Now that we’ve reached the end of another year, you may be looking around the cybersecurity infosphere and seeing a glut of posts offering “hot takes” on the 2024 threat landscape and predictions about what’s coming next. At Rapid7, we don’t truck in hot takes, but rather, cold hard facts. Staying ahead of adversaries requires more than just advanced tools — it requires the latest intelligence and collaborative insights from experts working from data that tells the whole story.
In this blog, the global experts across our Rapid7 Labs and Managed Services teams share real-time vulnerability insights and threat intelligence so that our customers can anticipate and prevent breaches, pinpoint critical threats, and confidently take command of their attack surface.
Our teams responded to hundreds of major incidents, significant vulnerabilities, and ransomware threats in 2024, bolstered by visibility into hundreds of trillions of events analyzed by the Rapid7 Threat Engine. Our response included emergent threat and external vulnerability research, which we share with the community regularly here on the Rapid7 blog, as well as incident response activities for our managed security customers around the globe.
The Rapid7 Labs team has rounded up statistics and trends that caught our eye throughout the year, spanning ransomware, initial access vectors, common malware strains, notable CVE exploitation, and more.
Ransomware Group Activity
The 2024 ransomware landscape was all about pushing boundaries, with several groups striving to make a name for themselves in extortion circles. Based on Rapid7 Labs data, 33 new or rebranded threat actors appeared between January 1 and December 10, 2024. In that same time period, there were a total of 75 groups (including the newbies) actively seeking to extort their victims by posting stolen data to their leak sites. Between these 74 groups there have been a total of 5,477 leak site posts.
Ransomware-as-a-service (RaaS) groups like RansomHub exfiltrated data from hundreds of targets spanning healthcare, financial services, critical manufacturing, and many more. Rapid7’s ransomware data shows that since this group emerged in early February of this year, it has made 573 posts to its leak site (as of November 30). This high number of posts has earned RansomHub a spot in Rapid7’s “Top 10 Active Ransomware Groups” list for 2024, coming in a very close second to LockBit, which finished November with 579 posts. View the entire top 10 in the graphic below.
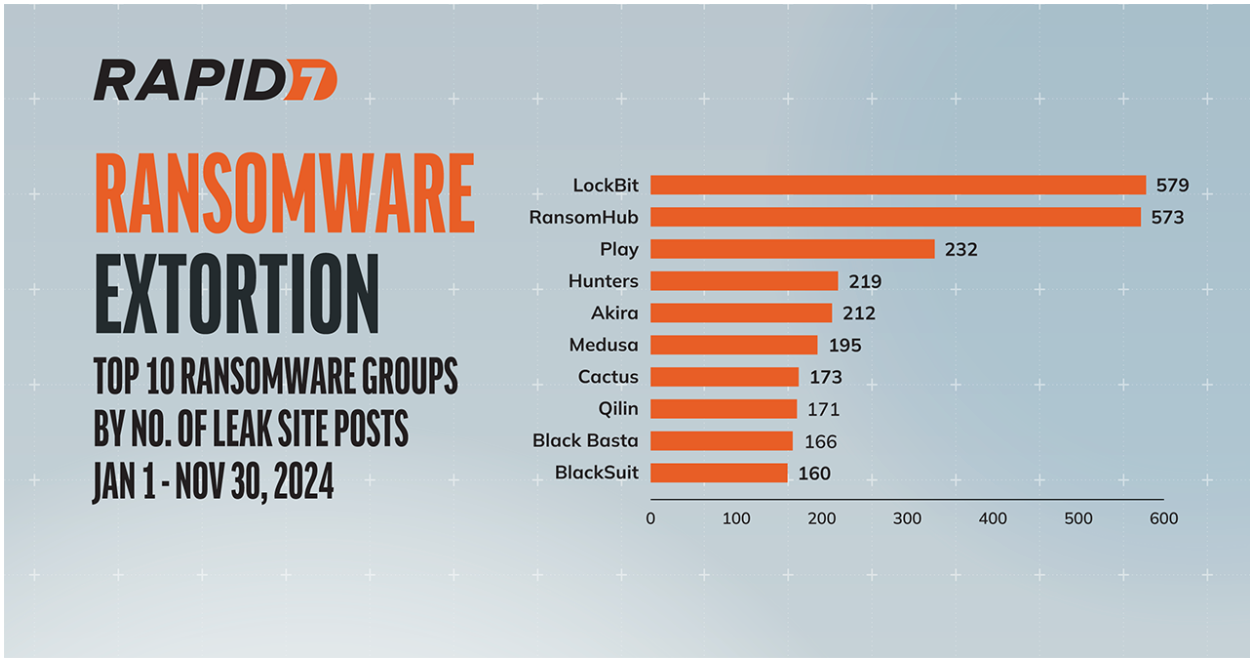
