Exposure Command provides 360-degree visibility and enables security teams to pinpoint and extinguish your most critical risks.
Security and IT teams are experiencing a significant shift in operations as they become more distributed. Development and procurement processes have decentralized, and sensitive data now extends far beyond the network edge. This expansion, coupled with growth and innovation outpacing security investments, has led to a significant "security visibility gap."
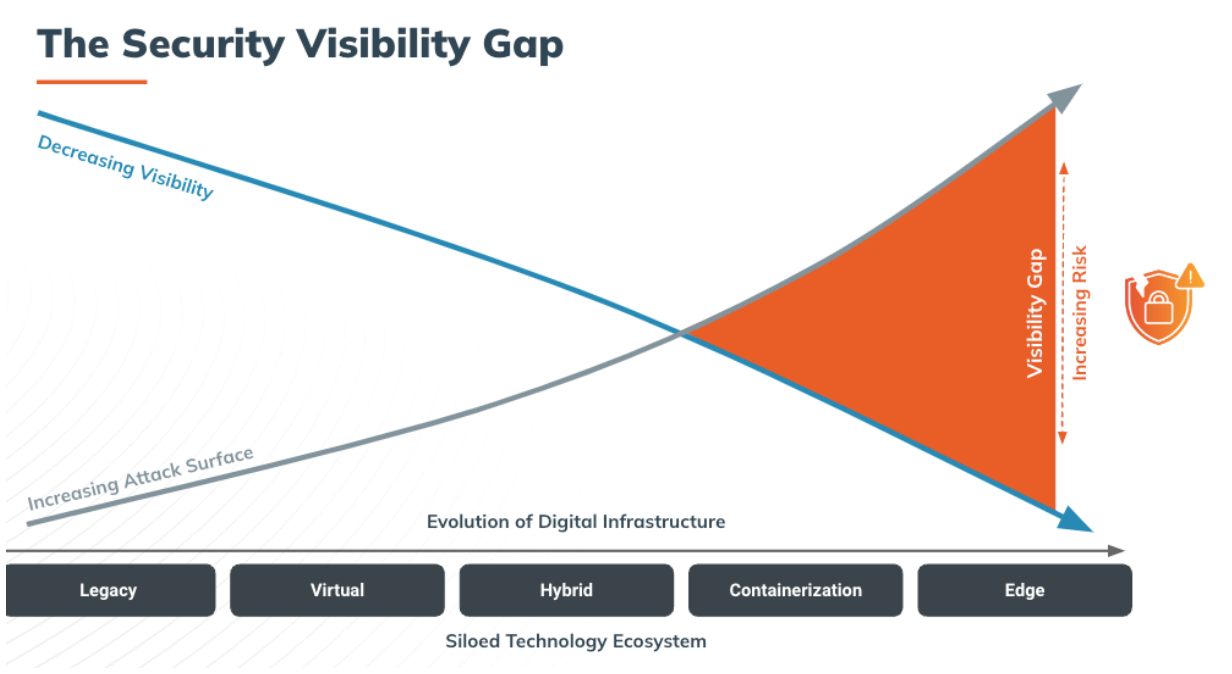
Disparate tools widen this gap, creating data silos and inconsistencies, leading to manual efforts and swivel-charing to manually correlate conflicting findings and dashboards. This situation has been exacerbated by broader industry trends. Gartner estimates that through 2026, 'unpatchable' attack surfaces will grow from less than 10% to more than half of the enterprise’s total exposure, reducing the effectiveness of traditional vulnerability management programs.
Security teams need to manage and interpret a broad range of different exposure types - cloud misconfigurations, user entitlements, unmanaged machines, vulnerabilities, etc. with conflicting and duplicate data from various different security and IT management tools with varying levels of data fidelity.
The only way to truly solve this problem is to implement a solution that treats third-party data as a first-class citizen, bringing together telemetry from all of your security tools to build a complete picture of your environment, and thereby your attack surface. To that end, Rapid7 announced the launch of two exciting new product offerings designed to unify your attack surface and deliver effective hybrid risk management: Surface Command and Exposure Command.
Unlock complete attack surface visibility to eliminate blind spots and uncover control gaps with Surface Command
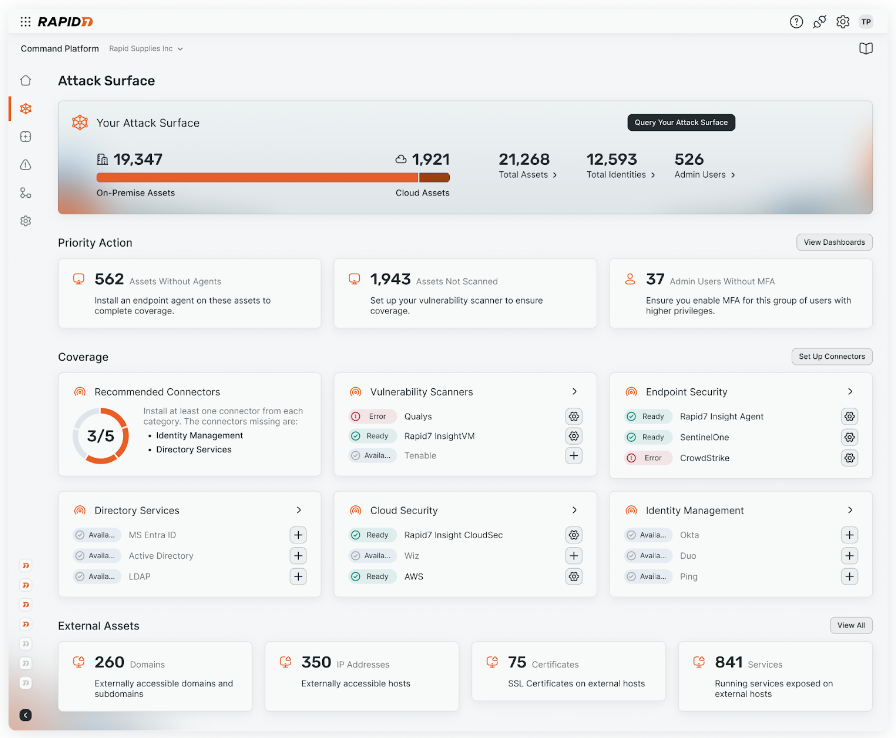
Surface Command closes the visibility gap by breaking down data silos, combining internal and external monitoring to build a 360-degree view of your entire environment, combining market leading Cyber Asset Attack Surface Management (CAASM) and External Attack Surface Management (EASM) capabilities into one unified offering.
External scans provide an adversary’s perspective on the attack surface, detecting and validating exposures. Surface Command combines these external scans with a detailed inventory of your internal assets, continuously ingested and updated from a wide range of security and IT tools and automatically correlates the assets to create detailed inventory of your 'true' attack surface, highlighting security control gaps.
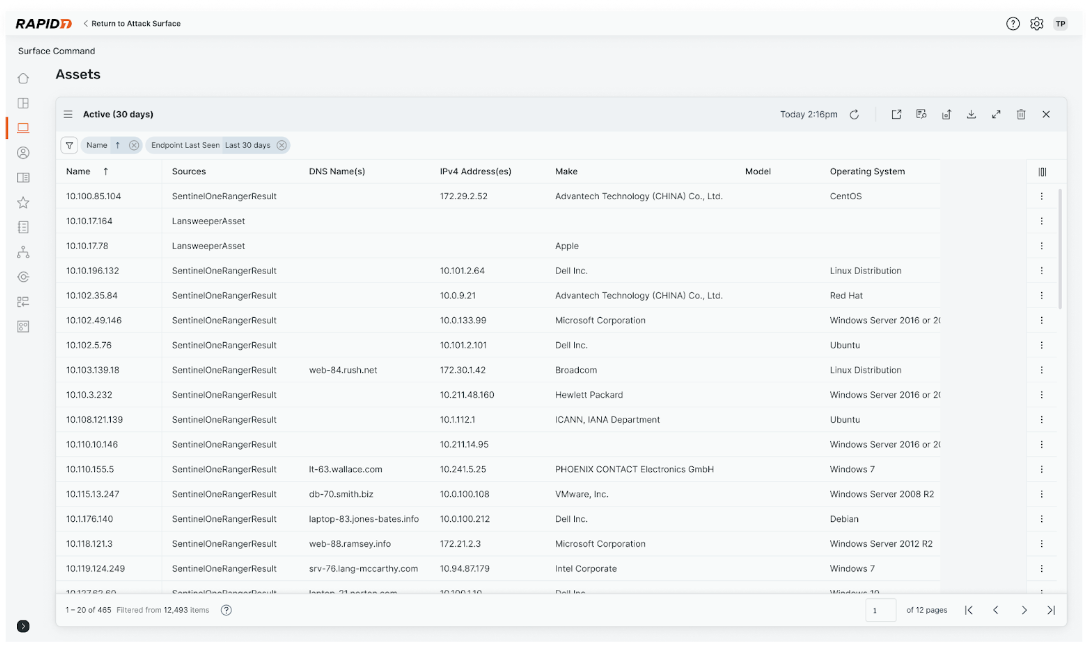
This process delivers a comprehensive view of your environment that teams across the organization can trust and align on as a ‘single source of truth’ without the risk of blind spots, unprotected assets, and ungoverned access. Understanding how all your interconnected assets are configured enables you to quickly identify and prioritize high-risk vulnerabilities, shadow IT, and compliance issues. With this more comprehensive visibility serving as the foundation of our Command Platform, security teams have a view of their attack surface they can trust and action across their wider organization.
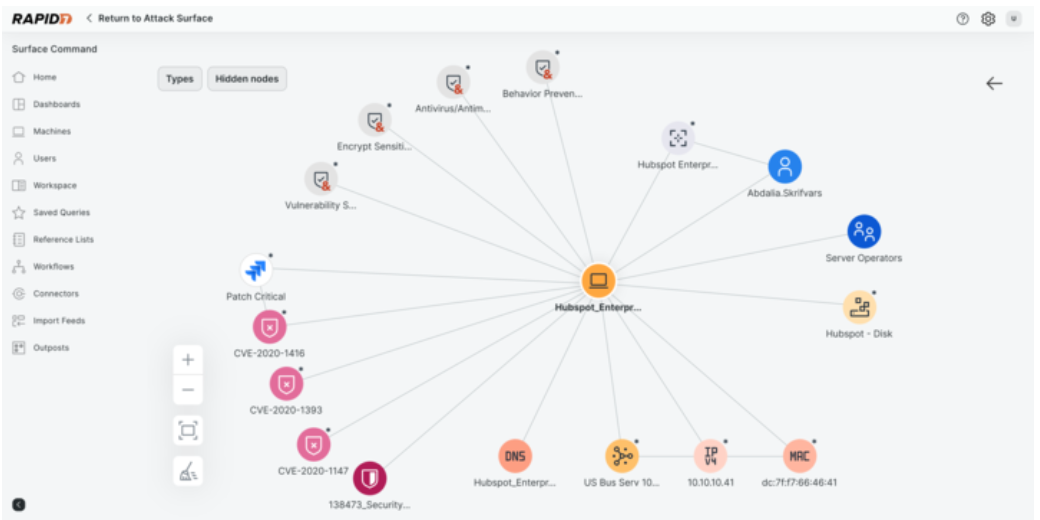
Automatically prioritize exposures across your hybrid environment with Exposure Command
Exposure Command extends the power of Surface Command even further, combining the same unified attack surface visibility with high-fidelity environment detail and risk context to help teams to zero-in on the exposures and vulnerabilities that attackers have in their sights with the threat-aware risk context needed to prioritize more efficiently and effectively.
With Exposure Command, every asset in your environment is enriched with relevant context from all of Rapid7’s exposure management capabilities, including our industry-leading VM, CNAPP and AppSec solutions, which provides teams an understanding of which assets are most critical to the business and those that suffer from toxic combinations that leave the organization vulnerable to a security incident.
This situational awareness allows teams to more effectively prioritize response efforts by honing in on the vulnerabilities that are either being actively exploited in the wild and/or those that present the most risk should a compromise occur.
Prioritization is critical, especially when you consider the massive volume of risk signals produced by modern cloud-native environments on a daily basis. It’s simply not feasible to expect to address everything, so making sure that teams are spending the time they do have on the actions that will have the greatest impact on reducing their overall risk posture and eliminating critical exposures is key.
When it comes to prioritization, there are three primary vectors that we need to consider: Opportunity, Likelihood and Impact of exploitation.
- Opportunity - The first step in prioritizing exposures is to understand whether a threat actor could exploit the issue in the first place by analyzing the downstream security controls and mechanisms in place - or not in place for that matter. This includes considering whether or not a resource is publicly accessible, if there are additional mitigating controls like web application or network firewalls, if an at-risk asset has an endpoint protection solution installed, etc.
- Likelihood - It’s important to understand how likely it is that an attacker would exploit a given exposure. This can be accomplished in a number of ways, including focusing on CVEs on CISA’s Known Exploited Vulnerabilities (KEV) list, but also involves looking at real-world activity via threat intelligence feeds - like those that feed into Rapid7’s Active Risk score - to get a sense for whether a vulnerability is being exploited elsewhere.
- Impact - Taking into account the business criticality of the asset, data or system, what would be the relevant impact should a given risk signal be exploited by a threat actor. This is often accomplished by assigning tags that flag whether or not a given resource is associated with a business critical application or is housing sensitive customer data.
To this end, a new feature coming to the Command Platform with Exposure Command, Remediation Hub, automatically surfaces the top areas teams need to focus on and elevates the mitigation activities that would have the largest impact in reducing the overall risk score of your environment along with any relevant contextual information to assist in validation and remediation efforts.
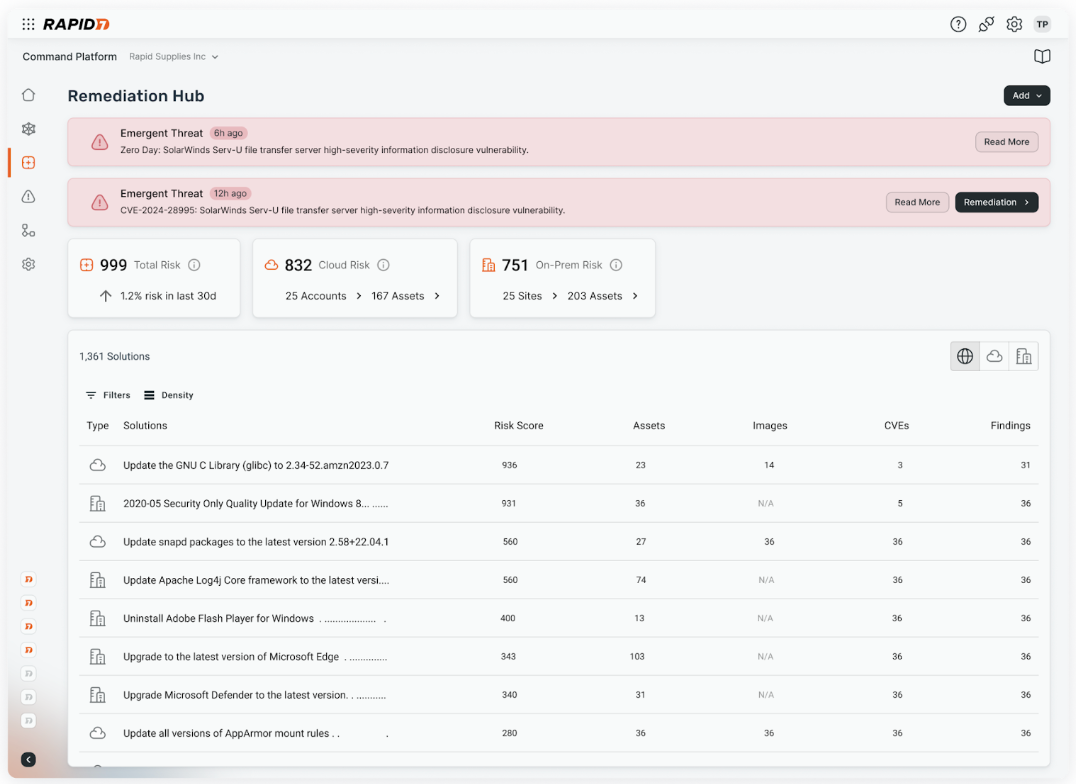
After 24+ years in exposure management, we are excited to partner with customers through the next era of the attack surface and hybrid risk with our new Exposure Command product. This is just the beginning. Stay tuned here for more updates as we continue to grow our Command Platform.
Learn more about Surface Command and Exposure Command
Attending Black Hat? Come see us at booth #2436 to get a one on one tour! If you can’t make it to the event you can also find additional information on the docs page, or give us a bit of information and we’ll have a member of the team reach out directly.
Learn More about Rapid7's Exposure Command ▶︎
Confidently identify and prioritize exposures from endpoint to cloud with full attack surface visibility and threat-aware risk context.
