It’s June, and it’s Patch Tuesday. The volume of fixes this month is typical compared with recent history: 94 in total (including Edge-on-Chromium). For the first time in a while, Microsoft isn’t offering patches for any zero-day vulnerabilities, but we do get fixes for four critical Remote Code Execution (RCE) vulnerabilities: one in .NET/Visual Studio, and three in Windows Pragmatic General Multicast (PGM). Also patched: a critical SharePoint Elevation of Privilege vulnerability.
SharePoint: Critical EoP via JWT spoofing
SharePoint administrators should start by looking at critical Elevation of Privilege vulnerability CVE-2023-29357, which provides attackers with a chance at Administrator privileges on the SharePoint host, provided they come prepared with spoofed JWT tokens. Microsoft isn’t aware of public disclosure or in-the-wild exploitation, but considers exploitation more likely.
The FAQ provided with Microsoft’s advisory suggests that both SharePoint Enterprise Server 2016 and SharePoint Server 2019 are vulnerable. So far so good for SharePoint 2019, but there is a lack of clarity around a patch for SharePoint 2016.
Initially, neither the advisory nor the SharePoint 2016 Release history listed a relevant patch for SharePoint 2016. Microsoft has since updated both the SharePoint 2016 release history to include a link to the June security update for SharePoint Enterprise Server 2016; however, the link incorrectly points to the May advisory, and should instead point to the June 2023 security update for SharePoint 2016 KB5002404.
Complicating matters further, KB5002404 does not mention CVE-2023-29357, and the advisory for CVE-2023-29357 still does not mention any patch for SharePoint 2016. Defenders responsible for SharePoint 2016 will no doubt wish to follow developments here closely; on present evidence, the only safe assumption is that there is no patch yet which addresses CVE-2023-29357 for SharePoint 2016.
Microsoft also mentions that there may be more than one patch listed for a particular version of SharePoint, and that every patch for a particular version of SharePoint must be installed to remediate this vulnerability (although order of patching doesn’t matter).
Windows PGM: Critical RCE
This is the third month in a row where Patch Tuesday features at least one critical RCE in Windows PGM, and June adds three to the pile. Microsoft hasn’t detected exploitation or disclosure for any of these, and considers exploitation less likely, but a trio of critical RCEs with CVSS 3.1 base score of 9.8 will deservedly attract a degree of attention.
All three PGM critical RCEs – CVE-2023-29363, CVE-2023-32014, and CVE-2023-32015 – require an attacker to send a specially-crafted file over the network in the hope of executing malicious code on the target asset. Defenders who successfully navigated last month’s batch of PGM vulnerabilities will find both risk profile and mitigation/remediation guidance very similar; indeed, CVE-2023-29363 was reported to Microsoft by the same researcher as last month’s CVE-2023-28250.
As with previous similar vulnerabilities, Windows Message Queueing Service (MSMQ) must be enabled for an asset to be exploitable, and MSMQ isn’t enabled by default. As Rapid7 has noted previously, however, a number of applications – including Microsoft Exchange – quietly introduce MSMQ as part of their own installation routine. With several prolific researchers active in this area, we should expect further PGM vulnerabilities in the future.
.NET & Visual Studio: Critical RCE
Rounding out this month’s critical RCE list is CVE-2023-24897: a flaw in .NET, .NET Framework and Visual Studio. Exploitation requires an attacker to convince the victim to open a specially-crafted malicious file, typically from a website.
Although Microsoft has no knowledge of public disclosure or exploitation in the wild, and considers exploitation less likely, the long list of patches – going back as far as .NET Framework 3.5 on Windows 10 1607 – means that this vulnerability has been present for years. Somewhat unusually for this class of vulnerability, Microsoft doesn’t give any indication of filetype. However, the Arbitrary Code Execution (ACE) boilerplate qualifier is present: “remote” refers here to the location of the attacker, rather than the attack, since local user interaction is required.
