The MITRE ATT&CK framework is one of the most comprehensive and reputable knowledge bases of known adversary tactics, pragmatic mitigation strategies, and prudent detection recommendations available today. ATT&CK is freely available and widely used by defenders in industry and government to find gaps in visibility, defensive tools, and processes as they evaluate and select options to improve their network defense. In addition, MITRE Engenuity makes the methodology and resulting data publicly available, so other organizations can benefit and conduct their own analysis and interpretation.
The framework strengthens the Detection and Investigation Management experiences within InsightIDR by providing context, evidence, and recommendations all in one place. Here's a closer look at 3 ways to bring that value to life.
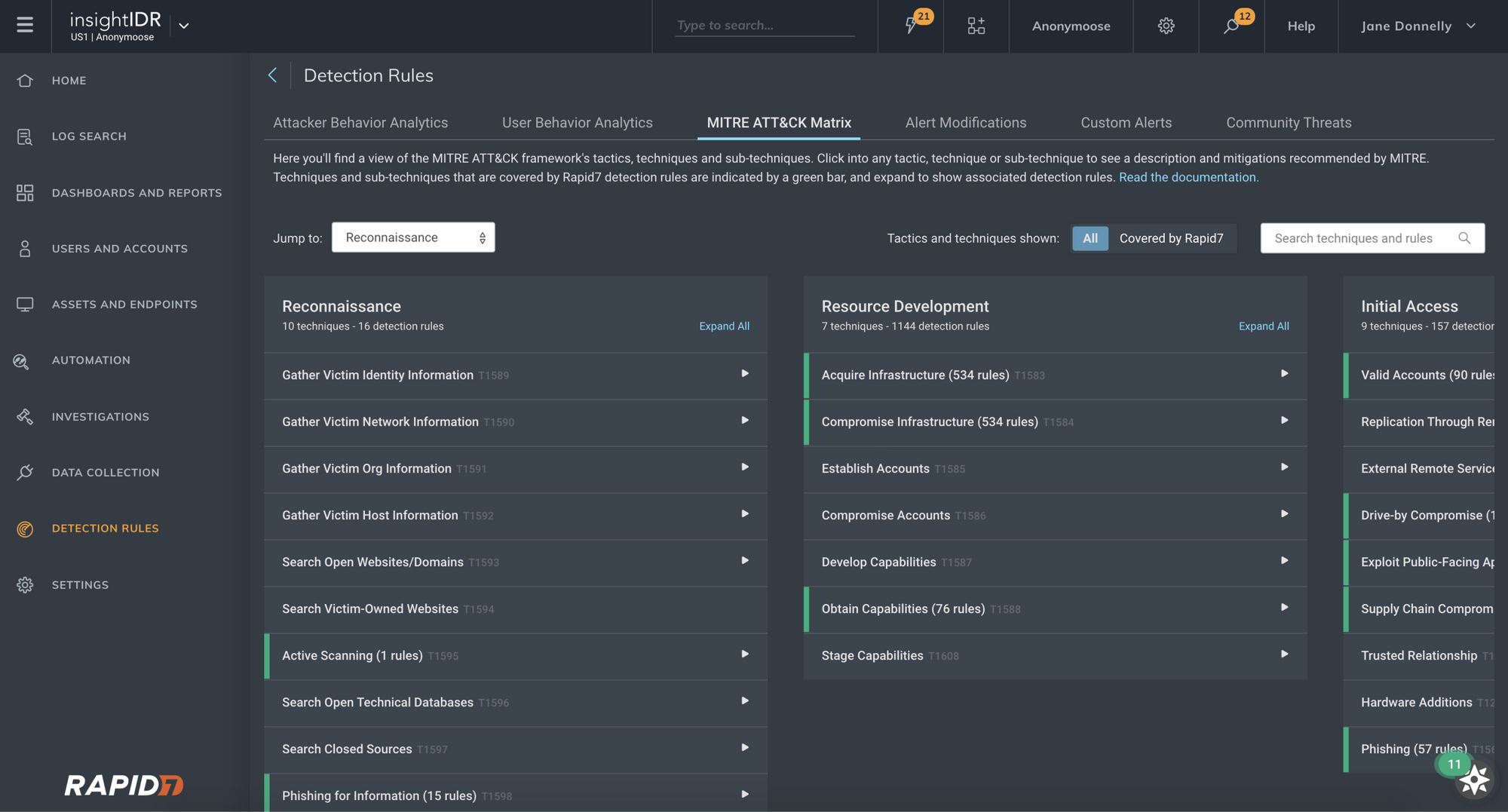
1. Visualize MITRE ATT&CK coverage
- Visualize which techniques and sub-techniques you have detections mapped to with information on each threat actor's TTPs (Tactics, Techniques, and Procedures).
