As part of our ongoing efforts to monitor emerging cyber threats, we have analyzed the activities of CyberVolk, a politically motivated hacktivist group that transitioned into using ransomware and has been active since June 2024. Unlike traditional ransomware groups, CyberVolk initially positioned itself as a hacktivist organization, and then started to use ransomware as a tool for retaliation. The group openly declares allegiance to Russia and operates within a broader hacktivist movement, launching attacks in response to geopolitical events. This report offers an in-depth analysis of CyberVolk’s ransomware tactics, underlying motivations, and technical behaviors.
Rapid7 Labs has an ongoing commitment to help organizations understand and mitigate risk from the complex world of ransomware, and this includes highlighting these newer groups. In this post we’re going to focus on CyberVolk's shift from a hacktivist group to one that now uses ransomware as a key tool in its operations.
Intro to the CyberVolk group
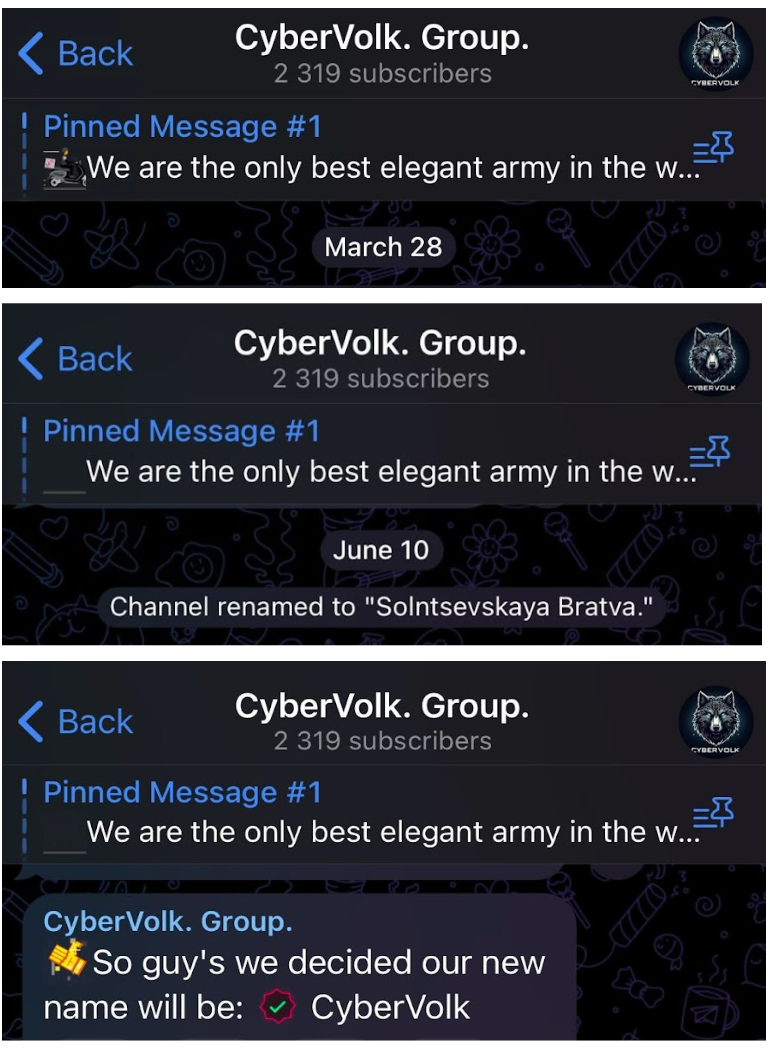
CyberVolk emerged in June 2024 as a hacktivist group associated with pro-Russian activities. Before settling on its current identity it went through several name changes. Initially known as GLORIAMIST India on March 28, 2024, the group rebranded itself as Solntsevskaya Bratva on June 10, 2024. However, this name was short-lived, and on June 23, 2024, the group adopted the name CyberVolk. Their operations escalated after the arrest of members from the hacktivist group NoName57(16), known for targeting NATO-aligned countries. In response, CyberVolk, alongside more than 70 affiliated hacktivist groups, launched coordinated Distributed Denial of Service (DDoS) and ransomware attacks against Spain, which had arrested the NoName57(16) members. These attacks are part of a broader strategy to retaliate against governments opposing Russian interests.
CyberVolk uses a combination of ransomware and DDoS attacks to undermine their targets. Spanish institutions have been a primary focus, with 27 entities reportedly affected since the campaign began.
