Greetings, fellow security professionals. As we enter into the new year, we wanted to provide a recap of product releases and features on the vulnerability management (VM) front for Q4 2021.
Let's start by talking about the elephant in the room. The end of last year was dominated by Log4Shell, the once-in-a-generation security vulnerability that impacted nearly every corner of the security industry and completely ruined every holiday party we were invited to. But as you will see below, in addition to providing you with strong Log4Shell coverage, our VM team has been hard at work on multitudes of other features and capabilities as well.
Chief among these are improvements to credential management aspects of scanning, in the form of Scan Assistant, and better Credential Status Reporting. Container scanning is also seeing improved integration of results, as well as enhanced checks leveraging Snyk. Last but not least, email distribution of reports will allow you to better communicate findings across the organization. In other words, Q4 was more than Log4Shell over here, and we're excited to tell you about it.
(Note: Starting this edition, you will see up front a label of [InsightVM] vs [InsightVM & Nexpose] to clarify which product a new feature or capability pertains to)
[InsightVM & Nexpose] Log4j security content
When Log4j hit in early December, our VM teams went into high gear offering solutions and boosting ways InsightVM can identify vulnerable software. Here's a recap of our current coverage:
- Authenticated, generic JAR-based coverage for Windows, macOS, and Unix-like operating systems
- Mitigation checks for macOS and Unix-like operating systems
- Remote check for vulnerable HTTP(S) applications
- Package-based checks for supported Linux distributions
- Coverage and mitigation checks for CVE-2021-44228 and CVE-2021-45046 affecting VMware vCenter Appliances
- We also added IVM checks to assess CVE-2021-45046 on VMware Horizon Connection Server and Horizon Agent
- Authenticated JAR-based checks for follow-on CVEs (CVE-2021-45046, CVE-2021-45105, CVE-2021-44832)
[InsightVM] Log4j dashboard and Query Builder
We added a log4j Query Builder query to the Helpful Queries section of Query Builder and a new dashboard template (the Specific Vulnerability Dashboard) designed to allow customers to visualize the impact of a specific vulnerability or vulnerabilities to their environment.
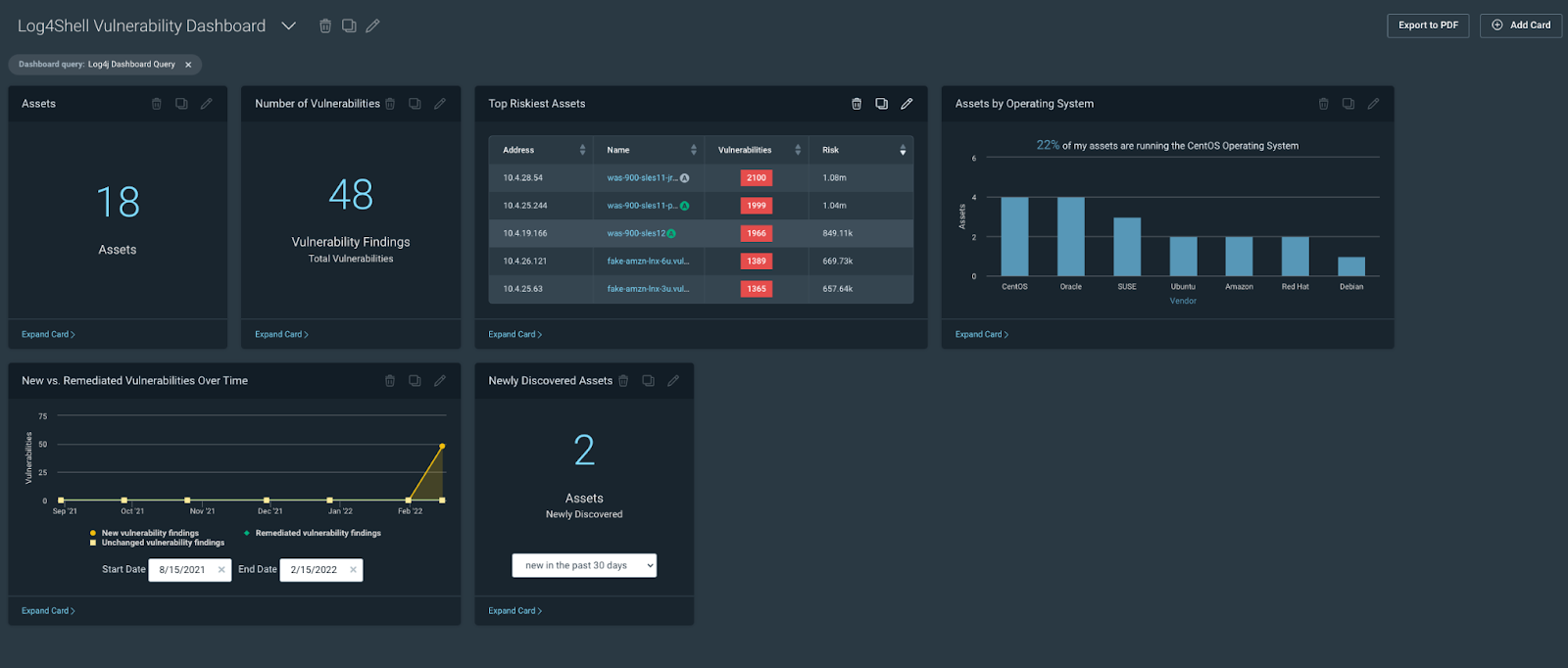
We have a TON of additional Log4j resources here for you to check out:
- A blog from our product manager Greg Wiseman that gives some great context on using InsightVM to detect Log4j
[InsightVM & Nexpose] Additional vulnerability checks and content (non-Log4Shell)
Believe it or not, the world has seen other vulns beyond Log4j. As a team, we added nearly 4,000 vulnerability checks to InsightVM and Nexpose in Q4 and more than a few that warrant mentioning here.
