This was one of the most exciting quarters at Rapid7 as we announced the next chapter in our mission to give customers command of their attack surface: the Rapid7 Command Platform, our unified threat exposure and detection and response platform. With this, we introduced two exciting new products:
- Surface Command: Unifies asset inventory and attack surface management
- Exposure Command: Brings together the comprehensive visibility of Surface Command with hybrid vulnerability management for true end-to-end risk management
While building on our legacy as a pioneer in vulnerability management, we’ve also made expansions on the detection and response side of the house – expanding our Managed Detection and Response capabilities with the release of MDR for the Extended Ecosystem. Read on for more details on these exciting launches across Rapid7 products and services.
Achieve complete attack surface visibility and proactively eliminate exposures from endpoint to cloud
As digital infrastructure continues to evolve from traditional on-prem models to hybrid, distributed teams and systems, one thing remains the same – the attack surface continues to grow, creating more risk and a wider visibility gap.
With the August launches of both Surface Command and Exposure Command, Rapid7 is closing the visibility gap and providing your team with the tools to visualize, prioritize, and remediate risk from endpoint to cloud.
Surface Command: Comprehensive visibility you can trust
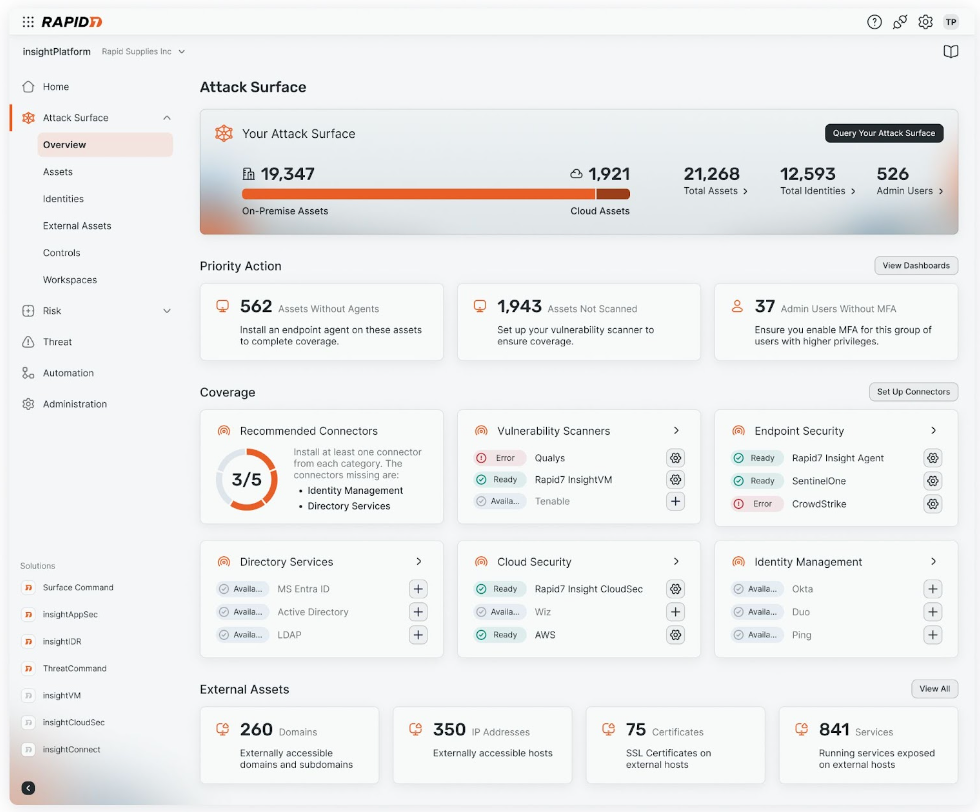
Surface Command provides the foundational attack surface visibility that underpins the Command Platform by breaking down security data silos and combining comprehensive external attack surface monitoring with internal asset visibility across hybrid environments. The result? A dynamic 360-degree view of your entire attack surface in one place. With this view, you can:
- Visualize your entire digital estate from endpoint to cloud
- Prioritize and mitigate exposures and potential threats with a risk-aware and adversary-driven view of your entire attack surface
- Identify and address misconfigurations, shadow IT, and compliance issues
Learn more about Surface Command.