Exchange: Important RCEs; Exploitation More Likely
After a brief reprieve last month, Exchange admins will want to patch a pair of RCE vulnerabilities this month. While neither CVE-2023-28310 nor CVE-2023-32031 quite manages to rank as critical vulnerabilities, either via CVSSv3 base score, or via Microsoft’s proprietary severity scale, they’re not far off. Only the requirement that the attacker has previously achieved an authenticated role on the Exchange server prevents these vulnerabilities from scoring higher – but that’s just the sort of issue that exploit chains are designed to overcome.
Microsoft expects to see exploitation for both of these vulnerabilities. Successful exploitation will make use of PowerShell remoting sessions to achieve remote code execution.
Azure DevOps: spoofing, information disclosure
A vulnerability in Azure DevOps server could lead to an attacker accessing detailed data such as organization/project configuration, groups, teams, projects, pipelines, boards, and wiki. CVE-2023-21565 requires an attacker to have existing valid credentials for the service, but no elevated privilege is required. The advisory lists patches for 2020.1.2, 2022 and 2022.0.1.
Summary Charts
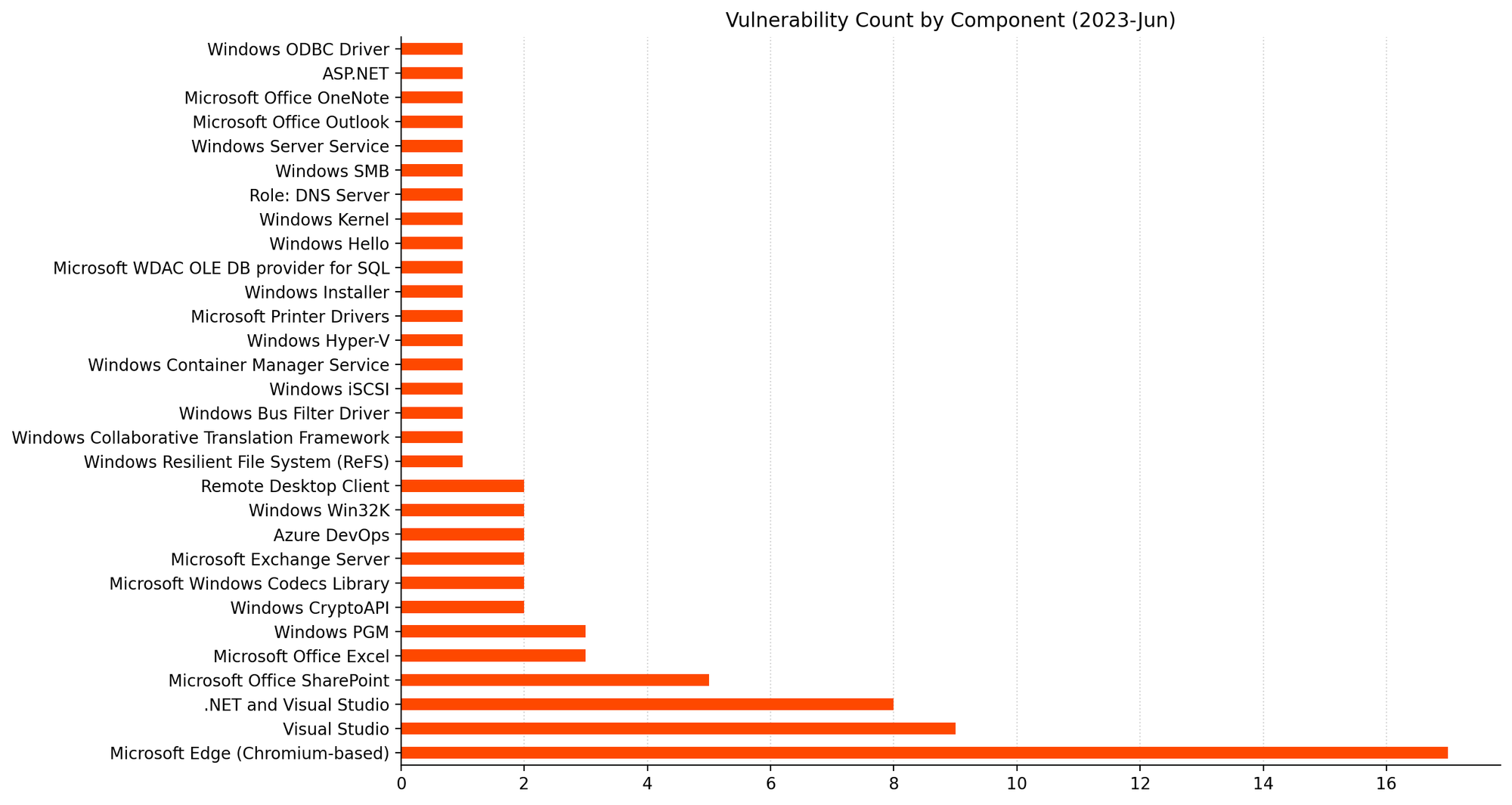
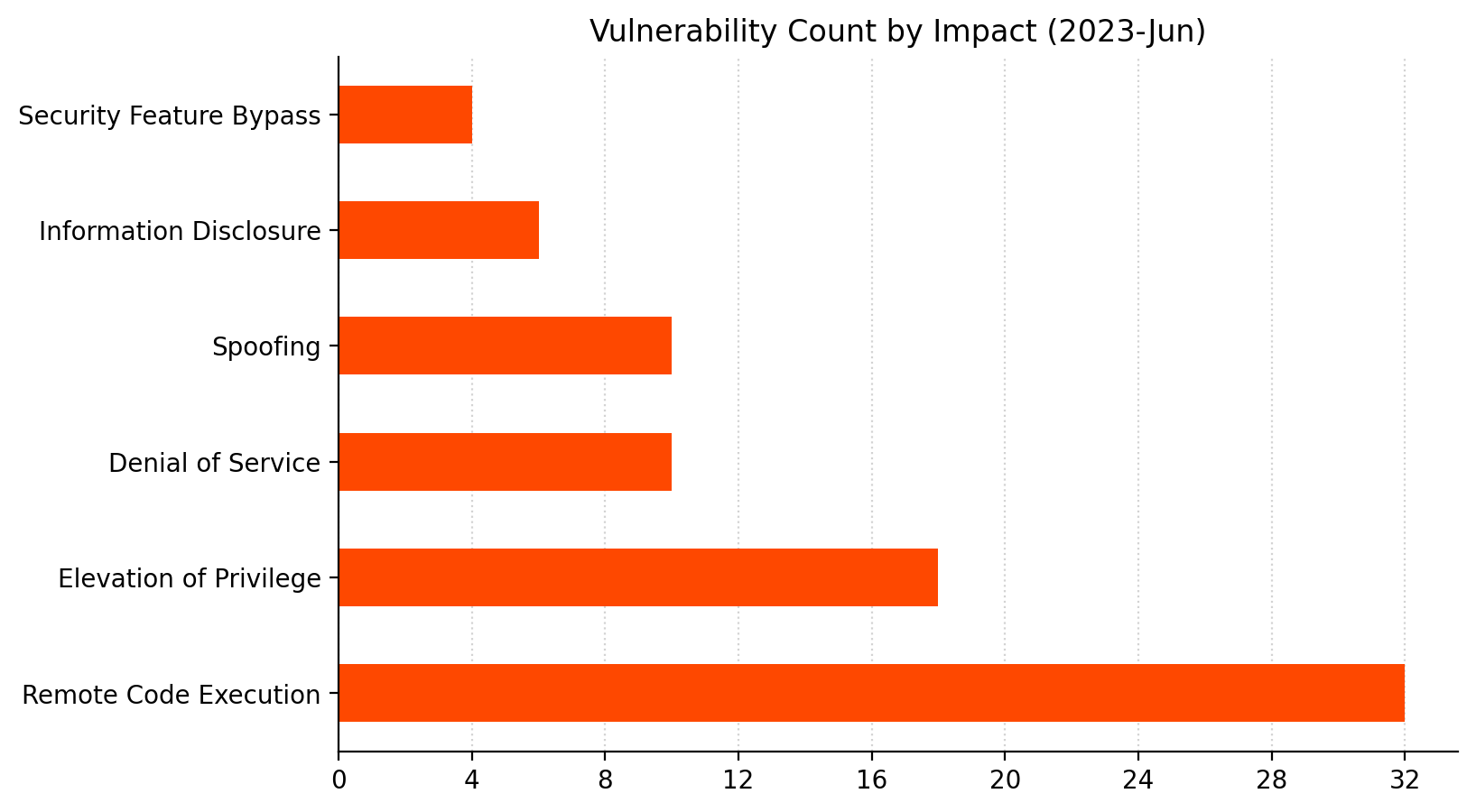
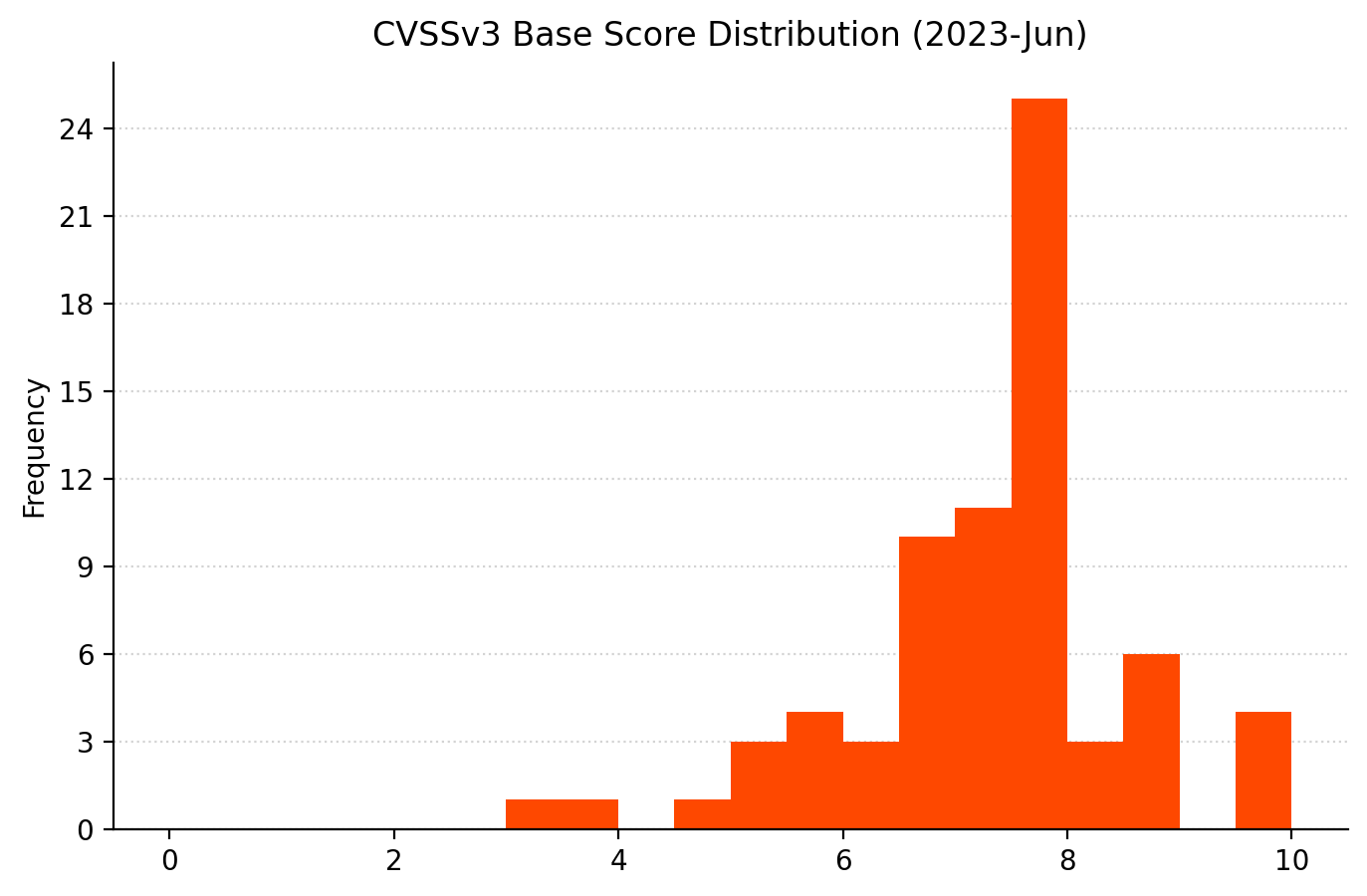
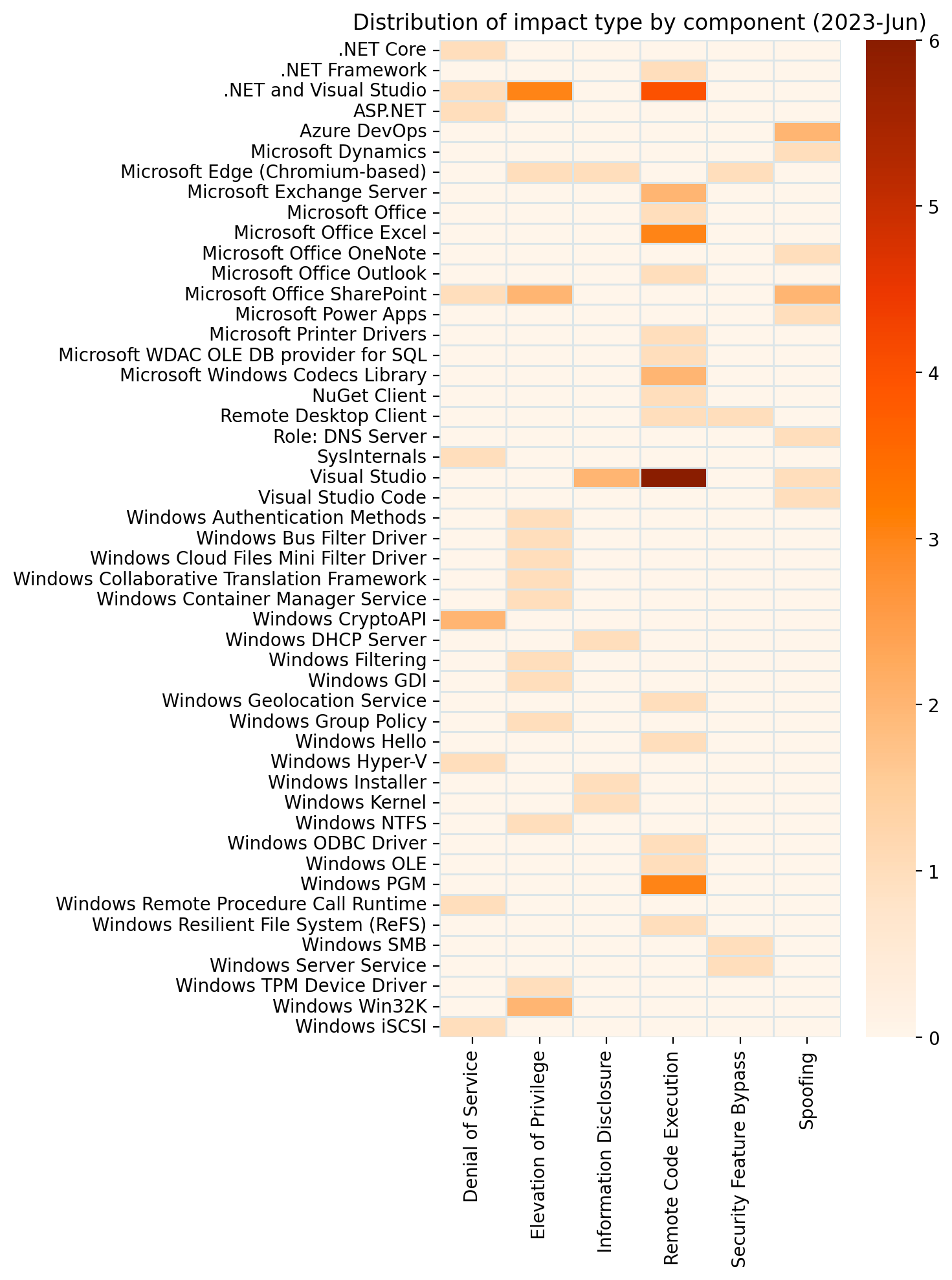
Summary Tables
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-33143 | Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability | No | No | 7.5 |
| CVE-2023-33145 | Microsoft Edge (Chromium-based) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-29345 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability | No | No | 6.1 |