- Zoho's ManageEngine portfolio was affected by critical unauthenticated remote code execution vulnerabilities in ServiceDesk Plus and Desktop Central
- We also saw opportunistic exploitation of CVE-2021-42237, an insecure deserialization vulnerability in the SiteCore Experience Platform
- The open-source CI/CD solution GoCD was hit by CVE-2021-43287, allowing unauthenticated attackers to leak configuration information, including build secrets and encryption keys, with a single HTTP request
If you want to learn more about these and many other threats that materialized during Q4, check out our Emergent Threat Response blogs (you should check those out regularly, because we are constantly and consistently writing about new threats in near real-time).
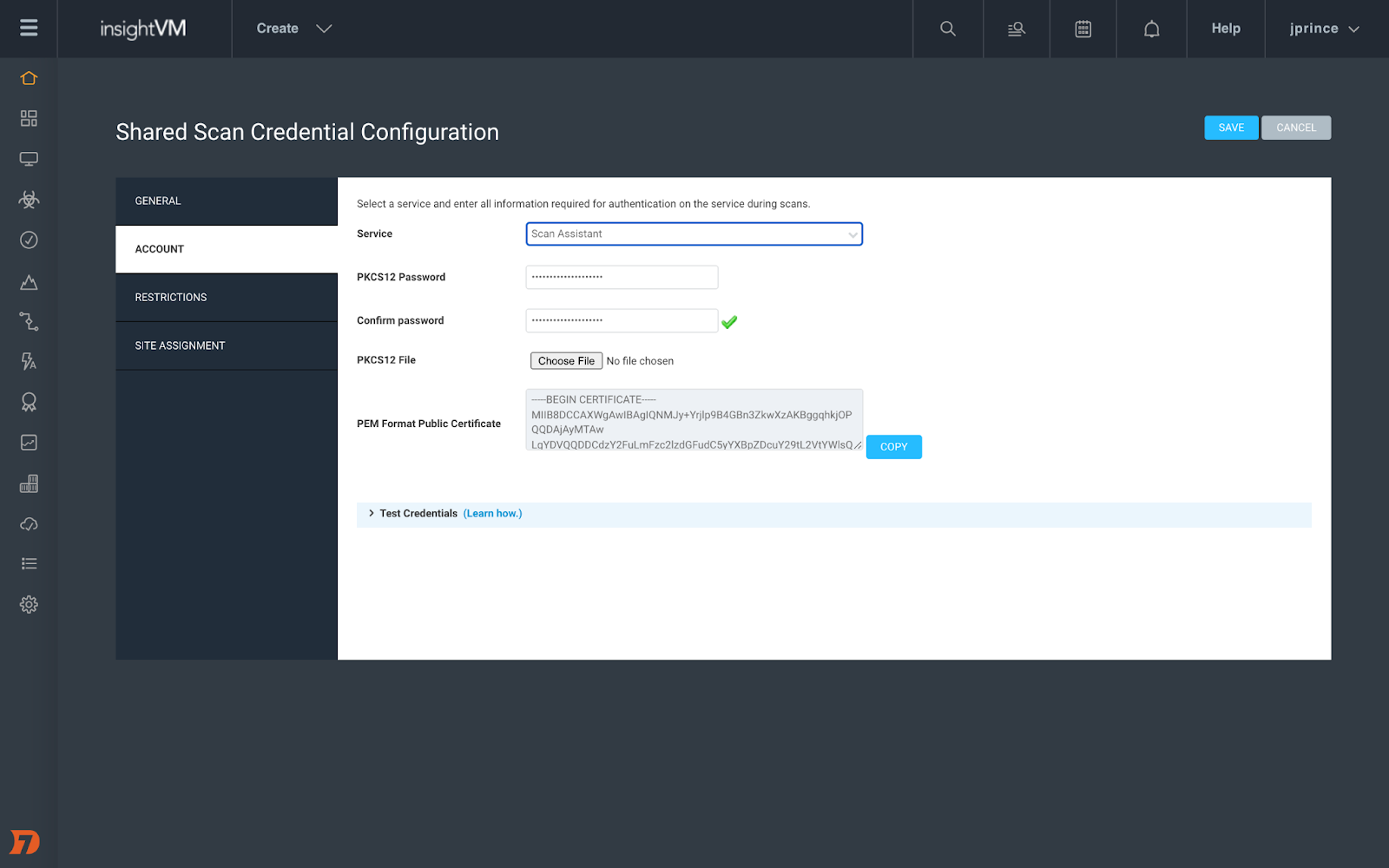
[InsightVM & Nexpose] Introducing Scan Assistant
Credential management for Scan Engine can be a huge burden on vulnerability management teams, especially when you are managing tens of thousands of devices. That's why we created Scan Assistant to help ease that burden.
