In today’s threat landscape, where cyber-attacks are increasingly sophisticated and pervasive, organizations face the daunting challenge of securing a constantly expanding attack surface. Traditional vulnerability management (VM) programs, while necessary, are no longer sufficient on their own. They often struggle to keep pace with the dynamic nature of threats and the complexity of modern IT environments.
This is where continuous threat exposure management (CTEM) comes into play – an approach that shifts the focus from merely identifying vulnerabilities to understanding and mitigating exposures across the entire attack surface.
Implementing a continuous threat and exposure management process
CTEM is a term originally coined by Gartner, who defined it as, “a five-stage approach that continuously exposes an organization's networks, systems, and assets to simulated attacks to identify vulnerabilities and weaknesses.”
The five stages of CTEM as defined by Gartner are:
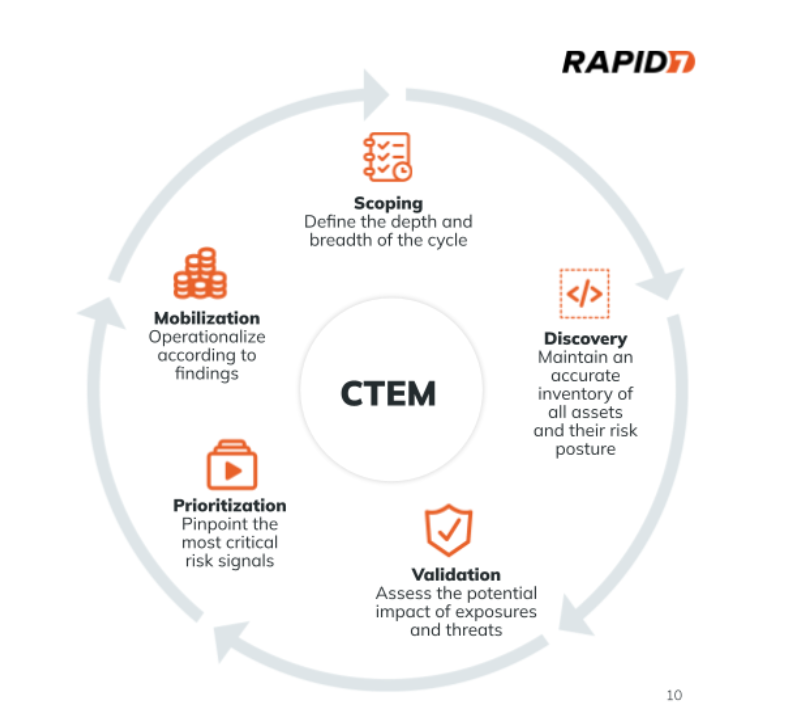
- Scoping: This involves understanding the full threat landscape by incorporating tools like external attack surface management (EASM) and network scanning. However, it emphasizes the need to think in terms of business context, focusing on crown jewels, critical applications, and understanding what matters most to the organization.
- Discovery: This stage focuses on discovering assets and profiling the associated risks. It requires visibility into both cloud and on-premises environments and extends beyond identifying vulnerabilities to include coverage gaps, misconfigurations, and other security risks.
- Prioritization: Since not all risks can be addressed simultaneously, this phase involves prioritizing issues based on a combination of factors like severity, exploitability, and potential business impact, to determine what should be tackled first.
- Validation: This stage emphasizes investing in tools that help validate security controls and map potential attack paths. It includes the use of breach and attack simulation (BAS) tools, continuous assessment services, controls monitoring, and attack path mapping to test the effectiveness of existing defenses.
- Mobilization: The final stage is about taking action. It includes both automation of responses and fostering cross-organizational alignment to ensure that remediation efforts are executed effectively and in sync with business priorities.
This framework helps organizations continuously manage and reduce their exposure to threats in a way that is strategic and aligned to the business.
The role of exposure assessment platforms (EAPs) in CTEM
Exposure assessment platforms (EAPs) are essential to a successful CTEM program. They continuously identify and prioritize exposures, such as vulnerabilities and misconfigurations, across a broad range of asset classes. By consolidating and contextualizing data from various sources, EAPs provide a more comprehensive view of an organization’s risk landscape. This enables security teams to prioritize remediation efforts based on factors such as asset criticality, business impact, and the likelihood of exploitation.
Gartner's insights into EAPs underscore their importance in modern cybersecurity strategies. By delivering a centralized view of high-risk exposures, EAPs empower organizations to take decisive actions to prevent breaches. They also enhance operational efficiency by offering a unified dashboard that tracks the lifecycle of vulnerabilities and other exposures.
How Rapid7 Exposure Command supports modern vulnerability management programs
Exposure Command is designed to bridge the security-visibility gap many organizations face. By integrating the capabilities of an EAP into a comprehensive security platform, Exposure Command enables organizations to modernize their VM programs and align them with the principles of CTEM.
Exposure Command can help organizations achieve this transformation in a few ways:
- Consolidated view of exposures from the inside out and outside in: Exposure Command provides a single, consolidated view of all assets and identified exposures from an internal and external perspective, including vulnerabilities, misconfigurations, and other risk signals. This unified view reduces the overhead associated with managing multiple tools and platforms, enabling security teams to focus on what matters most: mitigating the most critical threats.
- Vendor-agnostic approach: As organizations adopt a CTEM approach, they require tools that can evaluate a wide range of exposure telemetry, including security control configurations. Exposure Command excels in this area by leveraging data from existing endpoint and network investments to create a more accurate, situational picture of the organization’s risk landscape. This holistic view is crucial for making informed decisions about where to focus remediation efforts.
- Contextualized risk prioritization: Traditional VM programs often rely on CVSS scores to prioritize vulnerabilities, which can lead to misaligned efforts. Exposure Command, however, incorporates threat intelligence, asset criticality, and business impact into its risk-prioritization algorithms. This results in a more accurate and actionable understanding of which exposures pose the greatest risk to the organization.
- Identify exploitability and potential for lateral movement: Exposure Command provides the contextual asset enrichment that enables effective threat detection, investigation, and response. The platform showcases how an attacker might exploit vulnerabilities and provides guidance on how to prevent such incidents.
- Automated response workflows and deep ecosystem integration: One of the key benefits of Exposure Command is its ability to automate and streamline workflows. By integrating with existing security tools and platforms, Exposure Command can automatically ingest and analyze exposure data, reducing the manual effort required to maintain a VM program. This automation not only improves efficiency but also ensures security teams have access to the most up-to-date information. More and more we’re running into non-patchable systems too, and this deep integration and ability to provide bi-directional workflows enables more effective mobilization across teams, giving actionable feedback to those around the organization who have the ability to execute the necessary remediation actions.
While the benefits of Exposure Command are clear, it’s important to recognize that its effectiveness is tied to the maturity of the organization’s CTEM processes. If these processes are broken or immature, the value of Exposure Command may be limited. However, by adopting an outcome-driven approach that scopes the most critical aspects of the business and correlates asset context with dynamic risk ratings, organizations can maximize the benefits of Exposure Command.
Furthermore, the platform’s ability to integrate with a wide range of tools ensures it can enhance existing security programs, rather than requiring a complete overhaul. This makes it an ideal solution for organizations looking to modernize their VM programs and adopt a more proactive approach to threat management. As you look to strengthen your organization’s cybersecurity posture, consider how Rapid7 Exposure Command can help you bridge the security visibility gap and take a more proactive approach to managing your threat landscape.
Learn More about Rapid7's Exposure Command ▶︎
Confidently identify and prioritize exposures from endpoint to cloud with full attack surface visibility and threat-aware risk context.

