Microsoft is addressing 149 vulnerabilities this April 2024 Patch Tuesday, which is significantly more than usual. For the second month in a row, Microsoft indicated that they weren't aware of prior public disclosure or exploitation in the wild for any of the vulnerabilities patched today. However, later in the day, Microsoft subsequently updated the advisory for CVE-2024-26234 to acknowledge in-the-wild exploitation and public disclosure of the exploit. There are no new additions to CISA KEV at time of writing.
Despite the large number of vulnerabilities published today, Microsoft has ranked only three as critical under its proprietary severity scale. Five browser vulnerabilities were published separately this month, and are not included in the total.
Microsoft is now including two additional data points on advisories: Common Weakness Enumeration (CWE) and Vector String Source assessments.
Windows Proxy Driver: late-breaking zero-day spoofing vulnerability
When originally published, the advisory for CVE-2024-26234 did not indicate that Microsoft was aware of in-the-wild exploitation or public exploit disclosure. However, late on the day of publication, Microsoft updated the advisory to acknowledge awareness of both in-the-wild exploitation and public disclosure.
The advisory provides almost no detail about the nature of the exploit itself, beyond the basic facts: it's a proxy spoofing vulnerability, and patches are available for supported versions of Windows.
Defender for IoT: three critical RCEs
Microsoft Defender for IoT receives patches for three critical remote code execution (RCE) vulnerabilities. Microsoft describes Defender for IoT as an Azure-deployable agentless monitoring solution for Internet of Things (IoT) and Operational Technology (OT) devices.
The advisory for CVE-2024-21322 is light on detail, but notes that exploitation requires the attacker to have existing administrative access to the Defender for IoT web application; this limits the attacker value in isolation, although the potential for insider threat or use as part of an exploit chain remains.
CVE-2024-21323 describes an update-based attack and requires prior authentication; an attacker with the ability to control how a Defender for IoT sensor receives updates could cause the sensor device to apply a malicious update package, overwriting arbitrary files on the sensor filesystem via a path traversal weakness.
Exploitation of CVE-2024-29053 allows arbitrary file upload for any authenticated user, also via a path traversal weakness, although the advisory does not specify what the target is other than “the server”.
The Defender for IoT 24.1.3 release notes do not call out these security fixes and describe only improvements to clock drift detection and unspecified stability improvements; this omission highlights the evergreen value of timely patching.
SharePoint: XSS spoofing
SharePoint receives a patch for CVE-2024-26251, a spoofing vulnerability which abuses cross-site scripting (XSS) and affects SharePoint Server 2016, 2019, and Subscription Edition. Exploitation requires multiple conditions to be met, including but not limited to a reliance on user actions, token impersonation, and specific application configuration. On that basis, although Microsoft is in possession of mature exploit code, exploitation is rated less likely.
Excel: arbitrary file execution
Microsoft is patching a single Office vulnerability today. CVE-2024-26257 describes a RCE vulnerability in Excel; exploitation requires that the attacker convinces the user to open a specially-crafted malicious file.
Patches for Windows-based click-to-run (C2R) Office deployments and Microsoft 365 Apps for Enterprise are available immediately. Not for the first time, a patch for Office for Mac is unavailable at time of writing, and will follow at some unspecified point in the future.
SQL Server OLE DB driver: dozens of RCE
The Microsoft OLE DB Driver for SQL Server receives patches for no fewer than 38 separate RCE vulnerabilities today, which might be a record for a single component. The common theme here is that an attacker could trick a user into connecting to a malicious SQL server to achieve code execution in the context of the client.
All quiet on the Exchange front
There are no security patches for Exchange this month.
Microsoft advisory metadata: CWE and Vector String Source
The addition of CWE assessments to Microsoft security advisories helps pinpoint the generic root cause of a vulnerability; e.g., CVE-2024-21322 is assigned “CWE-77: Improper Neutralization of Special Elements used in a Command ('Command Injection').” By embracing CWE taxonomy, Microsoft is moving away from its own proprietary system to describe root cause. The CWE program has recently updated its guidance on mapping CVEs to a CWE Root Cause.
Analysis of CWE trends can help developers reduce future occurrences through improved Software Development Life Cycle (SDLC) workflows and testing, as well as helping defenders understand where to direct defense-in-depth and deployment-hardening efforts for best return on investment. At time of writing, the addition of CWE assessments does not appear to be retroactive.
The Common Vulnerability Scoring System (CVSS) is a widely-used standard for evaluation of vulnerability severity, and Microsoft has helpfully provided CVSS data for each vulnerability for a long time. The CVSS vector describes the variables which comprise the overall CVSS severity score for a vulnerability. The addition of Vector String Source — typically, the entity providing the CVSS assessment on a Microsoft vulnerability will be Microsoft — provides further welcome clarity, at least for vulnerabilities where Microsoft is the CVE Numbering Authority (CNA). It may not be a coincidence that Microsoft is choosing to start explicitly describing the source of the CVSS vector during the ongoing uncertainty around the future of the NVD program.
Lifecycle update
Several Microsoft products move past the end of mainstream support after today:
- Azure DevOps Server 2019.
- System Center 2019.
- Visual Studio 2019.
Additionally, some older products move past the end of extended support, including:
- Microsoft Deployment Agent 2013.
- Microsoft Diagnostics and Recovery Toolset 8.1.
- Visual Studio 2013.
Summary Charts
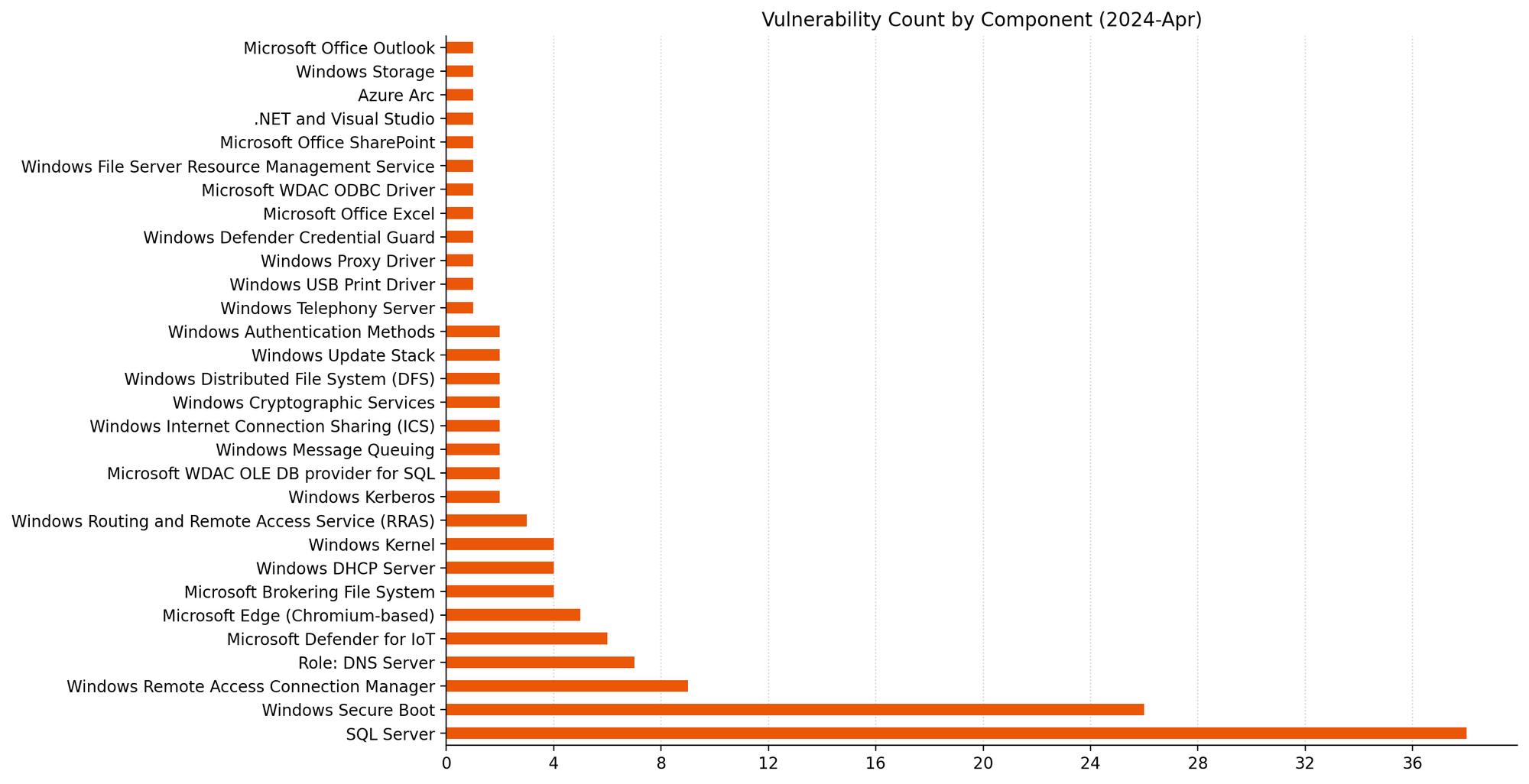
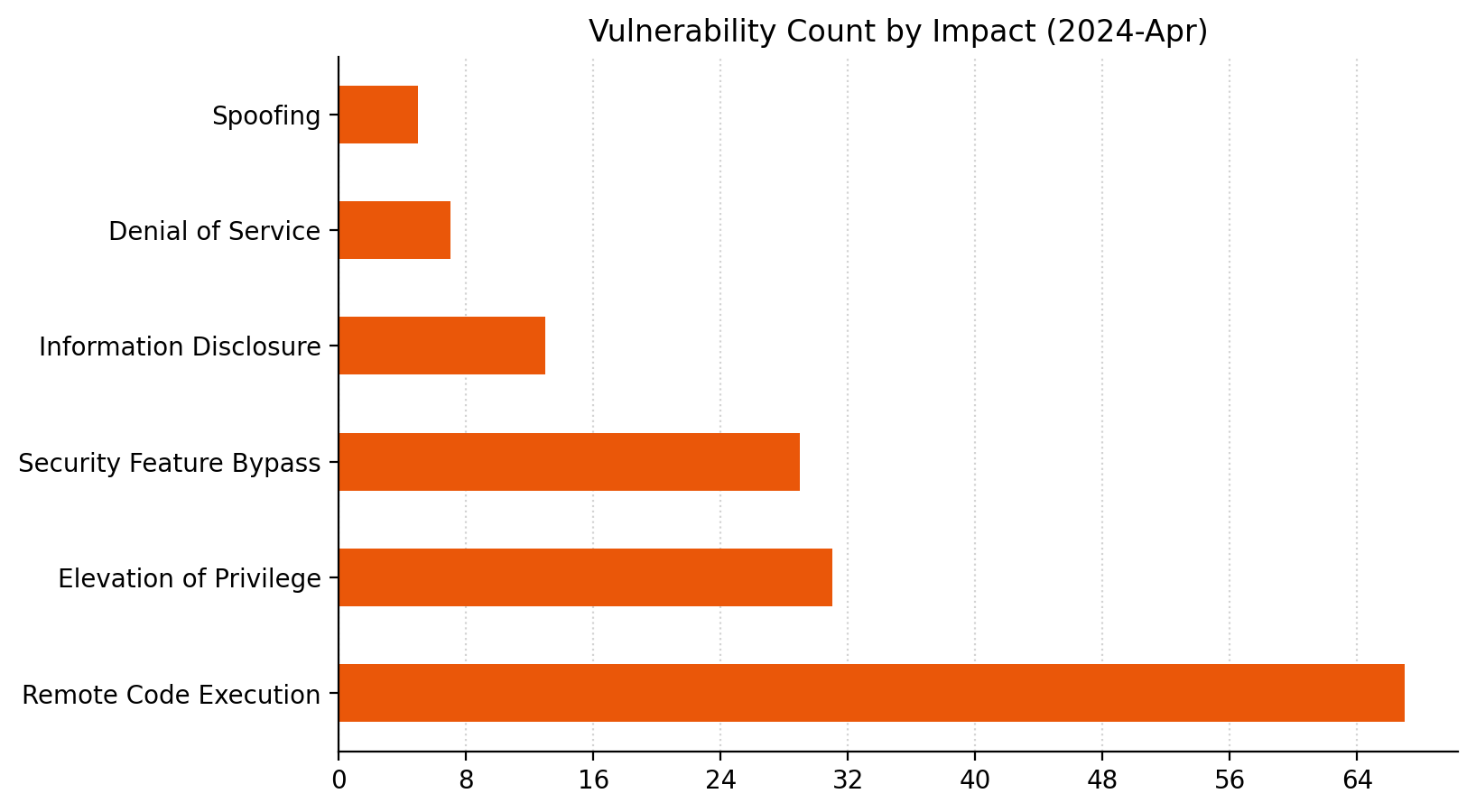
Summary Tables
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-29990 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability | No | No | 9 |
| CVE-2024-29993 | Azure CycleCloud Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2024-29989 | Azure Monitor Agent Elevation of Privilege Vulnerability | No | No | 8.4 |
| CVE-2024-29063 | Azure AI Search Information Disclosure Vulnerability | No | No | 7.3 |
| CVE-2024-21424 | Azure Compute Gallery Elevation of Privilege Vulnerability | No | No | 6.5 |
| CVE-2024-26193 | Azure Migrate Remote Code Execution Vulnerability | No | No | 6.4 |
| CVE-2024-28917 | Azure Arc-enabled Kubernetes Extension Cluster-Scope Elevation of Privilege Vulnerability | No | No | 6.2 |
| CVE-2024-20685 | Azure Private 5G Core Denial of Service Vulnerability | No | No | 5.9 |
| CVE-2024-29992 | Azure Identity Library for .NET Information Disclosure Vulnerability | No | No | 5.5 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-29981 | Microsoft Edge (Chromium-based) Spoofing Vulnerability | No | No | 4.3 |
| CVE-2024-29049 | Microsoft Edge (Chromium-based) Webview2 Spoofing Vulnerability | No | No | 4.1 |
| CVE-2024-3159 | Chromium: CVE-2024-3159 Out of bounds memory access in V8 | No | No | N/A |
| CVE-2024-3158 | Chromium: CVE-2024-3158 Use after free in Bookmarks | No | No | N/A |
| CVE-2024-3156 | Chromium: CVE-2024-3156 Inappropriate implementation in V8 | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21409 | .NET, .NET Framework, and Visual Studio Remote Code Execution Vulnerability | No | No | 7.3 |
ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-20688 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.1 |
| CVE-2024-20689 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.1 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-26257 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2024-26251 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 6.8 |
Other vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-20670 | Outlook for Windows Spoofing Vulnerability | No | No | 8.1 |
SQL Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-28906 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28908 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28909 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28910 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28911 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28912 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28913 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28914 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28915 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28939 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28942 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28945 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29047 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28926 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28927 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28940 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28944 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29044 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29046 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29048 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29982 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29983 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29984 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29985 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29043 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28941 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28943 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29045 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | No | No | 7.5 |
SQL Server Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-28929 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28931 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28932 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28936 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28930 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28933 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28934 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28935 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28937 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-28938 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21323 | Microsoft Defender for IoT Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29053 | Microsoft Defender for IoT Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21322 | Microsoft Defender for IoT Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-21324 | Microsoft Defender for IoT Elevation of Privilege Vulnerability | No | No | 7.2 |
| CVE-2024-29055 | Microsoft Defender for IoT Elevation of Privilege Vulnerability | No | No | 7.2 |
| CVE-2024-29054 | Microsoft Defender for IoT Elevation of Privilege Vulnerability | No | No | 7.2 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-29988 | SmartScreen Prompt Security Feature Bypass Vulnerability | No | No | 8.8 |
| CVE-2024-26256 | libarchive Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2024-26235 | Windows Update Stack Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-29052 | Windows Storage Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26245 | Windows SMB Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-20693 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26218 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26237 | Windows Defender Credential Guard Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-21447 | Windows Authentication Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-28920 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.8 |
| CVE-2024-28905 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-28904 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-28907 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-23593 | Lenovo: CVE-2024-23593 Zero Out Boot Manager and drop to UEFI Shell | No | No | 7.8 |
| CVE-2024-26254 | Microsoft Virtual Machine Bus (VMBus) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2024-26219 | HTTP.sys Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2024-26221 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26222 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26223 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26224 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26227 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26231 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26233 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26236 | Windows Update Stack Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-26243 | Windows USB Print Driver Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-26213 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-23594 | Lenovo: CVE-2024-23594 Stack Buffer Overflow in LenovoBT.efi | No | No | 6.4 |
| CVE-2024-29064 | Windows Hyper-V Denial of Service Vulnerability | No | No | 6.2 |
| CVE-2024-26255 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-26172 | Windows DWM Core Library Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-26220 | Windows Mobile Hotspot Information Disclosure Vulnerability | No | No | 5 |
Windows ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-26179 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-26200 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-26205 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-20678 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-26214 | Microsoft WDAC SQL Server ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-26210 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-26244 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-29050 | Windows Cryptographic Services Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2024-26180 | Secure Boot Security Feature Bypass Vulnerability | No | No | 8 |
| CVE-2024-26189 | Secure Boot Security Feature Bypass Vulnerability | No | No | 8 |
| CVE-2024-26240 | Secure Boot Security Feature Bypass Vulnerability | No | No | 8 |
| CVE-2024-28925 | Secure Boot Security Feature Bypass Vulnerability | No | No | 8 |
| CVE-2024-26230 | Windows Telephony Server Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26239 | Windows Telephony Server Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26211 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26228 | Windows Cryptographic Services Security Feature Bypass Vulnerability | No | No | 7.8 |
| CVE-2024-26229 | Windows CSC Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26241 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26175 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.8 |
| CVE-2024-29061 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.8 |
| CVE-2024-26158 | Microsoft Install Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26248 | Windows Kerberos Elevation of Privilege Vulnerability | No | No | 7.5 |
| CVE-2024-28896 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.5 |
| CVE-2024-26212 | DHCP Server Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2024-26215 | DHCP Server Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2024-26194 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.4 |
| CVE-2024-26216 | Windows File Server Resource Management Service Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2024-26232 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2024-29066 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26208 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26195 | DHCP Server Service Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-26202 | DHCP Server Service Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2024-29062 | Secure Boot Security Feature Bypass Vulnerability | No | No | 7.1 |
| CVE-2024-26242 | Windows Telephony Server Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-26252 | Windows rndismp6.sys Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-26253 | Windows rndismp6.sys Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-26168 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.8 |
| CVE-2024-28897 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.8 |
| CVE-2024-20669 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.7 |
| CVE-2024-26250 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.7 |
| CVE-2024-28921 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.7 |
| CVE-2024-28919 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.7 |
| CVE-2024-28903 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.7 |
| CVE-2024-26171 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.7 |
| CVE-2024-28924 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.7 |
| CVE-2024-26234 | Proxy Driver Spoofing Vulnerability | No | No | 6.7 |
| CVE-2024-26183 | Windows Kerberos Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2024-26226 | Windows Distributed File System (DFS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2024-28923 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.4 |
| CVE-2024-28898 | Secure Boot Security Feature Bypass Vulnerability | No | No | 6.3 |
| CVE-2024-20665 | BitLocker Security Feature Bypass Vulnerability | No | No | 6.1 |
| CVE-2024-28901 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-28902 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-26207 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-26217 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-28900 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-26209 | Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-2201 | Intel: CVE-2024-2201 Branch History Injection | No | No | 4.7 |
| CVE-2024-29056 | Windows Authentication Elevation of Privilege Vulnerability | No | No | 4.3 |
| CVE-2024-28922 | Secure Boot Security Feature Bypass Vulnerability | No | No | 4.1 |
Updates
- 2024-04-09: Updated discussion of vuln diclosure prior to publication to reflect Microsoft's update to the advisory for CVE-2024-26234.