This isn’t the first time a hacktivist group has taken a stroll down the dark side. Just last year, we covered the GhostLocker group, which made an attempt to transition from the hacktivist realm to ransomware-as-a-service (RaaS). Side bar: their debut into the ransomware world didn’t exactly go as planned. After realizing that success in the RaaS game wasn’t in their best interest, they swiftly pivoted back to their old hacktivist ways, likely with a sigh of relief. But let's go back to the CyberVolk (with "Volk" meaning "wolf" in Russian).
Technical analysis of CyberVolk ransomware
We analyzed a sample of the CyberVolk ransomware.
| SHA256 | 102276ae1f518745695fe8f291bf6e69856b91723244881561bb1a2338d54b12 |
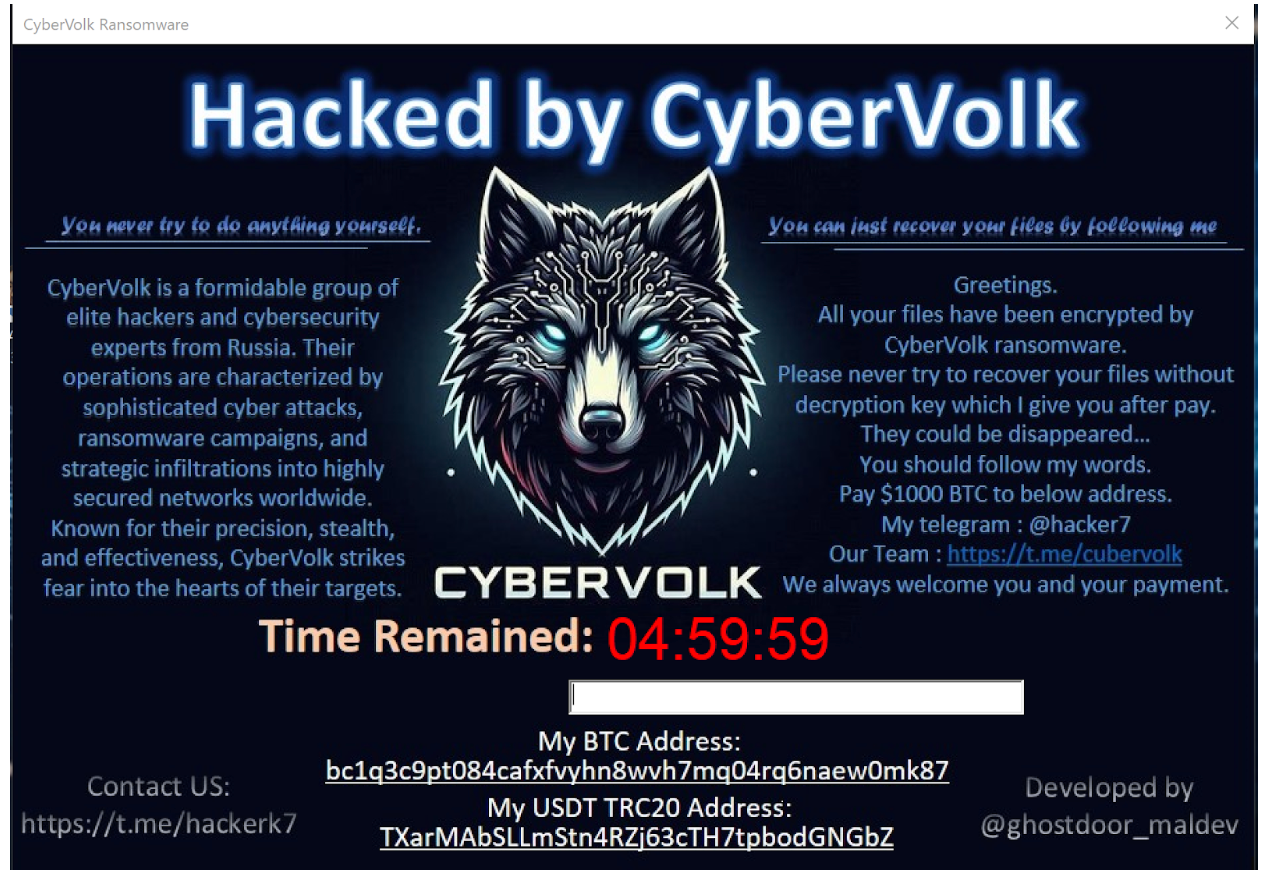
CyberVolk follows a standard execution flow typical to ransomware strains. One of the first actions it takes is saving an image file tmp.bmp to C:\Users\USER\AppData\Local\Temp\tmp.bmp and changing the victim’s desktop wallpaper — interestingly, this occurs before any files on the system are encrypted.
