- Product: Nexpose , Metasploit
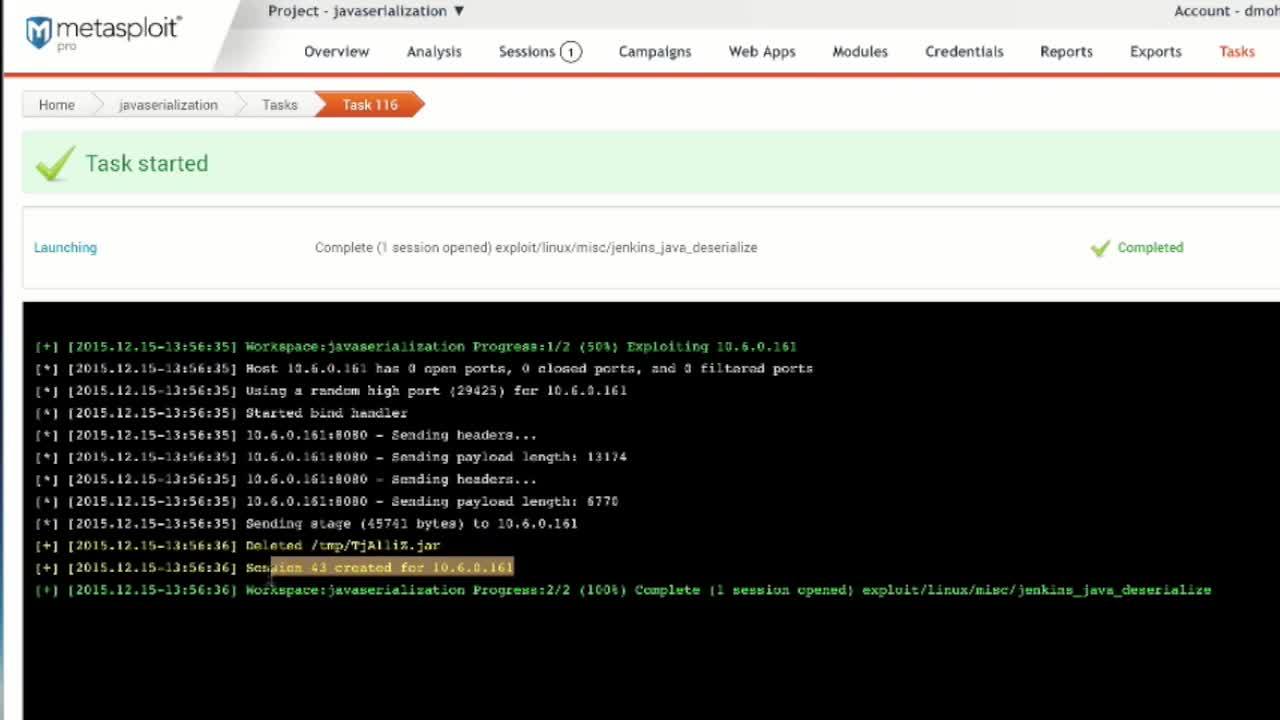
In this week’s Feature Friday, Brian O’Neill Sr. Product Strategist, will show you how to scan for the Java Deserialization vulnerability in Nexpose to see where this vulnerability exists on your network, and then validate exploitation is possible in Metasploit Pro.
The Java Deserialization vulnerability allows remote attackers to execute unknown and unapproved code in a java application. There are potentially millions of Java applications deployed on the internet that are vulnerable to this attack method. Several very common middle ware applications have already been proven to be exploitable such as jBoss, Oracle WebLogic, Jenkins and WebSphere. Luckily you can use Nexpose to determine if your applications are at risk and Metasploit Pro to validate this risk. You can read our blog post providing more details here.
By validating that this vulnerability is exploitable on your network, you are able to prove to your IT team that remediation needs to happen swiftly and demonstrate the real risk associated with it.
If you are interested in scanning for and validating vulnerabilities, download Nexpose and Metasploit.
See Nexpose in Action
Learn how our vulnerability management software can help you find, prioritize, and reduce risk.
Watch Demo