| CVE-2023-3079 | Chromium: CVE-2023-3079 Type Confusion in V8 | No | No | N/A |
| CVE-2023-2941 | Chromium: CVE-2023-2941 Inappropriate implementation in Extensions API | No | No | N/A |
| CVE-2023-2940 | Chromium: CVE-2023-2940 Inappropriate implementation in Downloads | No | No | N/A |
| CVE-2023-2939 | Chromium: CVE-2023-2939 Insufficient data validation in Installer | No | No | N/A |
| CVE-2023-2938 | Chromium: CVE-2023-2938 Inappropriate implementation in Picture In Picture | No | No | N/A |
| CVE-2023-2937 | Chromium: CVE-2023-2937 Inappropriate implementation in Picture In Picture | No | No | N/A |
| CVE-2023-2936 | Chromium: CVE-2023-2936 Type Confusion in V8 | No | No | N/A |
| CVE-2023-2935 | Chromium: CVE-2023-2935 Type Confusion in V8 | No | No | N/A |
| CVE-2023-2934 | Chromium: CVE-2023-2934 Out of bounds memory access in Mojo | No | No | N/A |
| CVE-2023-2933 | Chromium: CVE-2023-2933 Use after free in PDF | No | No | N/A |
| CVE-2023-2932 | Chromium: CVE-2023-2932 Use after free in PDF | No | No | N/A |
| CVE-2023-2931 | Chromium: CVE-2023-2931 Use after free in PDF | No | No | N/A |
| CVE-2023-2930 | Chromium: CVE-2023-2930 Use after free in Extensions | No | No | N/A |
| CVE-2023-2929 | Chromium: CVE-2023-2929 Out of bounds write in Swiftshader | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-24936 | .NET, .NET Framework, and Visual Studio Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2023-24897 | .NET, .NET Framework, and Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-24895 | .NET, .NET