June's Patch Tuesday sees Microsoft releasing fixes for over 60 CVEs. Top of mind for many administrators this month is CVE-2022-30190, also known as Follina, which was observed being exploited in the wild at the end of May. Microsoft provided mitigation instructions (disabling the MSDT URL protocol via the registry), but actual patches were not available until today’s cumulative Windows Updates. Even if the mitigation was previously applied, installing the updates is highly recommended.
None of the other CVEs being addressed this month have been previously disclosed or seen exploited yet. However, it won’t be long before attackers start looking at CVE-2022-30136, a critical remote code execution (RCE) vulnerability affecting the Windows Network File System (NFS). Last month, Microsoft fixed a similar vulnerability (CVE-2022-26937) affecting NFS v2.0 and v3.0. CVE-2022-30136, on the other hand, is only exploitable in NFS v4.1. Microsoft has provided mitigation guidance to disable NFS v4.1, which should only be done if the May updates fixing previous NFS versions have been applied. Again, even if the mitigation has been put into place, best to patch sooner rather than later.
Also reminiscent of last month is CVE-2022-30139, a critical RCE in LDAP carrying a CVSSv3 base score of 7.1, which again is only exploitable if the MaxReceiveBuffer LDAP policy value is set higher than the default. Rounding out the critical RCEs for June is CVE-2022-30163, which could allow a malicious application running on a Hyper-V guest to execute code on the host OS.
The other big news this month is the end of support for Internet Explorer 11 (IE11) on Windows 10 Semi-Annual Channels and Windows 10 IoT Semi-Annual Channels, as Microsoft encourages users to adopt the Chromium-based Edge browser (which saw fixes for 5 CVEs this month). Internet Explorer 11 on other versions of Windows should continue receiving security updates and technical support based on the OS support lifecycle, so this is only the beginning of the end for the legacy browser.
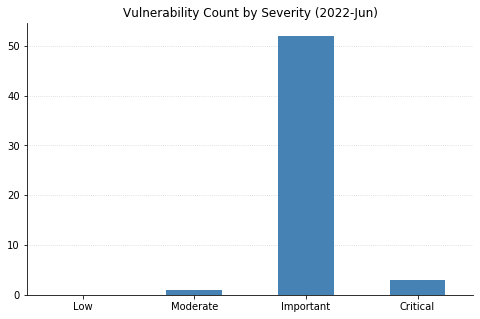
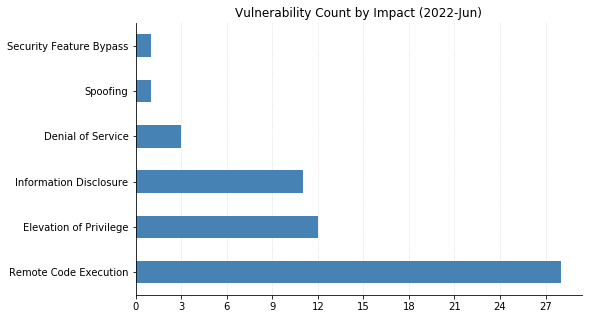
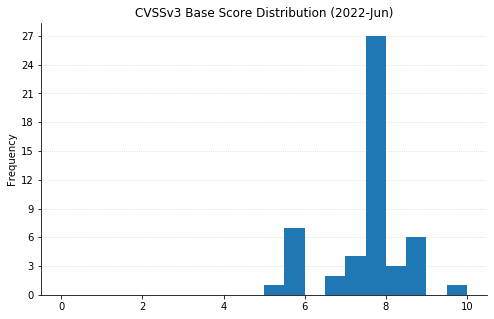
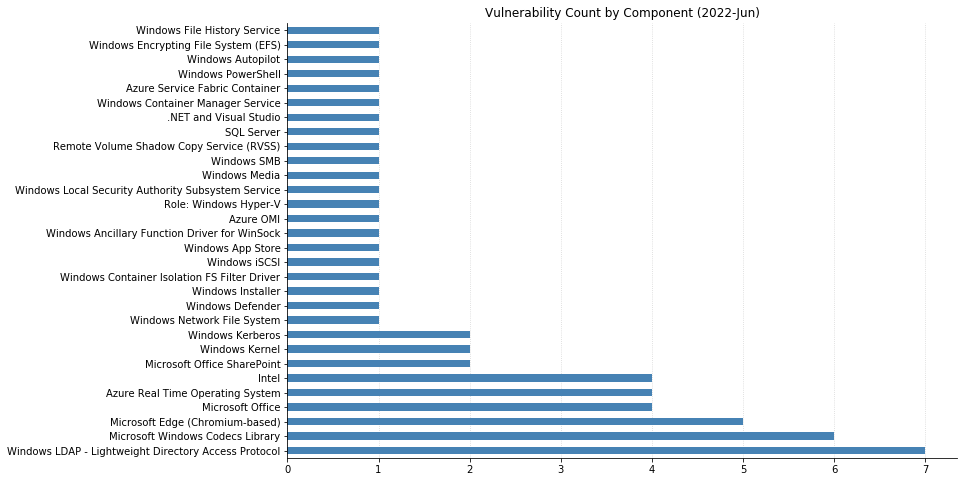
Summary charts
Summary tables
Apps vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-30168 | Microsoft Photos App Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-30137 | Azure Service Fabric Container Elevation of Privilege Vulnerability | No | No | 6.7 | Yes |
| CVE-2022-30177 | Azure RTOS GUIX Studio Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-30178 | Azure RTOS GUIX Studio Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-30179 | Azure RTOS GUIX Studio Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-30180 | Azure RTOS GUIX Studio Information Disclosure Vulnerability | No | No | 7.8 | Yes |
Azure System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-29149 | Azure Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability | No | No | 7.8 | Yes |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-22021 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | No | No | 8.3 | Yes |
| CVE-2022-2011 | Chromium: CVE-2022-2011 Use after free in ANGLE | No | No | N/A | Yes |
| CVE-2022-2010 | Chromium: CVE-2022-2010 Out of bounds read in compositing | No | No | N/A | Yes |
| CVE-2022-2008 | Chromium: CVE-2022-2008 Out of bounds memory access in WebGL | No | No | N/A | Yes |
| CVE-2022-2007 | Chromium: CVE-2022-2007 Use after free in WebGPU | No | No | N/A | Yes |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-30184 | .NET and Visual Studio Information Disclosure Vulnerability | No | No | 5.5 | Yes |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-30140 | Windows iSCSI Discovery Service Remote Code Execution Vulnerability | No | No | 7.1 | Yes |
| CVE-2022-30152 | Windows Network Address Translation (NAT) Denial of Service Vulnerability | No | No | 7.5 | No |
| CVE-2022-30135 | Windows Media Center Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2022-30153 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 8.8 | Yes |