Scan Assistant is a lightweight service that can be installed on each targeted scan. It allows you to scan targets without the need for credentials. When the Scan Engine scans a target with the Scan Assistant attached, it will automatically collect the information it needs to access the target without the need for additional scan credentials. In addition to enhanced security, Scan Assistant improves scan performance for vulnerability and policy scans, has a fully on-premise footprint, works with both InsightVM and Nexpose, and is completely idle until engaged by a scan. Scan Assistant has now GA'ed for Windows environment. We'll have coverage for other OSes to follow in the future.
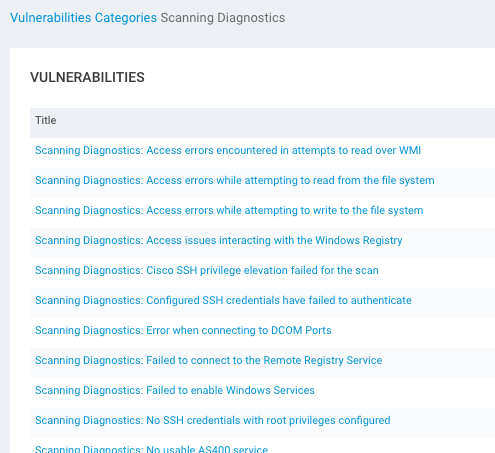
[InsightVM & Nexpose] NEW - Scan diagnostic checks for Credential Status Reporting
While we're on the subject of credentials during scans, every so often the scan engine can return a partial or total credential failure that might leave you scratching your head. With this new feature, InsightVM and Nexpose offer scan diagnostic checks that allow you to have more granular visibility into credential success (or lack thereof). This will allow you to better troubleshoot authenticated scans that return results you did not expect.
Results are written as vulnerability checks, giving you the ability to use aspects of the platform's functionality that you are already familiar with to assess where things went wrong.
[InsightVM] Container Image Scanner integration, additional container software library package checks, improved container scan results integration, and emailed reports
We are always looking for ways to make your life easier, and these three new improvements to the InsightVM platform are designed to do just that. First, we enhanced the Container Image Scanner to record and post results to InsightVM rather than just to the developer's local machine where the container lives. This allows the organization to better monitor the security of containers under development. Take a look for yourself — it's in the Builds tab of the Contain Security Section.
We've also launched a fingerprinter for .Net NuGet and Ruby Gem Packages. This allows us to check for vulnerabilities in these software packages leveraging the Snyk integration. This brings our support for Snyk security content to include Java Maven, Node NPM (Javascript), Python PIP, and now .Net NuGet Ruby Gem packages.
Finally, we're making it easier to share findings across your organization by allowing reports to be sent via email. The entire message includes a password-protected and encrypted pdf and recipients receive a password in a separate email to ensure the info remains secure.
Q4 was a trying time for everyone in the security sphere, and we know that our work on that front is far from done. We hope that some or all of these new InsightVM and Nexpose features make Q1 2022 and beyond a little easier, less stressful, and ultimately more secure. Stay strong!
Additional reading:
- Log4Shell 2 Months Later: Security Strategies for the Internet's New Normal
- Log4Shell Strategic Response: 5 Practices for Vulnerability Management at Scale
- Distribute Reports to Email Addresses in InsightVM
- InsightVM Scan Diagnostics: Troubleshooting Credential Issues for Authenticated Scanning
