Pool Party Windows Process Injection
This Metasploit-Framework release includes a new injection technique deployed on core Meterpreter functionalities such as process migration and DLL Injection.
The research of a new injection technique known as PoolParty highlighted new ways to gain code execution on a remote process by abusing Thread-Pool management features included on Windows kernel starting from Windows Vista. During our research effort to integrate the new injection technique inside the Meterpreter code-base we encountered some technical challenges we would like to share.. Currently Meterpreter makes use of the (in)famous system feature provided by Microsoft, the kernel32!CreateRemoteThread to achieve code injection. Although nowadays every EDR should be able to prevent an injection using this API call, this still is the most features rich way to inject code in a target process. Our goal during the porting of this technique was to find the variant more suitable for our needs:
- Able to pass a parameter pointer
- Able to be injected and later executed, like a Suspended Thread
- Be able to be injected from and to a WoW64 processes
- Leave less footprints as possible on the target process
From the Original Pool Party PoC we selected three candidates:
- TP_WAIT_INSERTION
- TP_DIRECT_INSERTION
- WORKER_THREAD_FACTORY_OVERWRITE
In order to achieve the same flexibility offered by the CreateRemoteThread an intermediate stub was developed in order to have correct parameter ordering, controlled execution over a duplicated handle and cleanup of the injection after successful execution making the migration chain looking like:
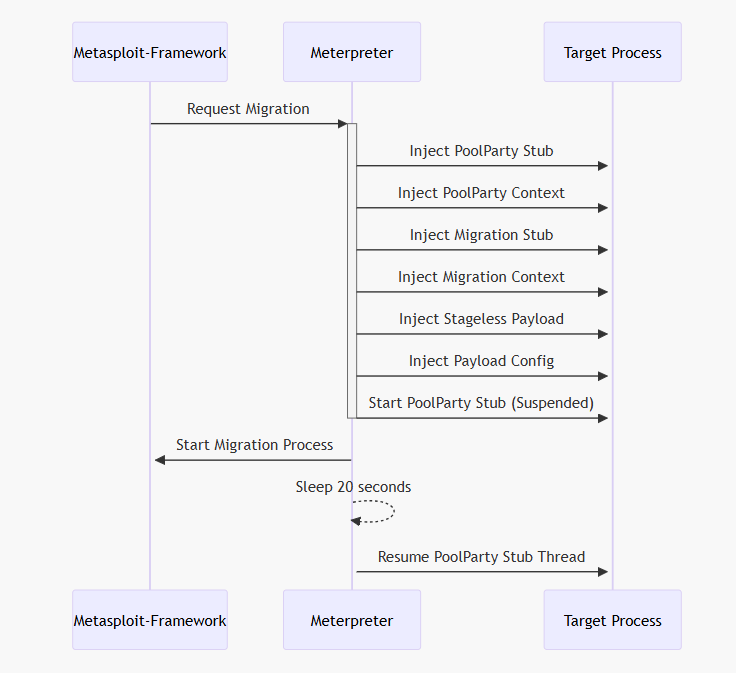
Pool-Party Stub Details
Argument Passing
The argument passing depends on the variant used, some of them allows argument passing but some doesn't, during our research we investigated and tested the following two variants for argument passing.
- TP_WAIT_INSERTION
- TP_DIRECT_INSERTION
Even if the TP_WAIT_INSERTION supports the argument pointer passing, the format of the WaitCallback expects the parameter to be on the second position instead of the first one, making necessary in an intermediate stub to avoid hot-patching the lpMigrationStub provided by framework.
To have an unified stub that could be used across all variants we decided to not use variant-specific argument passing and decided to retrieve our data from the end of the shellcode.
Delayed Execution
To achieve a suspended-like thread on the PoolParty we came up with the idea of creating and duplicating the HANDLE of an hEvent, in this way, when we perform the step 8. In our migration chain, the execution is delayed by the WaitForSingleObject inside the target process and later released by the Meterpreter using SetEvent against the duplicated handle.
