Over the 15 years I spent as a practitioner and consultant prior to joining Rapid7, a metric that I found to be ever elusive was a true custom prioritization score. You could get close- with enough time, energy, spreadsheets, and logs. But even then it wasn’t without fault. There were still questions like “what if that data isn’t there?” or “which tool do you trust most”. Ultimately it was a challenge and with every vendor having their own risk scores and priority matrices and scoring models, it was hard to make those predetermined elements fit into your particular environment with all the nuances you cared about.
With our recent launch of the Command Platform, Rapid7 now delivers a more comprehensive view of your attack surface, with transparency that you can trust. Anchored by Surface Command, our new unified asset inventory and attack surface management product, customers can get a more complete, vendor agnostic view of their internal and external attack surface—at a disruptive, all-in value.
Surface Command combines internal and external monitoring to build a 360-degree view of your entire environment, with market-leading Cyber Asset Attack Surface Management (CAASM) and External Attack Surface Management (EASM) capabilities in one unified offering. Surface Command combines external visibility from Rapid7’s native internet scanners with a detailed inventory of all your internal assets, continuously ingested and updated from a wide range of security and IT tools.
Surface Command’s ability to both understand and model your entire attack surface fundamentally changes how Rapid7 can help new and existing customers alike as a security partner. That’s why I’m excited to talk about just some of the features and use cases that really stood out to me.
It all starts with a foundation of complete attack surface visibility
If you want to have a true measure of risk or prioritization within your environment, you first have to be able to consume data from multiple sources, companies, and partners. Most exposure management tools today rely on the data being sourced from that vendor itself. The issue with this approach is it leaves out data competing vendors or solutions may have to bring in as well.
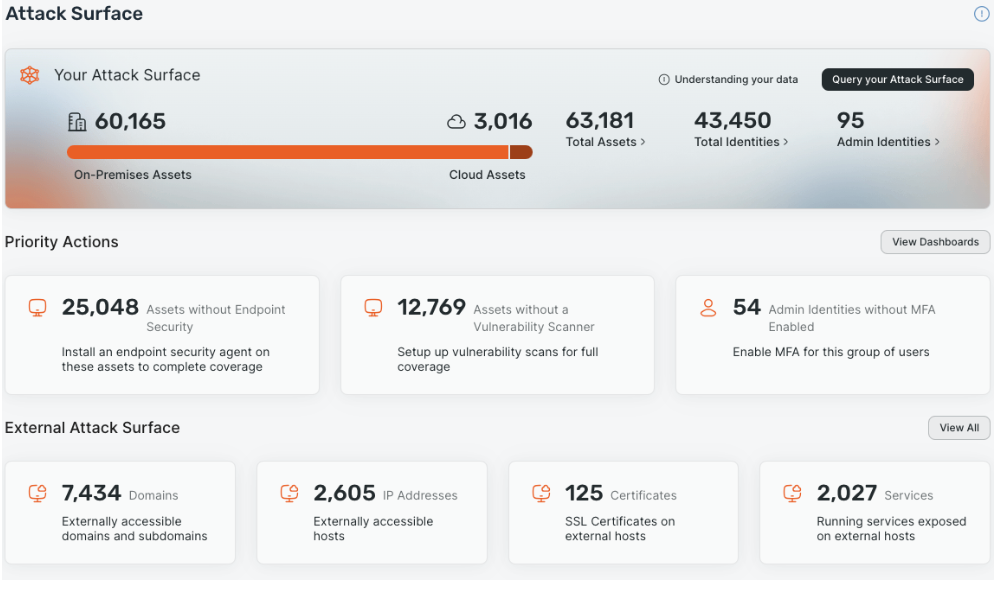
Conversely, Surface Command is wholly vendor agnostic. This allows you to bring in all the data you need from every security tool in your current technology stack, with over 110 connectors available out-of-the-box at time of writing this post and rapidly more being added by the day. You can find and keep up with our growing list of connectors here.
Obviously aggregating all that data means dealing with a substantial amount of information, some of which may be in conflict. So how do we handle this? A powerful, customizable, correlation engine.
Unmatched customizability with a tunable correlation engine
Immediately upon seeing the correlation engine, I knew we had something special. The biggest challenge with large datasets that gather from different tools and vendors is that each tool believes it is correct, as it should. However, in practice, we all know that some tools are great for a lot of the data it provides with some of the other data being… okay. This is very apparent when looking at CMDBs or GRC tools. They struggle to have a clean golden record because attributes are updated by tools with less fidelity than other tools that had already populated that field.
