The Lorex 2K Indoor Wi-Fi Security Camera is a consumer security device that provides cloud-based video camera surveillance capabilities. This device was a target at the 2024 Pwn2Own IoT competition. Rapid7 developed an unauthenticated remote code execution (RCE) exploit chain as an entry for the competition. On November 25, 2024, Lorex released a firmware update to resolve the five vulnerabilities that comprise the exploit chain reported by Rapid7. As of December 3, 2024, we are disclosing these issues publicly in coordination with the vendor.
Technical analysis
A detailed technical analysis for the exploit chain described in this blog can be found in Rapid7’s whitepaper here.
The accompanying source code for the exploit chain can be found here.
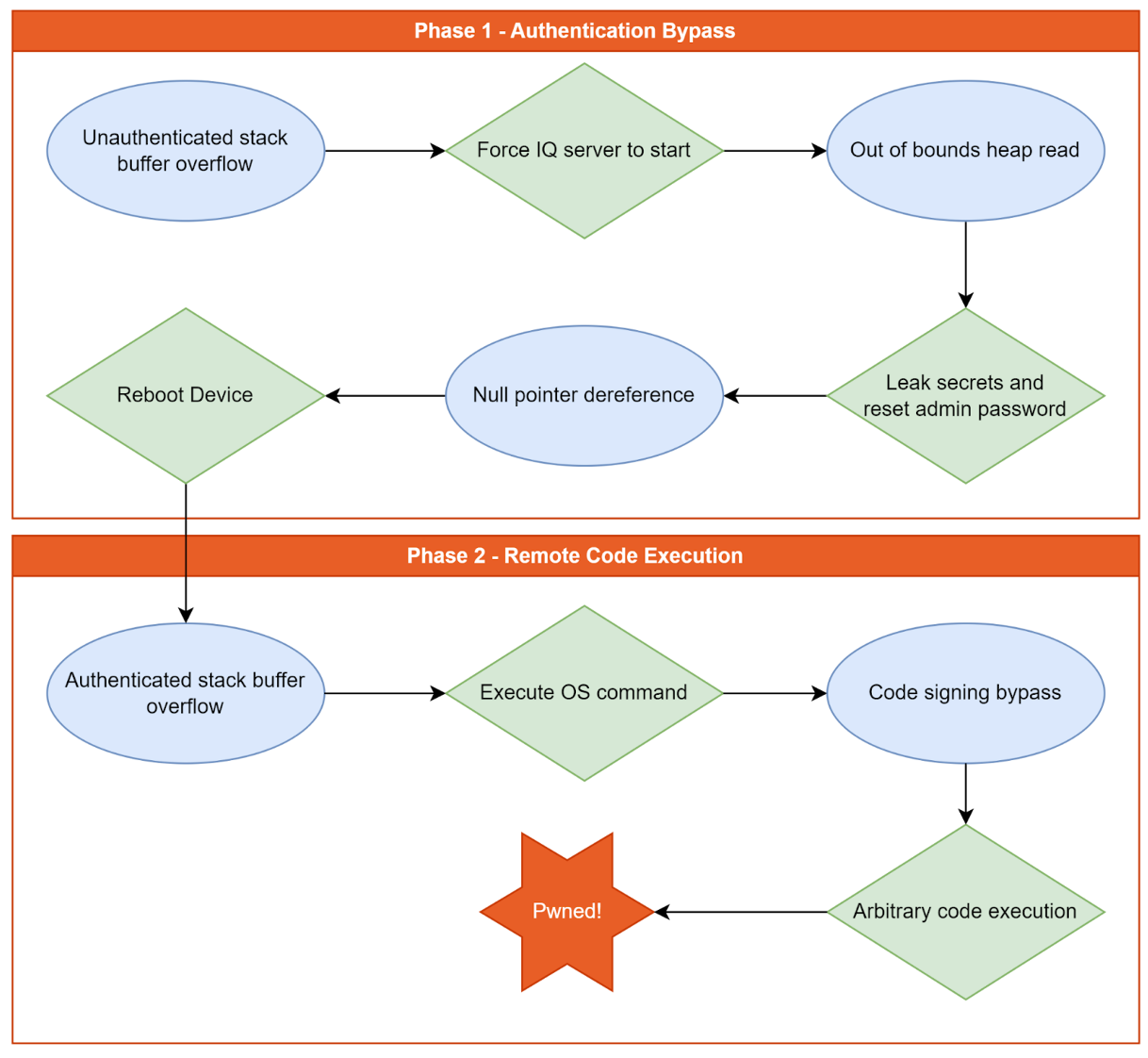
The exploit chain consists of five distinct vulnerabilities, which operate together in two phases to achieve unauthenticated RCE. The five vulnerabilities are listed below.
| CVE | Description | Affected Component | CVSS |
|---|---|---|---|
| CVE-2024-52544 | An unauthenticated attacker can trigger a stack-based buffer overflow. | DP Service (TCP port 3500) | 9.8 (Critical) |
| CVE-2024-52545 | An unauthenticated attacker can perform an out-of-bounds heap read. | IQ Service (TCP port 9876) | 6.5 (Medium) |
| CVE-2024-52546 | An unauthenticated attacker can perform a null pointer dereference. | DHIP Service (UDP port 37810) | 5.3 (Medium) |
| CVE-2024-52547 | An authenticated attacker can trigger a stack-based buffer overflow. | DHIP Service (TCP port 80) | 7.2 (High) |
| CVE-2024-52548 | An attacker can bypass code signing enforcements and execute arbitrary native code. | Kernel | 6.7 (Medium) |
Phase 1 performs an authentication bypass, allowing a remote unauthenticated attacker to reset the device's admin password to a password of the attacker's choosing. This phase leverages an unauthenticated stack-based buffer overflow, and an unauthenticated out-of-bounds (OOB) heap read vulnerability. The OOB heap read allows an attacker to leak secrets stored in the device’s memory that are required to compute a special code value; this code value is required for an administrator password reset to be performed. A null pointer dereference vulnerability is leveraged to force the device to reboot in order to allow the next phase to complete.
Phase 2 achieves remote code execution by leveraging the auth bypass in phase 1 to perform an authenticated stack-based buffer overflow and execute an operating system (OS) command with root privileges. This capability is then leveraged to write a file to disk and, in turn, bypass the device's code signing enforcement in order to execute arbitrary native code. Finally, the exploit will execute a reverse shell payload to give the remote attacker a root shell on the target device.
An overview of the two phases chained together can be seen below.
Impact
A remote unauthenticated attacker can leverage CVE-2024-52544, CVE-2024-52545, and CVE-2024-52546 (Phase 1) to reset a target device's admin password, to a password of the attacker’s choosing. With valid admin credentials, an attacker can then either view the live video and audio feed from the device, or proceed to leverage CVE-2024-52547 and CVE-2024-52548 (Phase 2) to achieve remote code execution with root privileges on the target device.
The below table lists the affected devices and firmware versions.
| Device | Firmware |
|---|---|
| W461AS-EG | 2.800.00LR000.0.R.210907 |
| W462AQ-EG | 2.800.00LR000.0.R.210907 |
| W461AS | 2.800.00LR000.0.R.210730 |
| W462AQ | 2.800.00LR000.0.R.210730 |
| W461AS-EG S2 | 2.800.0000000.3.R.20220331 |
| W462AC-EG S2 | 2.800.0000000.3.R.20220331 |
| W461AS | 2.800.0000000.3.R.202203 |
| W462AQ | 2.800.0000000.3.R.202203 |
| W461ASC | 2.800.030000000.3.R |
Credit
These vulnerabilities were discovered by Stephen Fewer, Principal Security Researcher at Rapid7 and are being disclosed in accordance with Rapid7’s vulnerability disclosure policy.
Vendor Statement
The following statement has been provided by the vendor.
Lorex Technology is dedicated to delivering the highest standards of protection and privacy for our customers and will collaborate with esteemed security experts to proactively identify and address potential vulnerabilities. In collaboration with Rapid7, we've been advised about one of our security cameras and successfully implemented a firmware update, which has fully resolved the identified security vulnerability.
Remediation
The following remediation steps have been provided by the vendor.
Our product team has decided to push the mandatory firmware updates to the devices. Upon opening Lorex app, users will be presented with the firmware update notice. User must accept the firmware update, and they cannot decline or postpone the firmware update. Camera will then flash new firmware and reboot. We advise that the users would not power down the camera during the firmware update. Once the camera reboots, the user can confirm that they have the latest version of firmware: V2.800.0000000.8.R.20241111
Disclosure timeline
October 29, 2024: Rapid7 contacts the vendor about the issues in this blog; vendor acknowledges.
October 31, 2024: Rapid7 shares disclosure write-up with the vendor.
November 4, 2024: Vendor indicates a patch is in development.
November 12, 2024: Rapid7 provides CVEs IDs for the issues identified.
November 13, 2024: Vendor verifies patch schedule.
November 19, 2024: Rapid7 and the vendor agree to a December 3, 2024 coordinated disclosure date.
December 3, 2024: This disclosure.
NEVER MISS AN EMERGING THREAT
Be the first to learn about the latest vulnerabilities and cybersecurity news.
Subscribe Now