Exposure Command: Pinpoint and extinguish critical risks from endpoint to cloud
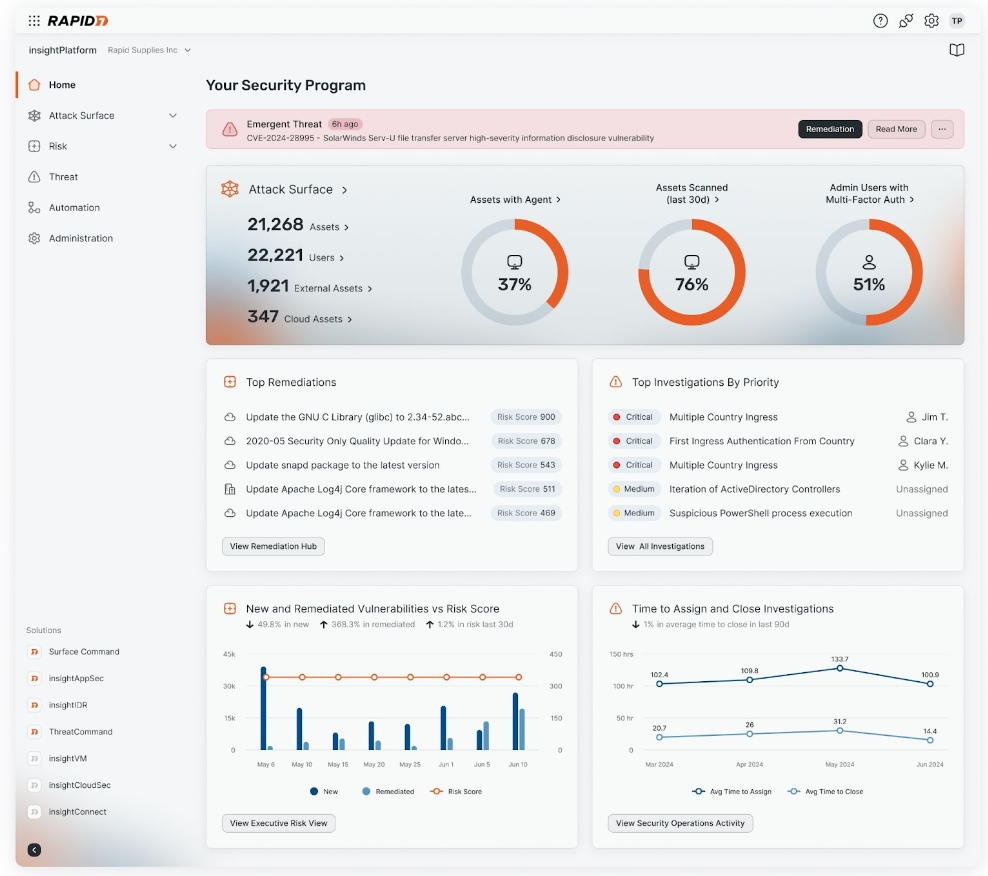
Exposure Command extends the power of Surface Command by combining complete attack surface visibility with high-fidelity risk context and insight into your organization’s security posture. Exposure Command aggregates findings from both Rapid7’s native exposure detection capabilities as well as third-party exposure and enrichment sources you’ve already got in place, so you are able to:
- Extend risk coverage to cloud environments with real-time agentless assessment
- Zero-in on exposures and vulnerabilities with the threat-aware risk context
- Continuously assess your attack surface, validate exposures, and receive actionable remediation guidance
- Efficiently operationalize your exposure management program and automate enforcement of security and compliance policies with native, no-code automation
Learn more about Exposure Command.
Continuous red teaming at your (managed) service with Vector Command
Attackers are relentlessly looking for weak spots and new access points into your organization – you should be too. Leverage Vector Command – our latest continuous red teaming service – to proactively test your external attack surface with ongoing red team exercises and expert guidance from Rapid7’s team of managed services experts.
