Introducing new InsightIDR capabilities to accelerate your detection and response program
When we talk to customers and security professionals about what they need more of in their security operations center (SOC), there is one consistent theme: time. InsightIDR — Rapid7's leading cloud SIEM and XDR — helps teams cut through the noise and accelerate their detection and response, without sacrificing comprehensive coverage across modern environments and advanced attacks. This Q1 2022 recap post digs into some of the latest investments we've made to drive tangible time savings for customers, while still leveling up your detection and response program with InsightIDR.
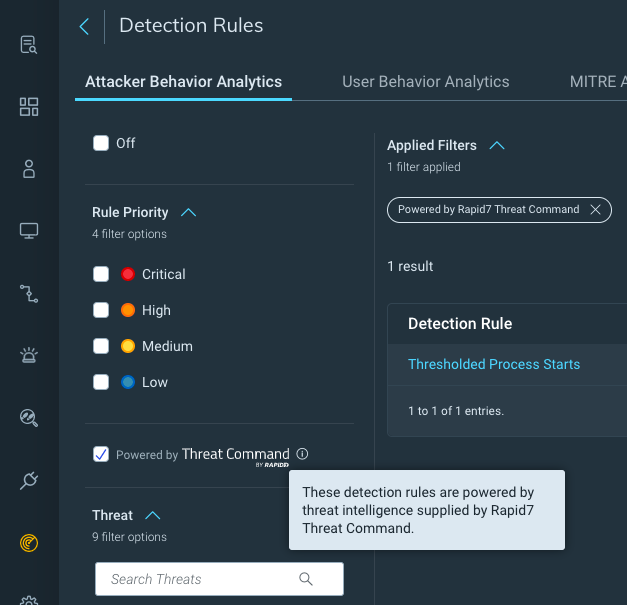
New InsightIDR Detections powered by Threat Command by Rapid7's TIP Threat Library
Following Rapid7's 2021 acquisition of IntSights and their leading external threat intelligence solution, Threat Command, we are excited to provide InsightIDR customers with new built-in threat intelligence via Threat Command's threat intelligence platform (TIP).
We have integrated Threat Command's TIP ThreatLibrary into InsightIDR, bringing its threat intelligence content into our detection library to ensure Rapid7 InsightIDR and Managed Detection and Response (MDR) customers have the most up-to-date and comprehensive detection coverage, more visibility into new IOCs, and continued strength around signal-to-noise.
Using the combined threat intelligence research teams across Rapid7 Threat Command and our services organization, this content will be maintained and updated across the platform – ensuring our customers get real-time protection from evolving threats.
InsightIDR delivers superior signal-to-noise in latest MITRE Engenuity ATT&CK evaluation
We're excited to share that InsightIDR has successfully completed the 2022 MITRE Engenuity ATT&CK Evaluation, which focused on how adversaries abuse data encryption for exploitation and/or ransomware. This evaluation tested InsightIDR's EDR capabilities (powered by our native endpoint agent, the Insight Agent) and our ability to detect these advanced attacks. A few key takeaways and result highlights:
- InsightIDR demonstrated solid visibility across the cyber kill chain – with visibility across 18 of the 19 phases covered across both simulations.
- Consistently identified threats early, with alerts firing in the first phase – Initial Compromise – for both the Wizard Spider and Sandworm attacks.
- Showcased our commitment to signal-to-noise – with targeted and focused detections across each phase of the attack (versus firing loads of alerts for every minute substep).
As our customers know, EDR is just one component of the detection coverage unlocked with InsightIDR. While beyond the scope of this evaluation, beyond endpoint coverage, InsightIDR delivers defense in depth across users and log activity, network, and cloud. Learn more about InsightIDR's MITRE evaluation results in our recent blog post.
Investigate in seconds with Quick Actions powered by InsightConnect
InsightIDR and InsightConnect teamed up to create Quick Actions, a new feature that provides instant automation within InsightIDR to reduce time to respond to investigations, all with the click of a button.
Quick Actions are pre-configured automation actions that customers can run within their InsightIDR instance to get the answers they need fast and make the investigative process more efficient, and there's no configuration required. Some Quick Actions use cases include:
- Threat hunting within log search. Use the "Look Up File Hash with Threat Crowd" quick action to learn more about a hash within an endpoint log. If the output of the quick action finds the file hash is malicious, you can choose to investigate further.
- More context around alerts in Investigations. Use the "Look Up Domain with WHOIS" quick action to receive more context around an IP associated with an alert in an investigation.