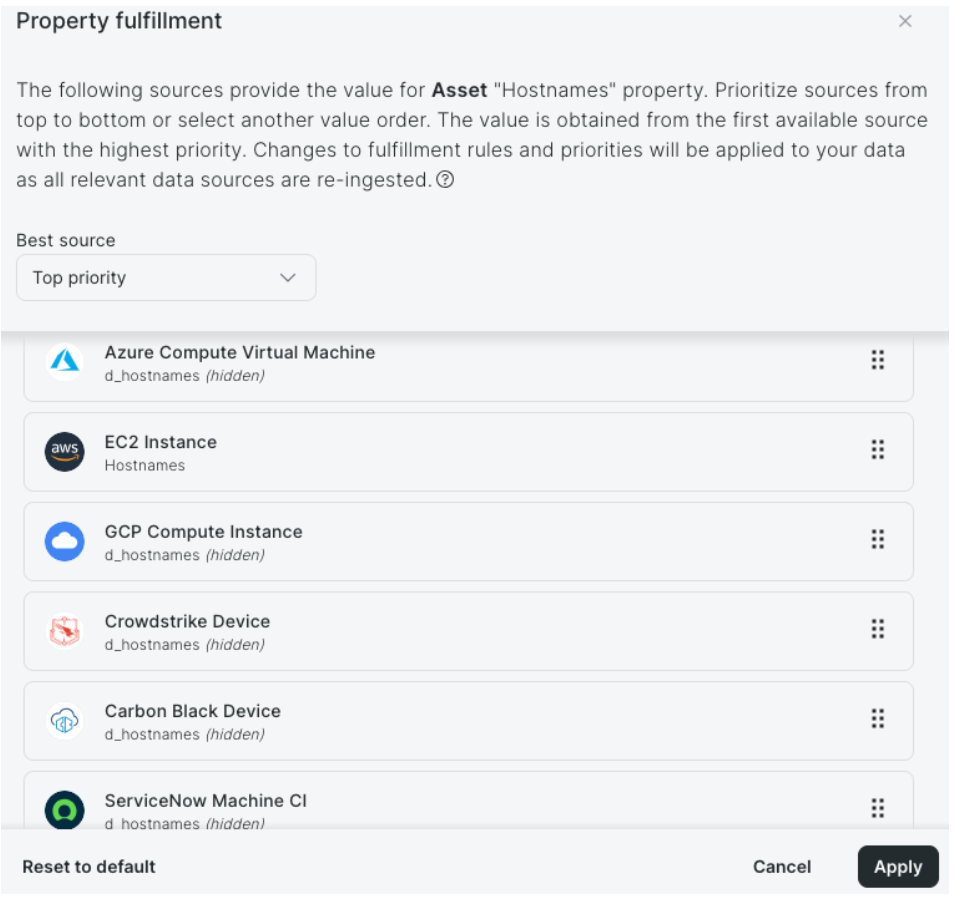
With Surface Command, this is a thing of the past. Each correlated value, such as hostnames, Operating System, Owners, etc. that would normally come from a variety of locations can be individually tuned. Rather than the traditional “last in wins” approach, we have a correlation priority strategy that you get to pick which tool you trust most for that single attribue. This allows for precision when creating your golden record for searching, feeding into your CMDB from a single source now, and also for queries within Surface Command.
Building complex queries with cypher
Surface Command runs on a Graph database and leverages Cypher for the query language. The UI has a very simple and intuitive interface that supports most common query use cases, but you can also select the “advanced query” option to see what that Cypher would look like. I personally used this to teach myself how to build some queries over the course of a week or two. Why? Because I knew what I was after: a custom vendor agnostic prioritization score.
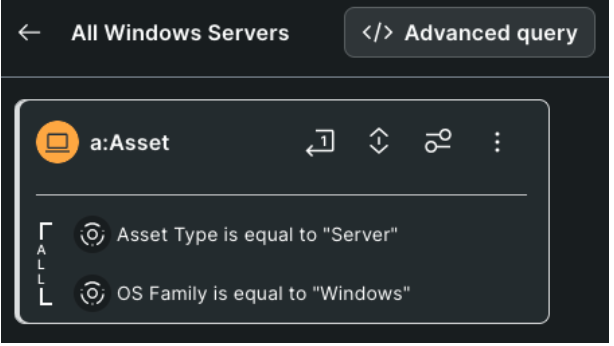
I was able to use the interface above to search through any of the correlations and data points I wanted to filter on. From there I could execute my query, view my results, and then even click the Advanced Query button to move into a Cypher view, as shown below. The ability to move from UI to Query that easily is a perfect way to increase your familiarity with the tool and data.