While not as prolific at posting on their leak site as RansomHub, Qilin is an example of an established player that has exposed troves of sensitive data as well as achieved significant payouts. Not one to shy away from the healthcare space, Qilin leaked just under 1 million patient records after an attempt to extort $50m from London hospitals earlier this year. With typical ransom demands ranging from $50,000 to $800,000, plus a generous affiliate scheme, Qilin will likely be a mainstay of 2025.
One or two new groups are combining high-visibility attacks with attention-grabbing marketing stunts, most likely to quickly work their way up the affiliate ladder. Hellcat has seemingly come from nowhere to demand $125,000 in “French bread” from one victim. This is, of course, a gimmick on their part, with the ransom expected to be paid in Monero cryptocurrency. There are frequently much larger ransoms demanded, but not all of them come with built-in press appeal.
Several groups have periods in which they seemingly “go dark,” where we do not see posts to their leak sites for weeks at a time. It may be that these groups are using this time to rework their infrastructure, or perhaps they are receiving quick payouts from victims wishing to avoid reputational damage and the negative press associated with a breach coming to light.
Incident Response Trends
Rapid7 incident responders have seen a combination of fresh-faced ransomware groups and old security tricks filling out much of the year. As organizations work to secure their externally facing systems, they must also account for criminals seeking to deceive employees with social engineering and psychological sleight of hand.
Looking out across organizations' expansive attack surfaces, Rapid7 incident responders observed several vulnerabilities exploited in the wild for initial access this year. The verticals Rapid7 saw targeted the most were manufacturing, professional services, retail, and healthcare.
Social engineering in 2024 was geared toward easy initial access via exploitation of support services. One customer case involved a help desk employee being tricked into configuring a new MFA device and resetting a user password. A separate incident involved an SEO poisoning attack and the download and installation of a trojanized version of the freeware disk analyzer tool SpaceSniffer. Analysis and cleanup tools are popular targets for fake advertisements and bogus downloads, which are typically found at the top of sponsored search results.
Most Observed Malware
Several forms of malware have been at the front of the pack throughout 2024 across all industries. SocGholish, GootLoader, and AsyncRAT led the charge with a heady mix of remote access and credential theft. More than one-quarter (28%) of the customer incidents Rapid7 responded to in 2024 involved one of these three malware families.