Execution Cleanup
On the original PoC's shellcode, the execution ends inside an infinite loop that prevents thread from returning successfully. In our investigation we observed different outcomes depending on the variant used to achieve the injection. We were able to successfully clean up the execution on the TP_DIRECT_INSERTION variant.
Injection Features and Limits
Currently the PoolParty injection works with all the 64-bit systems having a Windows Kernel >= 10.0, it supports injection from x64 -> x64 and WoW64 -> x64. Currently there is no support for systems between Windows Vista and Windows 8.1 and the WoW64 injections are partially implemented due to some security restrictions.
Feel free to share with us feedback, issues or requests for further coverage by opening an Issue on GitHub or by sending a message to our Slack Metasploit server.
New module content (3)
WordPress Ultimate Member SQL Injection (CVE-2024-1071)
Authors: Christiaan Swiers and Valentin Lobstein
Type: Auxiliary
Pull request: #19488 contributed by Chocapikk
Path: scanner/http/wp_ultimate_member_sorting_sqli
AttackerKB reference: CVE-2024-1071
Description: This adds a new auxiliary module to exploit an unauthenticated SQL injection vulnerability in the Ultimate Member plugin for WordPress versions 2.1.3 to 2.8.2. The vulnerability allows an unauthenticated attacker to extract sensitive data via the sorting parameter.
WordPress wp-automatic Plugin SQLi Admin Creation
Authors: Rafie Muhammad and Valentin Lobstein
Type: Exploit
Pull request: #19489 contributed by Chocapikk
Path: multi/http/wp_automatic_sqli_to_rce
AttackerKB reference: CVE-2024-27956
Description: This adds a new exploit module for the SQL injection vulnerability in the WordPress wp-automatic plugin, affecting versions prior to 3.92.1. The vulnerability allows unauthenticated attackers to inject SQL commands, enabling them to create a malicious administrator account. Using the newly created admin account, the attacker can upload a plugin and achieve remote code execution.
Advanced Browser Data Extraction for Chromium and Gecko Browsers
Author: Alexander "xaitax" Hagenah
Type: Post
Pull request: #19506 contributed by xaitax
Path: windows/gather/enum_browsers
Description: Adds a new post-exploitation post/windows/gather/enum_browsers module which extracts sensitive browser data from both Chromium-based and Gecko-based browsers on the target system. It supports the decryption of passwords and cookies using Windows Data Protection API (DPAPI) and can extract additional data such as browsing history, keyword search history, download history, autofill data, credit card information, browser cache and installed extensions.
Enhanced Modules (1)
Modules which have either been enhanced, or renamed:
- #19527 from Chocapikk - Updates the exploit/multi/http/wp_givewp_rce module with a patch bypass. This module is now compatible with GiveWP version 3.16.1.
Enhancements and features (2)
- #19597 from zeroSteiner - Fix symlink and junction detection on Python windows Meterpreter.
- #19600 from adfoster-r7 - Updates the post windows modules gather/credentials/seamonkey, gather/credentials/chrome, and gather/enum_chrome as being superseded by windows/gather/enum_browsers.
Bugs fixed (3)
- #19551 from smashery - This fixes an issue when the LDAP session feature is enabled that caused the USERNAME and PASSWORD datastore options to be required, despite not being necessary when the configuration is set to kerberos or schannel.
- #19553 from smashery - This fixes a bug in modules that use Kerberos authentication where when the KrbOfferedEncryptionTypes datastore option was set, it would be ignored instead of used to select a compatible ticket from the cache.
- #19607 from adfoster-r7 - Fixes a bug that caused tables to render incorrectly when running under docker.
Documentation
You can find the latest Metasploit documentation on our docsite at docs.metasploit.com.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate
and you can get more details on the changes since the last blog post from
GitHub:
If you are a git user, you can clone the Metasploit Framework repo (master branch) for the latest.
To install fresh without using git, you can use the open-source-only Nightly Installers or the commercial edition Metasploit Pro
NEVER MISS AN EMERGING THREAT
Be the first to learn about the latest vulnerabilities and cybersecurity news.
Subscribe Now