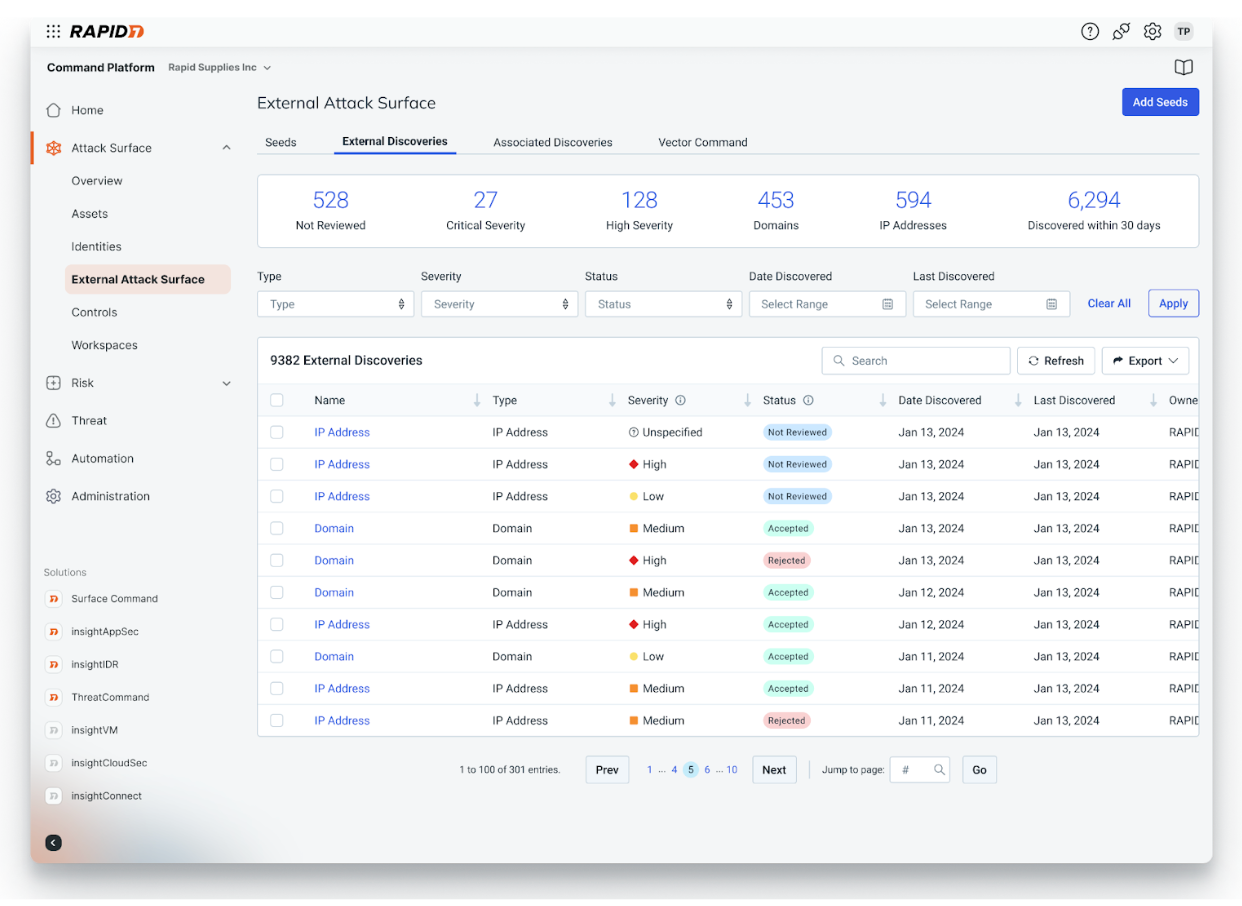
With Vector Command, your team will experience:
- Increased visibility of the external attack surface with persistent, proactive reconnaissance of both known and unknown internet-facing assets
- Improved prioritization with ongoing, expert-led red team operations to continuously validate your most critical external exposures
- Same-day reporting of successful exploits with expert-vetted attack paths for multi-vector attack chains and a curated list of “attractive assets” that are likely to be exploited
- Monthly expert consultation to confidently drive remediation efforts and resiliency planning
Learn more about Vector Command.
Improved scale, reliability and contextualized reporting for cloud and on-prem vulnerability management
The increased scale, rate of change, and complexity associated with cloud and on-prem environments makes managing vulnerabilities a challenge. This quarter we continued to advance our agentless vulnerability assessment capabilities to drive improved scalability and extended reporting to allow teams to quickly identify, prioritize, and remediate vulnerabilities at scale. This includes:
- In-cloud assessment for Azure hosts drive improved cost efficiency for running vulnerability assessments at scale across all cloud hosts running on Microsoft Azure.
- Unified cloud vulnerability reporting combines context and insights across discovered CVEs, software and resources with proof data included by default to enable more effective and accelerated vulnerability remediation.
- Increased granularity for cloud vulnerability first found dates enables teams to quickly understand where an organization is exposed to a given CVE both at an organizational level across their environment globally or on a per-resource basis.Accurately report on MTTR with first found date enhancement for on-prem vulnerabilities with the addition of “First Found” and “Reintroduced” columns, providing deeper visibility into when a vulnerability was first discovered and if it was later reintroduced after patching.