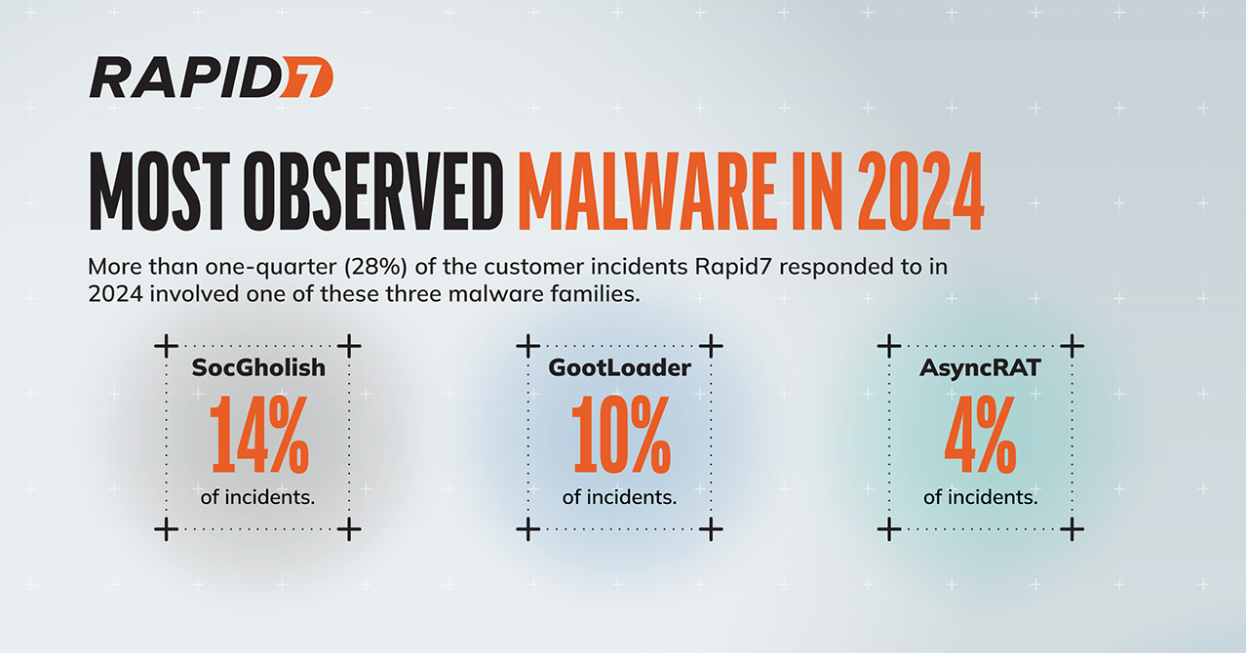
SocGholish was observed in 14% of incidents during 2024. The first of three heavily observed malware mainstays of 2024, SocGholish (also known as FakeUpdates) is rooted in website compromise and drive-by attacks. Hijacked websites are used to offer bogus “updates” to unsuspecting end users. You can see an example similar to SocGholish in our analysis of ClearFake from August 2023.
SocGholish updates often masquerade as commonly used programs like web browsers. If the campaign owners find the target system to be of interest, JavaScript is used to trigger a payload drawn from a wide variety of malware. In July of this year, SocGholish was used to distribute AsyncRAT, another of our most commonly observed remote access trojans (RATs).
GootLoader was observed in 10% of incidents during 2024. It is frequently observed in SEO poisoning campaigns typically involving targeted keywords on compromised websites. It is the delivery method for payloads such as Cobalt Strike via diverse search engine queries such as “Bengal cats” and “employment agreements.”
AsyncRAT was observed in 4% of incidents during 2024. It is a RAT that has been in use since 2019 for activities like data theft and keylogging. AsyncRAT typically arrives on a PC through social engineering or phony attachments and can also be used to deploy additional malware. It has also recently been used as part of a GenAI malware distribution campaign.
Initial Access Vectors
Vulnerability exploitation and remote access to systems without multi-factor authentication (MFA) continued to be the largest drivers of incidents overall in 2024, at 17% and 56% of incidents, respectively. We saw a significant (and rather unfortunate) shift in year-over-year initial access data in 2024 when compared to 2023. Roughly 40% of the incidents the Rapid7 Managed Services team saw in Q3 2023 were remote access to systems with missing or lax enforcement of MFA, particularly for VPNs and virtual desktop infrastructure (VDI). In Q3 2024, fully two-thirds (67%) of incident responses involved abuse of valid accounts and missing or lax enforcement of MFA — once again, mainly on VPNs and VDI, though exposed RDP also added a small number of incidents to remote access counts.
