Future-proofing the SOC: A CISO’s Perspective
Jeffrey Gardner, Practice Advisor - Detection & Response
Given the current cyber threat landscape, your in-scope attack surface extends way beyond your organizational perimeter to cloud services, IoT devices, your employee’s homes, and your suppliers and customers. Watch this session to understand how a more comprehensive approach to incident response can elevate the way you detect and respond to threats.

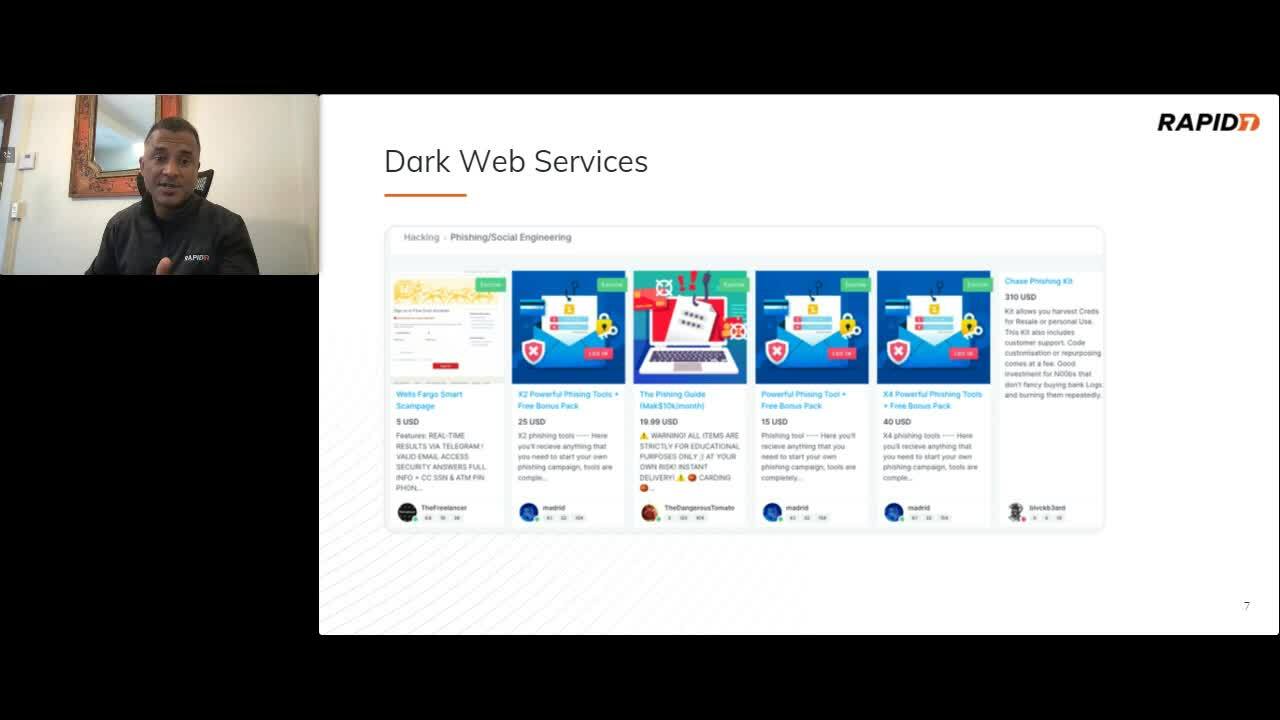
Threat Intelligence: Why it’s a Must-Have & How to Use it to Fortify Your Defenses
Mario Arrington, Senior Security Solutions Engineer II
It is no secret that there are lots of secrets on the Web. Unfortunately, some of these secret systems and software can be used to infiltrate your organization and steal/encrypt your data. This session will explore the latest tools, tactics, and techniques that threat actors are using to gain access to your organization’s data and how you can mount a proactive defense against them.
Threat Intelligence: Why it’s a Must-Have & How to Use it to Fortify Your Defenses (Part 2)
Karsten Chearis, Senior Security Solutions Engineer II
The more you know about potential attacks, attackers, their tools, targets and techniques, and the sooner you know about them, the better you can defend against them. This is why the best security programs incorporate external threat intelligence into their programs.