Comprehensive content coverage for policies and critical systems
We strive to provide you with fast and broad coverage for critical policies and systems so you can accurately assess the environment for vulnerability and compliance risks. This past quarter we added a number of new policy coverages and enhancements to InsightVM and Nexpose, including:
- Arista EOS coverage: Arista is a popular alternative to Cisco, and this expansion provides you with broader coverage of your boundary devices and better insights into critical assets.
- Released policy coverage for DISA STIG Windows Server 2016 and Windows Server 2019; DISA STIG for Red Hat Enterprise Linux 8 and Red Hat Enterprise Linux 9; and CIS Benchmark for Fortinet Fortigate to ensure continued compliance.
- Enhanced existing coverages for critical systems like Alpine Linux, Oracle Linux, Windows Server 2022, and Debian Linux.
Pinpoint critical signals and act confidently against threats with cloud-ready detection and response
Introducing MDR for the Extended Ecosystem
In an ever-expanding cybersecurity landscape, organizations are under more pressure than ever to keep pace with the widening attack surface. That’s why we’re so excited to bring extended support and coverage capabilities to our MDR customers with the launch of Rapid7 MDR for the Extended Ecosystem. With this addition, we’re extending our service to include triage, investigation, and response to alerts from third-party tools already in use within customer organizations.
This initial release will bring support for major EPPs such as Microsoft Defender for Endpoint, CrowdStrike Falcon, and SentinelOne, with plans to extend coverage to more third-party tools across cloud, identity, and network in the coming months.
Read this recent blog entry to learn how this extension of MDR sets Rapid7 apart and brings your team coverage, protection, and peace of mind.
Rapid7 named a Leader in IDC MarketScape: Worldwide SIEM for SMB and Enterprise
We’re excited to share we’ve been recognized as a Leader in the IDC MarketScape: Worldwide SIEM for SMB 2024 Vendor Assessment (doc #US52038824, September 2024) and the IDC MarketScape: Worldwide SIEM for Enterprise 2024 Vendor Assessment (doc #US51541324, September 2024). We’re proud that IDC highlights InsightIDR’s superior threat detection content, ease of implementation, and tangible ROI – all areas where we continually invest to provide users with a streamlined, complex-free experience.
To our customers: Thank you. Your partnership, feedback, and trust fuels our dedication to delivering the detection and response functionalities you need to take command of your attack surface and keep your organization safe. Read more about the reports here.
Intuitive log search enhancements to empower practitioners of all levels
Collecting, analyzing, and correlating logs from various sources is table stakes in identifying potential threats, detecting malicious behaviors, and responding to incidents effectively. Within InsightIDR we continue to enhance our Log Search functionality to empower you to go beyond simply correlating logs so you can feel confident securing your organization and enhancing your security posture.
Reformatted Log Search not only optimizes view and streamlines accessibility, but it reduces friction with notable enhancements:
- Pre-computed queries auto-run in less than half a second and can be leveraged from our OOTB library of queries or built custom using “groupby” or “calculate” commands.
- Automatic key suggestions are provided to analysts during query building based on the log selection to ensure faster time to investigate (as opposed to recalling and populating individually).
- Using the select clause, you can leverage new key suggestions to choose those to include in your search results. You can also customize their names and order.
The latest research and intelligence from Rapid7 Labs
Ransomware Radar Report: Findings and insights into the booming ransomware space
According to Rapid7 Labs Ransomware Radar Report, ransomware continues to evolve at a rapid pace. With the first half of 2024 seeing a +67% increase in the average number of ransomware groups actively posting to leak sites each month, it doesn’t appear that things are slowing down.
The report offers analysis and insights to help security practitioners understand and anticipate the latest developments around ransomware attacks. This research is based on data from Rapid7’s Incident Response and Rapid7 Labs teams as well as thousands of publicly reported ransomware incidents observed from January of 2023 through June of 2024.