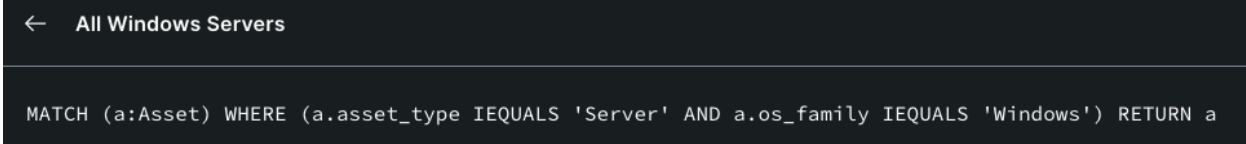
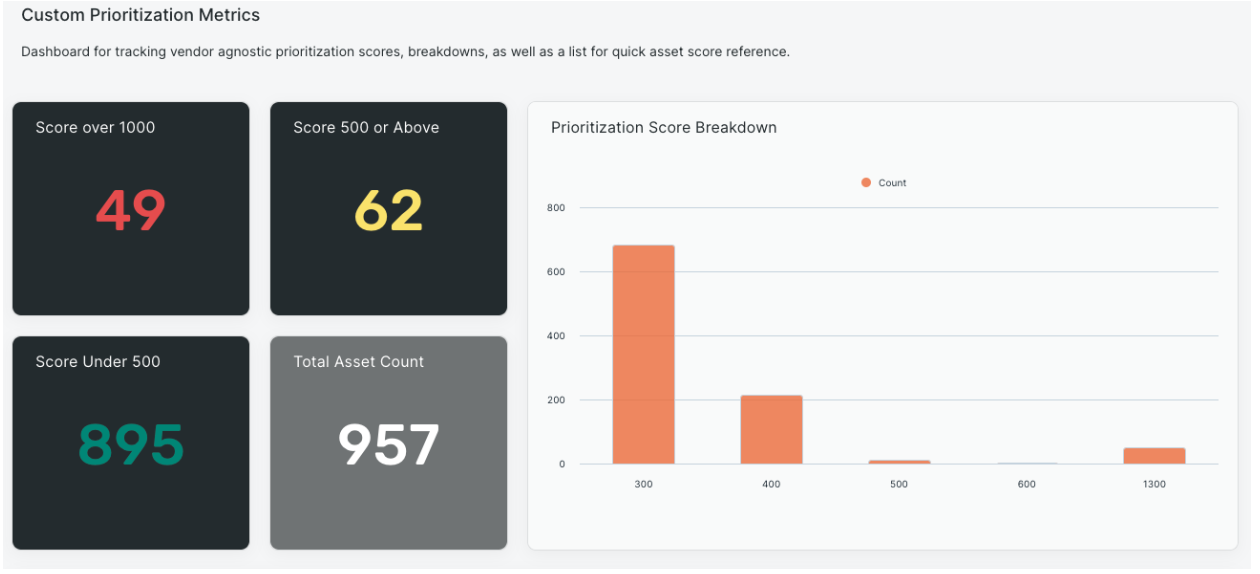
I started building my query and quickly saw the power of Surface Command. I first looked for mitigations (a searchable attribute) looking for assets without certain controls on them like Antivirus/Antimalware, Vulnerability Scans, etc. Again, this is all vendor agnostic. I didn’t care “which” AV/AM solution, just that it had one. I didn’t care if the vulnerabilities came from Rapid7, Defender, Tanium, Crowdstrike, etc. I just needed to know something was on the host. If not, increase that asset’s prioritization. Or pulling in specific elements like the Crowdstrike Status, something not correlated, but still within the dataset so easy to add. Testing all the IPs that I know from agents running on the asset, what Meraki knew, what AWS/Azure/GCP knew, and seeing if a public IP was on the asset. With each test I created, I assigned a weighing mechanism and score that I determined for my use case. This was it, it was what I had been chasing for so many years.
The Result: A tailored risk score built for YOUR business needs
What you can create is that custom vendor-agnostic prioritization score. You choose which tools you trust most for the attributes in your environment in a single CAASM platform that is vendor agnostic. You decide which data points are priorities to you and your security program. You determine how you want to view those data points and what scores to assign to them. You take control of what a prioritization score should look like, tailored to you and your colleagues at your company taking into account the things you care about most.
As I stated earlier, when I first saw Surface Command and got my hands on it, I knew we had something special. Think about the use case I have here, but let your imagination run. Maybe it’s not just a score you want, maybe it’s dashboards, exports, or feeding back into a CMDB or GRC tool. Maybe it’s taking actions with the data, looking for blindspots where coverage is lacking, or even planning for a budget to see how much of a license you are using or need.
We’d love to show you Surface Command and all that we think it can do, but we’d also love to hear how you would use it! Thanks so much for taking the time to read through this with me today and look forward to speaking with you soon!
Try Rapid7's Surface Command ▶︎
Access this hands-on, read-only experience of Surface Command to see how your team can accelerate high-risk asset identification, prioritization, and remediation.