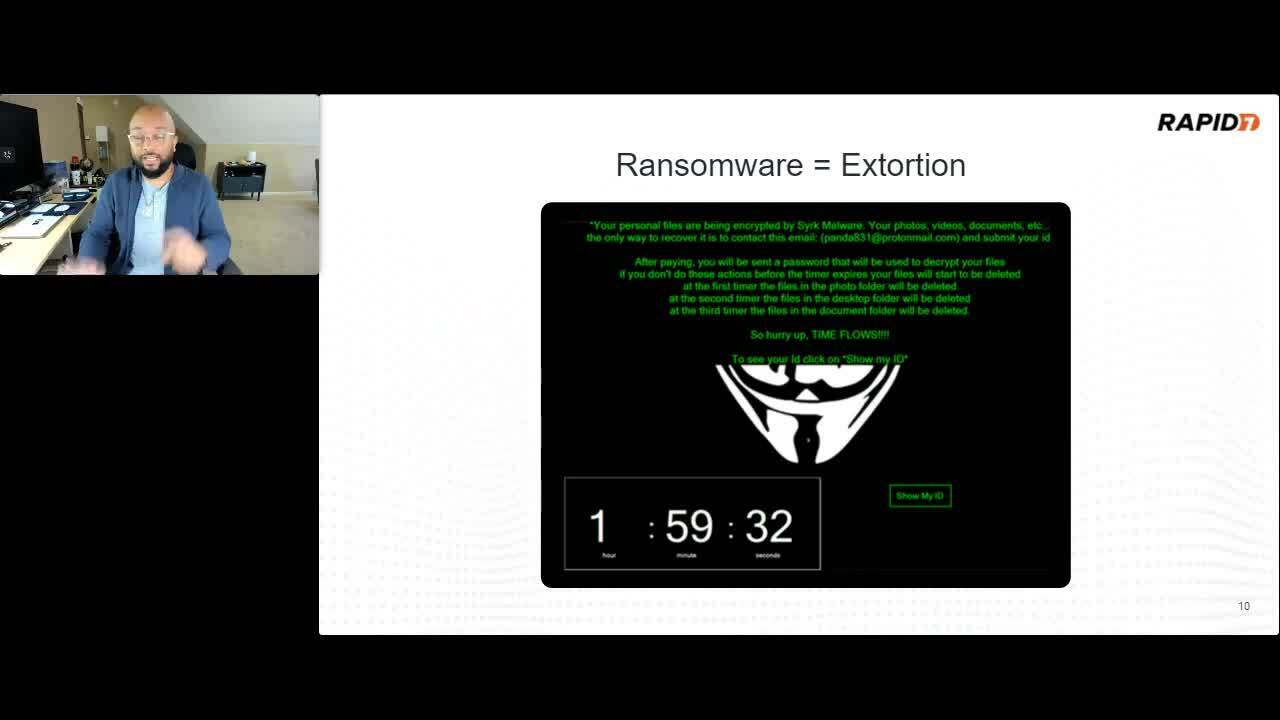
How to Pivot Fast and Defend Against Ransomware
Erick Galinkin, Principal Artificial Intelligence Researcher
We may all be targets, but we don’t have to be victims. As news and conversations focus on the trend of double extortion, how do defenses against “traditional” ransomware stack up? Learn about these trends and get specific advice on how to defend against them.

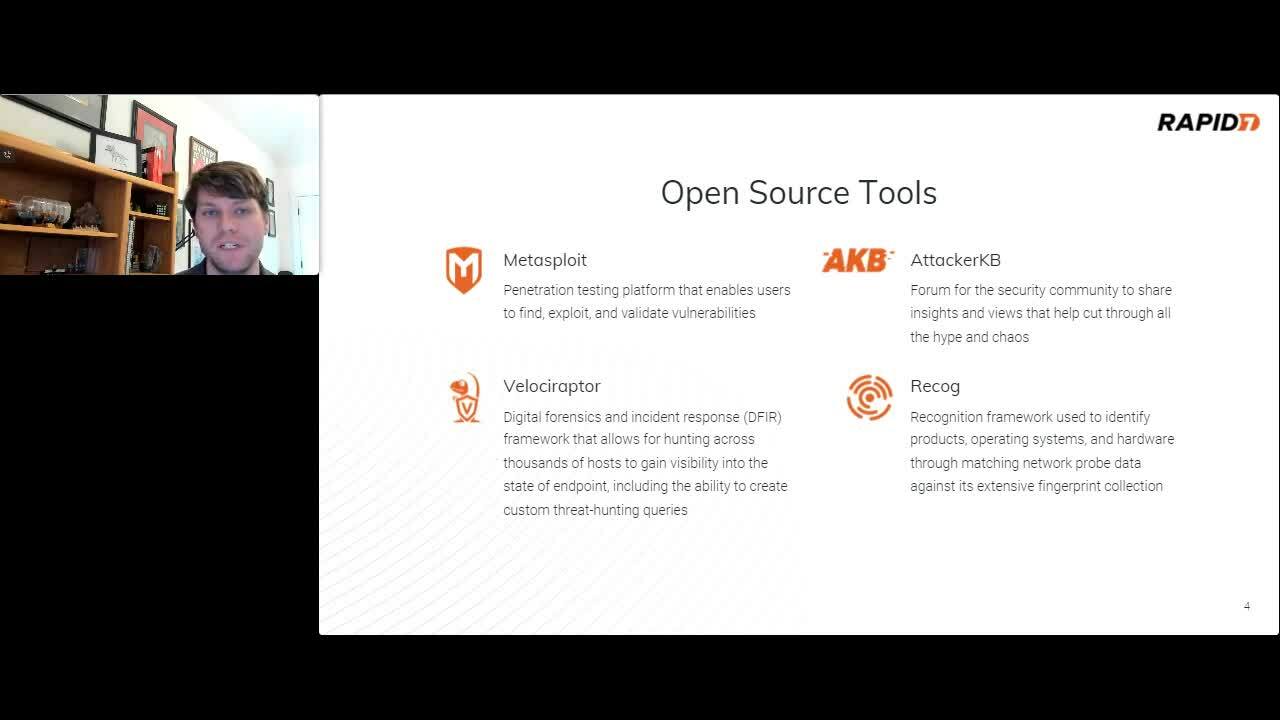
Better Together: Tips for Improving Your Security Program with Open Source Capabilities
Spencer McIntyre, Lead Security Researcher - VRM
Have you ever wondered why so much data, software, and threat intelligence is available in the public domain, via open source licensing? In this session we will review the “why” and the “how” of these projects and how you can leverage them to benefit your security program.