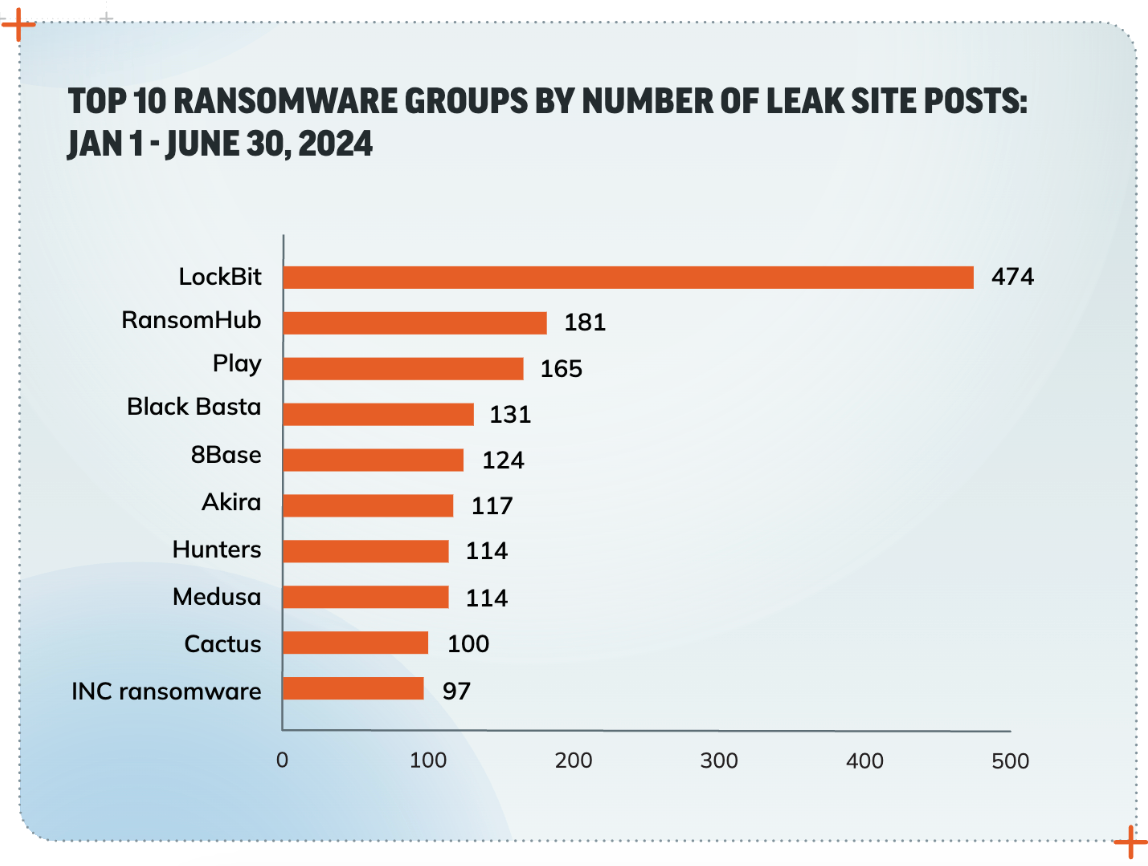
Read the Ransomware Radar Report now to learn the key takeaways for keeping your organization safe from ransomware.
Emergent Threat Response: Real-time guidance for critical threats
Rapid7’s Emergent Threat Response (ETR) program from Rapid7 Labs delivers fast, expert analysis and first-rate security content for the highest-priority security threats to help both Rapid7 customers and the greater security community understand their exposure and act quickly to defend their networks against rising threats.
In Q3, Rapid7’s Emergent Threat Response team provided expert analysis, InsightIDR and InsightVM content, and mitigation guidance for multiple critical, actively exploited vulnerabilities and widespread attacks:
- July 29: VMware ESXi CVE-2024-37085 Targeted in Ransomware Campaigns
- September 5: Rapid7 discovered and worked with the vendor to disclose CVE-2024-45195, a remote code execution vulnerability in Apache OFBiz
- September 9:
- Multiple Vulnerabilities in Veeam Backup & Replication
- CVE-2024-40766: Critical Improper Access Control Vulnerability Affecting SonicWall Devices
- September 19: High-risk vulnerabilities in common enterprise technologies, including Adobe ColdFusion CVE-2024-41874, Broadcom VMware vCenter Server CVEs (CVE-2024-38812, CVE-2024-38813), and Ivanti Endpoint Manager CVE-2024-29847
- September 26: Multiple Vulnerabilities in Common Unix Printing System (CUPS)
Follow along here to receive the latest emergent threat guidance from our team.
Stay tuned for more!
As always, we’re continuing to work on exciting product enhancements and releases throughout the year. Keep an eye on our blog and release notes as we continue to highlight the latest in product and service investments at Rapid7.
Try Rapid7's Surface Command ▶︎
Access this hands-on, read-only experience of Surface Command to see how your team can accelerate high-risk asset identification, prioritization, and remediation.

