- Home
- Products
- InsightCloudSec
- Use Cases
- Simplify Identity and Access Management
InsightCloudSec
Simplify Identity and Access Management
Simplify Identity and Access Management
In cloud environments, everything has an identity: users, applications, services, and systems. This provides enormous flexibility, but also creates the potential for substantial risk as every service is potentially reachable by every other one.
InsightCloudSec helps organizations adopt a least-privilege access model by proactively analyzing cloud environments for excessive entitlements at scale.
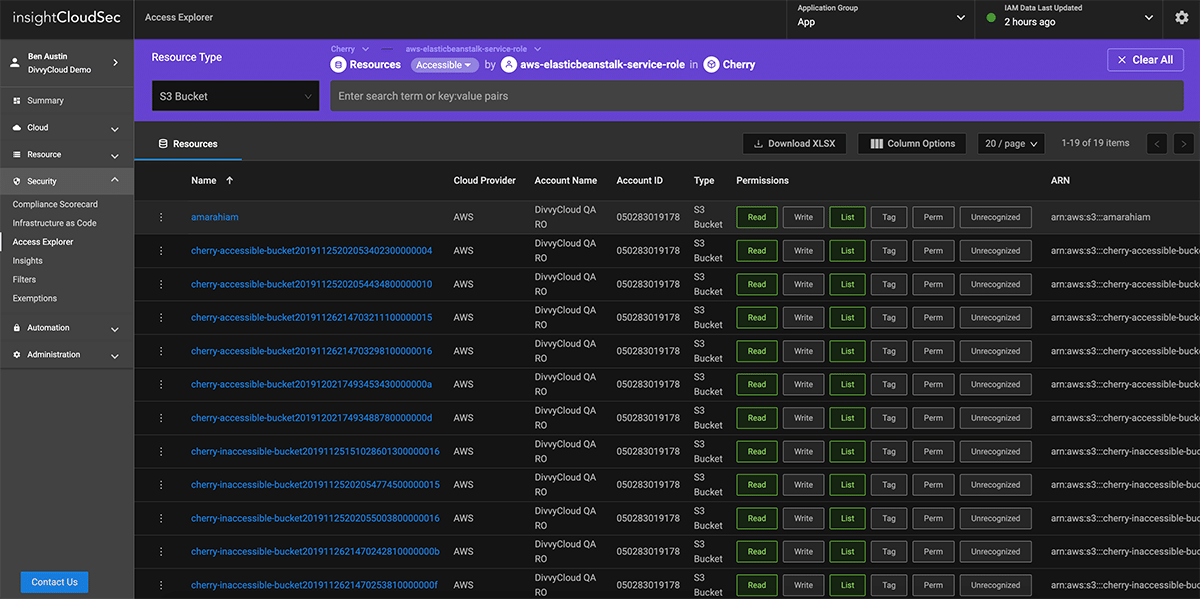

Organizations are adopting cloud and container services at scale in order to accelerate innovation. In this new era, Identify Access Management (IAM) becomes core to their ability to make cloud and container services secure and compliant.
The challenge is that IAM is extremely complicated, and governing within the self-service context of the cloud can be time-consuming. In these environments, everything has an identity: users, applications, services, and systems. This provides enormous flexibility, but also creates the opportunity for substantial risk, as every service is potentially reachable by every other service, regardless of location, but only if an implicit trust is defined.
Developers and other IT professionals are sometimes overwhelmed by the cloud IAM options available as they face competing goals: securing the environment while accomplishing their jobs with efficiency and speed. Further complicating this is the fact that the initial controls they implement will likely need to grow and adapt without disrupting productivity as cloud use scales and changes.
InsightCloudSec helps govern cloud IAM and creates a rational and sustainable approach for addressing perimeter fluidity and the substantial challenges of governing cloud environments at scale.
Protecting the identity perimeter at scale requires automated monitoring and remediation around access management, role management, identity authentication, and compliance auditing. InsightCloudSec helps you build a circle of trusted identities and layers of trust.