- Drill down and see the specific detection rules that map to each area of the framework in your environment.
- MITRE ATT&CK context and filters apply automatically against all of your data, helping you detect and respond to attacks early and giving you the alert fidelity you want, filled with the context you need.
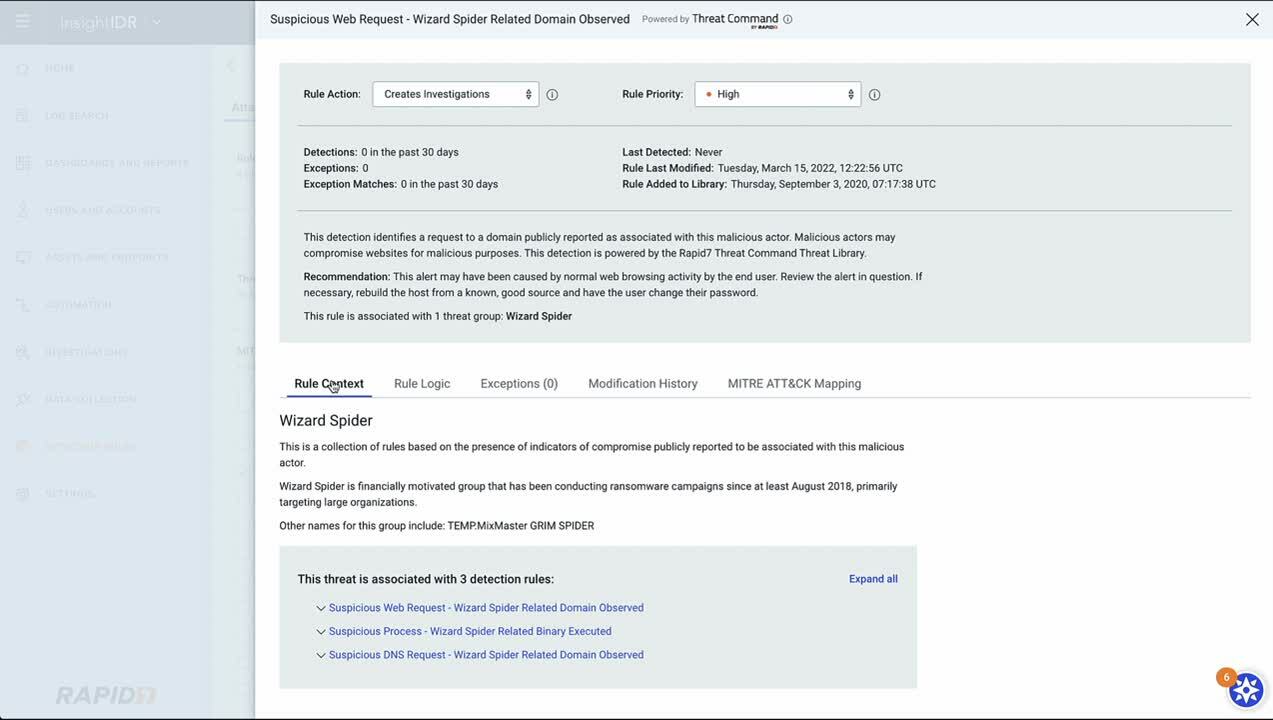
2. Triage and prioritize faster with MITRE filters
- Tune your detection rules based on the ATT&CK context and your unique security environment to reduce benign alerts and bring high-priority alerts to the forefront.
- Understand the context behind an alert by viewing information about the attacker's underlying techniques and sub techniques.
- Filter and sort your alerts and investigations based on the MITRE info to distill down to where it really matters when time is of the essence.

3. Accelerate mean time to respond (MTTR)
- Users can quickly prioritize which investigations are most critical to tackle first.
- Determine how to respond to the attack with the mitigation recommendations provided by MITRE ATT&CK.
- Leverage the strategies provided to work internally and take proactive steps within the organization to prevent the next attack, staying one step ahead of attackers.
- Use the MITRE insights provided in the evidence panel to inform the decision-makers on the best way to proceed.
With InsightIDR, your detections are vetted by a team of professional security operations center (SOC) analysts and mapped to MITRE ATT&CK to remove the guessing game of what an attacker might do next. If you're looking to hear more from us on MITRE, our Rapid7 MDR team shared their thoughts on MITRE ATT&CK.
Additional reading:
- Run Faster Log Searches With InsightIDR
- Demystifying XDR: How Curated Detections Filter Out the Noise
- This CISO Isn’t Real, But His Problems Sure Are
- Demystifying XDR: Where SIEM and XDR Collide
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe