Rapid7 is delighted to announce the launch of Vector Command, a continuous red teaming managed service designed to assess your external attack surface and identify gaps in the security defenses on an ongoing basis. Following the launch of Surface Command and Exposure Command in August, Vector Command will continue our expansion of Exposure Management protection for our customers.
In today’s digital landscape, organizations are more exposed to cyber threats than ever before. Cloud resources, SaaS solutions, and ever-growing shadow IT create vast external attack surfaces, making businesses increasingly vulnerable. Meanwhile attackers are constantly on the prowl, conducting reconnaissance to exploit weaknesses. Security teams lack visibility into their internet-facing exposures, leaving them vulnerable to potential breaches.
While external attack surface management (EASM) tools offer visibility, they often fall short in validation, resulting in lengthy lists of potential exposures for security teams to sift through. Traditional penetration testing can help validate vulnerabilities, but its point-in-time nature risks leaving critical exposures undetected for extended periods.
Introducing Vector Command
Vector Command is designed to address these challenges head-on, providing a continuous, proactive approach to securing your external attack surface by combining Rapid7’s trusted technology for external attack surface assessments with our world-class red team expertise. By providing an attacker’s perspective, Vector Command empowers security teams to visualize internet-facing assets, validate critical exposures, and take decisive action to mitigate risks.
Vector Command benefits include:
- Increased visibility of the external attack surface with persistent, proactive reconnaissance of both known and unknown internet-facing assets
- Improved prioritization with ongoing, expert-led red team operations to continuously validate your most critical external exposures
- Same-day reporting of successful exploits with expert-vetted attack paths for multi-vector attack chains and a curated list of “attractive assets” that are likely to be exploited
- Monthly expert consultation to confidently drive remediation efforts and resiliency planning
Rapid7 advantage: trusted technology and red team expertise
At the heart of Vector Command is our red team operators, among the best in the industry, bringing years of experience in simulating real-world attacks and identifying vulnerabilities that automated tools might miss. This combined with our recently launched Command Platform’s external attack surface assessment capability provides a unique and powerful solution to ensure that you are not just receiving a list of potential vulnerabilities, but actionable insights based on real-world attack scenarios.
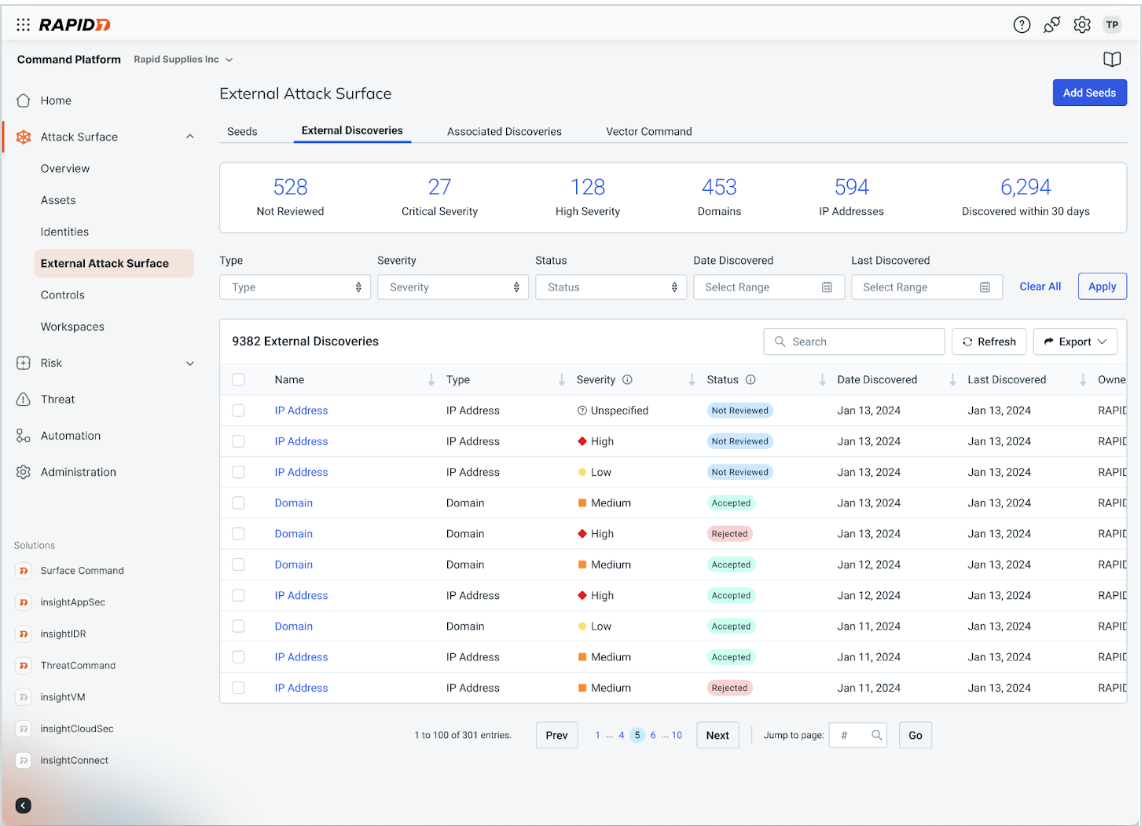
External attack surface assessment: Powered by Rapid7’s Command Platform, Vector Command will leverage the external attack surface capability to perform ongoing, active reconnaissance and discovery of your external attack surface to help you
- Find the unknown and ensure continuous understanding of where shadow IT or unknown business assets may exist like exposed web services, remote admin services, and more
- Zero-in on potential remote access risks, and risky or unencrypted services
Red team expertise: Our expert operators leverage the latest tactics, techniques, and procedures (TTPs) to safely exploit the external exposures and test your security controls with red team exercises like:
- Opportunistic phishing - Our experts will design and conduct phishing campaigns using the latest TTPs with focus on demonstrating the impact of credential capture and payload execution.
- External network assessment - Ongoing assessment of vulnerabilities exposed in the external network, focused on obtaining access to your organization and its sensitive systems.
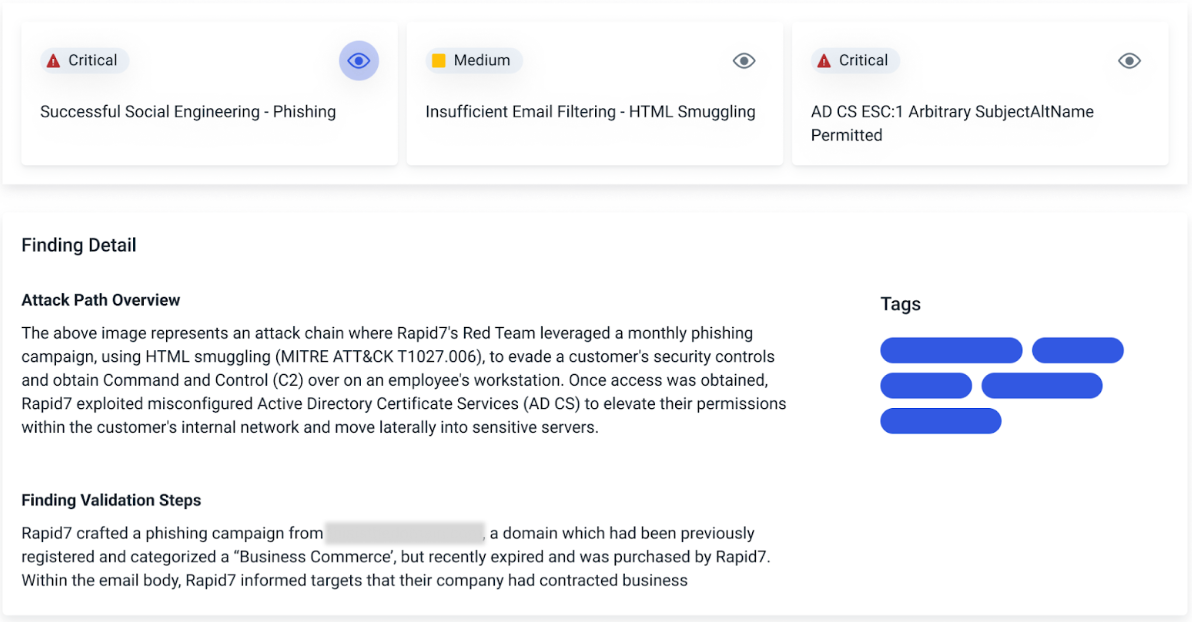
- Post-compromise breach simulation - Upon breach, our experts will safely emulate the latest tactics to obtain command and control over the compromised system. Post-exploitation activities emulate adversary behavior to assess privilege escalation, lateral movement, and persistence.
- Emergent threat validation - Assess your network perimeter’s susceptibility to the latest Rapid7 emergent threat vulnerabilities to validate patching and security configurations.
Take command of your attack surface defenses
In an era where cyber threats are constantly evolving, Vector Command empowers you to stay one step ahead of attackers. By providing continuous visibility, validation, and expert guidance, we help you transform your cybersecurity posture from reactive to proactive.
Don’t wait for a breach to expose weaknesses in your defenses. With Vector Command, you can command your attack surface with confidence, knowing that you have Rapid7’s trusted technology and Red Team expertise on your side.
Vector Command: Request Demo ▶︎
Ready to see how continuous red team managed services can ensure your potential attack pathways are remediated before they can ever be exploited?