Cybersecurity Compliance - Simplifying the Complex
Harley Geiger, Senior Director, Public Policy
The complexity of cybersecurity regulations is a barrier to aligning compliance obligations with security programs. Join us as we identify commonalities among 10 major cybersecurity regulations, break down complicated regulatory text into a set of consistent cybersecurity practices, and organize the practices into core components of organizational security programs.

A Global SOC Never Sleeps: Advice on How to Build and Manage Yours
Jeremiah Dewey, VP, Managed Services Delivery Practice, Rapid7
Warwick Webb, Senior Director, Detection & Response Services, Rapid7
While every organization currently deals with security incidents in some way, most organizations struggle under the weight of alert fatigue, lack of visibility, and prioritization challenges. The managed services and professional services teams at Rapid7 work with more than 1,000 organizations of all sizes and levels of security maturity to help them operate and mature their incident response programs. From these experiences, Rapid7 has discovered some very helpful keys that you can apply to your program.
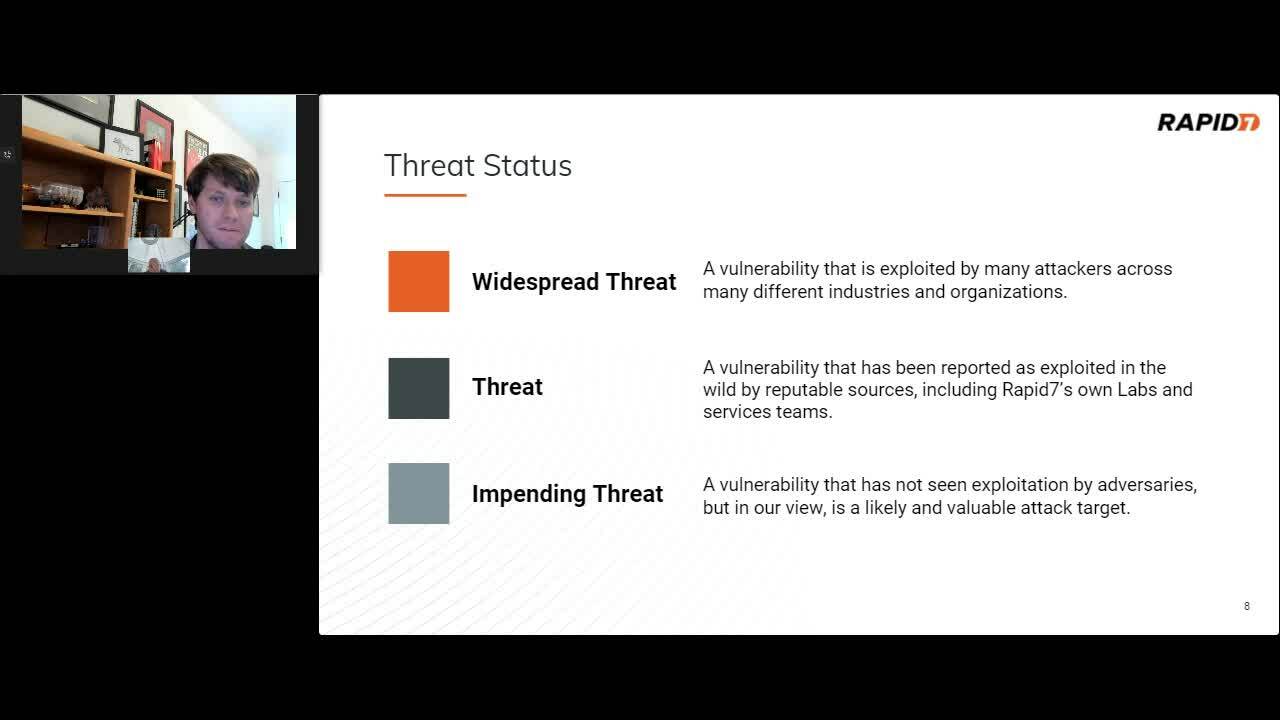
Into the Wild: Exploring Today’s Top Threats
Raj Samani, SVP, Chief Scientist, Rapid7
Spencer McIntyre, Lead Security Researcher
2021 was a challenging year for security and risk management teams. Today’s elevated threat climate demands a multi-faceted, context-aware approach to security. This presentation will explore how combining threat intelligence and vulnerability intelligence allows modern enterprises to anticipate and prevent attacks in addition to detecting and recovering from them more quickly.