Microsoft is addressing 64 vulnerabilities this November Patch Tuesday, including five zero-day vulnerabilities as well as one critical remote code execution (RCE) vulnerability. Overall, this month sees significantly fewer vulnerabilities addressed across a smaller number of products than has been typical of Patch Tuesday over the past year or two. Browser vulnerabilities account for 20 of the 64 vulnerabilities patched, and 14 of those are republished third-party vulnerabilities in Chromium.
Three vulnerabilities patched today are already present on the CISA Known Exploited Vulnerabilities (KEV) list: CVE-2023-36025, CVE-2023-36033, and CVE-2023-36036.
Windows SmartScreen: zero-day bypass
CVE-2023-36025 describes a Windows SmartScreen security feature bypass. An attacker who convinces a user to open a specially crafted malicious Internet Shortcut file could bypass the anti-phishing and anti-malware protection provided by Windows SmartScreen. This could be abused as an early stage in a more complex attack chain.
Windows DWM: zero-day EoP
Originally introduced in Windows Vista, the Windows Dynamic Window Manager (DWM) enables many of the modern UI features which users have come to expect from a Windows OS. This month, the DWM Core Library receives a patch for CVE-2023-36033, an elevation of privilege (EoP) vulnerability which Microsoft notes is both publicly disclosed and exploited in the wild. Exploitation leads to SYSTEM privileges, but Microsoft does not provide any further guidance on the attack mechanism.
Windows Cloud Files mini driver: zero-day EoP
Microsoft is patching CVE-2023-36036, an EoP vulnerability in the Windows Cloud Files Mini Filter Driver. No details of the attack mechanism are provided in the advisory, but exploitation leads to SYSTEM privileges.
Office Protected View: zero-day bypass
CVE-2023-36413 describes a publicly disclosed Microsoft Office security feature bypass. A user who opens a specially crafted malicious file would find themselves in Editing mode, rather than Protected View, and would thus lose out on warning banners and other defenses designed to detect and quarantine malicious code in Office documents.
ASP.NET Core: zero-day DoS
CVE-2023-36038 describes an ASP.NET Core denial of service (DoS) attack, which affects only .NET 8 RC 1 running on the IIS InProcess hosting model. The mechanism of the attack is resource exhaustion on the web server via cancellation of requests; this sounds very similar to last month’s CVE-2023-44487, dubbed “Rapid Reset”. However, there’s no mention of HTTP/2 in the advisory for CVE-2023-36038.
Fewer critical vulns this month
Only three vulnerabilities patched this month qualify as Critical under Microsoft’s proprietary severity ranking scale: one each in Windows Pragmatic General Multicast (PGM), the Azure CLI, and Windows HMAC Key Derivation.
Windows PGM: critical RCE via MSMQ
CVE-2023-36397 describes an RCE vulnerability in Windows PGM. As with other similar previous vulnerabilities, an attacker can send a specially-crafted file over the network to attempt malicious code execution on the target asset. Only systems where Windows Message Queueing Service (MSMQ) is enabled are exploitable, and it isn’t added to a default Windows installation. However, as Rapid7 has noted previously, administrators should be aware that a number of applications — including Microsoft Exchange — quietly introduce MSMQ as part of their own installation routine.
Hyper-V: critical VM escape
Attackers looking to escape from a low privilege Hyper-V guest OS and execute code as SYSTEM on the Hyper-V host system will take note of CVE-2023-36400. Successful exploitation requires running a specially crafted application in the context of the guest OS to exploit a weakness in Windows HMAC Key Derivation, so some prior access is required.
Azure CLI: critical credential leak via log files
The Azure CLI tool prior to version 2.53.1 does not sufficiently redact information published to log files in certain contexts, allowing recovery of plaintext(!) usernames and passwords. The advisory for CVE-2023-36052 notes that log files stored in open-source repositories are a potential avenue for credential leaks in this context. Although Microsoft understandably hasn’t provided any specific examples, it’s unlikely that they would mention this if they weren’t aware of one or more real world examples.
