Kubernetes, each node is actually a virtual Linux server running a container runtime daemon. A container runtime is responsible for managing the images and running and monitoring the containers, their storage and network provisioning, and more. You might be familiar with Docker as a container runtime. In reality, Docker is a company developing multiple container tools, and their container runtime is named containerd. Other container runtimes for Kubernetes include CRI-O, Rocket, and more.
Apart from a whole Linux server or virtual machine that uses its own single operating system, multiple containers are usually running over multiple operating systems that share the same host kernel. Although the operating systems of the containers are minimal, they may still have security holes. And the more holes the merrier for the attacker! Monitoring the container runtime activity can also yield a lot of information about what is going on in the node — what processes are running inside the container, any internal communication that might escape from network monitoring, the data being collected and created, and so on.
Right tools, lower risks
The unique interfaces and engines of Kubernetes can be an additional exposed surface in terms of security, especially when considering the complexity of the system. However, don't forget that distribution and containerization add to security and help isolate potential malware.
Kubernetes may come with a few new risks to watch out for, but that's no reason to be scared off. As long as you know what to look for, security for your Kubernetes clusters doesn't have to be any harder than it was for your Linux servers. And there's no need to go it alone — not when you can have handy tools like InsightCloudSec, Rapid7's cloud-native security platform, at your side.
Additional reading
- Why Security in Kubernetes Isn't the Same as in Linux: Part 1
- Stay Ahead of Threats With Cloud Workload Protection
- Kubernetes Guardrails: Bringing DevOps and Security Together on Cloud
- Time to Act: Bridging the Gap in Cloud Automation Adoption
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe