Rapid7 Strengthens Market Position With 360-Degree XDR and Best-in-Class Threat Intelligence Offerings
Time flies… and provides opportunities to establish proof points. After recently passing the one-year milestone of Rapid7’s acquisition of IntSights, the added value threat intelligence brings to our product portfolio is unmistakable.
Cross-platform SIEM, SOAR, and VM integrations expand capabilities and deliver super-charged XDR
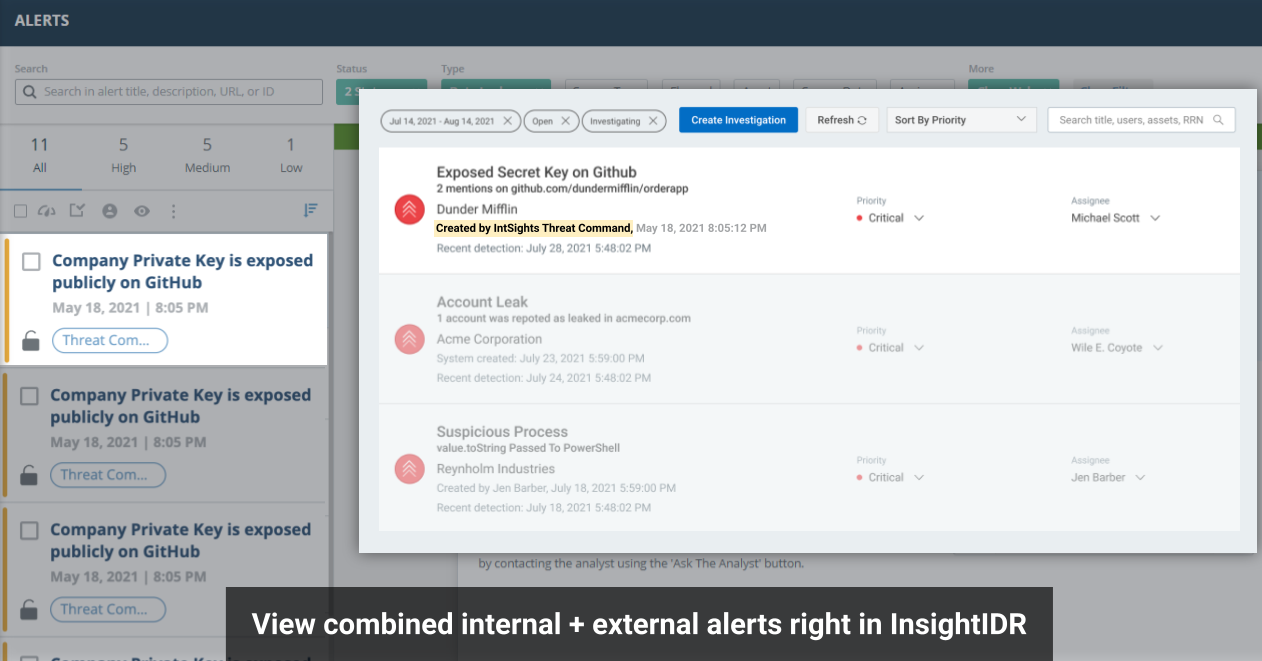
Integrations with Rapid7 InsightIDR (SIEM) and InsightConnect (SOAR) strengthen our product offerings. Infusing these tools with threat intelligence elevates customer security outcomes and delivers greater visibility across applications, while speeding response times. The combination of expertly vetted detections, contextual intelligence, and automated workflows within the security operations center (SOC) helps teams gain immediate visibility into the external attack surface from within their SIEM environments.
The threat intelligence integration with IDR is unique to Rapid7. It's the only XDR solution in the market to infuse both generic threat intelligence IOCs and customized digital risk protection coverage. Users receive contextual, tailored alerts based on their digital assets, enabling them to detect potential threats before they hit endpoints and become incident response cases.
Capabilities
- Expand and accelerate threat detection with native integration of Threat Command alerts and TIP Threat Library IOCs with InsightIDR.
- Proactively thwart attack plans with alerts that identify active threats across the attack surface.
Benefits
- 360-degree visibility and protection across your internal and external attack surface
- Faster automated discovery and elimination of threats via correlation of Threat Command alerts with InsightIDR investigative capabilities
Learn more: 360-Degree XDR and Attack Surface Coverage, XDR Solution Brief

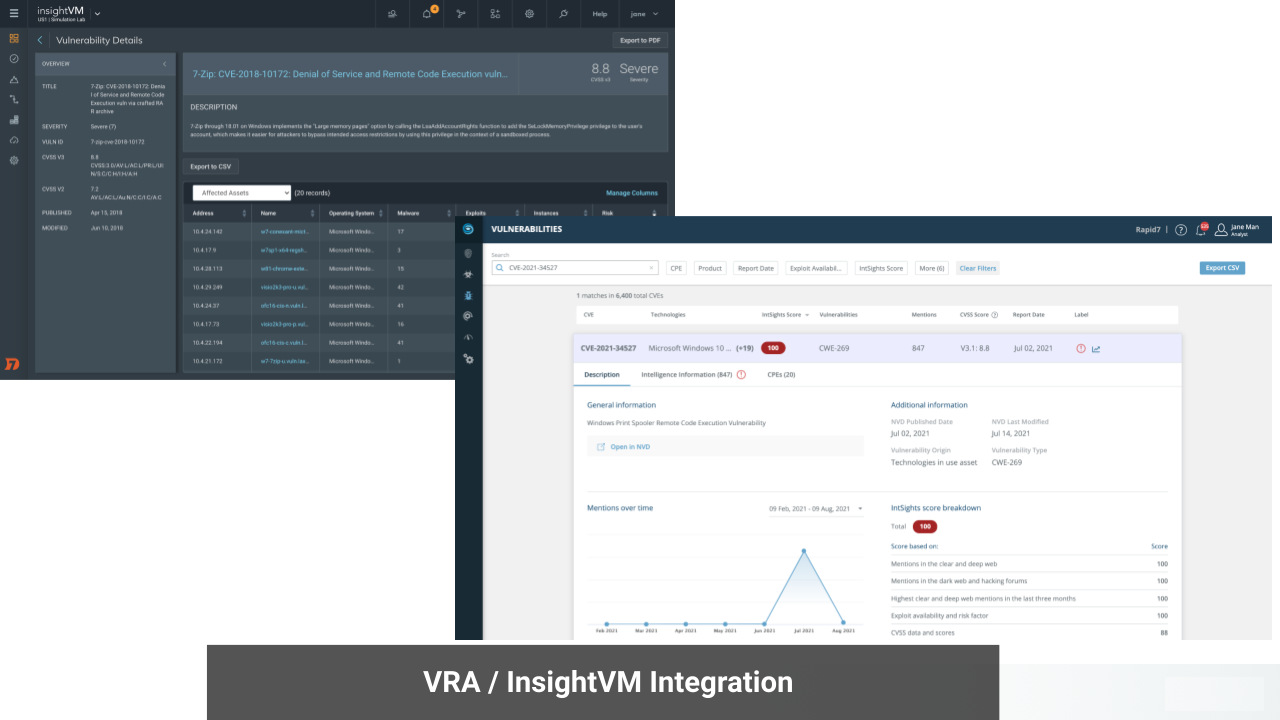
The Threat Command Vulnerability Risk Analyzer (VRA) + InsightVM integration delivers complete visibility into digital assets and vulnerabilities across your attack surface, including attacker perspective, trends, and active discussions and exploits. Joint customers can import data from InsightVM into their VRA environment where CVEs are enriched with valuable context and prioritized by vulnerability criticality and risk, eliminating the guesswork of manual patch management. VRA is a bridge connecting objective critical data with contextualized threat intelligence derived from tactical observations and deep research. In addition to VRA, customers can leverage Threat Command’s Browser Extension to obtain additional context on CVEs, and TIP module to see related IOCs and block actively exploited vulnerabilities.
Integration benefits
- Visibility: Continuously monitor assets and associated vulnerabilities.
- Speed: Instantly assess risk from emerging vulnerabilities and improve patching cadence.
- Assessment: Eliminate blind spots with enhanced vulnerability coverage.
- Productivity: Reduce time security analysts spend searching for threats by 75% or more.
- Prioritization: Focus on the vulnerabilities that matter most.
- Automation: Integrate CVEs enriched with threat intelligence into existing security stack.
- Simplification: Rely on intuitive dashboards for centralized vulnerability management.
Learn how to leverage this integration to effectively prioritize and accelerate vulnerability remediation in this short demo and Integration Solution Brief.
In addition to these game-changing integrations that infuse Rapid7 Insight Platform solutions with external threat intelligence, Threat Command also introduced numerous feature and platform enhancements during the past several months.
Expanded detections and reduced noise
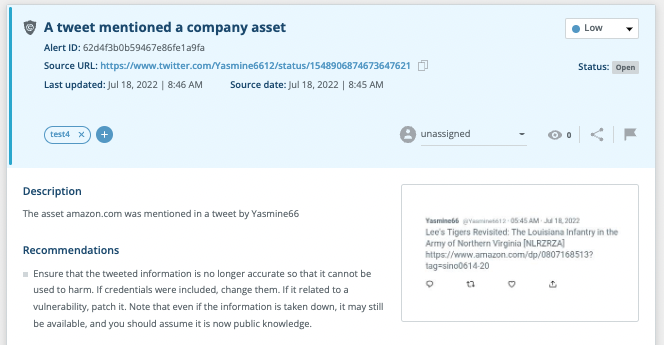
Of all mainstream social media platforms, Twitter has the fewest restrictions and regulations; coupled with maximum anonymity, this makes the service a breeding ground for hostile discourse.
Twitter by the numbers (in 2021)

Threat Command Twitter Chatter coverage continually monitors Twitter discourse and alerts customers regarding mentions of company domains. Expanded Twitter coverage later this year will include company and brand names.
Threat Command’s Information Stealers feature expands the platform’s botnets credentials coverage. We now detect and alert on information-stealing malware that gathered leaked credentials and private data from infected devices. Customers are alerted when employees or users have been compromised (via corporate email, website, or mobile app). Rely on extended protection against this prevalent and growing malware threat based on our unique ability to obtain compromised data via our exclusive access to threat actors.
Accelerated time to value
The recently enhanced Threat Command Asset Management dashboard provides visibility into the risk associated with specific assets, displays asset targeting trends, and enables drill-down for alert investigation. Users can now categorize assets using tags and comments, generate bulk actions for multiple assets, and see a historical perspective of all activity related to specific assets.
Better visibility for faster decisions
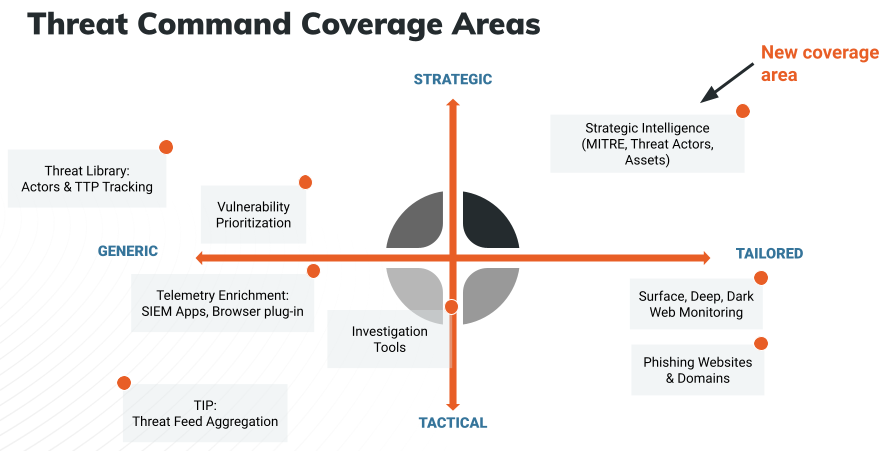
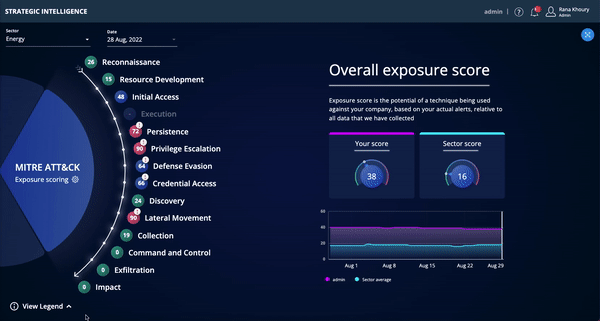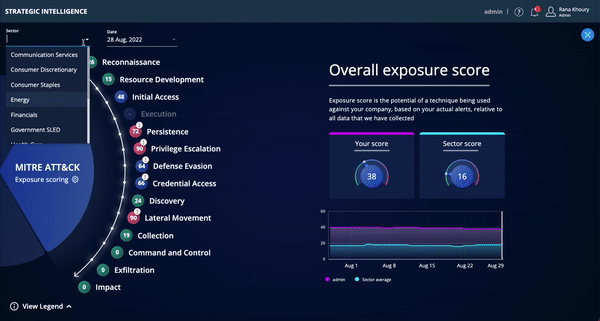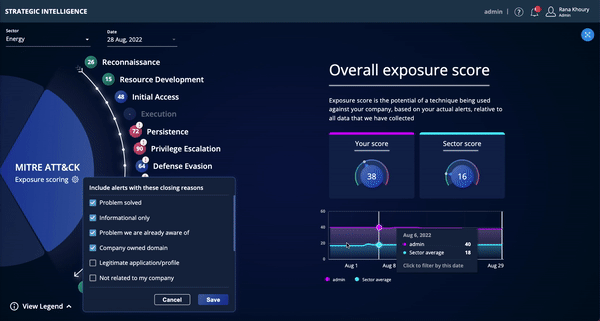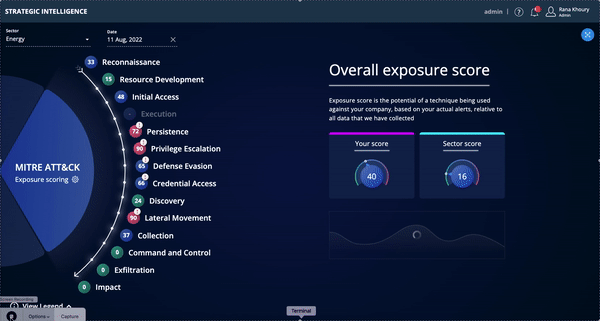
Strategic Intelligence is now available to existing Threat Command customers for a limited time in Open Preview mode. The Strategic Intelligence dashboard, aligned to the MITRE ATT&CK framework, enables CISOs and other security executives to track risk over time and assess, plan, and budget for future security investments.
Capabilities
- View potential vulnerabilities attackers may use to execute an attack – aligned to the MITRE ATT&CK framework (tactics & techniques).
- See trends in your external attack surface and track progress over time in exposed areas.
- Benchmark your exposure relative to other Threat Command customers in your sector/vertical.
- Easily communicate gaps and trends to management via dashboard and/or reports.
Benefits
- Rapid7 is the first vendor in the TI space to provide a comprehensive strategic view of an organization's external threat landscape.
- Achieve your security goals with complete, forward-looking, and actionable intelligence context about your external assets.
- Bridge the communication and reporting gap between your CTI analysts dealing with everyday threats and the CISO, focused on the bigger picture.
Stay tuned!
There are many more exciting feature enhancements and new releases planned by year end.
Learn more about how Threat Command simplifies threat intelligence, delivering instant value for organizations of any size or maturity, while reducing risk exposure.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
SubscribeAdditional reading: