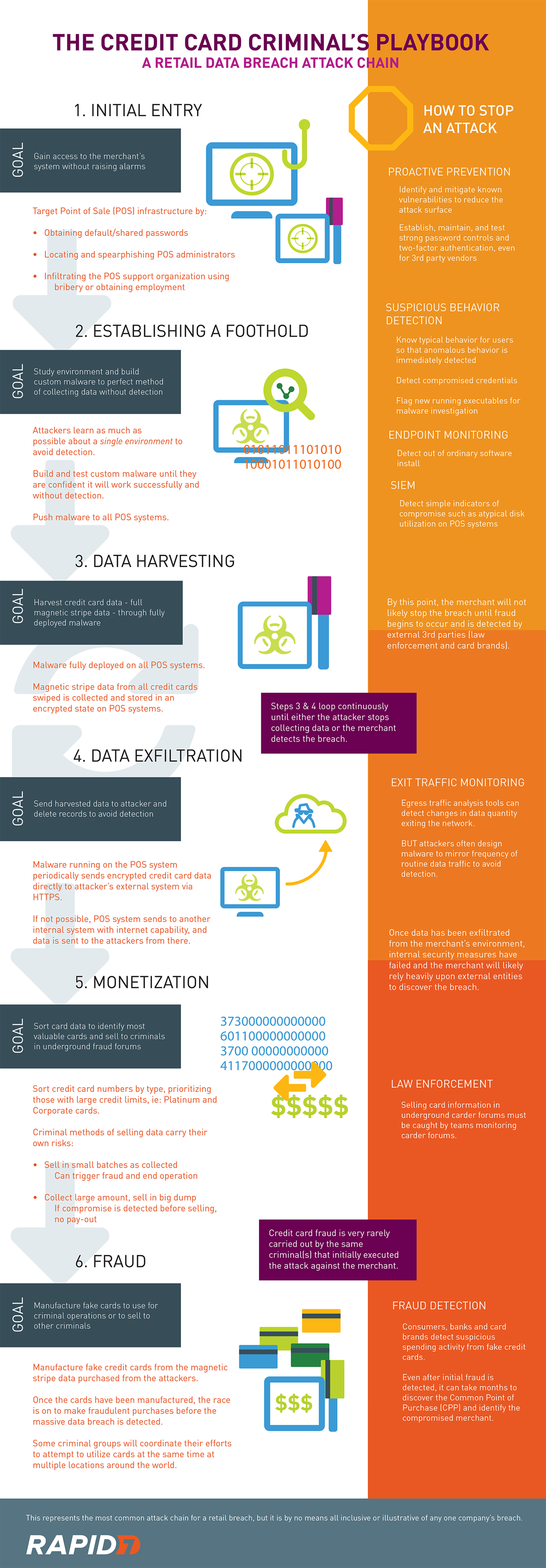
From initial entry to fraud, this timeline of a retail breach shows the steps criminals take to execute a retail data breach attack.
[Toolkit] CIS Top 20 Controls
Looking to implement the CIS top 20 security controls? Download our toolkit to get started.
Download Now