Framework, and Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-29326 | .NET Framework Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33141 | Yet Another Reverse Proxy (YARP) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-29331 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-32030 | .NET and Visual Studio Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-33126 | .NET and Visual Studio Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-33128 | .NET and Visual Studio Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-33135 | .NET and Visual Studio Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2023-29337 | NuGet Client Remote Code Execution Vulnerability | No | No | 7.1 |
| CVE-2023-32032 | .NET and Visual Studio Elevation of Privilege Vulnerability | No | No | 6.5 |
| CVE-2023-33139 | Visual Studio Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-29353 | Sysinternals Process Monitor for Windows Denial of Service Vulnerability | No | No | 5.5 |
| CVE-2023-33144 | Visual Studio Code Spoofing Vulnerability | No | No | 5 |
| CVE-2023-29012 | GitHub: CVE-2023-29012 Git CMD erroneously executes doskey.exe in current directory, if it exists | No | No | N/A |
| CVE-2023-29011 | GitHub: CVE-2023-29011 The config file of connect.exe is susceptible to malicious placing | No | No | N/A |
| CVE-2023-29007 | GitHub: CVE-2023-29007 Arbitrary configuration injection via git submodule deinit | No | No | N/A |
| CVE-2023-25815 | GitHub: CVE-2023-25815 Git looks for localized messages in an unprivileged place | No | No | N/A |
| CVE-2023-25652 | GitHub: CVE-2023-25652 "git apply --reject" partially-controlled arbitrary file write | No | No | N/A |