| CVE-2022-30161 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 8.8 | Yes |
| CVE-2022-30141 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 8.1 | Yes |
| CVE-2022-30143 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 7.5 | Yes |
| CVE-2022-30149 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 7.5 | Yes |
| CVE-2022-30146 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 7.5 | Yes |
| CVE-2022-30155 | Windows Kernel Denial of Service Vulnerability | No | No | 5.5 | Yes |
| CVE-2022-30147 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2022-30163 | Windows Hyper-V Remote Code Execution Vulnerability | No | No | 8.5 | Yes |
| CVE-2022-30142 | Windows File History Remote Code Execution Vulnerability | No | No | 7.1 | Yes |
| CVE-2022-30151 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 | Yes |
| CVE-2022-30160 | Windows Advanced Local Procedure Call Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2022-30166 | Local Security Authority Subsystem Service Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2022-21166 | Intel: CVE-2022-21166 Device Register Partial Write (DRPW) | No | No | N/A | Yes |
| CVE-2022-21127 | Intel: CVE-2022-21127 Special Register Buffer Data Sampling Update (SRBDS Update) | No | No | N/A | Yes |
| CVE-2022-21125 | Intel: CVE-2022-21125 Shared Buffers Data Sampling (SBDS) | No | No | N/A | Yes |
| CVE-2022-21123 | Intel: CVE-2022-21123 Shared Buffers Data Read (SBDR) | No | No | N/A | Yes |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-30157 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 | Yes |
| CVE-2022-30158 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 | Yes |
| CVE-2022-30174 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.4 | Yes |
| CVE-2022-30159 | Microsoft Office Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2022-30171 | Microsoft Office Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2022-30172 | Microsoft Office Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2022-30173 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
SQL Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-29143 | Microsoft SQL Server Remote Code Execution Vulnerability | No | No | 7.5 | Yes |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score | Has FAQ? |
|---|
| CVE-2022-32230 | Windows SMB Denial of Service Vulnerability | No | No | N/A | Yes |
| CVE-2022-30136 | Windows Network File System Remote Code Execution Vulnerability | No | No | 9.8 | Yes |
| CVE-2022-30139 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 7.5 | Yes |
| CVE-2022-30162 | Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2022-30165 | Windows Kerberos Elevation of Privilege Vulnerability | No | No | 8.8 | Yes |
| CVE-2022-30145 | Windows Encrypting File System (EFS) Remote Code Execution Vulnerability | No | No | 7.5 | Yes |
| CVE-2022-30148 | Windows Desired State Configuration (DSC) Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2022-30150 | Windows Defender Remote Credential Guard Elevation of Privilege Vulnerability | No | No | 7.5 | Yes |
| CVE-2022-30132 | Windows Container Manager Service Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2022-30131 | Windows Container Isolation FS Filter Driver Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2022-30189 | Windows Autopilot Device Management and Enrollment Client Spoofing Vulnerability | No | No | 6.5 | Yes |
| CVE-2022-30154 | Microsoft File Server Shadow Copy Agent Service (RVSS) Elevation of Privilege Vulnerability | No | No | 5.3 | Yes |
| CVE-2022-30164 | Kerberos AppContainer Security Feature Bypass Vulnerability | No | No | 8.4 | Yes |
| CVE-2022-29111 | HEVC Video Extensions Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-22018 | HEVC Video Extensions Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-30188 | HEVC Video Extensions Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-29119 | HEVC Video Extensions Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-30167 | AV1 Video Extension Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2022-30193 | AV1 Video Extension Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
SubscribeAdditional reading: