As part of our research and tracking of threats, Rapid7 Labs is actively monitoring new and upcoming threat groups and the ransomware domain is known for having a large number of them. In the Ransomware Radar Report, Rapid7 Labs shared the observation that in the first half of 2024, 21 new or rebranded ransomware groups surfaced. Many of those are not immediately coming into the spotlight as abusing some fancy new or recently discovered vulnerability, or — as we measure activity — posting a large number of data leaks.
Rapid7 Labs has an ongoing commitment to help organizations understand and mitigate the complex world of ransomware, and this includes highlighting these newer groups. In this post we’re going to focus on the recently-emerged Lynx ransomware group.
Intro to the Lynx group
The Lynx ransomware group was identified in July 2024, and has claimed more than 20 victims in various industry sectors to date. The group is using both single and double extortion techniques against their victims; however, they claim to be “ethical” with regards to choosing victims, according to their press release on July 24th:
“Lynx Ransomware core motivation is grounded in financial incentives, with a clear intention to avoid undue harm to organizations. We recognize the importance of ethical considerations in the pursuit of financial gain and maintain a strict policy against targeting governmental institutions, hospitals, or non-profit organizations, as these sectors play vital roles in society.”When a victim has been hit, the infamous readme.txt surfaces on desktops and contains the link to the Tor site of Lynx and the ID needed to enter the portal:
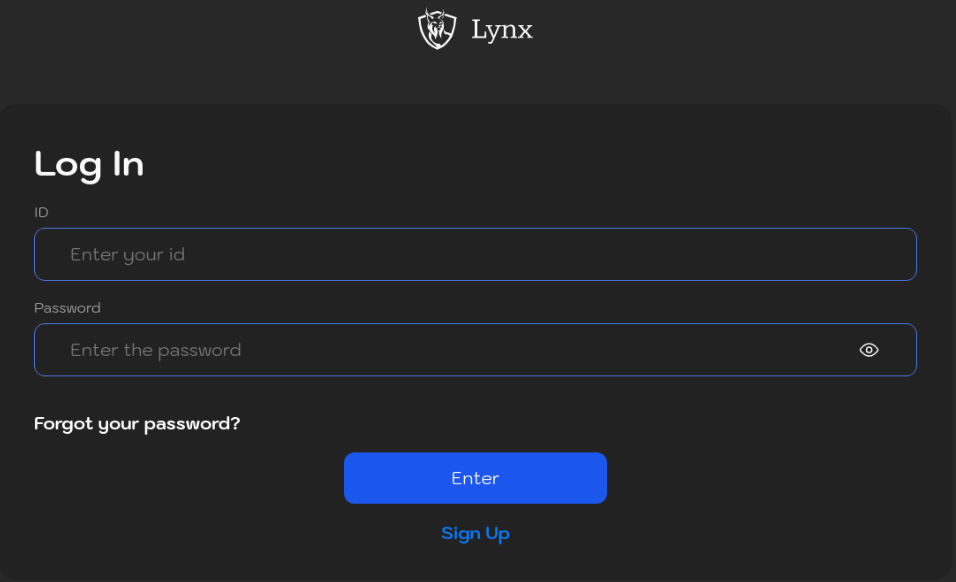
Along with the portal for victims to log in, the group is hosting a public blog and also a leaks page where victims are showcased in an attempt to enforce payment.
Analyzing Lynx ransomware
In order to conduct our analysis, we took a sample that had been observed being used in August 2024.
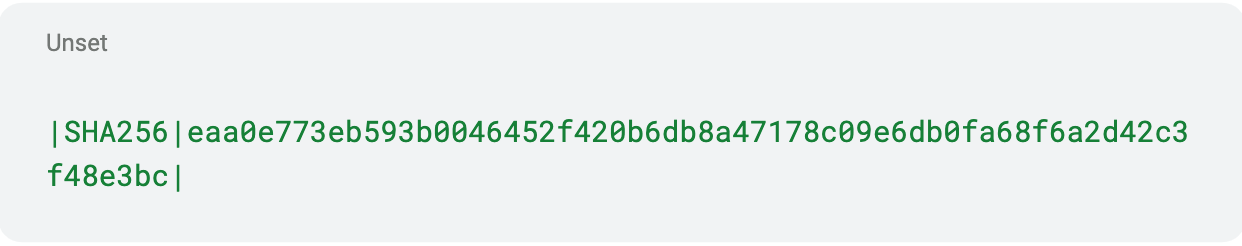
Underground rumors claim that the Lynx group has purchased the source code from another group Rapid7 tracks: INC ransomware. When conducting a binary diff on the samples of Lynx and INC ransomware, the overall results show a 48 percent similarity score, where the functions have a score of 70.8 percent:
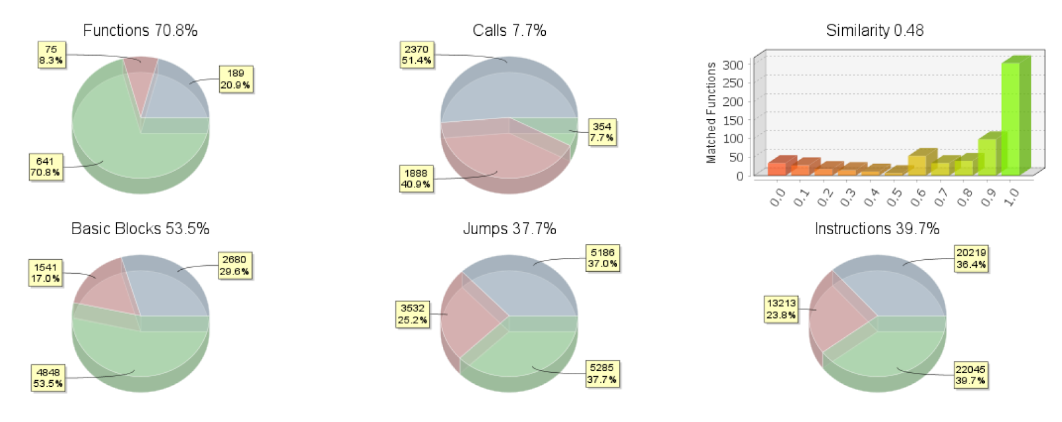
Based on the diff and some other comparisons we conducted, there are overlaps in functions and arguments, but in our opinion not enough to prove fully that Lynx was derived from INC ransomware’s source code.
An initial look at the Lynx ransomware sample finds that in the code, three URLs stand out as already pointing to suspicious sites:
hxxp://lynxblog[.]net/
hxxp://lynxch2k5xi35j7hlbmwl7d6u2oz4vp2wqp6qkwol624cod3d6iqiyqd[.]onion/login
hxxp://lynxbllrfr5262yvbgtqoyq76s7mpztcqkv6tjjxgpilpma7nyoeohyd[.]onion/disclosures
In addition, the ransomware has several command line options to run:
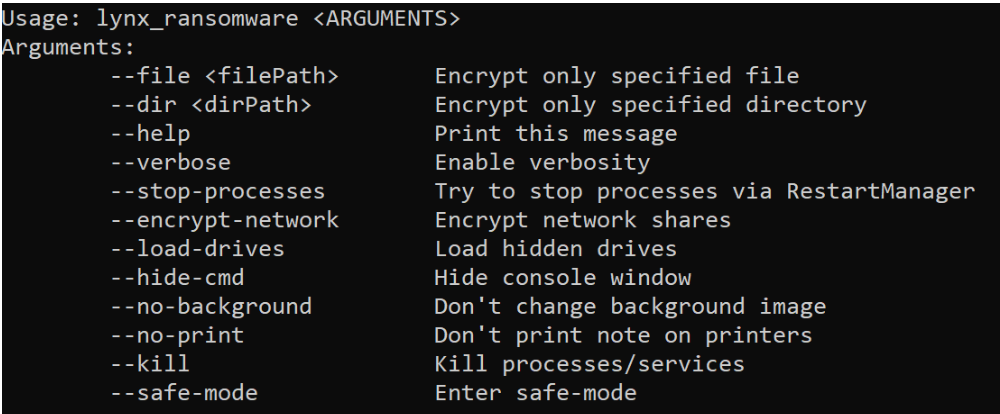
Inside the ransomware, the readme.txt — aka the ransomware notification — is hidden using Base64 to decode the message. The ID to log into the portal will be generated, but overall the note is similar to other ransomware notes:
Your data is stolen and encrypted.
Download TOR Browser to contact with us.
ID
~ %id%
Chat site:
~ TOR Network: http://lynxchatly4zludmhmi75jrwhycnoqvkxb4prohxmyzf4euf5gjxroad.onion/login
~ TOR Mirror #1: http://lynxchatfw4rgsclp4567i4llkqjr2kltaumwwobxdik3qa2oorrknad.onion/login
~ TOR Mirror #2: http://lynxchatohmppv6au67lloc2vs6chy7nya7dsu2hhs55mcjxp2joglad.onion/login ~ TOR Mirror #3: http://lynxchatbykq2vycvyrtjqb3yuj4ze2wvdubzr2u6b632trwvdbsgmyd.onion/login
Key ransomware functionalities:
1.Process and Service Management:
- The ransomware attempts to kill various system processes and services using methods like the RestartManager. It specifically targets services that might hinder the encryption process, such as backup-related services.
- It enumerates and stops dependent services and processes, utilizing system APIs such as EnumDependentServicesW and ControlService.
2.Shadow Copy Deletion:
- A major target of this ransomware is deleting volume shadow copies, which are often used to restore data. The string “Successfully delete shadow copies from %c:” suggests the use of vssadmin or other similar commands to ensure backup files are removed.
3.File Encryption:
- It encrypts files across the system, including network shares and drives (Encrypt network shares, Load hidden drives). The use of terms like “Encrypting file: %s” and “Encrypt only specified directory” indicates the ransomware can focus on specific folders or file types, increasing its precision.
- There is also the ability to encrypt only selected files, directories, or network shares based on configuration (--file, --dir <dirPath>, --encrypt-network).
Lynx: Ones to watch
While the Lynx ransomware group says it takes an "ethical" stance, there is no scenario where attacking and extorting victims can be viewed in that way. Lynx’s aggressive targeting and dual extortion tactics make them a threat to watch. With overlaps in functionality between Lynx and INC ransomware, the potential for source code sharing and evolution among ransomware groups remains a critical concern for defenders.
As organizations navigate these threats, it's crucial to stay vigilant, invest in robust security measures, and be prepared to respond quickly to ransomware incidents. Rapid7 Labs will continue to monitor and analyze the activities of groups like Lynx to provide timely insights and actionable intelligence for the community.
