A recently published ESG research ebook, sponsored by Rapid7, SOC Modernization and the Role of XDR, shows that organizations are increasingly leveraging security orchestration, automation, and response (SOAR) systems in an attempt to keep up with their security operations challenges. This makes sense, as every organization is facing the combined pressure of the growing threat landscape, expanding attack surface, and the cybersecurity skills shortage. To address these challenges, 88% of organizations report that they plan to increase their spending on security operations with the specific goal of better operationalizing threat intelligence, leveraging asset data in their SOC, improving their alert prioritization, and better measuring and improving their KPIs. All of these initiatives fall squarely into the purpose and value of SOAR.
In the same research, ESG also uncovered both praise and challenges for SOAR systems. On the praise side, there is very broad agreement that SOAR tools are effective for automating both complex and basic security operations tasks. But on the challenges side, the same respondents report unexpectedly high complexity and demands on programming and scripting skills that are getting in the way of SOAR-enabled value realization.
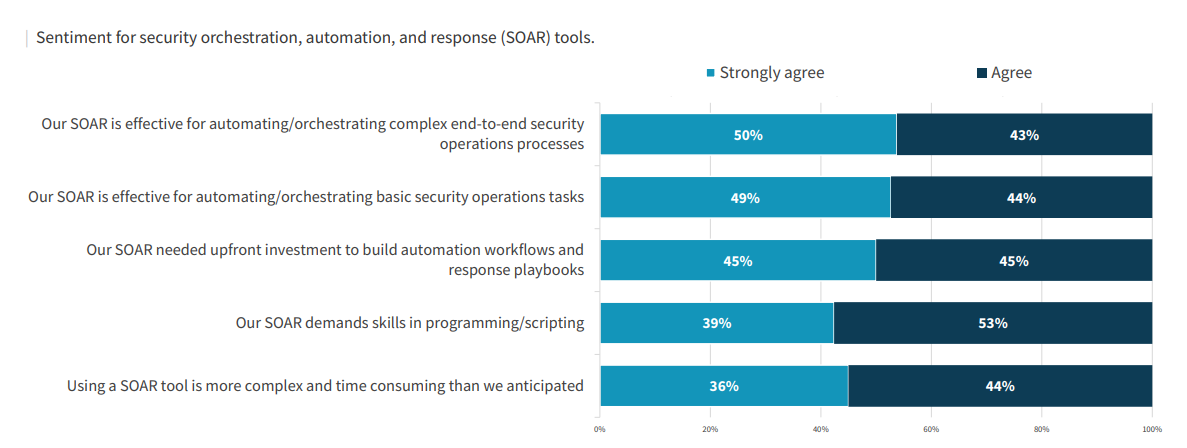
The SOC Modernization and the Role of XDR ebook, my years in the security industry, and my last year heavily focused on security operations and SOAR bring to mind five common SOAR myths worth debunking.
Myth #1: SOAR-enabled security automation is about eliminating security analysts
Security professionals, you can put away your wooden shoes (Sabot). There is no risk of job losses resulting from the use of SOAR tools. While in some cases, security tasks can be fully automated away, in the vast majority of SOAR-enabled automations, the value of SOAR is in teeing up the information necessary for security analysts to make good decisions and to leverage downstream integrations necessary to execute those decisions.
If you love manually collecting data from multiple internal and external sources necessary to make an informed decision and then manually opening tickets in IT service management systems or opening admin screens in various security controls to execute those decisions, stay away from using SOAR! Want to hear directly from an organization regarding this myth? Check out this Brooks case study and a supporting blog. The point of SOAR is to elevate your existing security professionals, not eliminate them.
Myth #2: SOAR requires programming skills
While SOARs require programming logic, they don’t generally require programming skills. If you know what process, data, decision points, and steps you need to get the job done, a SOAR system is designed to elevate the implementer of these processes out of the weeds of integrations and code-level logic steps necessary to get the job done.
The purpose of a well-designed SOAR is to elevate the security analyst out of the code and into the logic of their security operations. This is why a SOAR is not a general-purpose automation tool but is specifically designed and integrated to aid in the management and automation of tasks specific to security operations. Programming skills are not a prerequisite for getting value from a SOAR tool.
Myth #3: SOAR is only for incident response
While clearly the origin story of SOAR is closely connected to incident response (IR) and security operations centers (SOCs), it is a myth that SOARs are exclusively used to manage and automate IR-related processes. While responding effectively and quickly to incidents is critical, preparing your IT environment well through timely and efficient vulnerability management processes is equally important to the risk posture of the organization.
We see here at Rapid7 that just as many vulnerability management use cases are enabled with our SOAR solution, as are incident response ones.
Myth #4: You must re-engineer your security processes before adopting SOAR
Some organizations get caught in a security catch-22. They are too busy with manual security tasks to apply automation to help reduce the time necessary to conduct these security tasks. This is a corollary to the problem of being too busy working to do any work. The beauty of SOAR solutions is that you don’t have to know exactly what your security processes need to be before using a SOAR. Fortunately, thousands of your peer organizations have been working on hundreds of these security processes for many years.
Why create from scratch when you can just borrow what has already been crowdsourced? Many SOAR users freely publish what they consider to be the best practice security process automations for the various security incidents and vulnerabilities that you will likely encounter. SOAR vendors, such as Rapid7, curate and host hundreds of pre-built automations that you can study and grab for free to apply (and customize as appropriate) to your organization. These crowdsourced libraries mean that you do not need to start your security automation projects with a blank sheet of paper.
Myth #5: SOAR tools are not needed if you use managed security service providers
There is no question that managed security service providers in general and managed detection and response (MDR) providers – such as Rapid7 – in particular can deliver critical security value to organizations. In fact, in the same ESG research, 88% of organizations reported that they would increase their use of managed services for security operations moving forward. The economic value of an MDR service like Rapid7’s was demonstrated in a newly published Forrester TEI report. But what happens to SOAR when you leverage an MDR provider?
The reality is that managed providers complement and extend your security teams and thus don’t fully replace them. While managed providers can and do automate aspects of your security operations – most typically detections and investigations – rarely are they given full reign to make changes in your IT and security systems or to drive responses directly into your organization. They provide well-vetted recommendations, and you, the staff security professionals, decide how and when best to implement those recommendations. This is where SOAR comes in, doing what it does best: helping you manage and automate the execution of those recommendations. In fact, debunking the myth, SOAR tools can directly complement and extend the value of managed security service providers.
Clearly, there is no shortage of things to do and improve in most organizations to bend the security curve in favor of the good guys. My hope is that this latest research from ESG and the SOAR myth-busting in this blog will help you and your organization bend the security curve in your favor.
Additional reading:
- Simplify SIEM Optimization With InsightIDR
- 4 Key Statistics to Build a Business Case for an MDR Partner
- Gimme! Gimme! Gimme! (More Data): What Security Pros Are Saying
- Today’s SOC Strategies Will Soon Be Inadequate