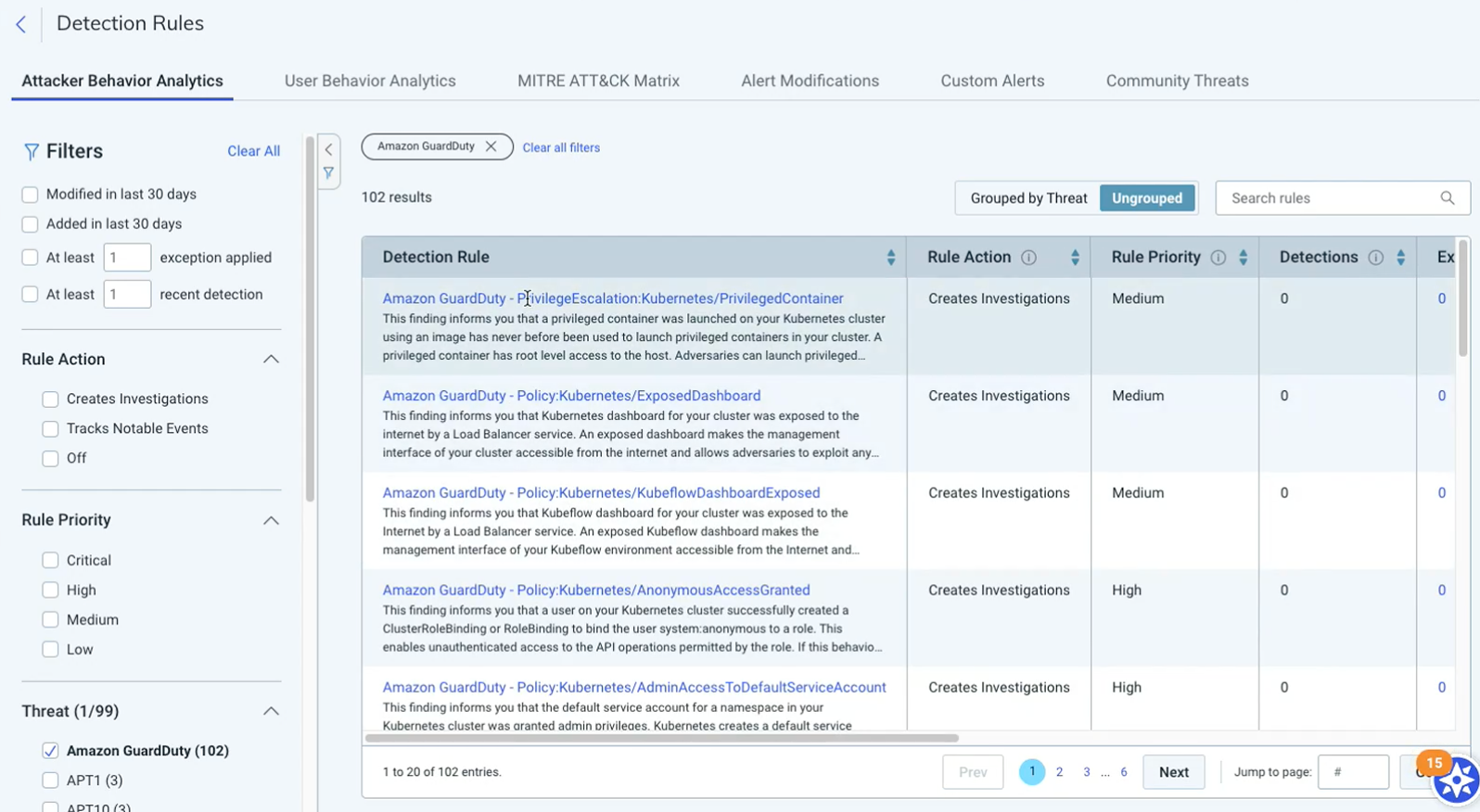
More customizability with AWS GuardDuty detection rules
We now have over 100 new AWS GuardDuty Attacker Behavior Analytics (ABA) detection rules to provide significantly more customization and tuning ability for customers compared to our previous singular third-party AWS GuardDuty UBA detection rule. With these new ABA alerts, it's possible to set rule actions, tune rule priorities, or add an exception on each individual GuardDuty detection rule.
New pre-built CIS control dashboards and overall dashboard improvements
We're continually expanding our pre-built dashboard library to allow users to easily visualize their data within the context of common frameworks.
The CIS Critical Security Controls are a recommended set of actions for cyber defense that provide specific and actionable ways to thwart the most pervasive attacks. We know CIS is one of the most common security frameworks our customers consider, so we've recently added 3 new CIS control dashboards that cover CIS Control 5: Account Management, CIS Control 9: Email and Web Browser Protections, and CIS Control 10: Malware Defenses.
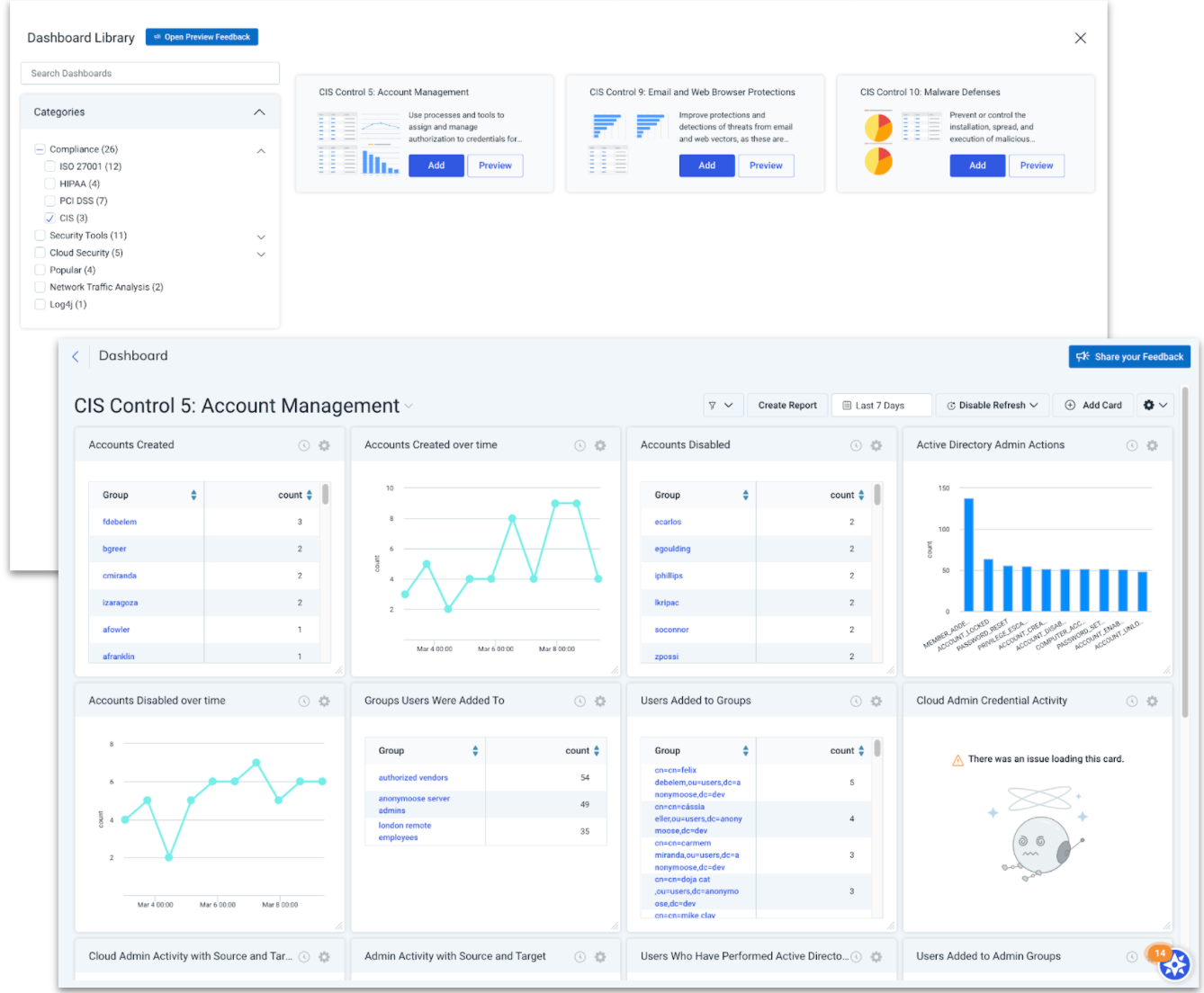
We also continue to make changes and additions to our overall Dashboard capabilities. Within the card builder, we've added the ability to:
- Change chart colors
- Add a chart caption
- Swap between linear and logarithmic scale for charts
- Add data labels on top of dashboard charts
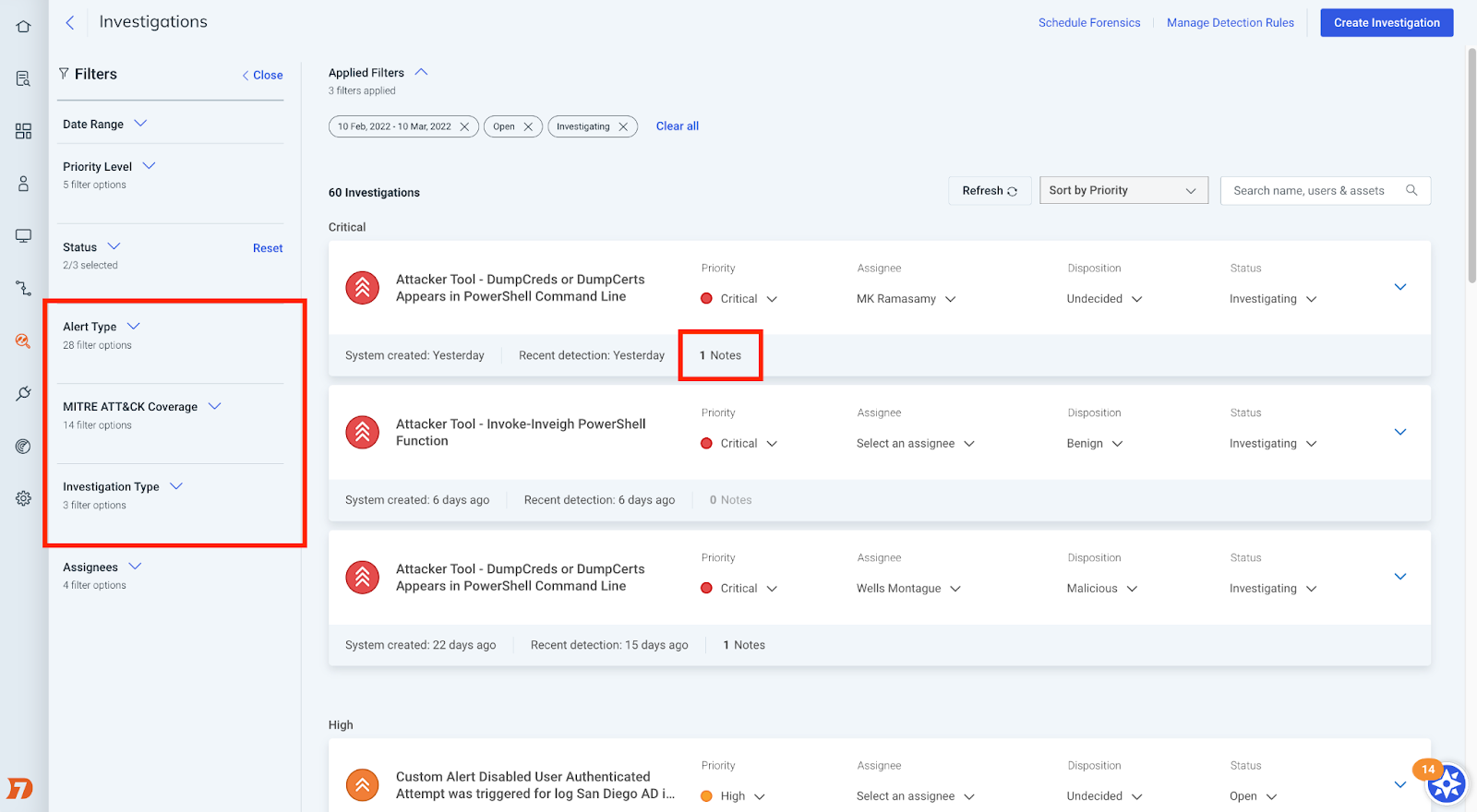
Continuous improvements to Investigation Management
Another area we are continuously making improvements in is Investigation Management. A huge part of this ongoing development is customer feedback, and over the last quarter, we've made some additions to the experience based on just that. We've added:
- New filters for alert type, MITRE ATT&CK tactic, and investigation type to provide more options when it comes to tailoring the list view of investigations
- The new "notes count" feature, which allows customers to save time and track the status of an ongoing collaboration within an investigation
- Improvements to the bulk-close feature within Investigation Management, and new progress banners so you can easily track the status of each bulk-close request
Other updates
- New CATO Networks event source can now be configured to send InsightIDR WAN firewall and internet firewall data.
- Log Search Syntax Highlighting applies different colors and formatting to the distinct components of a LEQL query (such as the search logic and values) to improve overall readability and provide an easy way to identify potential errors within queries.
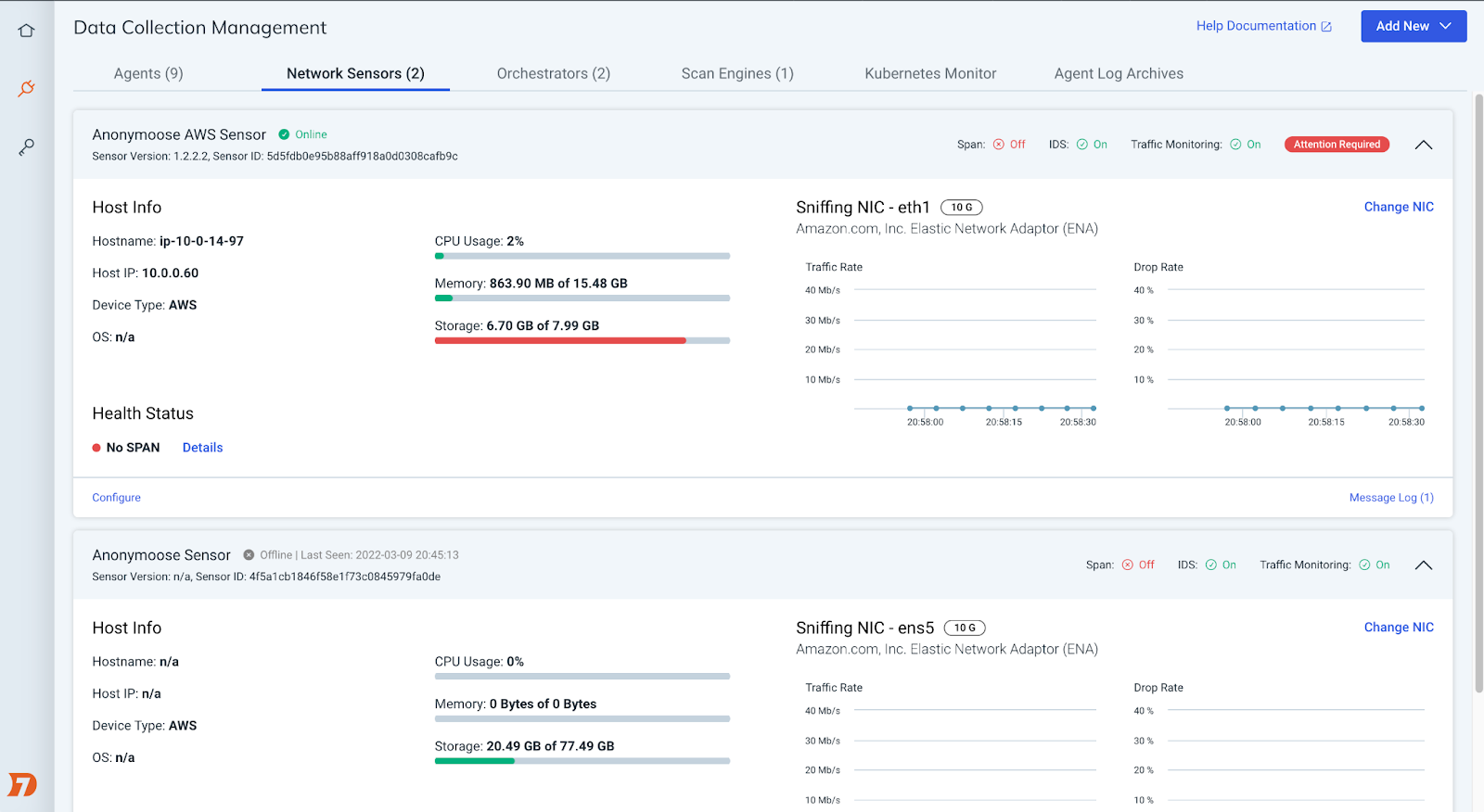
- New curated IDS Rules powered by the Insight Network Sensor help you detect activity associated with thousands of common pieces of malware.
- Insight Network Sensor management page updates make it easier to deploy and maintain your fleet of Network Sensors. We've rebuilt the sensor management page to better surface critical configuration statuses, diagnostic information, and links to support documentation.
Stay tuned!
As always, we're continuing to work on exciting product enhancements and releases throughout the year. Keep an eye on our blog and release notes as we continue to highlight the latest in detection and response at Rapid7.
Additional reading:
- Sharpen Your IR Capabilities With Rapid7’s Detection and Response Workshop
- MITRE Engenuity ATT&CK Evaluation: InsightIDR Drives Strong Signal-to-Noise
- Demystifying XDR: The Time for Implementation Is Now
- 3 Ways InsightIDR Customers Leverage the MITRE ATT&CK Framework