It’s time to take your threat intelligence to the skies. Today’s attackers can easily contort malware and switch up their infrastructure, leaving security teams that chase attackers with static indicators and artifacts constantly feeling a step behind. While IP addresses, processes, and domains change, there is an underlying set of stealthy attacker techniques that foreshadow every successful breach.
At Rapid7, we see a constant stream of threats, from the Metasploit project, our Managed Detection and Response customers, and incident response and penetration testing engagements. During threat investigations, our expert analysts zero in on these stealthy techniques, while researching the attacker’s targets and goal. This intelligence is crafted into Attacker Behavior Analytics (ABA) detections, which can find malicious behaviors even if they have been altered to evade prevention defenses.
[ウェブキャスト] ATT&CK のコツをつかむ
このオンデマンド・ウェブキャストで、お客様がMITRE ATT&CKフレームワークをどのように活用できるかを学んでくだい。
今すぐ視聴するAttacker Behavior Analytics Library
Below is a list of released ABA detections, all of which come with our threat detection solution, InsightIDR, and automatically match against your data in real time. This is threat intelligence that moves at the speed of the attacker—if a new exploit comes out, our team will craft a detection, test it against the Rapid7 Platform, and deploy it in InsightIDR—all within hours. Still craving that aged, open-source threat feed now?
- Office 365 Spearphishing Campaigns Verticals targeted: All
- Mshta Used to Evade Prevention Defenses Verticals targeted: All
- Hidden Cobra Verticals targeted: All
- Leafminer Verticals targeted: Government
- Luoxkep Campaign Verticals targeted: All
- Remote Desktop Brute-Force Attempt IPs, Existing ABA Updates Verticals targeted: All
- Thrip Attack Group, Remote Admin Tools Verticals targeted: Communications, defense contractors, others
- VPNFilter Verticals targeted: All
- Malicious PowerShell Verticals targeted: All
- Valyria Downloader, OilRig Verticals targeted: All
- Satan Ransomworm, Orangeworm Verticals targeted: Healthcare, manufacturing, agriculture
- Fauxpersky, SamSam Verticals targeted: Healthcare, government, education
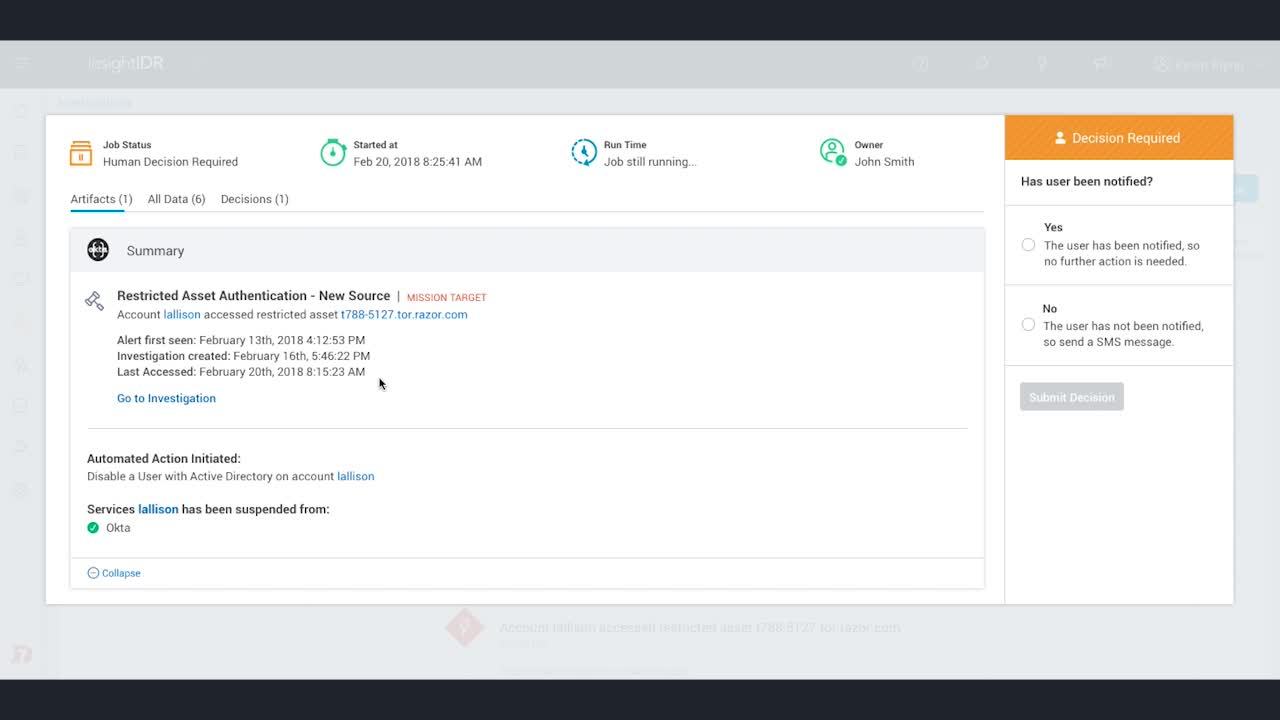
攻撃者の行動分析の実際の動作
InsightIDRでどのように攻撃者の行動を検知しているか、クラウドSIEMの詳細をご覧ください。
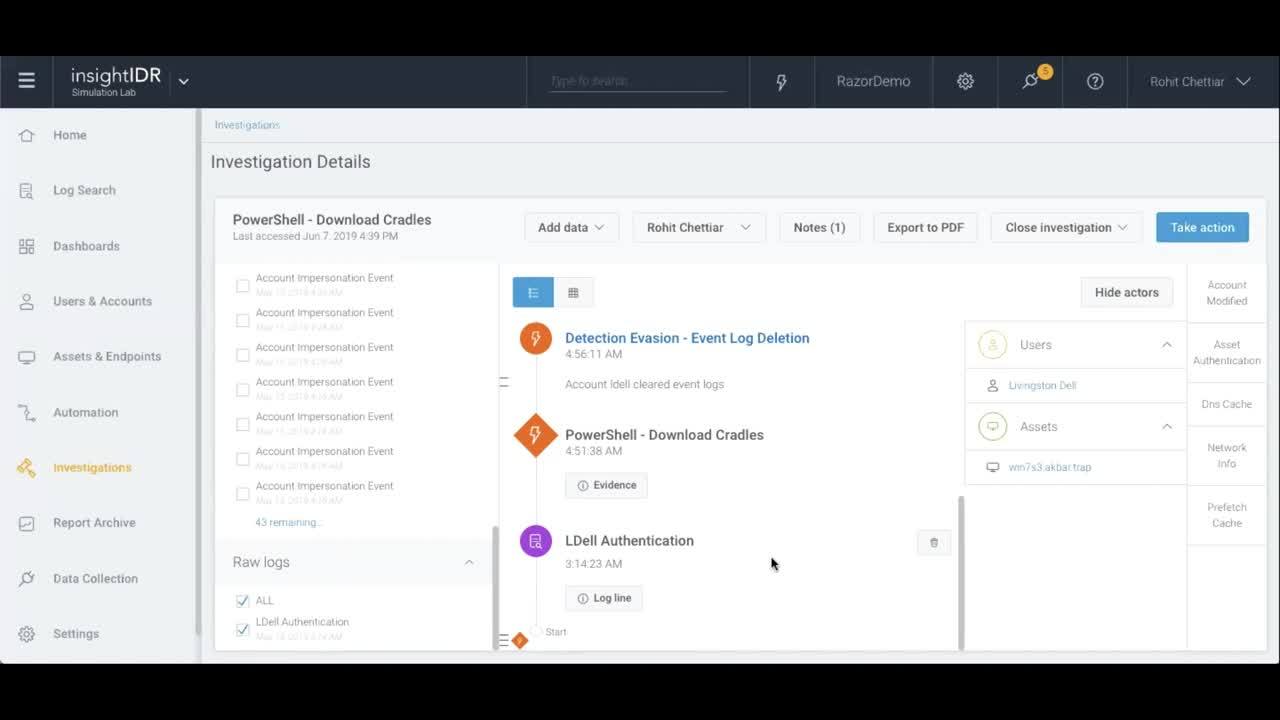
InsightIDRでPowerShellとMimikatzのアクティビティを調査する
nsightIDRが、PowerShellを使用してインターネットから実行可能ファイルをダウンロードする攻撃者の動作を検出する方法をご覧ください。