The ransomware then creates multiple threads to handle various tasks, including:
- User interaction: A thread manages the interaction with the victim, displaying dialog boxes for the ransom message, decryption key entry, and cryptocurrency payment options for BTC (Bitcoin) and USDT ERC20. The addresses used are:
- BTC: bc1q3c9pt084cafxfvyhn8wvh7mq04rq6naew0mk87
-
USDT: TXarMAbSLLmStn4RZj63cTH7tpbodGNGbZ At the time of writing, the BTC wallet had a balance of 0, and the USDT wallet held 34.79 USDT.
-
Task manager monitoring: Another thread checks repeatedly if Task Manager is running by searching for a window with the class name "TaskManagerWindow." If found, it attempts to kill the process by sending a WM_CLOSE message. This action requires the ransomware to run with escalated privileges.
- File scanning and encryption: CyberVolk performs a systematic scan of all available drive letters (from a to z) to identify valid drives for encryption. Once the encryption routine is triggered:
- Files on the infected system are encrypted and given the .cvenc extension.
-
The ransomware methodically scans directories and subdirectories, encrypting files as it proceeds.
- Decryption key management: After encrypting the files, CyberVolk presents the victim with an interface to input a decryption key following ransom payment. Here’s how the decryption process works:
- Key validation: The ransomware checks if the entered decryption key is exactly 36 characters long. However, despite the full key being 36 characters, only the first 16 characters are passed to a substitution function that transforms part of the key using a predefined substitution table.
- Substitution function: The function processes multiple encrypted string arrays and performs character substitution based on a preset character set. It compares each character from the first 16 characters of the entered key with encrypted string arrays and replaces them using the substitution table.
- Writing the key: The transformed output is written to a file named dec_key.dat, which is then used to complete the decryption process. If the decryption key passes all checks, the ransomware decrypts the files.
- Cleanup: After successful decryption, it removes files like dec_key.dat and time.dat from C:\Users\USER\AppData\Roaming\ to cover its tracks.
Experiment: Decryption key testing with CyberVolk ransomware
As part of a small experiment, we attempted to execute the CyberVolk ransomware with a pre-created dec_key.dat file placed in C:\Users\USER\AppData\Roaming\. This file contained hardcoded strings we found in the code, such as fc99bb1c28a5ae006e567faf4cfc0d707c1528e and ce12f0967bd216d248cafda3d46ad1368d9f3dee.
Upon running the malware, the presence of the file successfully triggered the decryption routine. However, despite the original file names being restored, the files themselves were empty.
In another experiment, we manually entered 36 random characters into the decryption key dialog box. Again, this triggered the decryption process, and although the file names were restored, the files remained empty.
Additionally, the ransomware claims that it will delete files if an incorrect decryption key is entered. We tested this by entering an invalid key (aaaa). The malware displayed a warning, but when we proceeded, all files remained encrypted, and none were deleted.
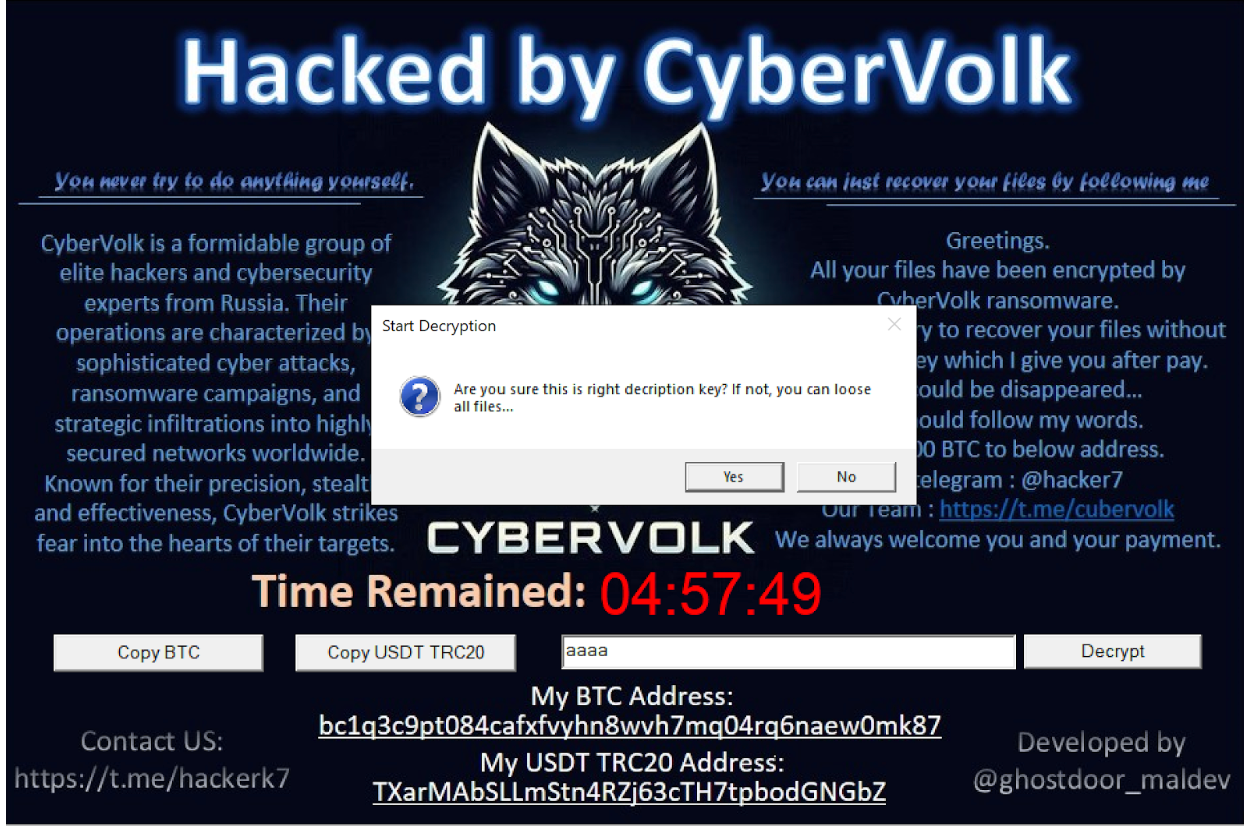
CyberVolk's decryption routine seems to have a weakness in its validation process, allowing it to proceed with decryption even with incorrect or random keys. However, without the correct key, the files are rendered unusable, suggesting that the key validation might only partially function or that the ransomware is designed to deceive victims into thinking decryption is occurring, when in reality, the files remain damaged. This could be a design flaw or a deliberate tactic to further frustrate victims.
