Executive Summary
It’s harvest time (at least here in the United States), and as we prepare to reap the bounties of the land, so too have we seen attackers make good use of the exploits they’ve sown and infrastructure they’ve co-opted. The credential compromises and remote access attempts of Q2 have ripened into suspicious service logins and lateral movement actions involving credentials, along with increases in the presence of malware on systems. We've included a handful of Q3 highlights below, but read the full report to learn more, and be sure to register for our webcast (November 15, 2:00 p.m. ET/11:00 a.m. PT) to hear directly from researchers what these trends mean for 2018.
Adversaries on vacation:
Summertime generally means vacation time, and as a result there’s a definite slowdown in threat events involving user interaction. We'll watch for a return to "normal" in Q4.
Detected Emotet/Hedeo use:
We saw Emotet/Hedeo campaign usage in 70% of malware-oriented incidents in September across many industries, including healthcare, real estate, and construction. The entry point? Malicious spam or phishing emails.
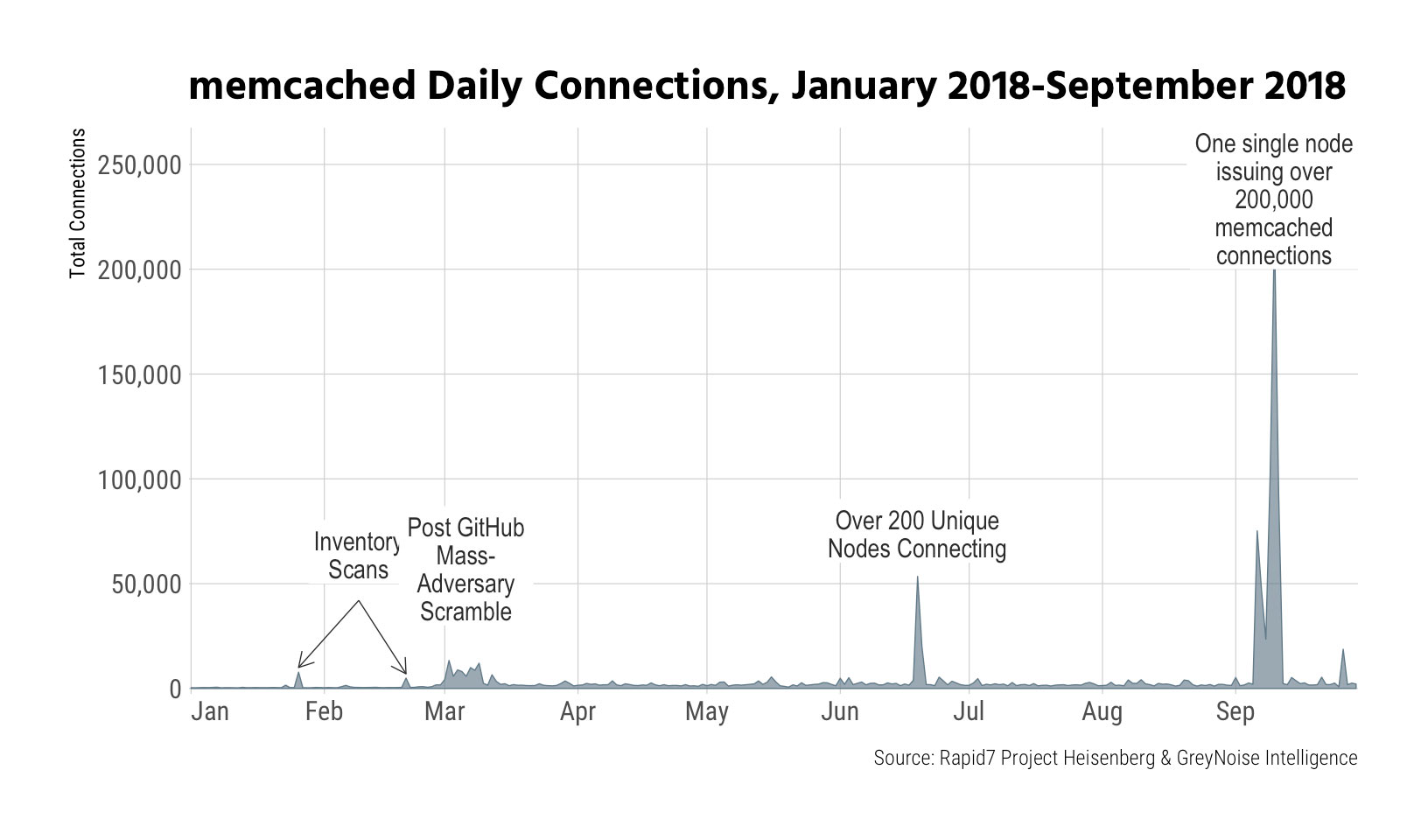
Memcached resurgance:
There was a continued threat of memcached being used in amplification attacks, including from a single node in Indonesia IPv4-space, along with Mirai letting us know “it’s not dead yet.”