Exchange: RCE, spoofing, and ZDI disclosures
Patch Tuesday typically sees at least one Exchange remote code execution vulnerability fixed, and this month is no exception. Exploitation of CVE-2023-36439 requires that the attacker have valid credentials for an Exchange user, and be present on the local network, but grants execution as NT AUTHORITY\SYSTEM on Exchange server host; this is a built-in account with extensive privileges, including the ability to act as the computer on the network.
A trio of Exchange server spoofing vulnerabilities — CVE-2023-36035 CVE-2023-36039 and CVE-2023-36050 — are also patched today. Successful exploitation requires that an attacker be present on the local network with valid Exchange credentials, but can lead to exposure of credentials or an NTLM hash for other users. Two of these vulnerabilities are exploited via PowerShell remoting.
Somewhat conspicuous by their absence: four flaws in Exchange published by Trend Micro’s Zero Day Initiative (ZDI) on 2023-11-02 do not appear to have received patches today. Microsoft had previously told ZDI that these vulnerabilities did not require immediate servicing. Since Microsoft is the CVE Numbering Authority (CNA) for its own products, there are no publicly available CVE numbers for these vulnerabilities yet.
cURL: patch for much-anticipated vuln
Microsoft admins who have been waiting for a patch for last month’s cURL SOCKS5 vulnerability CVE-2023-38545 will be pleased to see that Microsoft has included curl.exe 8.4.0 as part of the November updates for current versions of Windows. Many observers ultimately concluded that this vulnerability was perhaps of more limited scope and attacker value than the pre-publication buzz may have suggested, but a patch is always appreciated.
Is it 23H2 already?
A new arrival: Windows 11 23H2 was released on 2023-10-31 across all editions, and receives its first patches today.
Summary Charts
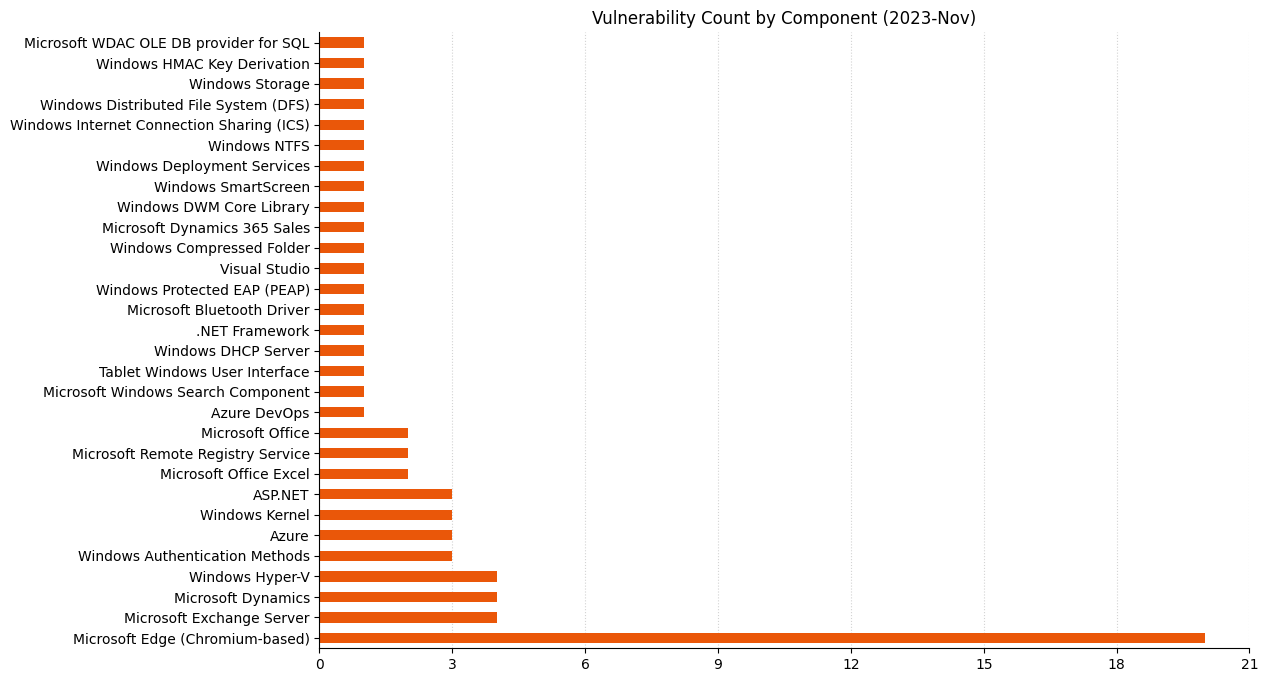
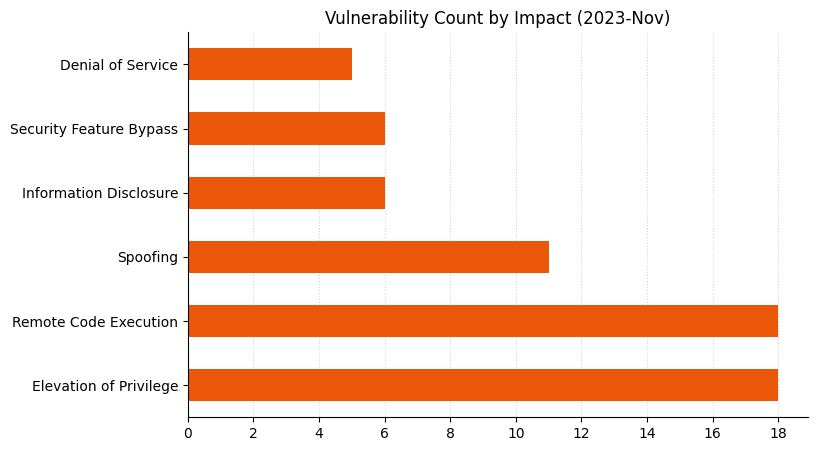
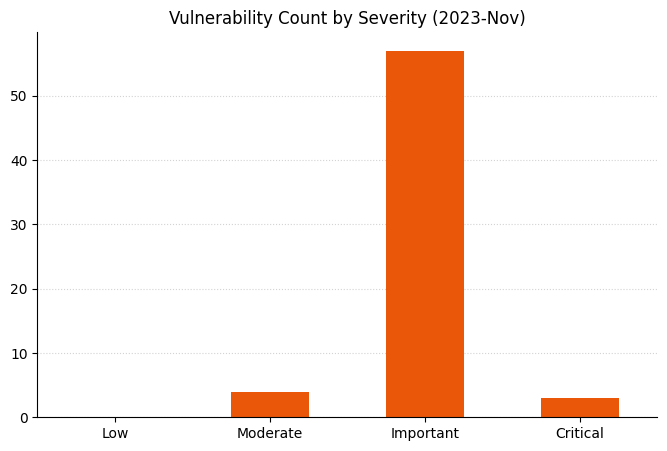
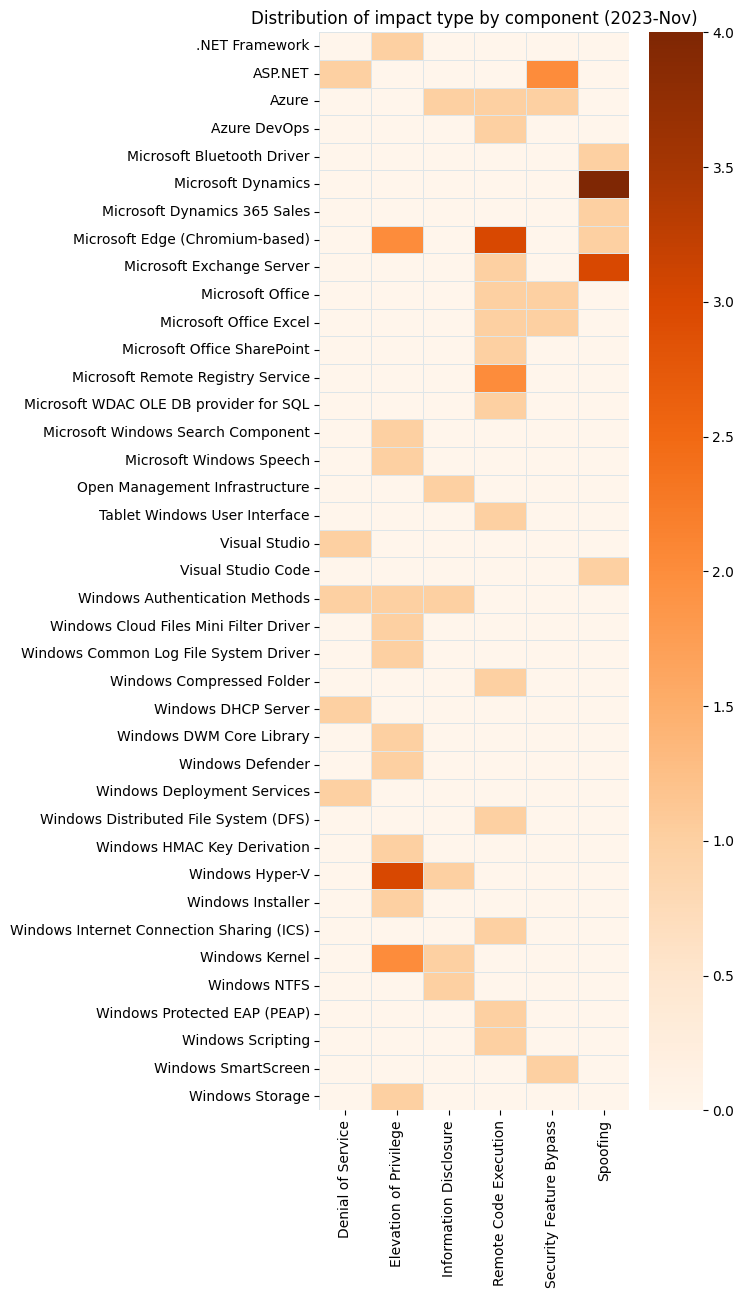
Summary Tables
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-38151 | Microsoft Host Integration Server 2020 Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-36437 | Azure DevOps Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-36052 | Azure CLI REST Command Information Disclosure Vulnerability | No | No | 8.6 |
| CVE-2023-36021 | Microsoft On-Prem Data Gateway Security Feature Bypass Vulnerability | No | No | 8 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36034 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36014 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36024 | Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-36027 | Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-36022 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-36029 | Microsoft Edge (Chromium-based) Spoofing Vulnerability | No | No | 4.3 |
| CVE-2023-5996 | Chromium: CVE-2023-5996 Use after free in WebAudio | No | No | N/A |
| CVE-2023-5859 | Chromium: CVE-2023-5859 Incorrect security UI in Picture In Picture | No | No | N/A |
| CVE-2023-5858 | Chromium: CVE-2023-5858 Inappropriate implementation in WebApp Provider | No | No | N/A |
| CVE-2023-5857 | Chromium: CVE-2023-5857 Inappropriate implementation in Downloads | No | No | N/A |
| CVE-2023-5856 | Chromium: CVE-2023-5856 Use after free in Side Panel | No | No | N/A |
| CVE-2023-5855 | Chromium: CVE-2023-5855 Use after free in Reading Mode | No | No | N/A |
| CVE-2023-5854 | Chromium: CVE-2023-5854 Use after free in Profiles | No | No | N/A |
| CVE-2023-5853 | Chromium: CVE-2023-5853 Incorrect security UI in Downloads | No | No | N/A |
| CVE-2023-5852 | Chromium: CVE-2023-5852 Use after free in Printing | No | No | N/A |
| CVE-2023-5851 | Chromium: CVE-2023-5851 Inappropriate implementation in Downloads | No | No | N/A |
| CVE-2023-5850 | Chromium: CVE-2023-5850 Incorrect security UI in Downloads | No | No | N/A |
| CVE-2023-5849 | Chromium: CVE-2023-5849 Integer overflow in USB | No | No | N/A |
| CVE-2023-5482 | Chromium: CVE-2023-5482 Insufficient data validation in USB | No | No | N/A |
| CVE-2023-5480 | Chromium: CVE-2023-5480 Inappropriate implementation in Payments | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36560 | ASP.NET Security Feature Bypass Vulnerability | No | No | 8.8 |
| CVE-2023-36038 | ASP.NET Core Denial of Service Vulnerability | No | Yes | 8.2 |
| CVE-2023-36018 | Visual Studio Code Jupyter Extension Spoofing Vulnerability | No | No | 7.8 |
| CVE-2023-36049 | .NET, .NET Framework, and Visual Studio Elevation of Privilege Vulnerability | No | No | 7.6 |
| CVE-2023-36042 | Visual Studio Denial of Service Vulnerability | No | No | 6.2 |
| CVE-2023-36558 | ASP.NET Core - Security Feature Bypass Vulnerability | No | No | 6.2 |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36397 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-36025 | Windows SmartScreen Security Feature Bypass Vulnerability | Yes | No | 8.8 |
| CVE-2023-36017 | Windows Scripting Engine Memory Corruption Vulnerability | No | No | 8.8 |
| CVE-2023-36402 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-36719 | Microsoft Speech Application Programming Interface (SAPI) Elevation of Privilege Vulnerability | No | No | 8.4 |
| CVE-2023-36425 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2023-36393 | Windows User Interface Application Core Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36705 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36424 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36036 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | Yes | No | 7.8 |
| CVE-2023-36395 | Windows Deployment Services Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36392 | DHCP Server Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36423 | Microsoft Remote Registry Service Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-36401 | Microsoft Remote Registry Service Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-36403 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36398 | Windows NTFS Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-36428 | Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability | No | No | 5.5 |
Exchange Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36050 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2023-36039 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2023-36035 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2023-36439 | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36007 | Microsoft Send Customer Voice survey from Dynamics 365 Spoofing Vulnerability | No | No | 7.6 |
| CVE-2023-36410 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 7.6 |
| CVE-2023-36031 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 7.6 |