The fact that files are not deleted as promised when an incorrect key is entered also indicates a discrepancy between the ransomware’s claims and its actual behavior. This could either be a design flaw or a deliberate tactic to further confuse and frustrate victims. Ultimately, even if the ransomware initiates decryption, without the correct key, files remain damaged and unusable.
Ransom note
After encryption, a file named CyberVolk_ReadMe.txt is placed in every affected folder. The ransom note contains the following message:
All your files have been encrypted by CyberVolk ransomware.
Do not attempt to recover your files without the decryption key, which I will provide after you make the payment.
Failure to do so may result in your files being permanently lost.
Follow my instructions carefully.
Payment Details:
Transfer $1000 in Bitcoin to the following address.
You can contact me via Telegram: @hacker7
Our team is available at https:[//]t.me/cubervolk. We look forward to receiving your payment.
The ransom note directs victims to a non-existing channel https:[//]t.me/cubervolk. Looks like the ransomware creators were in such a rush to demand the ransom that they forgot to double-check their own link.
Code reuse from Babuk ransomware
Our comparison of CyberVolk and Babuk ransomware using BinDiff revealed some similarities, particularly in cryptographic routines and system-level interactions. For example, the function CryptAcquireContextW and other cryptographic setups show significant overlap between the two, indicating that CyberVolk's developers likely reused Babuk’s encryption framework.
However, CyberVolk has added unique functionality, such as:
- Anti-analysis techniques: Efforts to evade detection through Task Manager termination.
- AES encryption: Unlike Babuk, CyberVolk incorporates the AES encryption algorithm, enhancing its cryptographic capabilities and further differentiating the two strains.
Conclusion
CyberVolk ransomware shows off the usual ransomware tricks complete with a few bugs for good measure. By reusing some of Babuk’s code — particularly in its cryptographic routines — it’s clear that ransomware authors are getting creative with their remix skills, building on old frameworks to make their threats just a little more polished.CyberVolk also introduces some original features, such as attempting to terminate system processes like Task Manager. It succeeds in this task when run with elevated privileges.
Our decryption tests revealed that ransomware has some flaws. CyberVolk’s key validation is weak enough that even random keys trigger the decryption routine, though files remain unusable without the correct key. Despite its warnings about deleting files if an incorrect key is entered, we found that files remained encrypted but were not deleted, highlighting a gap between what the ransomware claims and what it actually does.
Still, CyberVolk has caused significant disruption, particularly in Spain. With its mix of DDoS and ransomware attacks, it’s becoming a more serious threat. As the group refines its tactics, cybersecurity professionals should keep a close eye on its continued evolution.
Cybersecurity professionals should keep this ransomware on their radar. Despite its bugs, CyberVolk is evolving and has already proven effective, causing significant damage to entities in Spain. It adds enough new tricks to the traditional ransomware formula to evade detection and create serious headaches for its victims.
Read up on additional ransomware groups and get other insights from Rapid7 Labs here.