Vulnerability exploitation also remains a prevalent initial access vector, holding firm at 13% of incidents for both Q3 2023 and Q3 2024. Rapid7 MDR observed exploitation of the following CVEs in customer environments between January and November 2024 (non-exhaustive):
- CVE-2024-3400 in Palo Alto Networks PAN-OS
- CVE-2024-24919 in Check Point Security Gateways
- CVE-2024-1709 in ConnectWise ScreenConnect
- CVE-2023-48788 in Fortinet FortiClient
- CVE-2023-48365 in Qlik Sense Enterprise for Windows
- CVE-2023-36025 in Windows SmartScreen
- CVE-2020-14882 in Oracle WebLogic Server (Oracle Fusion Middleware)
- CVE-2018-15961 in Adobe ColdFusion
As the CVEs above demonstrate, the vulnerability exploitation Rapid7 has observed in managed customer environments has included newer flaws in addition to older, known vulnerabilities that have previously been under attack. Both Adobe ColdFusion CVE-2018-15961 and Oracle WebLogic Server CVE-2020-14882 have been on the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) list of Known Exploited Vulnerabilities (KEV) since November 2021.
Notable Vulnerabilities
While Rapid7 observed continued adversary use of zero-day vulnerabilities in network edge technologies like VPNs and secure gateways, zero-day flaws represented a lower overall percentage of major 2024 vulnerabilities when compared with what we saw in 2023. File transfer technologies also had a number of severe vulnerabilities disclosed in 2024 — but surprisingly, several of these have remained unexploited beyond the usual attempts to attack internet-facing honeypots. Critical issues in both Fortra’s GoAnywhere MFT software and Progress Software’s MOVEit Transfer solution were expected to see large-scale attacks, but happily, thus far those attacks have not materialized.
In Rapid7’s 2024 Attack Intelligence Report, we found that fully a quarter of widespread threat vulnerabilities our team analyzed for the period were the result of broad, global, zero-day exploitation by a single highly skilled threat actor. That trend lost traction in the back half of the year, but we still saw it rear its head from time to time. October 2024’s FortiManager RCE (CVE-2024-47575) offers a salient example: By the time the vulnerability was disclosed publicly, dozens of organizations around the world had already been compromised by a targeted but prolific threat campaign. A pair of widely exploited zero-day flaws in Palo Alto Networks firewalls (CVE-2024-0012, CVE-2024-9474) made for another prominent example. Rumors of a possible zero-day vulnerability swirled for weeks before the vendor was able to confirm real-world attacks in mid-November.
Below is a sample of notable CVEs from Rapid7’s vulnerability intelligence data, most (but not all) of which came under attack over the past 11 months.

Rapid7’s open platform for vulnerability research, AttackerKB, incorporated new tags in 2024 to allow users to note when vulnerabilities were observed in ransomware or state-sponsored attacks. Our team and our community added ransomware tags to more than 250 CVEs in 2024, and 75-plus vulnerabilities have been tagged for their (verified) use in known, state-sponsored threat campaigns. More than 1,700 unique CVEs have been reported exploited in the wild in AttackerKB, and we’ve incorporated hundreds of detailed vulnerability assessments from security researchers, incident responders, and pen testers. Interested in exploring more vulnerability data? Join the community here.
Key Learnings
The threat landscape in 2024 saw a host of new ransomware actors creating chaos in novel ways, but it also showed that attackers are willing to use tried and true techniques to breach defenses. At the end of the day (ahem, year) the best practices remain the best practices. Having a strong vulnerability risk management program in place, building strong defenses against phishing and spear phishing campaigns, having robust patching procedures (particularly for zero-days), and instituting multi-factor authentication remain some of the strongest ways to prevent threat actors from making your organization another statistic. Speaking of statistics, here’s an infographic with some highlights from this post.
As always, Rapid7 Labs is here to help. We’ve spent 2024 doing unique and groundbreaking research into the behaviors of threat actors and we have no plans to let up in 2025. If you would like to see our work to date, head over to the Rapid7 Labs page. And keep an eye on it for big things to come next year.