| CVE-2023-27911 | AutoDesk: CVE-2023-27911 Heap buffer overflow vulnerability in Autodesk® FBX® SDK 2020 or prior | No | No | N/A |
| CVE-2023-27910 | AutoDesk: CVE-2023-27910 stack buffer overflow vulnerability in Autodesk® FBX® SDK 2020 or prior | No | No | N/A |
| CVE-2023-27909 | AutoDesk: CVE-2023-27909 Out-Of-Bounds Write Vulnerability in Autodesk® FBX® SDK 2020 or prior | No | No | N/A |
Developer Tools Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21565 | Azure DevOps Server Spoofing Vulnerability | No | No | 7.1 |
| CVE-2023-21569 | Azure DevOps Server Spoofing Vulnerability | No | No | 5.5 |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-29363 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-32014 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-32015 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-29362 | Remote Desktop Client Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-29372 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-29373 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-29351 | Windows Group Policy Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2023-29365 | Windows Media Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-29358 | Windows GDI Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-29371 | Windows GDI Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-29346 | NTFS Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-32017 | Microsoft PostScript Printer Driver Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-29359 | GDI Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-32011 | Windows iSCSI Discovery Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-29368 | Windows Filtering Platform Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-29364 | Windows Authentication Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-32016 | Windows Installer Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-32020 | Windows DNS Spoofing Vulnerability | No | No | 3.7 |
Exchange Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-32031 | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-28310 | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-24896 | Dynamics 365 Finance Spoofing Vulnerability | No | No | 5.4 |
| CVE-2023-32024 | Microsoft Power Apps Spoofing Vulnerability | No | No | 3 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-29357 | Microsoft SharePoint Server Elevation of Privilege Vulnerability | No | No | 9.8 |
| CVE-2023-33131 | Microsoft Outlook Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-33146 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-32029 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33137 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33133 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33130 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 7.3 |
| CVE-2023-33142 | Microsoft SharePoint Server Elevation of Privilege Vulnerability | No | No | 6.5 |
| CVE-2023-33129 | Microsoft SharePoint Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-33140 | Microsoft OneNote Spoofing Vulnerability | No | No | 6.5 |
| CVE-2023-33132 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 6.3 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-32009 | Windows Collaborative Translation Framework Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-29367 | iSCSI Target WMI Provider Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-29360 | Windows TPM Device Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-32008 | Windows Resilient File System (ReFS) Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-29370 | Windows Media Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-32018 | Windows Hello Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-29366 | Windows Geolocation Service Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-32022 | Windows Server Service Security Feature Bypass Vulnerability | No | No | 7.6 |
| CVE-2023-32021 | Windows SMB Witness Service Security Feature Bypass Vulnerability | No | No | 7.1 |
| CVE-2023-29361 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-32010 | Windows Bus Filter Driver Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-29352 | Windows Remote Desktop Security Feature Bypass Vulnerability | No | No | 6.5 |
| CVE-2023-32013 | Windows Hyper-V Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-24937 | Windows CryptoAPI Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-24938 | Windows CryptoAPI Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-29369 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-32012 | Windows Container Manager Service Elevation of Privilege Vulnerability | No | No | 6.3 |
| CVE-2023-29355 | DHCP Server Service Information Disclosure Vulnerability | No | No | 5.3 |
| CVE-2023-32019 | Windows Kernel Information Disclosure Vulnerability | No | No | 4.7 |