| CVE-2023-36016 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 6.2 |
| CVE-2023-36030 | Microsoft Dynamics 365 Sales Spoofing Vulnerability | No | No | 6.1 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36045 | Microsoft Office Graphics Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36037 | Microsoft Excel Security Feature Bypass Vulnerability | No | No | 7.8 |
| CVE-2023-36041 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36413 | Microsoft Office Security Feature Bypass Vulnerability | No | Yes | 6.5 |
| CVE-2023-38177 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 6.1 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36422 | Microsoft Windows Defender Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36043 | Open Management Infrastructure Information Disclosure Vulnerability | No | No | 6.5 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36028 | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-36400 | Windows HMAC Key Derivation Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-36408 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36407 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36033 | Windows DWM Core Library Elevation of Privilege Vulnerability | Yes | Yes | 7.8 |
| CVE-2023-36396 | Windows Compressed Folder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36047 | Windows Authentication Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36399 | Windows Storage Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-36046 | Windows Authentication Denial of Service Vulnerability | No | No | 7.1 |
| CVE-2023-36394 | Windows Search Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36405 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36427 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36404 | Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-36406 | Windows Hyper-V Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-24023 | Mitre: CVE-2023-24023 Bluetooth Vulnerability | No | No | N/A |
Updates
- 2023-11-14: Shortly after initial publication, some Microsoft advisory web pages were not listing any patches, although patches did exist. Microsoft appears to have remediated the issue with the advisory web pages. Removed a paragraph from the blog which mentioned this.

