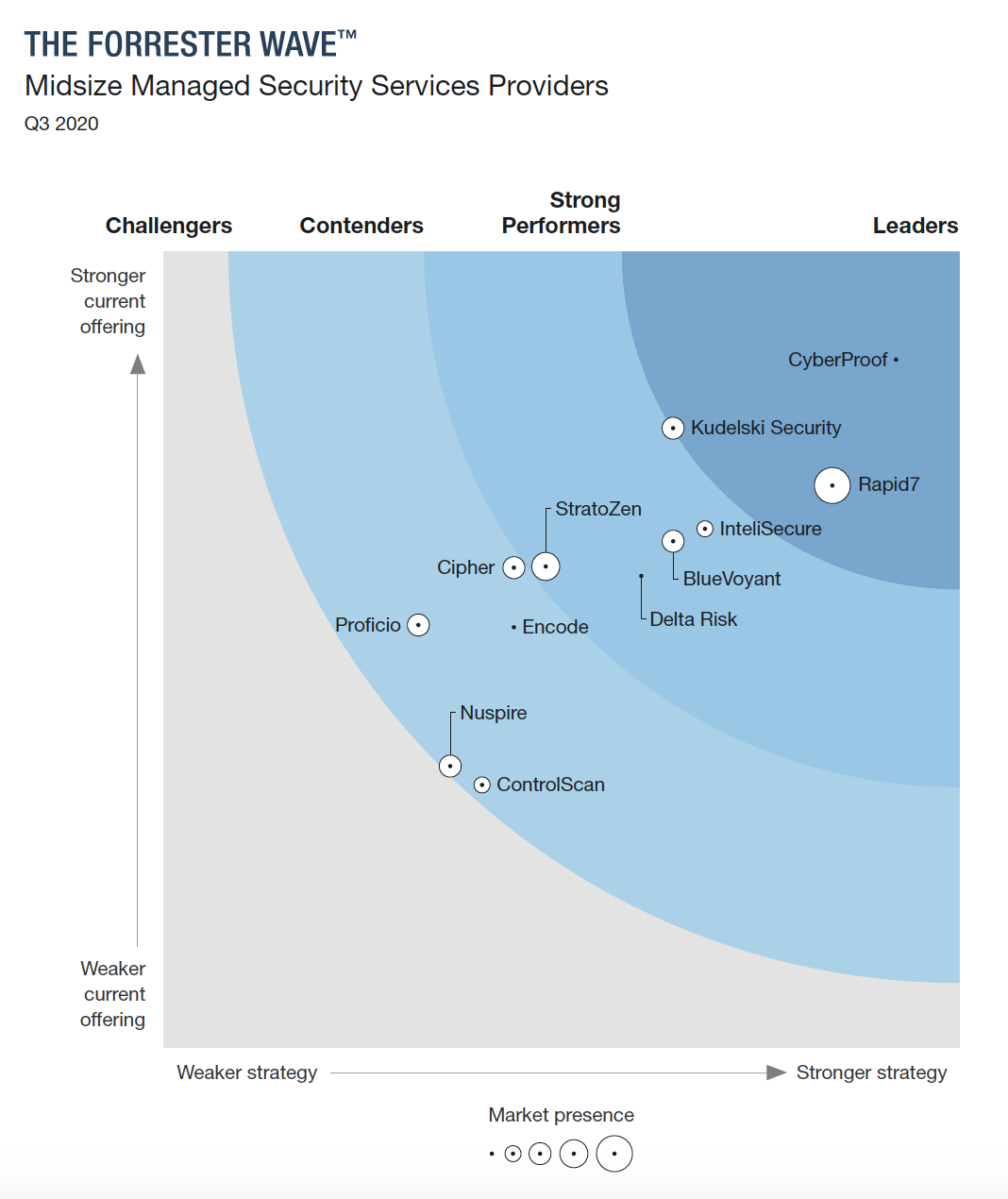
Forrester cites 26 significant criteria when evaluating MSSPs, with Rapid7’s comprehensive portfolio receiving the highest scores possible in 11 criteria. We believe our unique approach makes Rapid7 a viable alternative to traditional MSSPs. Our customers tell us that the following five criteria are especially critical.
5 Capabilities your managed security services provider needs:
1
A focus on three key areas of security excellence
Our experts partner with you to make sure you’re protected from all attack vectors:
users, endpoints, applications, and your network. Our mission is to accelerate your
security—no matter your current maturity level—with the tools, resources, and security
talent necessary to improve your detection and response , vulnerability management , and application security programs.
2
Proactive and reactive approaches to security
In addition to continuously scanning and monitoring your applications, users, network,
and endpoints for vulnerabilities or threats, our services also include built-in
detections for what our experts are seeing across all of our customer environments,
ensuring you’re always one step ahead of attackers.
3
A tailored program for your business
We’ve infused expertise from our researchers and global threat intel network into our managed services.
Our team learns your unique environment and provides tailored guidance
so you’ll always know what to do next to reduce attacker success, respond to events
quickly and confidently, and advance your security posture.
4
Foundational security capabilities, not just reports of alerts
Not only do our managed services customers each have a designated security advisor to
help strengthen your program and provide guidance on industry trends, but you’ll also
receive full access to the technology our team is using for transparency. This includes
dashboards, reporting, and the ability to further customize information and alerts if
needed.
5
World-class service from global experts
We have five managed services SOCs around the globe, meaning you’re covered no matter
where you are. Our team includes over 70 team members and 40+ security advisors who have
an average of five years security experience and over 500+ collective security
certifications. And with an outstanding 95+% 4-year analyst retention rate, you can
always count on us as an extension of your team.
Download Report
Rapid7's Insight Platform trusted by 9,100+ organizations & 120+ countries.



Reasons our customers love Rapid7 managed security services:
Simple and predictable pricing
Say goodbye to dynamic, data-based pricing. When it comes to strengthening your security posture, your goal is to protect your environment—not deplete your budget. Rapid7 offers unlimited data collection with pricing based on endpoints, IPs, and applications.
Exceptional business value even your CFO will love
Low total cost of ownership, great return on investment, and no need for additional headcount to build an effective security program. With transparency and reporting that any executive can follow, justifying the value of Rapid7’s managed services is easy.
Technical experts as an extension of your team
We care for your business as if it were our own. Each service is supported by multiple security experts that align delivery to your short- and long-term goals to ensure you’re not just protected, but always learning and always growing.
Understand every threat, with clear next steps
By combining technology and service, we uncover any vulnerable aspects or threats to your business. Then we detail exactly what’s needed to bolster your defenses, with clear direction so you understand the threats you face, prioritize which ones matter most, and respond with confidence.
Automate actions to free up your time
With Rapid7 managed services, we include prebuilt workflows to accelerate and streamline processes—no code necessary. When combined with our SOAR solution, InsightConnect, you expand these possibilities with 290+ plugins and workflows to automate aspects of your business, security, and IT.